Get started with insider risk management
Important
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider risk management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Use insider risk management policies to identify risky activities and management tools to act on risk alerts in your organization. Complete the following steps to set up prerequisites and configure an insider risk management policy.
Important
The insider risk management solution provides a tenant level option to help customers facilitate internal governance at the user level. Tenant level administrators can set up permissions to provide access to this solution for members of your organization and set up data connectors in the Microsoft Purview portal or the Microsoft Purview compliance portal to import relevant data to support user level identification of potentially risky activity. Customers acknowledge insights related to the individual user's behavior, character, or performance materially related to employment can be calculated by the administrator and made available to others in the organization. In addition, customers acknowledge that they must conduct their own full investigation related to the individual user's behavior, character, or performance materially related to employment, and not just rely on insights from the insider risk management service. Customers are solely responsible for using the insider risk management service, and any associated feature or service in compliance with all applicable laws, including laws relating to individual user identification and any remediation actions.
For more information about how insider risk policies can help you manage risk in your organization, see Learn about insider risk management.
Tip
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview trials hub. Learn details about signing up and trial terms.
Subscriptions and licensing
Before getting started with insider risk management, you should confirm your Microsoft 365 subscription and any add-ons. To access and use insider risk management, administrators need to verify their organization has a supported subscription and the appropriate licenses are assigned to users. For more information about subscriptions and licensing, see the subscription requirements for insider risk management.
Important
Insider risk management is currently available in tenants hosted in geographical regions and countries supported by Azure service dependencies. To verify that insider risk management is supported for your organization, see Azure dependency availability by country/region.
If you don't have an existing Microsoft 365 Enterprise E5 plan and want to try insider risk management, you can add Microsoft 365 to your existing subscription or sign up for a trial of Microsoft 365 Enterprise E5.
Pay-as-you-go billing
Some indicators included in insider risk management are only available if you enable the pay-as-you-go billing model for your organization. For more information see Configure policy indicators in insider risk management.
Recommended actions
Recommended actions can help your organization quickly get with insider risk management. Recommended actions, which are included on the Overview page, help guide you through the steps to configure and deploy policies.
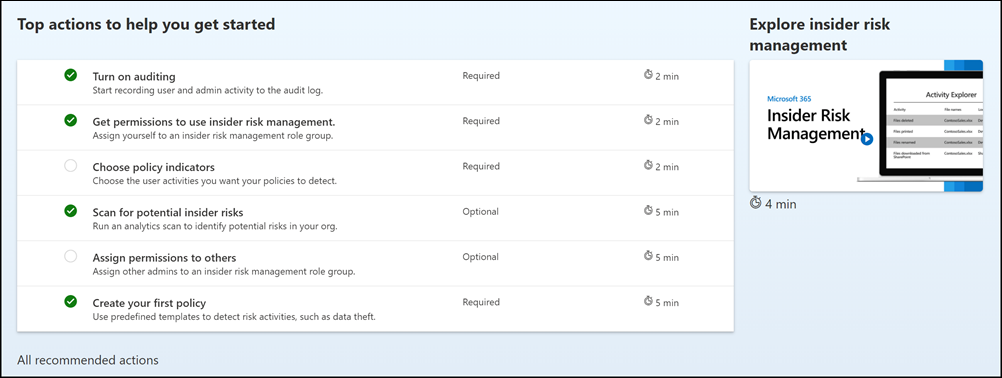
The following recommendations are available to help you get started with or maximize your insider risk management configuration:
- Turn on auditing: When turned on, user and admin activity in your organization is recorded to the Microsoft 365 audit log. Insider risk policies and analytics scans use this log to detect risk activities.
- Get permissions to use insider risk management: The level of access you have to insider risk management features depends on which role group you were assigned. To access and configure recommended actions, users must be assigned to the Insider Risk Management or Insider Risk Management Admins role groups.
- Choose policy indicators: Indicators are essentially the risk management activities you want to detect and investigate. You can choose indicators to detect activity across several Microsoft 365 locations and services.
- Scan for potential insider risks: Run an analytics scan to discover potential insider risks occurring in your org. After evaluating results, review recommended policies to set up.
- Assign permissions to others: If there are additional team members who are responsible for managing insider risk features, you need to assign them to the appropriate role groups.
- Create your first policy: To receive alerts on potentially risky activities, you must set up policies based on predefined templates that define the user activities you want to detect and investigate.
Each recommended action included in this experience has four attributes:
- Action: Name and description of the recommended action.
- Status: Status of the recommended action. Values are Not started, In progress, Saved for later, or Completed.
- Required or optional: Whether the recommended action is required or optional for insider risk management features to function as expected.
- Estimated time to complete: Estimated time to complete the recommended action in minutes.
Select a recommendation from the list to get started with configuring insider risk management. Each recommended action guides you through the required action for the recommendation, including any requirements, what to expect, and the impact of configuring the feature in your organization. Each recommended action is automatically marked as complete when configured or you'll need to manually select the action as complete when configured.
Step 1 (required): Enable permissions for insider risk management
Important
After configuring your role groups, it may take up to 30 minutes for the role group permissions to apply to assigned users across your organization.
There are six role groups used to configure insider risk management features. To make Insider risk management available as a menu option in Microsoft Purview and to continue with these configuration steps, you must be assigned to one of the following roles or role groups:
- Microsoft Entra ID Global Administrator role
- Microsoft Entra ID Compliance Administrator role
- Microsoft Purview Organization Management role group
- Microsoft Purview Compliance Administrator role group
- Insider Risk Management role group
- Insider Risk Management Admins role group
Depending on how you wish to manage insider risk management policies and alerts, you'll need to assign users to specific role groups to manage different sets of insider risk management features. You can assign users with different compliance responsibilities to specific role groups to manage different areas of insider risk management features. Or you may decide to assign all user accounts for designated administrators, analysts, investigators, and viewers to the Insider Risk Management role group. Use a single role group or multiple role groups to best fit your compliance management requirements.
Choose from these role group options and solution actions when working with insider risk management:
| Actions | Insider Risk Management | Insider Risk Management Admins | Insider Risk Management Analysts | Insider Risk Management Investigators | Insider Risk Management Auditors | Insider Risk Management Approvers |
|---|---|---|---|---|---|---|
| Configure policies and settings | Yes | Yes | No | No | No | No |
| Access analytics insights | Yes | Yes | Yes | No | No | No |
| Access & investigate alerts | Yes | No | Yes | Yes | No | No |
| Access & investigate cases | Yes | No | Yes | Yes | No | No |
| Access & view the Content Explorer | Yes | No | No | Yes | No | No |
| Configure notice templates | Yes | No | Yes | Yes | No | No |
| View & export audit logs | Yes | No | No | No | Yes | No |
| Access & view forensic evidence captures | Yes | No | No | Yes | No | No |
| Create forensic evidence capturing request | Yes | Yes | No | No | No | No |
| Approve forensic evidence capturing requests | Yes | No | No | No | No | Yes |
| Configure Adaptive Protection | Yes | Yes | No | No | No | No |
| View Adaptive Protection users tab | Yes | No | Yes | Yes | No | No |
| View alert and case reports | Yes | Yes | Yes | Yes | No | No |
Important
Make sure you always have at least one user in the built-in Insider Risk Management or Insider Risk Management Admins role groups (depending on the option you choose) so that your insider risk management configuration doesn't get into a 'zero administrator' scenario if specific users leave your organization.
Members of the following roles can assign users to insider risk management role groups and have the same solution permissions included with the Insider Risk Management Admins role group:
- Microsoft Entra ID Global Administrator
- Microsoft Entra ID Compliance Administrator
- Microsoft Purview Organization Management
- Microsoft Purview Compliance Administrator
Important
Microsoft recommends that you use roles with the fewest permissions. Minimizing the number of users with the Global Administrator role helps improve security for your organization. Learn more about Microsoft Purview roles and permissions.
Add users to the Insider Risk Management role group
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Select Settings in the upper-right corner of the page, select Roles and groups, and then select Roles groups in the left navigation pane.
- Select the Insider Risk Management role group, and then select Edit.
- Select Choose users, and then select the checkboxes for all the users you want to add to the role group.
- Choose Select, and then select Next.
- Select Save to add the users to the role group, and then select Done.
Consider administrative units if you want to scope user permissions to a region or department
You can use administrative units in insider risk management (preview) to scope user permissions to a particular geography or department. For example, a global company that has subsidiaries throughout the world might want to create an admin unit that provides a German scope for investigators so that they only see user activity for German users.
To use admin units in insider risk management, you must first create the admin units (if they haven't already been created), and then assign the admin units to members of role groups. After you assign admin units to members of role groups, those members become restricted administrators and have limited access to insider risk management settings, policies, and user data in the organization. Members who aren't assigned administrative units are unrestricted administrators and have access to all settings, policies, and user data.
Important
Restricted administrators can't access alerts for the users assigned to them through security groups or distribution groups added in administrative units. Such user alerts are visible only to unrestricted administrators. Microsoft recommends adding users directly to administrative units to ensure their alerts are also visible to restricted administrators with administrative units assigned.
Effect of admin unit scoping on insider risk management roles
The following table shows how admin units, when enforced, affect each combination of insider risk management task/role.
Note
Scoped, in the following table, means that the admin actions for that role are limited by their assigned admin unit.
| Task | Scoped Insider Risk Management | Scoped Insider Risk Management Admin | Scoped Insider Risk Management Analysts | Scoped Insider Risk Management Investigators | Scoped Insider Risk Management Approvers |
|---|---|---|---|---|---|
| Configure global settings | Unrestricted | Unrestricted | Never allowed | Never allowed | Never allowed |
| Configure policies | Scoped | Scoped | Never allowed | Never allowed | Never allowed |
| Start scoring activity for users | Scoped | Scoped | Scoped | Scoped | Never allowed |
| Access analytics insights | Not allowed, if scoped | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed |
| Access and investigate alerts | Scoped | Never allowed | Scoped | Scoped | Never allowed |
| Investigate user activity | Scoped | Never allowed | Never allowed | Scoped | Never allowed |
| Access and investigate cases | Scoped | Never allowed | Scoped | Scoped | Never allowed |
| Access and view the Content explorer | Unrestricted | Never allowed | Never allowed | Unrestricted | Never allowed |
| Configure notice templates | Unrestricted | Never allowed | Unrestricted | Unrestricted | Never allowed |
| Access and view forensic evidence captures | Not allowed, if scoped | Never allowed | Never allowed | Not allowed, if scoped | Never allowed |
| Create forensic evidence capturing request | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| Approve forensic evidence capturing requests | Not allowed, if scoped | Never allowed | Never allowed | Never allowed | Not allowed, if scoped |
| Configure Adaptive Protection | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| View Adaptive Protection users tab | Not allowed, if scoped | Never allowed | Not allowed, if scoped | Not allowed, if scoped | Never allowed |
| View device health report | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| Create quick policies | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| Configure priority-user-specific policies | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| Configure priority user groups | Not allowed, if scoped | Not allowed, if scoped | Never allowed | Never allowed | Never allowed |
| Assign or reassign alerts | Not allowed, if scoped | Never allowed | Not allowed, if scoped | Not allowed, if scoped | Never allowed |
| Assign or reassign cases | Not allowed, if scoped | Never allowed | Not allowed, if scoped | Not allowed, if scoped | Never allowed |
| View alert and case reports | Scoped | Scoped | Scoped | Scoped | Scoped |
Note
You can use adaptive scopes (preview for insider risk management) together with admin units. If role groups are scoped by one or more admin units for your organization, the adaptive scopes that you can select when you create or edit a policy are limited by the admin units.
Step 2 (required): Enable the Microsoft 365 audit log
Insider risk management uses Microsoft 365 audit logs for user insights and risk management activities identified in policies and analytics insights. The Microsoft 365 audit logs are a summary of all activities within your organization and insider risk management policies may use these activities for generating policy insights.
Auditing is enabled for Microsoft 365 organizations by default. Some organizations may have disabled auditing for specific reasons. If auditing is disabled for your organization, it might be because another administrator has turned it off. We recommend confirming that it's OK to turn auditing back on when completing this step.
For step-by-step instructions to turn on auditing, see Turn audit log search on or off. After you turn on auditing, a message is displayed that says the audit log is being prepared and that you can run a search in a couple of hours after the preparation is complete. You only have to do this action once. For more information about the using the Microsoft 365 audit log, see Search the audit log.
Step 3 (optional): Enable and view insider risk analytics insights
If you enable insider risk management analytics, you can:
- Scan for potential insider risks before creating policies. You can conduct an evaluation of potential insider risks in your organization without configuring any insider risk policies. This evaluation can help your organization identify potential areas of higher user risk and help determine the type and scope of insider risk management policies you might want to configure. This evaluation may also help you determine needs for additional licensing or future optimization of existing policies. Analytics scan results may take up to 48 hours before insights are available as reports for review. To learn more about analytics insights, see Insider risk management settings: Analytics and check out the Insider Risk Management Analytics video to help understand how analytics can help accelerate the identification of potential insider risks and help you to quickly take action.
- Receive real-time recommendations for indicator threshold settings. Manually tuning policies to reduce "noise" can be a very time-consuming experience that requires you to do a lot of trial and error to determine the desired configuration for your policies. If analytics is turned on, insider risk management can provide real-time recommendations for indicator thresholds. You can also manually adjust the provided recommendations and see in real time how many users are brought into scope of the policy based on the changes you make. Learn more about real-time indicator threshold recommendations
Note
To enable insider risk analytics, you must be a member of the Insider Risk Management, Insider Risk Management Admins, or Microsoft 365 Global admin role group.
Important
Microsoft recommends that you use roles with the fewest permissions. Minimizing the number of users with the Global Administrator role helps improve security for your organization. Learn more about Microsoft Purview roles and permissions.
Enable insider risk analytics
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Insider Risk Management solution.
- On the Overview tab, on the Scan for insider risks in your organization card, select Run scan. This action turns on analytics scanning for your organization. You can also turn on scanning by going to Insider risk settings > Analytics and enabling Scan your tenant's user activity to identify potential insider risks.
- On the Analytics details pane, select Run scan to start the scan for your organization. Analytics scan results may take up to 48 hours before insights are available as reports for review.
After reviewing the analytics insights, choose the insider risk policies and configure the associated prerequisites that best meet your organization's insider risk mitigation strategy.
Step 4 (recommended): Configure prerequisites for policies
Most insider risk management policies have prerequisites that must be configured for policy indicators to generate relevant activity alerts. Configure the appropriate prerequisites depending on the policies you plan to configure for your organization.
Connect to cloud apps in Microsoft Defender
Insider risk management includes the following cloud indicators (preview):
- Cloud storage indicators, including Google Drive, Box, and Dropbox
- Cloud service indicators, including Amazon S3 and Azure (Storage and SQL Server)
Cloud storage indicators
Use cloud storage indicators to detect for the following activities in Google Drive, Box, and Dropbox:
- Discovery: Techniques used to figure out the environment
- Collection: Techniques used to gather data of interest
- Exfiltration: Techniques used to steal data, such as sensitive documents
- Deletion (impact): Techniques used to disrupt the availability or compromise the integrity of a system
Cloud service indicators
Use cloud service indicators to detect for the following activities in Amazon S3 and Azure:
- Defense evasion: Techniques used to avoid detection of risky activities by disabling trace logs or by updating or deleting SQL Server firewall rules
- Exfiltration: Techniques used to steal data, such as sensitive documents
- Deletion (impact): Techniques used to disrupt the availability or compromise the integrity of a system
- Privilege escalation: Techniques used to gain higher-level permissions to systems and data
Prerequisites for accessing cloud indicators
To select from cloud indicators in insider risk management settings and policies, you must first connect to the relevant cloud app(s) in Microsoft Defender, if you haven't already done so.
After connecting to the app(s), the indicators are available on the Policy indicators settings page and from individual policies.
Configure Insider Risk Indicator (preview) connector
You can extend insider risk management by importing detections for non-Microsoft (third-party) workloads. For example, you might want to extend your detections to include Salesforce and Dropbox activities and use them alongside the built-in detections provided by the insider risk management solution, which is focused on Microsoft services like SharePoint Online and Exchange Online.
To bring your own detections to the insider risk management solution, you import preprocessed, aggregated detections from security information and event management (SIEM) solutions such as Microsoft Sentinel or Splunk. You do this by importing a sample file into the Insider Risk Indicators connector workflow. The connector workflow analyzes the sample file and configures the required schema.
Note
Currently, you cannot import "raw" detection signals into insider risk management. You can only import pre-processed aggregations as a file.
You can use a custom indicator as:
- A trigger used to bring a user into the scope of a policy.
- A policy indicator used to score the user for risk.
See the Insider Risk Indicators connector article for step-by-step guidance to configure the Insider Risk Indicators connector for your organization. After you've configured the connector, return to these configuration steps.
Configure Microsoft 365 HR connector
Insider risk management supports importing user and log data imported from 3rd-party risk management and human resources platforms. The Microsoft 365 Human Resources (HR) data connector allows you to pull in human resources data from CSV files, including user termination dates, last employment dates, performance improvement plan notifications, performance review actions, and job level change status. This data helps drive alert indicators in insider risk management policies and is an important part of configuring full risk management coverage in your organization. If you configure more than one HR connector for your organization, insider risk management automatically pulls indicators from all HR connectors.
The Microsoft 365 HR connector is required when using the following policy templates:
- Data leaks by risky users
- Departing user data theft
- Patient data misuse
- Security policy violations by departing users
- Security policy violations by risky users
See the Set up a connector to import HR data article for step-by-step guidance to configure the Microsoft 365 HR connector for your organization. After you've configured the HR connector, return to these configuration steps.
Configure a Microsoft Healthcare connector
Insider risk management supports importing user and log data imported from 3rd-party on existing electronic medical record (EMR) systems. The Microsoft Healthcare connector allows you to pull in activity data from your EMR system with CSV files, including improper patient record access, suspicious volume activities, and editing and exporting activities. This data helps drive alert indicators in insider risk management policies and is an important part of configuring full risk management coverage in your organization.
If you configure more than one Healthcare connector for your organization, insider risk management automatically supports event and activities signals from all Healthcare connectors. The Microsoft 365 Healthcare is required when using the following policy templates:
- Patient data misuse
See the Set up a connector to import healthcare data article for step-by-step guidance to configure a healthcare-specific connector for your organization. After you've configured a connector, return to these configuration steps.
Configure Data Loss Prevention (DLP) policies
Insider risk management supports using DLP policies to help identify the intentional or accidental exposure of sensitive information to unwanted parties for High severity level DLP alerts. When configuring an insider risk management policy with any of the Data leaks templates, you can assign a specific DLP policy to the policy for these types of alerts.
Tip
You can also use Adaptive Protection in insider risk management to dynamically apply DLP protection controls to high-risk users while maintaining productivity for lower-risk users. Learn more about Adaptive Protection
Data loss policies help identify users to activate risk scoring in insider risk management for high severity DLP alerts for sensitive information and are an important part of configuring full risk management coverage in your organization. For more information about insider risk management and DLP policy integration and planning considerations, see Insider risk management policies.
Important
Make sure you've completed the following:
- You understand and properly configure the in-scope users in both the DLP and insider risk management policies to produce the policy coverage you expect.
- The Incident reports setting in the DLP policy for insider risk management used with these templates are configured for High severity level alerts. Insider risk management alerts won't be generated from DLP policies with the Incident reports field set at Low or Medium.
A DLP policy is optional when using the following policy templates:
- Data leaks
- Data leaks by priority users
See the Create and Deploy data loss prevention policies article for step-by-step guidance to configure DLP policies for your organization. After you've configured a DLP policy, return to these configuration steps.
Note
Endpoint DLP now supports virtualized environments, which means that the insider risk management solution supports virtualized environments through endpoint DLP. Learn more about support for virtualized environments in endpoint DLP.
Configure sharing of insider risk levels with Microsoft Defender and DLP alerts
You can share insider risk levels from insider risk management (preview) to bring unique user context to Microsoft Defender and DLP alerts. Insider risk management analyzes user activities over a period of 90-120 days and looks for anomalous behavior over that period of time. Adding this data to Microsoft Defender and DLP alerts enhances the data available in those solutions to help analysts prioritize alerts. Learn more about sharing user risk severity levels with Microsoft Defender and DLP alerts.
Sharing insider risk management user risk severity levels also enhances the Microsoft Security Copilot. For example, in Security Copilot, you might want to start by asking Copilot to summarize a DLP alert, and then ask Copilot to show the insider risk level associated with the user flagged in the alert. Or you might want to ask why the user is considered a high-risk user. The user risk information in this case comes from insider risk management. Security Copilot seamlessly integrates insider risk management with DLP to assist with investigations. Learn more about using the standalone version of Copilot for combined DLP/insider risk management investigations.
Configure priority user groups
Insider risk management includes support for assigning priority user groups to policies to help identify unique risk activities for user with critical positions, high levels of data and network access, or a past history of risk behavior. Creating a priority user group and assigning users to the group help scope policies to the unique circumstances presented by these users.
You can create a priority user group and assign users to the group to help you scope policies specific to the unique circumstances presented by these identified users. To enable the priority user groups risk score booster, go to the Insider risk management settings page, then select Policy indicators and Risk score boosters. These identified users are more likely to receive alerts, so analysts and investigators can review and prioritize these users' risk severity to help triage alerts in accordance with your organization's risk policies and standards.
A priority user group is required when using the following policy templates:
- Security policy violations by priority users
- Data leaks by priority users
See the Getting started with insider risk management settings article for step-by-step configuration guidance.
Configure Physical badging connector
Insider risk management supports importing user and log data from physical control and access platforms. The Physical badging connector allows you to pull in access data from JSON files, including user IDs, access point IDs, access time and dates, and access status. This data helps drive alert indicators in insider risk management policies and is an important part of configuring full risk management coverage in your organization. If you configure more than one Physical badging connector for your organization, insider risk management automatically pulls indicators from all Physical badging connectors. Information from the Physical badging connector supplements other insider risk signals when using all insider risk policy templates.
Important
For insider risk management policies to use and correlate signal data related to departing and terminated users with event data from your physical control and access platforms, you must also configure the Microsoft 365 HR connector. If you enable the Physical badging connector without enabling the Microsoft 365 HR connector, insider risk management policies will only process events for unauthorized physical access for users in your organization.
See the Set up a connector to import physical badging data article for step-by-step guidance to configure the Physical badging connector for your organization. After you've configured the connector, return to these configuration steps.
Configure Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. To have better visibility of security violations in your organization, you can import and filter Defender for Endpoint alerts for activities used in policies created from insider risk management security violation policy templates.
If you create security violation policies, you need to have Microsoft Defender for Endpoint configured in your organization and enable Defender for Endpoint for insider risk management integration in the Defender Security Center to import security violation alerts. For more information about requirements, see the Minimum requirements for Microsoft Defender for Endpoint article.
See the Configure advanced features in Defender for Endpoint article for step-by-step guidance to configure Defender for Endpoint for insider risk management integration. After you've configured the Microsoft Defender for Endpoint, return to these configuration steps.
Configure forensic evidence
Having visual context is crucial for security teams during forensic investigations to get better insights into risky user activities that may lead to a security incident. With customizable event triggers and built-in user privacy protection controls, forensic evidence enables customizable capturing across devices to help your organization better mitigate, understand, and respond to potential data risks like unauthorized data exfiltration of sensitive data.
See the Get started with insider risk management forensic evidence article for step-by-step guidance to configure forensic evidence for your organization.
Configure optical character recognition
Microsoft Purview can scan for sensitive content in documents to help protect those documents from inappropriate exposure. When you enable optical character recognition (OCR) in Microsoft Purview, data classifiers, such as sensitive information types and trainable classifiers, can also detect characters in stand-alone images. After configuring OCR settings (preview), your existing insider risk policies are applied to both images and documents.
For the OCR preview, insider risk management supports scanning in the following locations: Windows endpoint devices, SharePoint Online, and Teams. Exchange Online and OneDrive aren't supported for the preview.
OCR settings don't apply to forensic evidence clips in insider risk management.
Learn more about setting up OCR scanning and pay-as-you-go billing.
Step 5 (required): Configure insider risk settings
Insider risk settings apply to all insider risk management policies, regardless of the template you choose when creating a policy. Settings are configured using Settings located at the top of insider risk management pages. These settings control privacy, indicators, global exclusions, detection groups, intelligent detections, and more. Learn more about settings to consider before you creating a policy.
Step 6 (required): Create an insider risk management policy
Insider risk management policies include assigned users and define which types of risk indicators are configured for alerts. Before potentially risky activities can trigger alerts, a policy must be configured. Use the policy workflow to create new insider risk management policies.
Note
To create a custom trigger or indicator for a non-Microsoft workload, see Custom indicators.
Create policy
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
Go to the Insider Risk Management solution.
Select Policies in the left navigation.
Select Create policy to open the policy workflow.
On the Policy template page, choose a policy category and then select the template for the new policy. These templates are made up of conditions and indicators that define the risk activities you want to detect and investigate. Review the template prerequisites, triggering events, and detected activities to confirm this policy template fits your needs.
Important
Some policy templates have prerequisites that must be configured for the policy to generate relevant alerts. If you haven't configured the applicable policy prerequisites, see Step 4.
Select Next to continue.
On the Name and description page, complete the following fields:
- Name (required): Enter a friendly name for the policy. This name can't be changed after the policy is created.
- Description (optional): Enter a description for the policy.
Select Next to continue.
If admin units have been created for your tenant, you'll see the Admin units page. Otherwise, you'll see the Users and groups page and can skip to the next step.
If you want to scope the policy to one or more admin units, select Add admin units, and then select the admin unit(s) that you want to apply to the policy.
Note
You can only see the admin units that are scoped to your role. If you're an unrestricted administrator, you can see all admin units for the tenant. To view a summary of the role groups and admin units that you're assigned to, select View my permissions.
Select Next to continue.
On the Users and groups page, select one of the following options:
Include all users and groups. Selecting this option causes insider risk management to look for triggering events for all users and groups in your organization to start assigning risk scores for the policy.
If your policy is scoped by one or more admin units, this option selects all users and groups within the administrative unit(s).
Note
To take advantage of real-time analytics (preview) for indicator threshold settings, you must scope your policy to Include all users and groups. Real-time analytics enables you to see estimates of the number of users that could potentially match a given set of policy conditions in real time. This helps you efficiently adjust the selection of indicators and thresholds of activity occurrence so you don’t have too few or too many policy alerts. Scoping your policy to Include all users and groups also provides better overall protection across your tenant. For more information on real-time analytics for indicator threshold settings, see Indicator level settings.
Include specific users and groups. Select this option to define which users or groups are included in the policy.
If your policy is scoped by one or more admin units, you can only choose users within the admin unit scope.
Note
Guest accounts aren't supported.
Adaptive scope. This option (preview for insider risk management) appears if you select the Include specific users and groups option. Select Add or edit adaptive scopes to apply an adaptive scope to the policy. The adaptive scope must be created before you create or edit the policy. If the policy is also scoped by one or more admin units, the adaptive scopes available to you are limited by the admin unit(s). Learn how adaptive scopes work together with admin units.
Add or edit priority user groups. This option will only appear if you chose the Data leaks by priority users template. Select this option, and then add or edit priority user groups.
Note
If the policy template is based on priority user groups, you can't select an admin unit to scope the policy. Priority user groups are not currently supported for use with admin units.
Select Next to continue.
If you selected Include all users and groups in the previous step, the Exclude users and groups (optional) (preview) page appears.
Note
At this time, you have to select Include all users and groups to exclude users and groups.
Use this page if you want to exclude certain users or groups from the policy scope. For example, you might want to create a policy that detects for potentially risky actions for people in the whole organization but exclude executive-level sales managers. Select Add or edit users or Add or edit groups to select the users or groups that you want to exclude. If your policy is scoped by one or more admin units, you can only exclude users or groups that are within the admin unit scope.
On the Content to prioritize page, you can assign (if needed) the sources to prioritize, which increases the chance of generating a high severity alert for these sources. Select one of the following choices:
I want to prioritize content. Selecting this option enables you to prioritize SharePoint sites, Sensitivity labels, Sensitive info types, and File extensions content types. If you choose this option, you must select at least one priority content type.
I don't want to specify priority content right now. If you select this option, the priority content detail pages in the workflow are skipped.
Select Next to continue.
If you've selected I want to prioritize content in the previous step, you'll see the detail pages for SharePoint sites, sensitivity labels, sensitive info types, file extensions, and Scoring. Use these detail pages to define the SharePoint, sensitive info types, sensitivity labels, trainable classifiers, and file extensions to prioritize in the policy. The Scoring detail page allows you to scope the policy to only assign risk scores and generate alerts for specified activities that include priority content.
SharePoint sites: Select Add SharePoint site and select the SharePoint sites you have access to and want to prioritize. For example, "group1@contoso.sharepoint.com/sites/group1".
Note
If your policy is scoped by one or more admin units, you will still see all SharePoint sites, not just SharePoint sites scoped to your admin unit(s) since admin units do not support SharePoint sites.
Sensitive info type: Select Add sensitive info type and select the sensitivity types you want to prioritize. For example, "U.S. Bank Account Number" and "Credit Card Number".
Sensitivity labels: Select Add sensitivity label and select the labels you want to prioritize. For example, "Confidential" and "Secret".
Trainable classifiers: Select Add trainable classifier and select the trainable classifiers you want to prioritize. For example, Source code.
File extensions: Add up to 50 file extensions. You can include or omit the '.' with the file extension. For example, .py or py would prioritize Python files.
Scoring: Decide whether to assign risk scores to all risk management activities detected by this policy or only for activities that include priority content. Choose Get alerts for all activity or Get alerts only for activity that includes priority content.
Select Next to continue.
If you've selected the Data leaks or Data leaks by priority users templates, you see options on the Triggers for this policy page for custom-triggering events and policy indicators. You have the choice to select a DLP policy or indicators for triggering events that bring users assigned to the policy in-scope for activity scoring. If you select the User matches a data loss prevention (DLP) policy triggering event option, you must select a DLP policy from the DLP policy dropdown list to enable triggering indicators for the DLP Policy for this insider risk management policy. If you select the User performs an exfiltration activity triggering event option, you must select one or more of the listed indicators for the policy triggering event.
Note
Priority user groups are not currently supported for admin units. If you are creating a policy based on the Data leaks by priority users template or the Security policy violations by priority users template, you can't select admin units for scoping the policy. Unrestricted administrators can select priority user groups without selecting admin units, but restricted or scoped administrators can't create these policies at all.
Important
If you're unable to select a listed indicator or sequence, it's because they aren't currently enabled for your organization. To make them available to select and assign to the policy, select the Turn on indicators prompt.
If you've selected other policy templates, custom triggering events aren't supported. The built-in policy triggering events apply. Skip to Step 15 without defining policy attributes.
If you've selected the Data leaks by risky users or Security policy violations by risky users templates, you'll see options on the Triggers for this policy page for integration with communication compliance and HR data connector events. You have the choice to assign risk scores when users send messages that contain potentially threatening, harassing, or discriminatory language or to bring users into the policy scope after risky user events are reported in your HR system. If you select the Risk triggers from communication compliance (preview) option, you can accept the default communication compliance policy (automatically created), choose a previously created policy scope for this trigger, or create another scoped policy. If you select HR data connector events, you must configure an HR data connector for your organization.
Select Next to continue.
If you've selected the Data leaks or Data leaks by priority users templates and have selected the User performs an exfiltration activity and associated indicators, you can choose custom or default thresholds for the indicator triggering events that you've selected. Choose either the Use default thresholds (Recommended) or Use custom thresholds for the triggering events.
Select Next to continue.
If you've selected Use custom thresholds for the triggering events, for each triggering event indicator that you selected in Step 10, choose the appropriate level to generate the desired level of activity alerts. You can use the recommended thresholds, custom thresholds, or thresholds based on anomalous activities (for certain indicators) over the daily norm for users.
Select Next to continue.
On the Policy indicators page, you'll see the indicators that you've defined as available on the Insider risk settings > Indicators page which will include indicator variants if you have defined any. Select the indicators you want to apply to the policy.
Important
If indicators on this page can't be selected, you'll need to select the indicators you want to enable for all policies. You can use Turn on indicators in the workflow or select indicators on the Insider risk management > Settings > Policy indicators page.
If you've selected at least one Office or Device indicator, select the Risk score boosters as appropriate. Risk score boosters are only applicable for selected indicators. If you've selected a Data theft or Data leaks policy template, select one or more Sequence detection methods and a Cumulative exfiltration detection method to apply to the policy. If you've selected the Risky browser usage policy template, select one or more of the Browsing indicators.
Select Next to continue.
On the Decide whether to use default or custom indicator thresholds page, choose custom or default thresholds for the policy indicators that you've selected. Choose either the Use default thresholds for all indicators or Specify custom thresholds for the selected policy indicators. If you've selected Specify custom thresholds, choose the appropriate level to generate the desired level of activity alerts for each policy indicator.
Tip
Select the View impact link in the insight below each set of threshold settings to view a graph that can help you determine appropriate threshold settings. Learn more about manually customizing thresholds.
Select Next to continue.
On the Review page, review the settings you've chosen for the policy and any suggestions or warnings for your selections. Select Edit to change any of the policy values or select Submit to create and activate the policy.
Next steps
After you've completed these steps to create your first insider risk management policy, you'll start to receive alerts from activity indicators after about 24 hours. Configure additional policies as needed using the guidance in Step 4 of this article or the steps in Create a new insider risk policy.
To learn more about investigating insider risk alerts and the Alerts dashboard, see Insider risk management activities.