Add firewall rules
With public access enabled, you can configure firewall rules to allow connections originating from specific IP addresses, or from any Azure service.
Using the Azure portal:
Select your Azure Database for PostgreSQL flexible server.
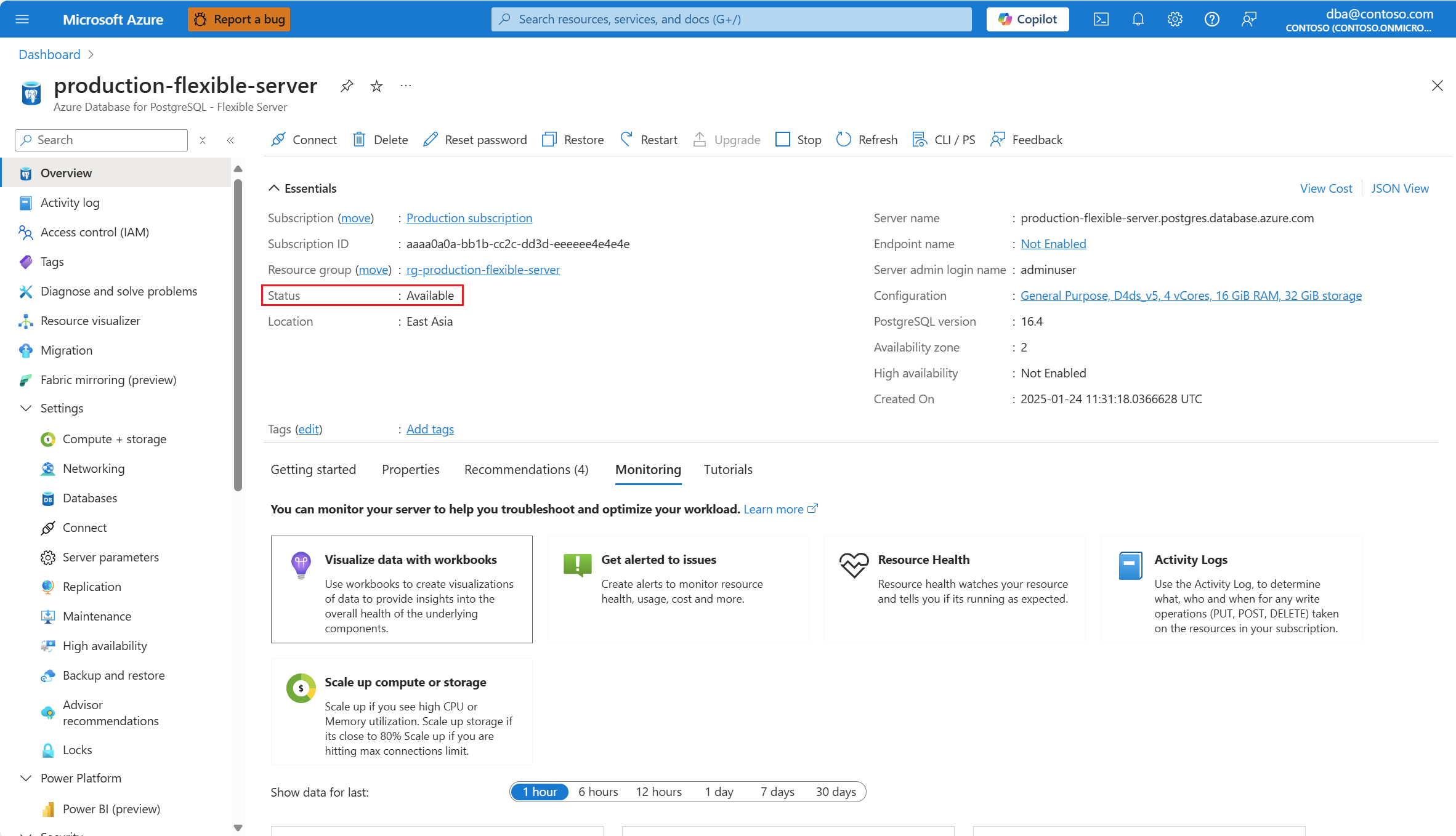
In the resource menu, select Overview.
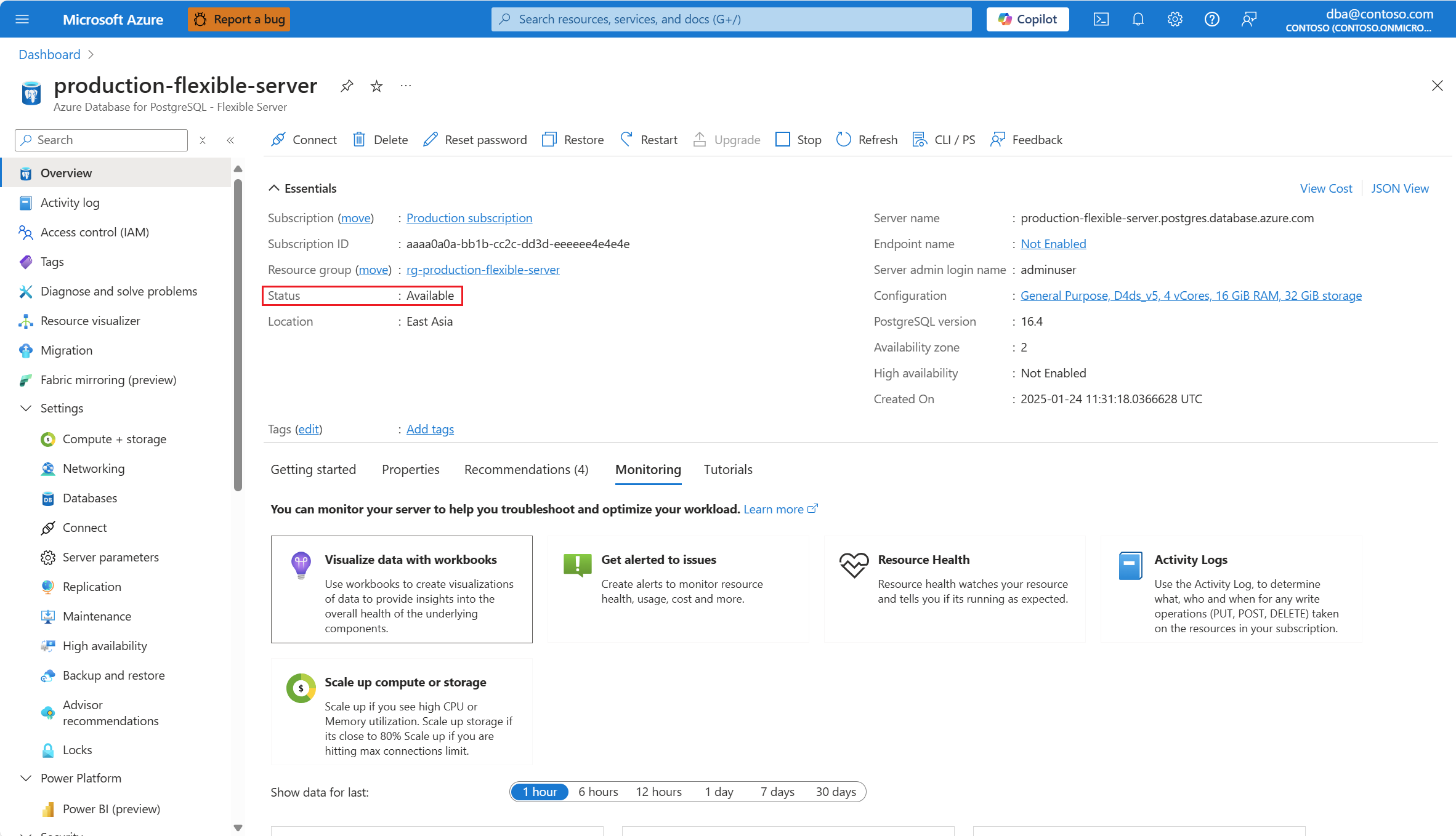
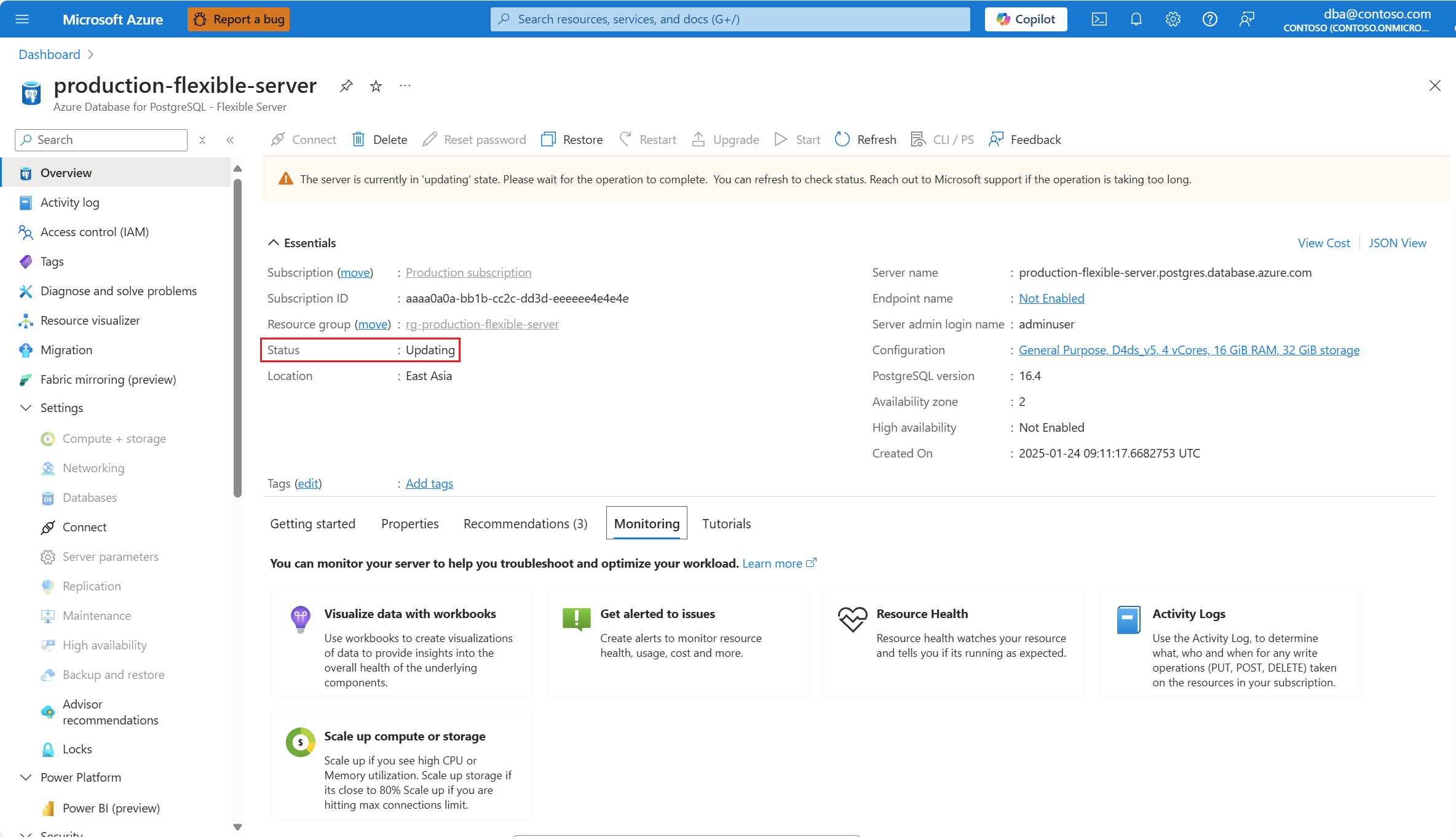
The status of the server must be Available, for the Networking menu option to be enabled.
If the status of the server isn't Available, the Networking option is disabled.
Note
Any attempt to configure the networking settings of a server whose status is other than available, would fail with an error.
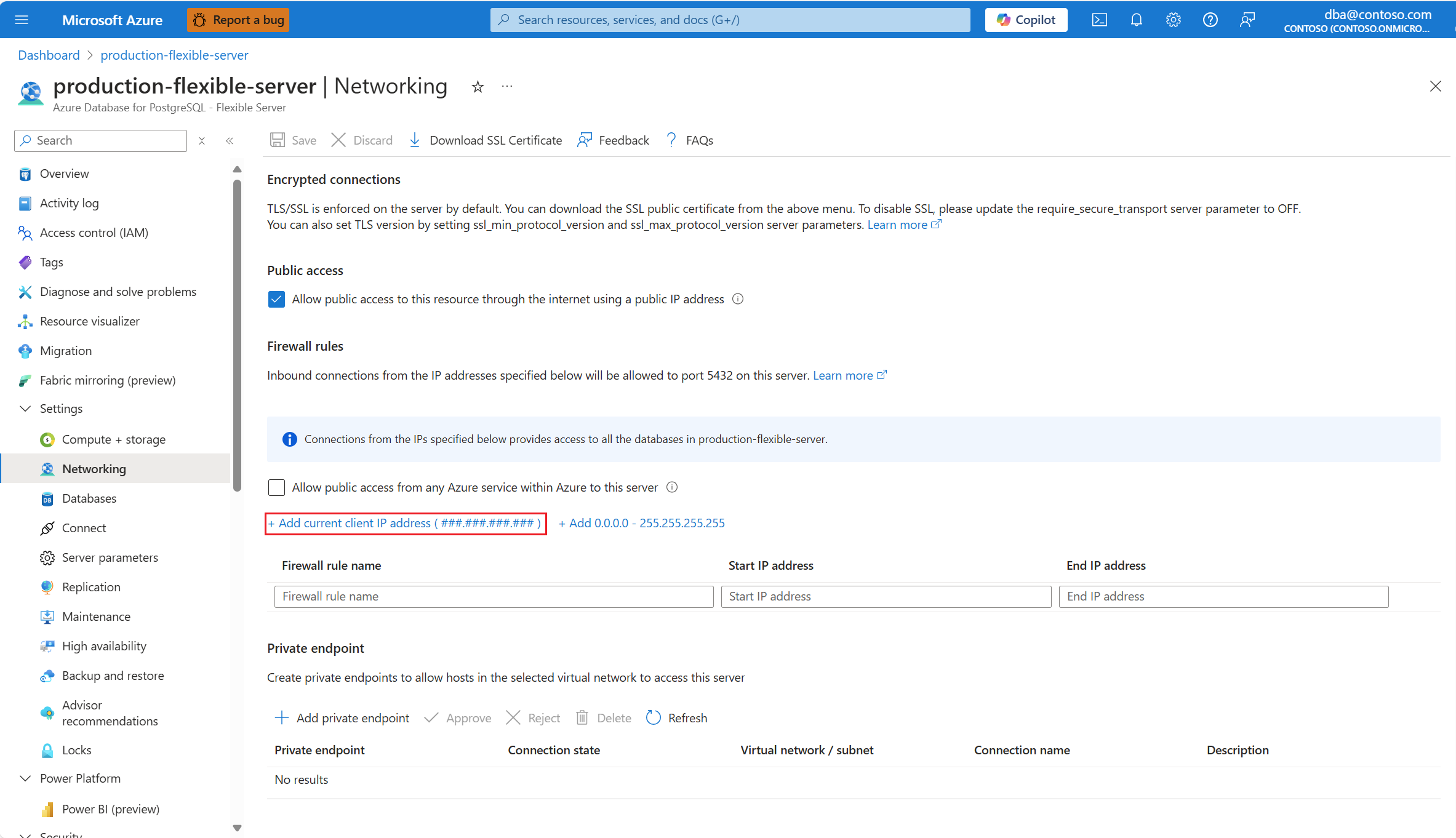
In the resource menu, select Networking.
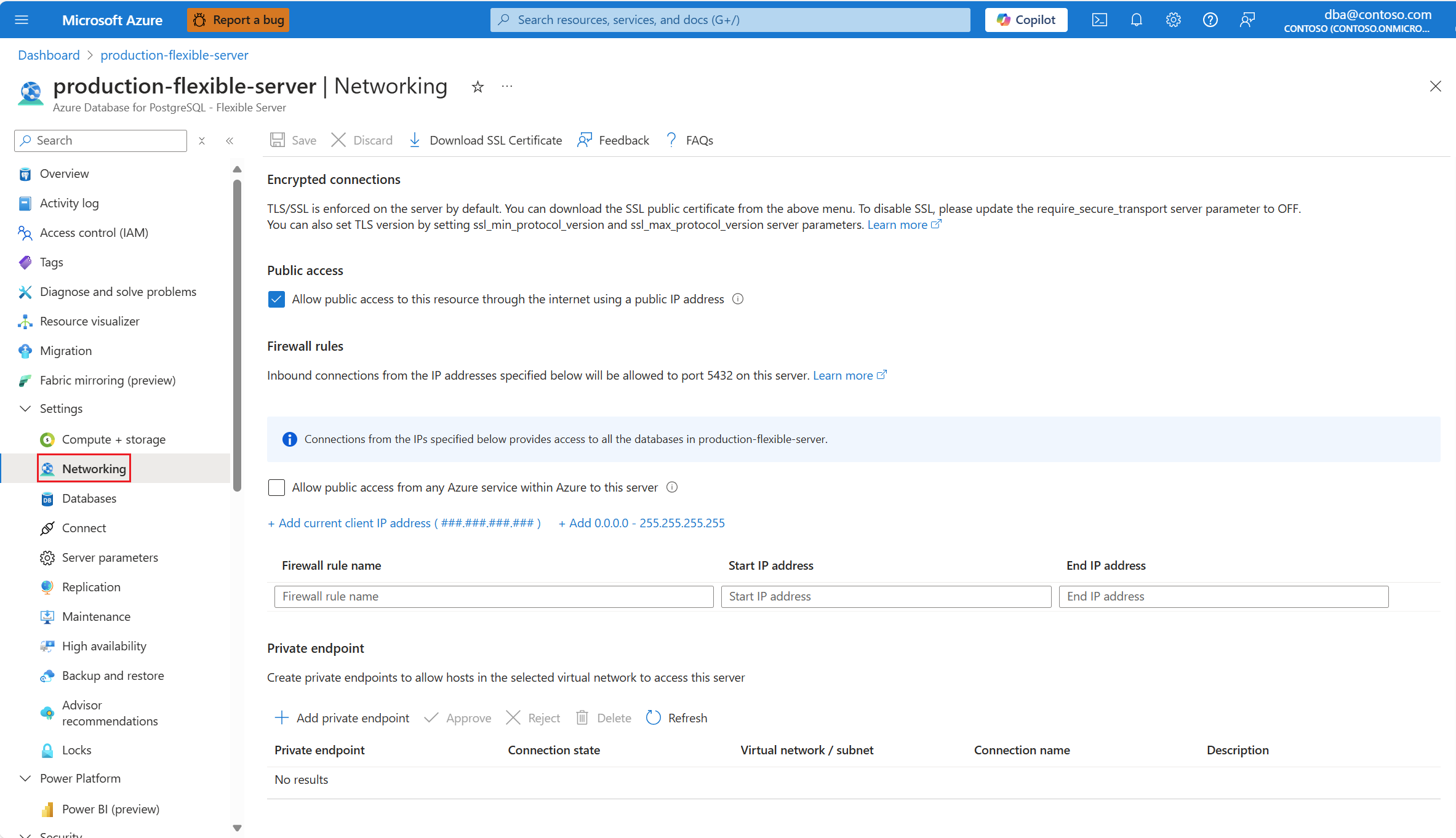
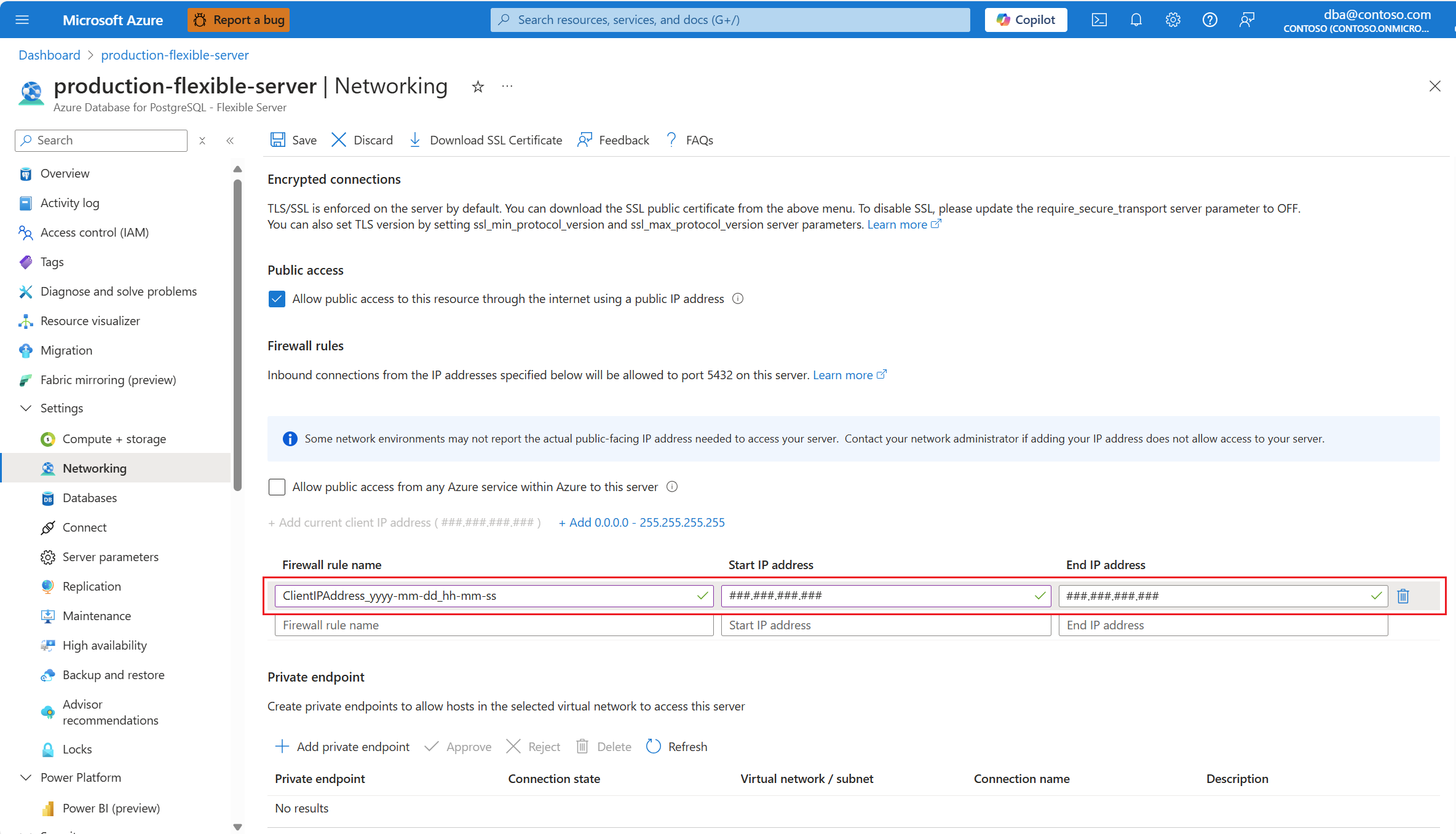
If you want to create a firewall rule to allow connections originating from the public IP address of the client machine that you're using to connect to navigate the portal, select Add current client IP address (###.###.###.###).
A new firewall rule is added to the grid. Its Firewall rule name is automatically generated, but you can change it to any valid name of your preference. Start IP address and End IP address are set to the public IP address from which you're connected to the Azure portal.
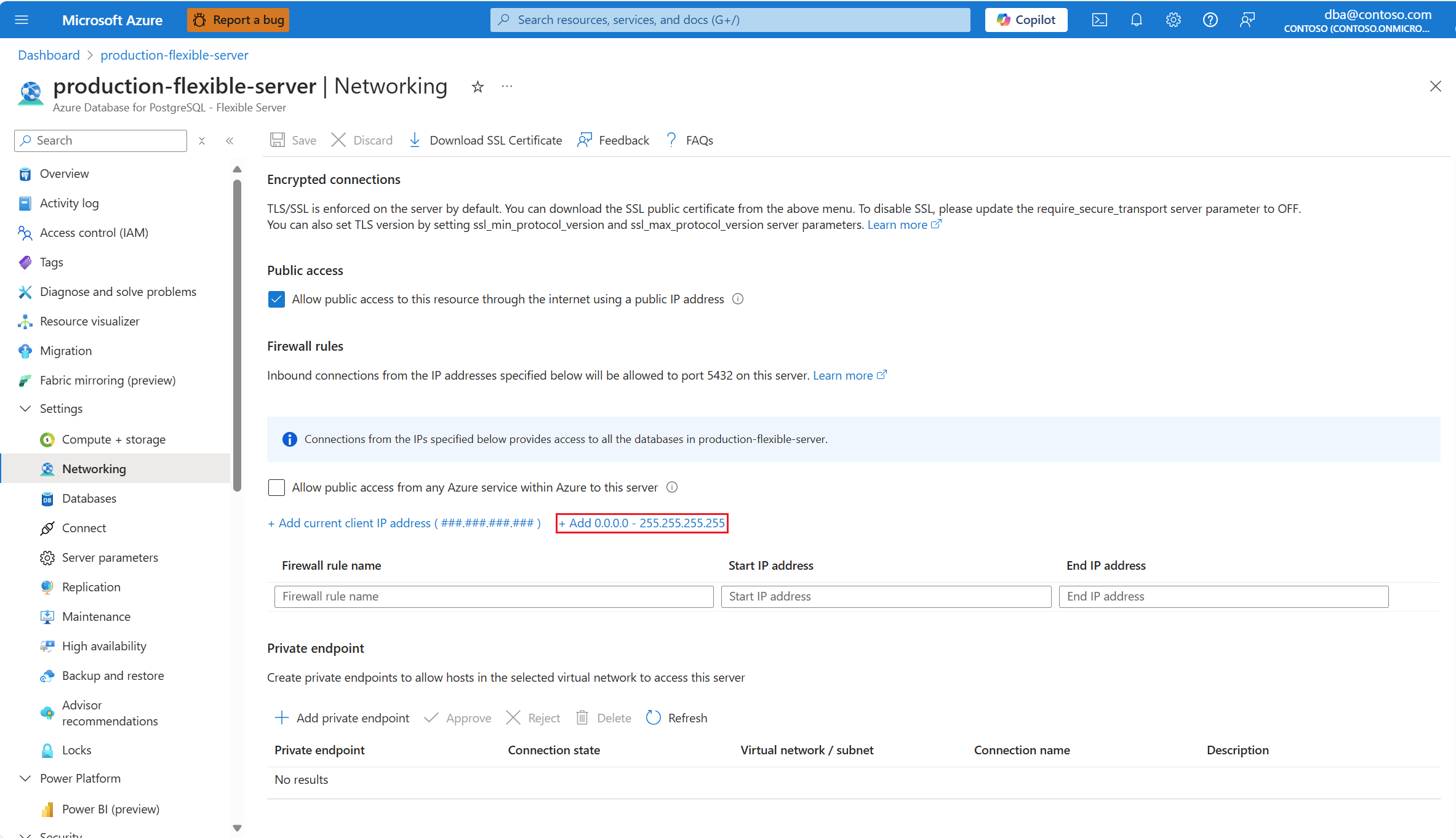
If you want to create a firewall rule to allow connections originating from any public IP address, select Add 0.0.0.0 / 255.255.255.255.
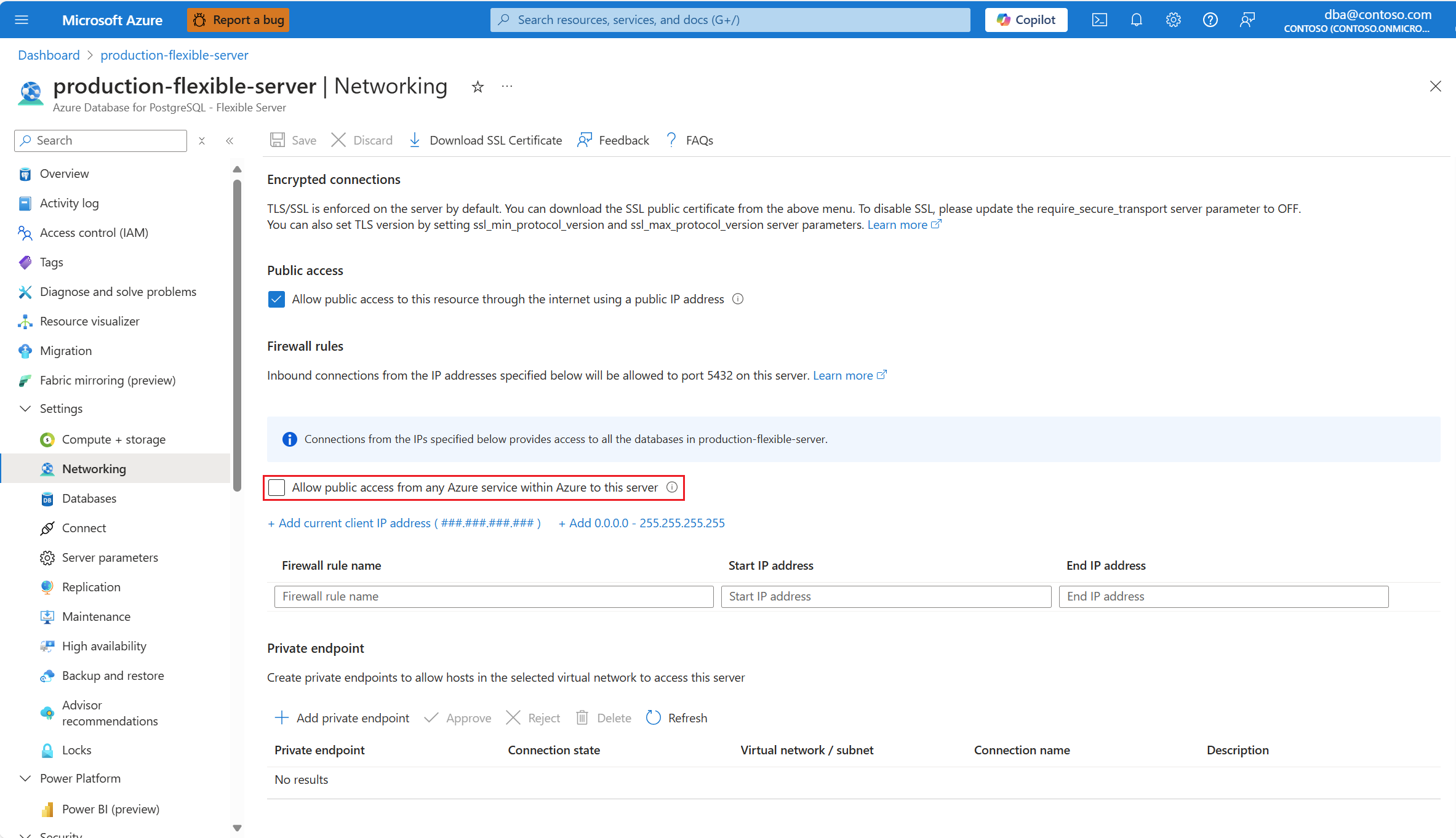
If you want to create a firewall rule to allow connections originating from any IP address allocated to any Azure service or asset, select Allow public access from any Azure service within Azure to this server.
Important
Allow public access from any Azure service within Azure to this server creates a firewall rule whose start and end IP addresses are set to 0.0.0.0. The presence of such rule configures the firewall to allow connections from IP addresses allocated to any Azure service or asset, including connections from the subscriptions of other customers.