Desabilitar o acesso público
Se você desabilitar o acesso público, a conectividade com o servidor só será possível por meio de pontos de extremidade privados.
Você deve configurar esses pontos de extremidade privados para que os hosts que podem rotear o tráfego para a rede virtual do Azure na qual você injeta os pontos de extremidade privados possam acessar o servidor flexível do Banco de Dados do Azure para PostgreSQL.
Quando o acesso público é desabilitado, todas as regras de firewall que você criou enquanto o acesso público estava habilitado não são impostas.
Além disso, todas as modificações feitas nas regras de firewall são descartadas.
Usando o portal do Azure:
Selecione seu servidor flexível do Banco de Dados do Azure para PostgreSQL.
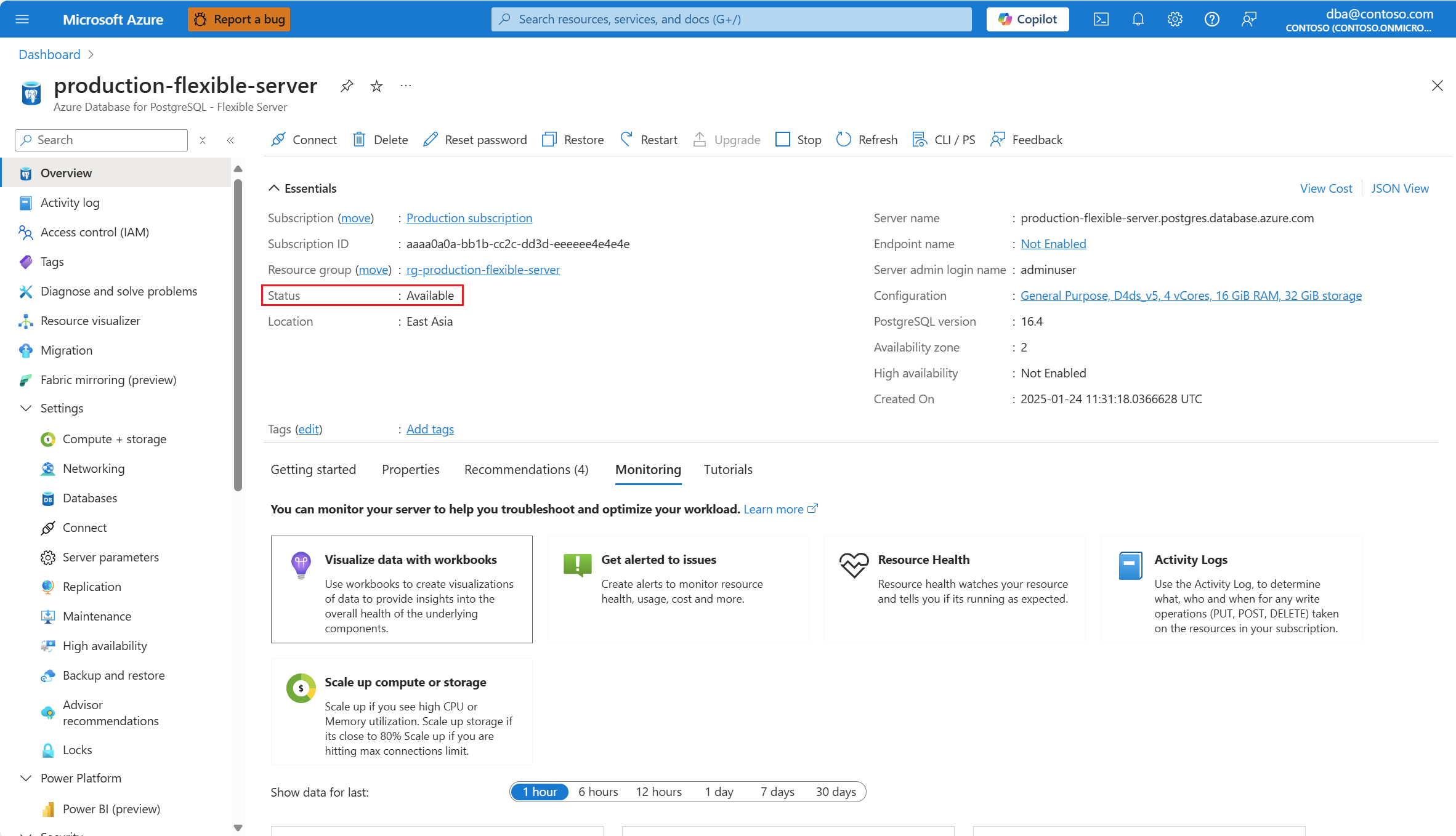
No menu de recursos, selecione Visão geral.
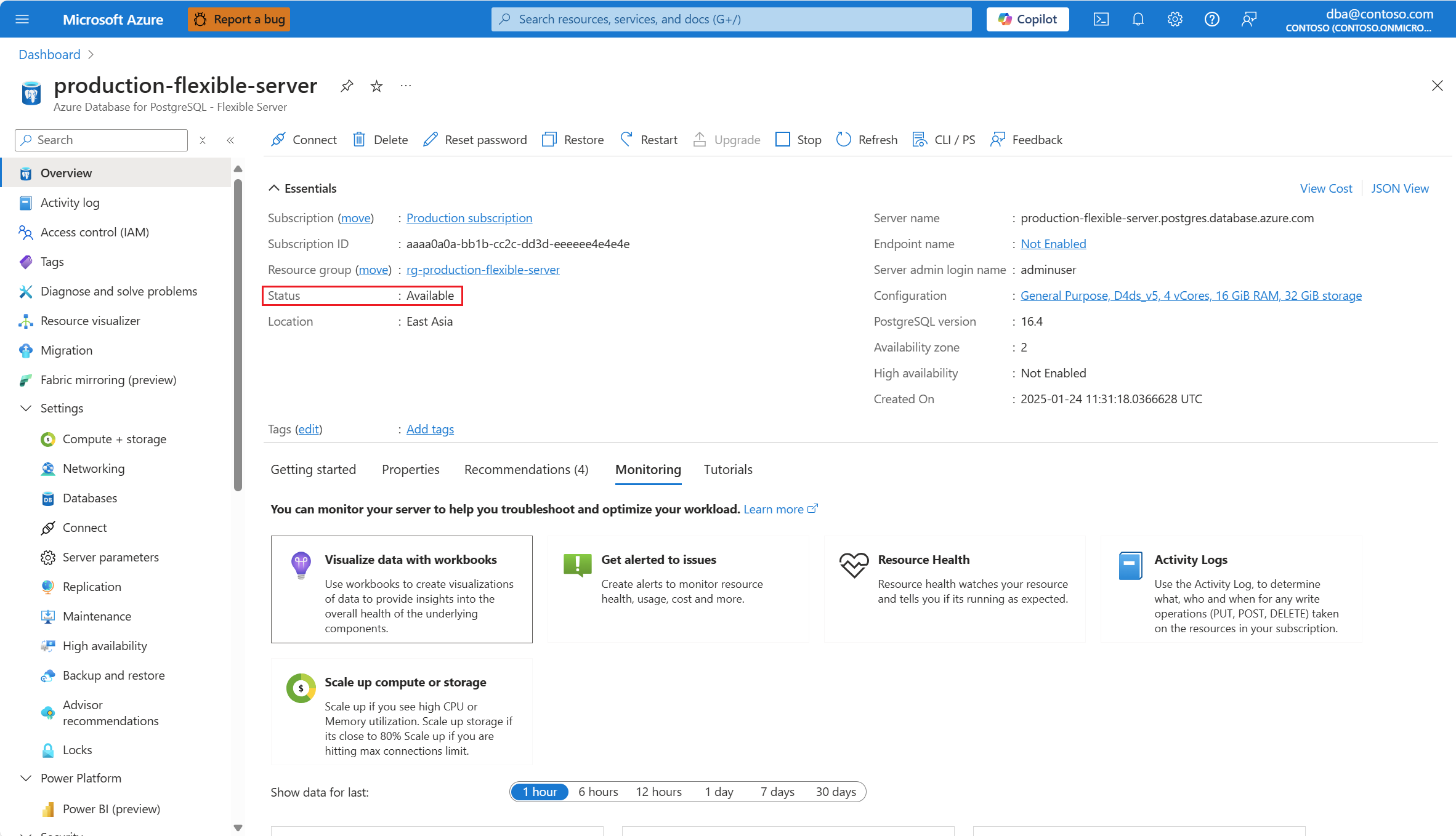
O status do servidor deve estar Disponível, para que a opção de menu Rede seja habilitada.
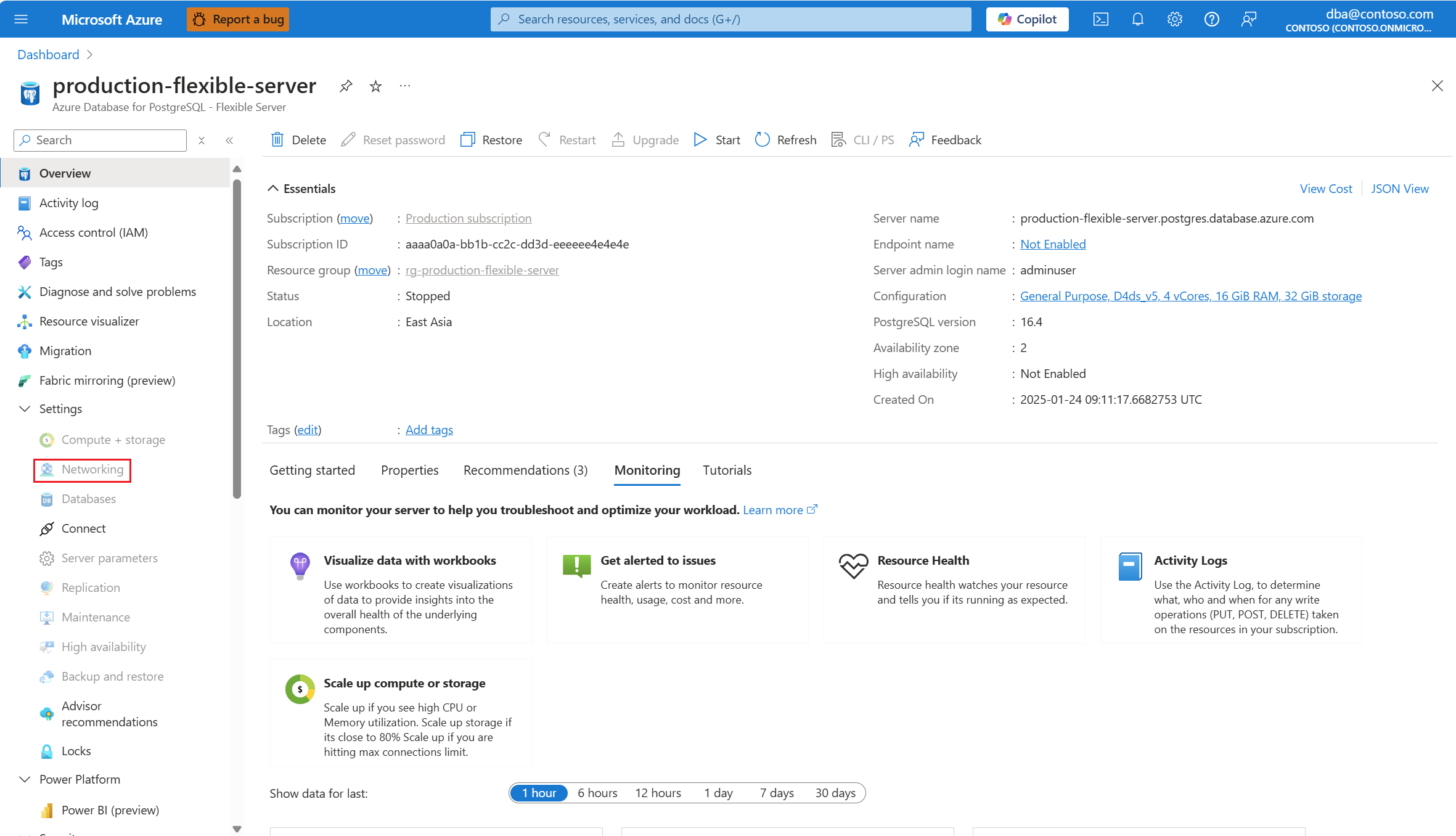
Se o status do servidor não estiver Disponível, a opção Rede será desabilitada.
Observação
Qualquer tentativa de definir as configurações de rede de um servidor cujo status não está disponível falhará com um erro.
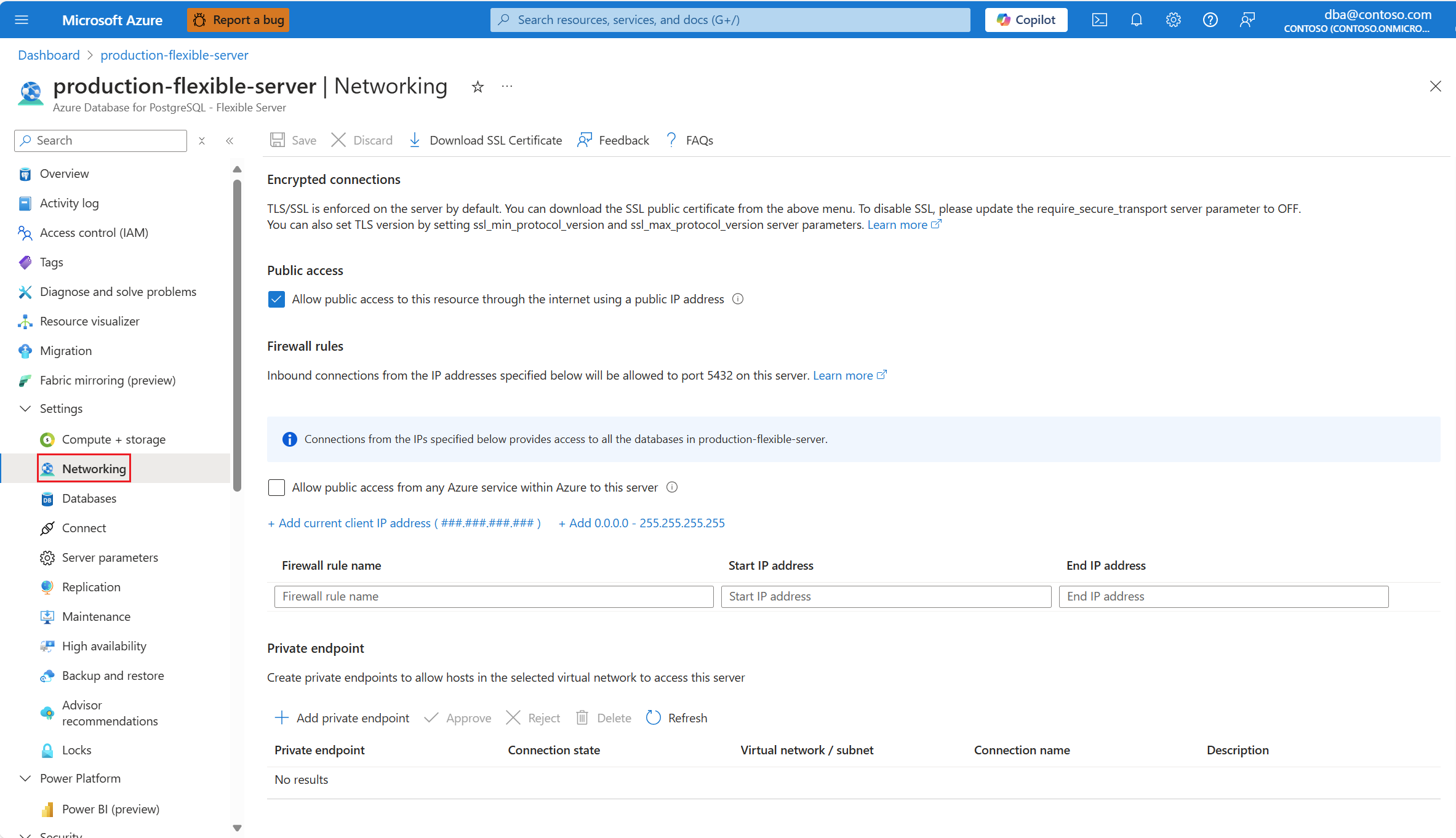
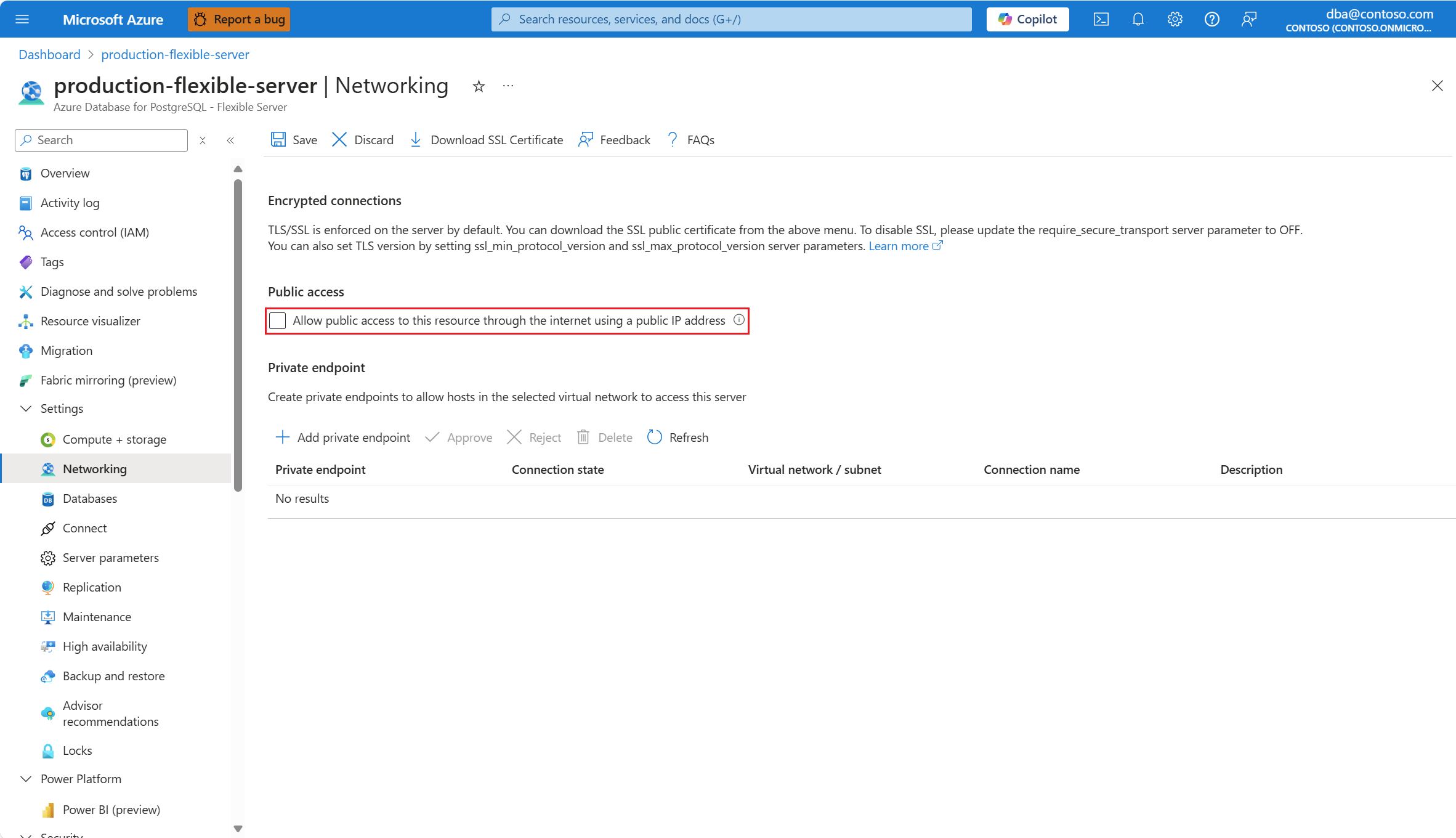
No menu de recursos, selecione Rede.
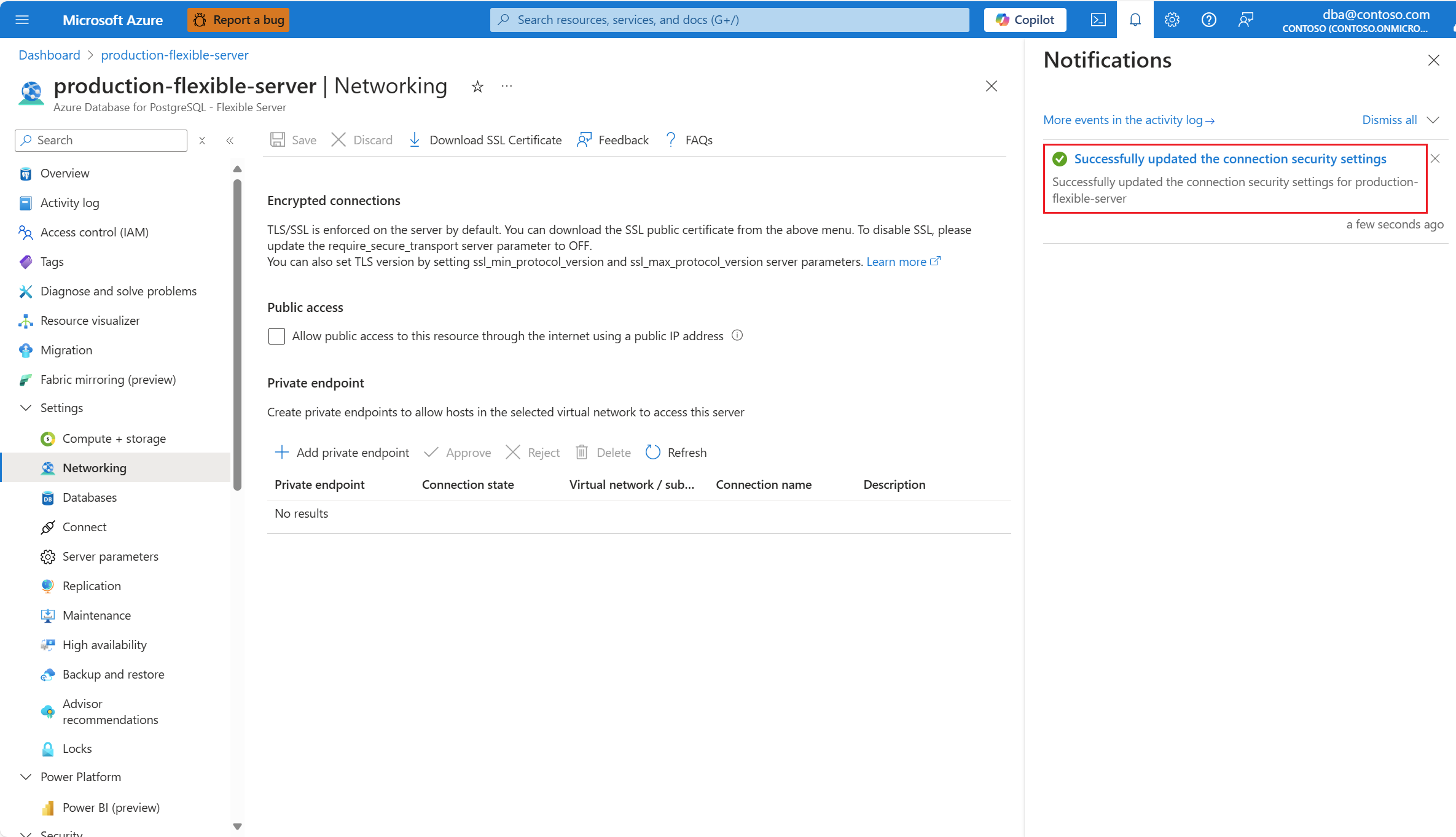
Desmarque a caixa de seleção Permitir acesso público a esse recurso por meio da Internet usando uma caixa de seleção de endereço IP público.
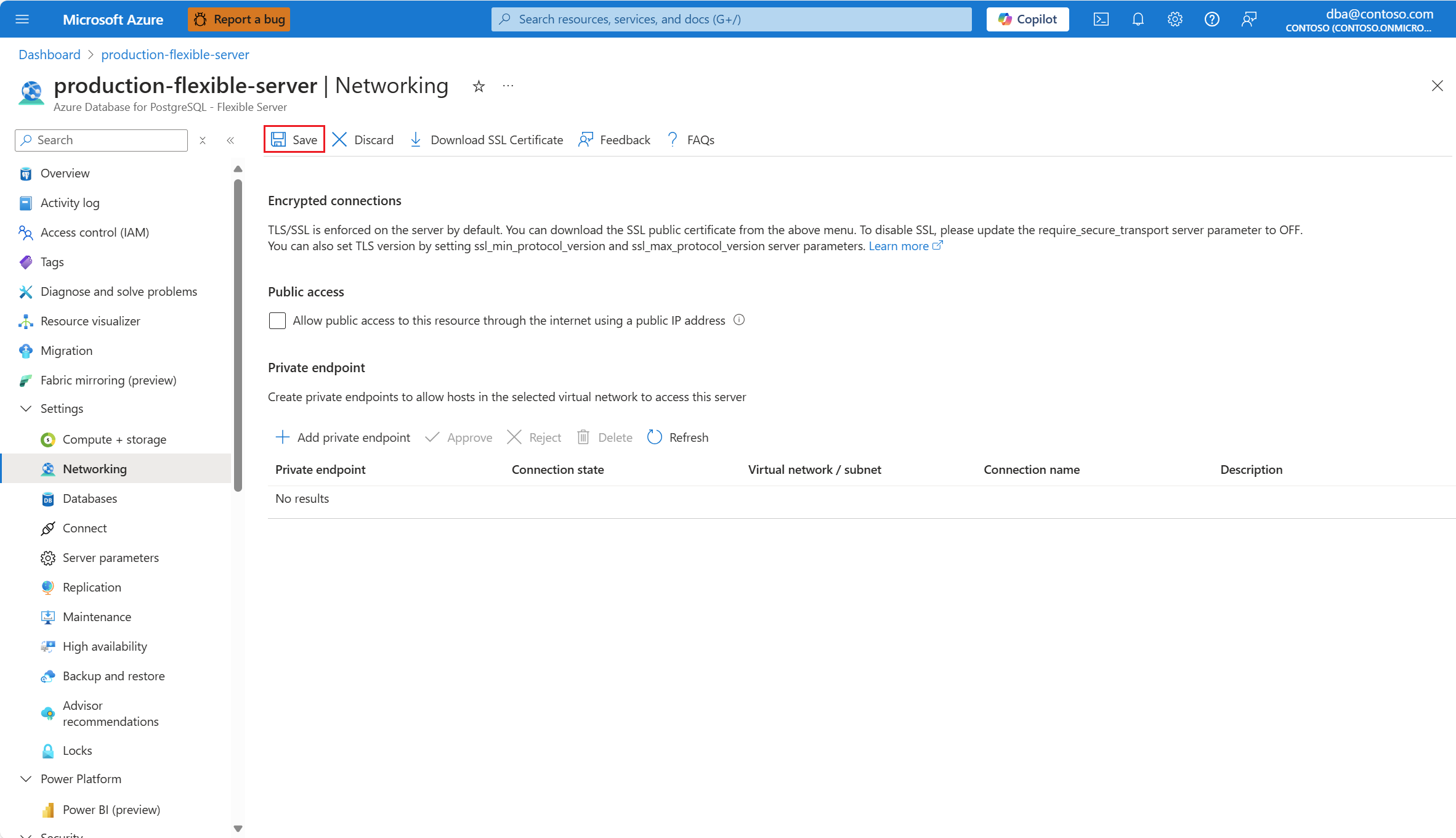
Selecione Salvar.
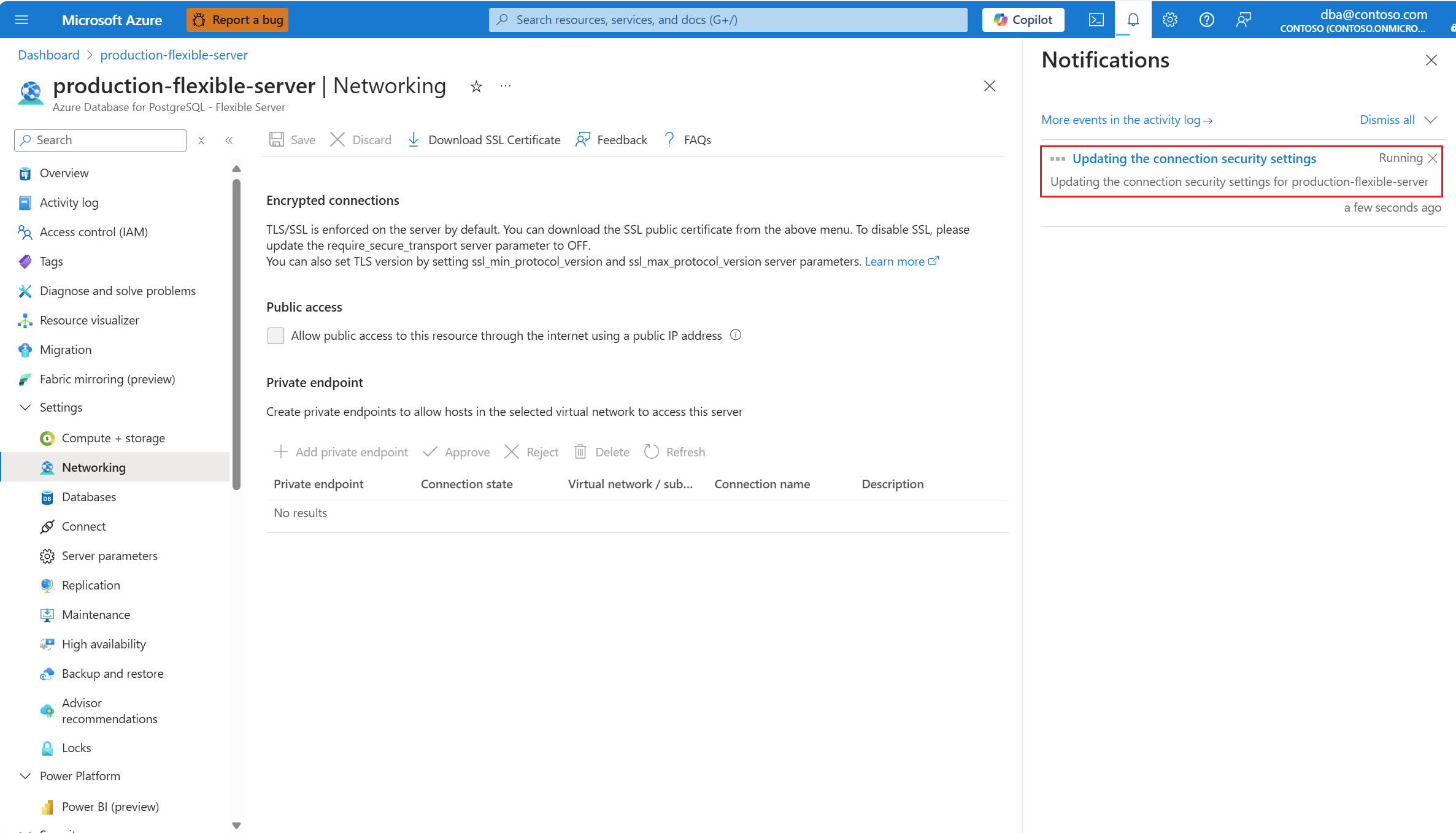
Uma notificação informa que as alterações estão sendo aplicadas.
Além disso, o status do servidor muda para Atualização.
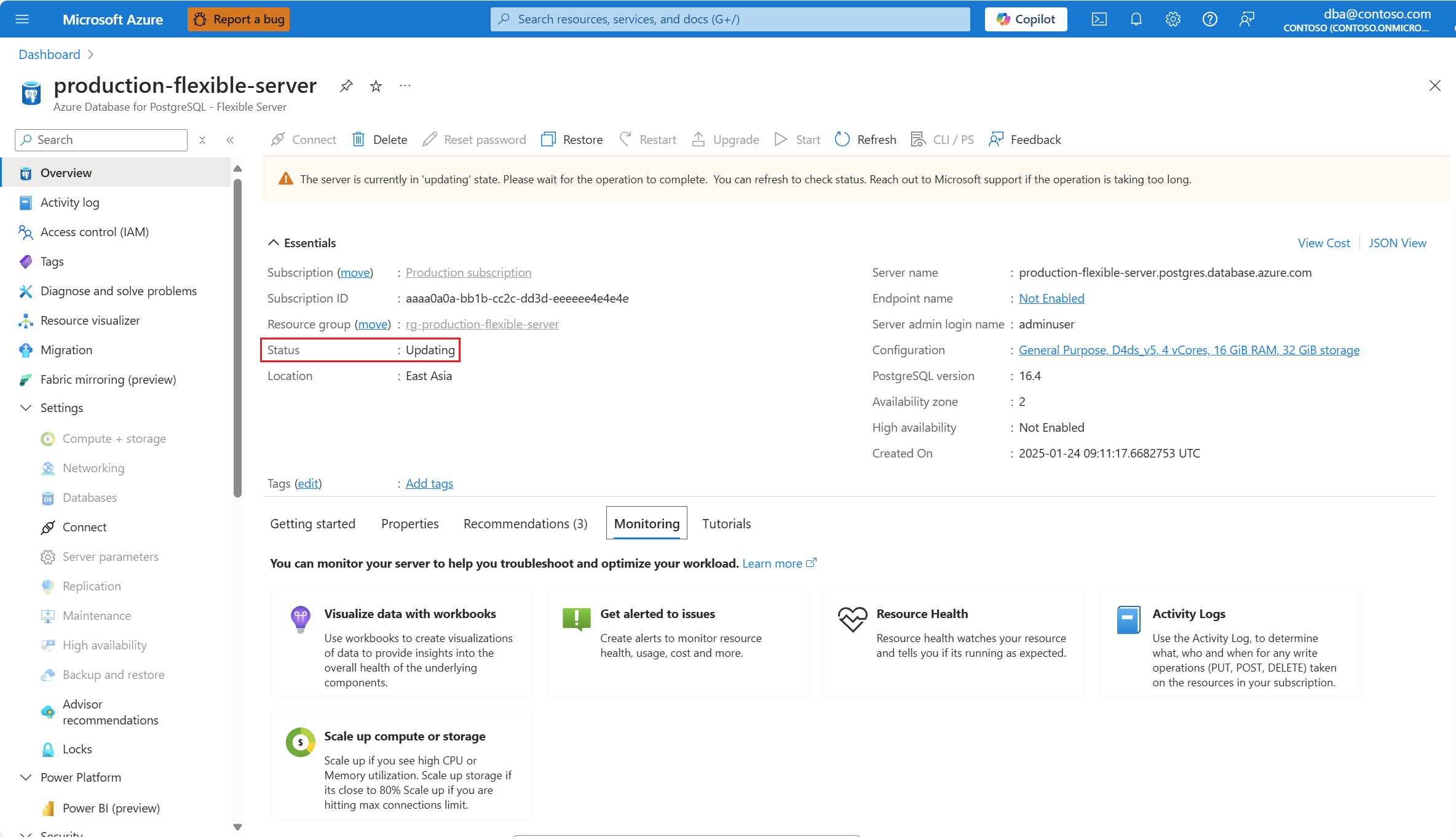
Quando o processo é concluído, uma notificação informa que as alterações foram aplicadas.
Além disso, o status do servidor muda para Disponível.
Conteúdo relacionado
- Redes.
- Permitir o acesso público.
- Adicionar as regras de firewall.
- Excluir as regras de firewall.
- Adicionar as conexões do ponto de extremidade privado.
- Excluir conexões de ponto de extremidade privado.
- Aprovar as conexões do ponto de extremidade privado.
- Rejeitar conexões de ponto de extremidade privado.