Configurer SAM-R pour activer la détection de chemin de mouvement latéral dans Microsoft Defender pour Identity
Microsoft Defender pour Identity mappage pour les chemins de mouvement latéral potentiels s’appuie sur des requêtes qui identifient les administrateurs locaux sur des machines spécifiques. Ces requêtes sont effectuées avec le protocole SAM-R, à l’aide du compte de service d’annuaire Defender pour Identity que vous avez configuré.
Remarque
Cette fonctionnalité peut potentiellement être exploitée par un adversaire pour obtenir le hachage Net-NTLM du compte DSA en raison d’une limitation Windows dans les appels SAM-R qui permet de passer de Kerberos à NTLM. Le nouveau capteur Defender pour Identity n’est pas affecté par ce problème, car il utilise différentes méthodes de détection.
Il est recommandé d’utiliser un compte DSA à faibles privilèges. Vous pouvez également contacter le support technique pour ouvrir un cas et demander de désactiver complètement la fonctionnalité de collecte de données chemins de mouvement latéral . Notez que cela réduit les données disponibles pour la fonctionnalité de chemin d’attaque dans Gestion des expositions.
Cet article décrit les modifications de configuration requises pour permettre au compte des services d’annuaire (DSA) Defender pour Identity d’effectuer les requêtes SAM-R.
Conseil
Bien que cette procédure soit facultative, nous vous recommandons de configurer un compte de service d’annuaire et de configurer SAM-R pour la détection de chemin de mouvement latéral afin de sécuriser entièrement votre environnement avec Defender pour Identity.
Configurer les autorisations sam-R requises
Pour vous assurer que les clients et serveurs Windows autorisent votre compte de services d’annuaire (DSA) Defender pour Identity à effectuer des requêtes SAM-R, vous devez modifier les stratégie de groupe et ajouter le DSA, en plus des comptes configurés répertoriés dans la stratégie d’accès réseau. Veillez à appliquer des stratégies de groupe à tous les ordinateurs à l’exception des contrôleurs de domaine.
Importante
Effectuez d’abord cette procédure en mode audit , en vérifiant la compatibilité de la configuration proposée avant d’apporter les modifications à votre environnement de production.
Le test en mode audit est essentiel pour garantir que votre environnement reste sécurisé et que les modifications apportées n’auront pas d’impact sur la compatibilité de votre application. Vous pouvez observer une augmentation du trafic SAM-R généré par les capteurs Defender pour Identity.
Pour configurer les autorisations requises :
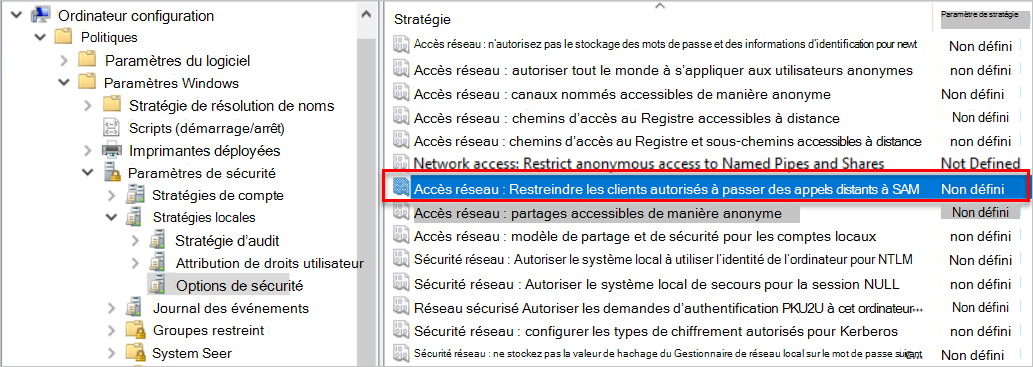
Recherchez la stratégie. Dans votre Configuration > ordinateur Paramètres Windows Paramètres > de sécurité Stratégies > locales > Options de sécurité, sélectionnez la stratégie Accès réseau - Restreindre les clients autorisés à effectuer des appels distants à SAM . Par exemple :
Ajoutez le DSA à la liste des comptes approuvés capables d’effectuer cette action, ainsi que tout autre compte que vous avez découvert pendant le mode audit.
Pour plus d’informations, consultez Accès réseau : Restreindre les clients autorisés à effectuer des appels distants à SAM.
Vérifiez que le DSA est autorisé à accéder aux ordinateurs à partir du réseau (facultatif)
Remarque
Cette procédure n’est requise que si vous avez déjà configuré le paramètre Accéder à cet ordinateur à partir du réseau , car le paramètre Accéder à cet ordinateur à partir du réseau n’est pas configuré par défaut
Pour ajouter le DSA à la liste des comptes autorisés :
Accédez à la stratégie et accédez à Configuration ordinateur ->Stratégies ->Paramètres Windows ->Stratégies locales ->Attribution de droits utilisateur, puis sélectionnez le paramètre Accéder à cet ordinateur à partir du réseau . Par exemple :
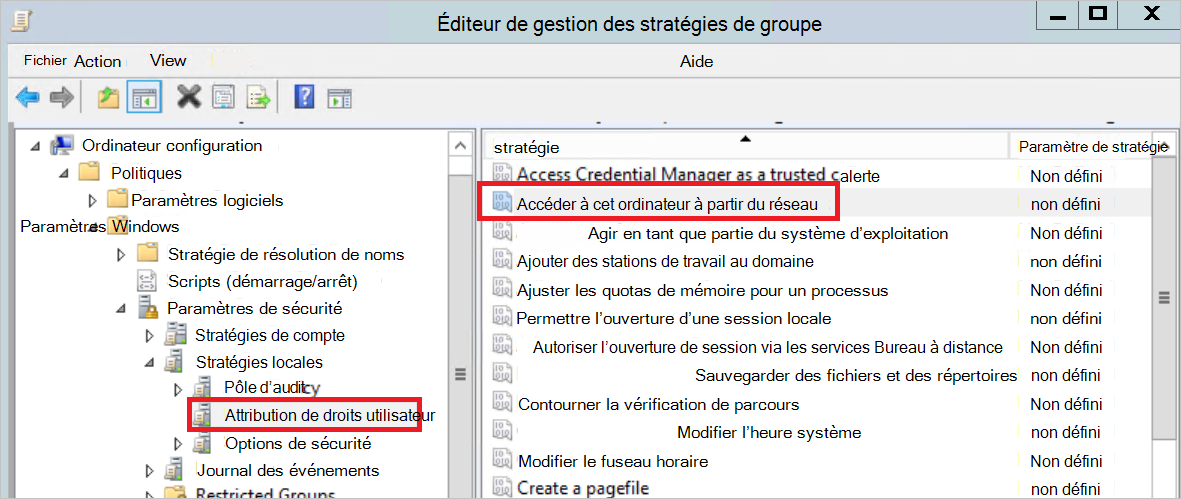
Ajoutez le compte de service d’annuaire Defender pour Identity à la liste des comptes approuvés.
Importante
Lors de la configuration des attributions de droits utilisateur dans des stratégies de groupe, il est important de noter que le paramètre remplace le paramètre précédent au lieu de l’ajouter. Par conséquent, veillez à inclure tous les comptes souhaités dans la stratégie de groupe effective. Par défaut, les stations de travail et les serveurs incluent les comptes suivants : Administrateurs, Opérateurs de sauvegarde, Utilisateurs et Tout le monde.
Microsoft Security Compliance Toolkit recommande de remplacer la valeur par défaut Tout le monde par utilisateurs authentifiés pour empêcher les connexions anonymes d’effectuer des connexions réseau. Passez en revue vos paramètres de stratégie locale avant de gérer le paramètre Accéder à cet ordinateur à partir du réseau à partir d’un objet de stratégie de groupe, et envisagez d’inclure des utilisateurs authentifiés dans l’objet de stratégie de groupe si nécessaire.
Configurer un profil d’appareil pour Microsoft Entra appareils joints hybrides uniquement
Cette procédure explique comment utiliser le centre d’administration Microsoft Intune pour configurer les stratégies dans un profil d’appareil si vous utilisez Microsoft Entra appareils joints hybrides.
Dans le centre d’administration Microsoft Intune, créez un profil d’appareil, en définissant les valeurs suivantes :
- Plateforme : Windows 10 ou version ultérieure
- Type de profil : Catalogue de paramètres
Entrez un nom et une description explicites pour votre stratégie.
Ajoutez des paramètres pour définir une stratégie NetworkAccess_RestrictClientsAllowedToMakeRemoteCallsToSAM :
Dans le sélecteur Paramètres, recherchez Accès réseau Restreindre les clients autorisés à effectuer des appels distants à SAM.
Sélectionnez pour parcourir la catégorie Stratégies locales Options de sécurité , puis sélectionnez le paramètre Accès réseau Restreindre les clients autorisés à effectuer des appels distants à SAM .
Entrez le descripteur de sécurité (SDDL) :
O:BAG:BAD:(A;;RC;;;BA)(A;;RC;;;%SID%), en%SID%remplaçant par le SID du compte du service d’annuaire Defender pour Identity.Veillez à inclure le groupe Administrateurs intégré :
O:BAG:BAD:(A;;RC;;;BA)(A;;RC;;;S-1-5-32-544)
Ajoutez des paramètres pour définir une stratégie AccessFromNetwork :
Dans le sélecteur Paramètres, recherchez Accès à partir du réseau.
Sélectionnez cette option pour parcourir la catégorie Droits de l’utilisateur , puis sélectionnez le paramètre Accès à partir du réseau .
Sélectionnez pour importer les paramètres, puis accédez à et sélectionnez un fichier CSV qui contient une liste d’utilisateurs et de groupes, y compris des SID ou des noms.
Veillez à inclure le groupe Administrateurs intégré (S-1-5-32-544) et le SID du compte du service d’annuaire Defender pour Identity.
Continuez l’Assistant pour sélectionner les balises d’étendue et les affectations, puis sélectionnez Créer pour créer votre profil.
Pour plus d’informations, consultez Appliquer des fonctionnalités et des paramètres sur vos appareils à l’aide de profils d’appareil dans Microsoft Intune.