Configure policy indicators in insider risk management
Important
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider risk management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
Insider risk policy templates in Microsoft Purview Insider Risk Management define the type of risk activities that you want to detect and investigate. Each policy template is based on specific indicators that correspond to specific triggers and risk activities. All global indicators are disabled by default; you must select one or more indicators to configure an insider risk management policy.
Signals are collected and alerts are triggered by policies when users perform activities related to indicators.
Tip
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview trials hub. Learn details about signing up and trial terms.
Types of events and indicators
Insider risk management uses different types of events and indicators to collect signals and create alerts:
Triggering events: Events that determine if a user is active in an insider risk management policy. If a user is added to an insider risk management policy that doesn't have a triggering event, the user isn't evaluated by the policy as a potential risk. For example, User A is added to a policy created from the Data theft by departing users policy template and the policy and Microsoft 365 HR connector are properly configured. Until User A has a termination date reported by the HR connector, User A isn't evaluated by this insider risk management policy for potential risk. Another example of a triggering event is if a user has a High severity data loss prevention (DLP) policy alert when using Data leaks policies.
Global settings indicators: Indicators enabled in global settings for insider risk management define both the indicators available for configuration in policies and the types of events signals collected by insider risk management. For example, if a user copies data to personal cloud storage services or portable storage devices and these indicators are selected only in global settings, the user's potentially risky activity is available for review in the Activity explorer. If this user isn't defined in an insider risk management policy, the user isn't evaluated by the policy as a potential risk and therefore isn't assigned a risk score or generate an alert.
Policy indicators: Indicators included in insider risk management policies are used to determine a risk score for an in-scope user. Policy indicators are enabled from indicators defined in global settings and are only activated after a triggering event occurs for a user. Examples of policy indicators include:
- A user copies data to personal cloud storage services or portable storage devices.
- A user account is removed from Microsoft Entra ID.
- A user shares internal files and folders with unauthorized external parties.
Certain policy indicators and sequences might also be used for customizing triggering events for specific policy templates. When configured in the policy workflow for the General data leaks or Data leaks by priority users templates, these indicators or sequences allow more flexibility and customization for your policies and when users are in-scope for a policy. Also, you can define risk management activity thresholds for these triggering indicators for more fine-grained control in a policy.
Define the insider risk policy indicators that are enabled in all insider risk policies
Select Settings, and then select Policy indicators.
Select one or more policy indicators. The indicators selected on the Policy indicators settings page can't be individually configured when creating or editing an insider risk policy in the policy workflow.
Note
It might take several hours for new manually added users to appear in the Users dashboard. Activities for the previous 90 days for these users might take up to 24 hours to display. To view activities for manually added users, select the user on the Users dashboard and open the User activity tab in the details pane.## Two types of policy indicators: built-in indicators and custom indicators
Indicators and pay-as-you-go billing
Some indicators included in insider risk management require that you enable the pay-as-you-go billing model for your organization. Depending on your configured billing model, a notification might be displayed prompting you to configure pay-as-you-go billing to use these indicators.
Built-in indicators vs. custom indicators
Policy indicators are organized into two tabs:
- Built-in indicators: Insider risk management includes many built-in indicators for various scenarios that you can use right away in your policies. Choose the indicators that you want to activate, and then customize indicator thresholds for each indicator level when you create an insider risk policy. The built-in indicators are described in more detail in this article.
- Custom indicators: Use custom indicators together with the Insider Risk Indicators (preview) connector to bring non-Microsoft detections to insider risk management. For example, you might want to extend your detections to include Salesforce and Dropbox and use them alongside the built-in detections provided by the insider risk management solution, which is focused on Microsoft workloads (SharePoint Online and Exchange Online, for example). Learn more about creating a custom indicator
Built-in indicators
Insider risk management includes the following built-in indicators.
Office indicators
These include policy indicators for SharePoint sites, Microsoft Teams, and email messaging.
Cloud storage indicators (preview)
Important
This indicator requires you to enable the pay-as-you-go billing model for this feature in your organization.
These include policy indicators for Google Drive, Box, and Dropbox that you can use to detect for techniques used to determine the environment, gather and steal data, and disrupt the availability or compromise the integrity of a system. To select from cloud storage indicators, you must first connect to the relevant cloud storage app(s) in Microsoft Defender.
After configuring, you can turn off indicators for the apps you don't want to use in settings. For example, you can select a content download indicator for Box and Google Drive, but not Dropbox.
Cloud service indicators (preview)
Important
This indicator requires you to enable the pay-as-you-go billing model for this feature in your organization.
These include policy indicators for Amazon S3 and Azure (SQL Server and Storage) that you can use to detect for techniques used to avoid detection or risky activities. These might include:
- Disabling trace logs
- Updating or deleting SQL Server firewall rules
- Techniques used to steal data, such as sensitive documents
- Techniques used to disrupt the availability or compromise the integrity of a system
- Techniques used to gain higher-level permissions to systems and data.
To select from cloud service indicators, you must first connect to the relevant source service app(s) in Microsoft Defender.
Microsoft Entra ID indicators (preview)
These include risk detections from Microsoft Entra ID Protection. Risk detections are a powerful resource that can include any suspicious or anomalous activity related to a user account in the directory. Microsoft Entra ID Protection risk detections can be linked to an individual user or sign-in event.
User risk detections might flag a legitimate user account as at risk, when a potential threat actor gains access to an account by compromising their credentials or when they detect some type of anomalous user activity. Sign-in risk detections represent the probability that a given authentication request isn't the authorized owner of the account.
To maintain relevance of the indicators to insider risk management policies, only Entra alerts in a ConfirmedCompromised or Remediated status state are evaluated. To learn more about the risk detections in Microsoft Entra ID Protection, see Risks detections in Microsoft Entra ID Protection.
Microsoft Fabric indicators (preview)
Important
This indicator requires you to enable the pay-as-you-go billing model for this feature in your organization.
These include policy indicators for Microsoft Power BI that you can use to detect for techniques used to figure out the environment (such as viewing Power BI reports and dashboards) and techniques used to gather data of interest (such as downloading Power BI reports).
Generative AI apps indicators (preview)
These include policy indicators for numerous generative AI applications. Use these indicators in policies to analyze interactions (prompts and responses) entered into these applications and help detect inappropriate or risky interactions or sharing of confidential information. These indicators the following generative AI applications:
- Microsoft Copilot experiences: Support for user interactions in Microsoft 365 Copilot and other Copilots built using Microsoft Copilot Studio.
- Enterprise AI apps: Non-Copilot AI applications connected using Microsoft Entra and Microsoft Purview Data Map connectors.
- Other AI applications: AI applications discovered from browser and network activity by users in your organization.
- Azure AI Content Safety indicators: Support for communication compliance indicators to identify prompts and responses matching classifiers provided by Azure AI Content Safety like Prompt shields and Protected Materials.
Note
Separate Teams, Copilot, and AI app locations are rolling out and might not yet be visible in your Purview tenant at this time.
Communication compliance indicators
These include policy indicators that detect for employment stressor events, such as emotional outbursts, bullying, failure to take criticism, inability to work or communicate with a team or group, discrimination, violent threats, extremist behavior, and so on. Insider risk management works together with the Microsoft Purview Communication Compliance solution to detect for these types of stressors that indicate an unhealthy workplace environment. Employment stressor events can impact user behavior for risky personas (whether initiators or targets of bad behavior) in several ways that relate to insider risks. Counterproductive work behavior can be a precursor to more serious violations, such as sabotaging company assets or leaking sensitive information.
Additionally, you can choose to detect messages matching specific sensitivity information types (SITs). Including sensitive information inadvertently or maliciously included in messages to user risk scores and their activity history provides investigators with more information to help quickly take actions to mitigate potential data leakage. You can select up to 30 SITs for a policy. Some scenarios might include helping to detect:
- Foreign recruitment
- State actor poaching
- Sharing sensitive information like secret formulas, financial reports, and other proprietary property
- Sharing passwords
Note
You can also use a communication compliance policy as a trigger.
How it works
You can choose from these communication compliance indicators:
- Sending inappropriate content
- Sending financial regulatory text that might be risky
- Sending inappropriate images
You can also choose to detect sensitive information types included in messages.
When you select Create policy from the Communication compliance indicators section:
A single policy is created in communication compliance that detects for messages in Microsoft Exchange Online, Microsoft Teams, Microsoft Viva Engage, and Microsoft 365 Copilot and Microsoft 365 Copilot Chat. The communication compliance policy is based on the indicators and SITs you select. Each indicator is associated with specific trainable classifiers used by communication compliance. Each indicator is associated with specific trainable classifiers and sensitive info types. For more information, see Content safety classifiers based on large language models.
Tip
You can select the information icon next to each indicator to see the trainable classifiers that the indicator uses.
In communication compliance, the trainable classifiers and SITs are listed as conditions for the policy.
The communication compliance policy is named "Insider risk indicator" plus the timestamp, for example: "Insider risk indicator 24-05-01T09.27.17Z" or "Insider risk SIT indicator 24-05-01T09.27.17Z".
Anyone with the Insider Risk Investigators role in insider risk management is automatically added as a reviewer for the communication compliance policy.
Note
After the communication compliance policy is created, to add a reviewer to the policy, you must add the reviewer manually to the Communication Compliance Investigators role group.
If you turn off all of the indicators in the Policy indicators setting, the communication compliance policy is paused. The policy is reenabled if you turn any of the indicators back on.
The communication compliance indicators are made available for new and existing policies in insider risk management that are based on the Data theft or Data leaks templates.
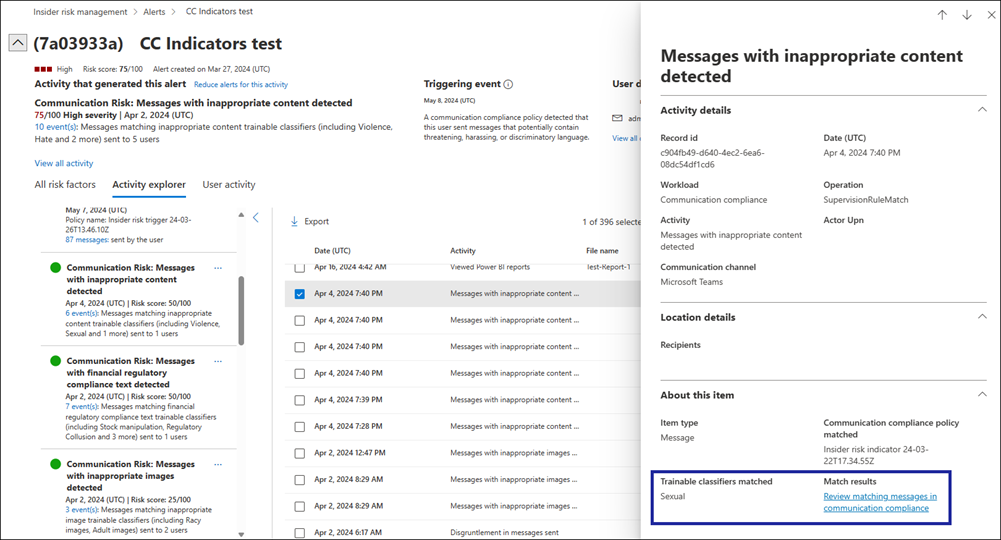
If content sent in a message matches any of the trainable classifiers, it results in a policy match in communication compliance that can be remediated from the Policies page.
Indicators included in insider risk management policies are used to determine a risk score for an in-scope user. They're only activated after a triggering event occurs for a user.
Communication Risk insights appear in the Activity explorer and User activity tabs in insider risk management. If you drill down into a policy match from the Activity explorer or User activity tab, you can learn more about the activity and access a link that opens the communication compliance policy. In the communication compliance policy, you can see the content of the messages that were sent.
Note
You must have the Communication Compliance role or the Communication Compliance Investigators role to access the communication compliance link.
Enable communication compliance indicators in insider risk management
In insider risk management, go to Settings > Policy indicators, and then scroll to the Communication compliance indicators (preview) section.
Under Detect messages matching specific trainable classifiers (preview), select Create policy.
A policy is created in communication compliance and the communication compliance indicators become available in the Policy indicators setting.
Note
If you already created a communication compliance policy this way, but paused it for any reason, selecting Create policy causes the communication compliance policy to resume. In this case, the Status column in the communication compliance Policies list shows "Resuming".
Select one or more of the communication compliance indicators in the Policy indicators setting.
Note
If you had already created a communication compliance policy, if you select different indicators, the communication compliance policy is changed to reflect the appropriate trainable classifiers. Turning off all indicators pauses the communication compliance policy.
Select Save.
To use the indicators, create a new insider risk policy or edit an existing policy. The indicators appear on the Indicators page of the policy workflow. You can adjust thresholds for the indicators as you would for any other indicators in an insider risk management policy.
Note
At this time, real-time analytics for indicator threshold settings aren't available for the communication compliance indicators.
Data loss prevention alerts indicators (preview)
These include policy indicators that are integrated with data loss prevention (DLP) policies. By selecting DLP policies as indicators in insider risk management policies, you can automatically detect if a user has existing alerts in connected DLP policies. DLP policies help to protect sensitive information and reduce the risks of oversharing data with inappropriate users or organizations.
When an insider risk management alert is generated for a user, you can quickly determine if the user has any high risk alerts associated with DLP policies in your organization without having to navigate to DLP solution in the Microsoft Purview portal. You can review and evaluate the insider risk management activity and associated DLP alerts within insider risk management in a unified view.
Configure DLP alerts indicators (preview)
Step 1: To enable the DLP alerts as indicators, complete the following steps:
- In insider risk management settings, select Policy indicators and then select the Built-in Indicators tab.
- Navigate to Data loss prevention (DLP) indicators (preview)
- Select Add DLP policies
- Select the DLP policies that you want to see alerts for in insider risk management.
- Select Add.
- Select the Generating alerts from selected DLP policies checkbox.
- Select Save.
Step 2: To assign DLP alerts indicators to a specific insider risk management policy, complete the following steps:
Create a custom policy using the one of the following templates:
- Data theft by departing users
- Data leaks
- Data leaks by priority users
- Data leaks by risky users
- Risky AI usage
Configure the policy as applicable until you reach the Indicators page.
On the Indicators page, navigate to Data loss prevention (DLP) indicators (preview).
Select the Generating alerts from selected DLP policies checkbox.
Complete the policy configuration workflow and save the new policy.
Device indicators
These include policy indicators for activity such as sharing files over the network or with devices. Indicators include activities involving all file types, excluding executable (.exe) and dynamic link library (.dll) file activity. If you select Device indicators, activity is processed for devices with Windows 10 Build 1809 or higher and macOS (three latest released versions) devices. For both Windows and macOS devices, you must first onboard devices. Device indicators also include browser signal detection to help your organization detect and act on exfiltration signals for nonexecutable files viewed, copied, shared, or printed in Microsoft Edge and Google Chrome. For more information on configuring Windows devices for integration with insider risk, see Enable device indicators and onboard Windows devices in this article. For more information on configuring macOS devices for integration with insider risk, see Enable device indicators and onboard macOS devices in this article. For more information about browser signal detection, see Learn about and configure insider risk management browser signal detection.
Microsoft Defender for Endpoint indicators (preview)
These include indicators from Microsoft Defender for Endpoint related to unapproved or malicious software installation or bypassing security controls. To receive alerts in insider risk management, you must have an active Defender for Endpoint license and insider risk integration enabled. For more information on configuring Defender for Endpoint for insider risk management integration, see Configure advanced features in Microsoft Defender for Endpoint.
Health record access indicators
These include policy indicators for patient medical record access. For example, attempted access to patient medical records in your electronic medical records (EMR) system logs can be shared with insider risk management healthcare policies. To receive these types of alerts in insider risk management, you must have a healthcare-specific data connector and the HR data connector configured.
Physical access indicators
These include policy indicators for physical access to sensitive assets. For example, attempted access to a restricted area in your physical badging system logs can be shared with insider risk management policies. To receive these types of alerts in insider risk management, you must have priority physical assets enabled in insider risk management and the Physical badging data connector configured. To learn more about configuring physical access, see the Priority physical access section in this article.
Microsoft Defender for Cloud Apps indicators
These include policy indicators from shared alerts from Defender for Cloud Apps. Automatically enabled anomaly detection in Defender for Cloud Apps immediately starts detecting and collating results, targeting numerous behavioral anomalies across your users and the machines and devices connected to your network. To include these activities in insider risk management policy alerts, select one or more indicators in this section. To learn more about Defender for Cloud Apps analytics and anomaly detection, see Get behavioral analytics and anomaly detection.
Risky AI usage indicators (preview)
These include policy indicators for Microsoft AI tools and applications. Risky prompt behavior from users and AI-generated responses that include sensitive information are both included in these indicators. For example, attempted sharing of sensitive information in an AI tool or application by a user is considered risky activity. Similarly, an AI tool or application returning a response that contains sensitive information is also considered risky behavior.
Risky browsing indicators (preview)
These include policy indicators for browsing activity related to websites that are considered malicious or risky and pose potential insider risk that might lead to a security or compliance incident. Risky browsing activity refers to users who visit potentially risky websites, such as those associated with malware, pornography, violence, and other unallowed activities. To include these risk management activities in policy alerts, select one or more indicators in this section. To learn about configuring browser exfiltration signals, see Insider risk management browser signal detection.
Cumulative exfiltration detection
Detects when a user's exfiltration activities across all exfiltration channels over the last 30 days exceeds organization or peer group norms. For example, if a user is in a sales role and communicates regularly with customers and partners outside of the organization, their external email activity will likely be higher than the organization's average. However, the user's activity might not be unusual compared to the user's teammates, or others with similar job titles. A risk score is assigned if the user's cumulative exfiltration activity is unusual and exceeds organization or peer group norms.
Note
Peer groups are defined based on organization hierarchy, access to shared SharePoint resources, and job titles in Microsoft Entra ID. If you enable cumulative exfiltration detection, your organization is agreeing to share Microsoft Entra data with the compliance portal, including organization hierarchy and job titles. If your organization does not use Microsoft Entra ID to maintain this information, then detection might be less accurate.
Risk score boosters
These include raising the risk score for activity for the following reasons:
Activity that is above the user's usual activity for that day: Scores are boosted if the detected activity deviates from the user's typical behavior.
User had a previous case resolved as a policy violation: Scores are boosted if the user had a previous case in insider risk management that was resolved as a policy violation.
User is a member of a priority user group: Scores are boosted if the user is a member of a priority user group.
User is detected as a potential high impact user: When this is enabled, users are automatically flagged as potential high-impact users based on the following criteria:
- The user interacts with more sensitive content compared to others in the organization.
- The user's level in the organization's Microsoft Entra hierarchy.
- The total number of users reporting to the user based on the Microsoft Entra hierarchy.
- The user is a member of a Microsoft Entra built-in role with elevated permissions.
Note
When you enable the potential high impact user risk score booster, you're agreeing to share Microsoft Entra data with the compliance portal. If your organization doesn't use sensitivity labels or has not configured organization hierarchy in Microsoft Entra ID, this detection might be less accurate. If a user is detected as both a member of a priority user group and also a potential high-impact user, their risk score will only be boosted once.
In some cases, you might want to limit the insider risk policy indicators that are applied to insider risk policies in your organization. You can turn off the policy indicators for specific areas by disabling them from all insider risk policies in global settings. Triggering events can only be modified for policies created from the Data leaks or Data leaks by priority users templates. Policies created from all other templates don't have customizable triggering indicators or events.
Custom indicators
Use the Custom Indicators tab to create a custom indicator to use as a trigger or as a policy indicator in your policies.
Note
Before you can create a custom indicator to import third-party indicator data, you must create an Insider Risk Indicators connector (preview).
In insider risk management settings, select Policy indicators and then select the Custom Indicators tab.
Select Add custom indicator.
Enter an indicator name and a description (optional).
In the Data connector list, select the Insider Risk Indicator connector that you created previously.
When you select a data connector:
- The name of the source column that you selected when you created the connector is displayed in the Source column from mapping file field. If you didn't select a source column when you created the connector, None appears in this field and you don't need to make a selection.
- In the Values in source column list, select the value that you want to assign to the custom indicator. These are the values that are related to the source column that you specified when you created the connector. For example, if you created a single connector that includes data for two indicators (Salesforce and Dropbox), you would see those values in the list.
If you want to use a column to set threshold values, in the Data from mapping file list, select the column that you want to use for the threshold setting; otherwise, select the Use only as a triggering event without any thresholds option.
Note
Only fields that have a Number data type appear in the Data from mapping file list, since a Number data type is required to set a threshold value. The data type is specified when you set up the connector.
Select Add indicator. The indicator is added to the Custom Indicators list.
Now you can use the custom indicator in any Data theft or Data leaks policies that you create or edit.
- If you're using the custom indicator as a trigger, select your custom trigger on the Triggers page when you create or edit the policy.
- If you're using the custom indicator as a policy indicator, select your custom indicator on the Indicators page when you create or edit the policy.
Note
After selecting your custom trigger or indicator, make sure to set a custom threshold (it's not recommended that you use the default thresholds). You can't set trigger thresholds on a custom indicator if you selected the Use only as a triggering event without any thresholds option.
After adding the custom indicator to your policies, the triggers and insights generated based on the custom indicators appear in the Alerts dashboard, Activity explorer, and User timeline.
Important
- Make sure to wait 24 hours before uploading the data after the custom indicators and the associated policies have been updated. This is because it can take several hours to sync all components. If you immediately upload the data while the updates are syncing, some data might not be scored for risk.
Create a variant of a built-in indicator
You can create detection groups (preview) and use them together with variants of built-in indicators (preview) to tailor detections for different sets of users. For example, to reduce the number of false positives for email activities, you might want to create a variant of the Sending email with attachments to recipients outside the organization built-in indicator to only detect email sent to personal domains. A variant inherits all the properties of the built-in indicator. You can then modify the variant with exclusions or inclusions.
In insider risk management settings, select Policy indicators.
Select New indicator variant (preview). This opens the New indicator variant (preview) pane on the right side of the screen.
In the Base indicator list, select the indicator that you want to create a variant for.
Note
You can create up to three variants for each built-in indicator. If you have already created three variants for a particular built-in indicator, the built-in indicator is grayed out in the list. There are also some built-in indicators (Microsoft Defender for Endpoint indicators, for example) that don't support variants.
Add a name for the variant (or accept the suggested name). A variant name can't be more than 110 characters.
Add a description for the variant (optional). The description appears in the policy to help you differentiate it from other indicators or indicator variants. A description for a variant can't be more than 256 characters.
Under Detection group, select one of the following options:
Ignore activity involving items in selected groups. Select this option if you want to capture everything except for a few exclusions. For example, you might want to use this option to capture all outgoing email except for email sent to specific domains.
Only detect activity involving items in selected groups. Select this option if you want to specify inclusions to capture. For example, select this option if you want to capture only email sent to certain domains.
Note
If you haven't already created a detection group, you won't be able to select an option in the Detection group section.
In the Select one or more detection groups list, select the detection group(s) that you want to apply to the variant. Detection groups are listed under the appropriate detection type heading to help you find the appropriate group. For a single variant, you can add up to five detection groups of a single type. For example, you can add up to five groups of domains, five groups of file types, and so on.
Note
Only detection groups that are applicable to the variant appear in the list. For example, a file type detection group won't appear for the Sharing SharePoint folders with people outside the organization indicator since it's not applicable.
Select Save.
In the Next steps dialog box, if you want to apply the new variant to a specific policy, select the Policies page link.
Tip
To make sure that a variant captures all the important activities that you want to detect, you can apply the built-in indicator and the variant of the built-in indicator in the same policy. You can then observe the activities that each indicator captures in alerts and then use only the variant indicator after making sure everything is detected.
Use a variant in a policy
Go to the Indicators page of the policy workflow.
Find the built-in indicator that includes one or more variants. Built-in indicators that have variants are marked with a small blue box in the variant checkbox and a list appears at the end of the indicator descriptor text to indicate the number of selected variants. Open the list to see the variants.
Note
If you select one or all of the checkboxes in the variant list, the first-level checkbox for the built-in indicator becomes a solid blue checkbox. If none of the boxes in the variant list are selected, the first-level checkbox is blank.
Select Next.
In the Customize thresholds page, you can customize threshold values for variants individually.
Investigate insights provided by variants
Once variants are added to policies, alerts are generated in the dashboard, and an investigator can view more details in the Activity explorer and User activity tabs.
Edit a variant
Select the blue text at the end of the indicator description text. For example, select +2 variants as shown in the following screenshot example.
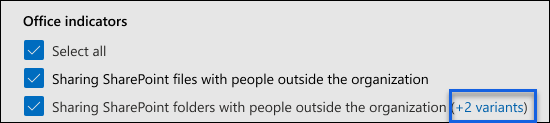
In the View/edit indicators page, select Edit.
Make your changes.
Variant limitations
- You can create up to three variants per built-in indicator.
- For a single variant, you can add up to five detection groups of a single type. For example, you can add a maximum of five groups of domains, five groups of file types, and so on.
- For the detections group preview, variants don't support sequences, cumulative exfiltration activities, the risk score booster, or real-time analytics.
How variants are prioritized against global exclusions and priority content
The scoping of activities happens at multiple places in insider risk management. Scoping happens in the following priority order:
Global exclusions
Variant scoping exclusion/inclusion
Priority content
Enable device indicators and onboard Windows devices
To enable the detection of risk activities on Windows devices and include policy indicators for these activities, your Windows devices must meet the following requirements, and you must complete the following onboarding steps. Learn more about device onboarding requirements
Step 1: Prepare your endpoints
Make sure that the Windows 10 devices that you plan on reporting in insider risk management meet these requirements.
- The device must be running Windows 10 x64 build 1809 or later and the Windows 10 update (OS Build 17763.1075) from February 20, 2020 must be installed.
- The user account used to log into the Windows 10 device must be an active Microsoft Entra account. The Windows 10 device might be Microsoft Entra ID, Microsoft Entra hybrid, joined, or registered.
- Install the Microsoft Edge browser on the endpoint device to detect actions for the cloud upload activity. See Download the new Microsoft Edge based on Chromium.
Note
Endpoint DLP now supports virtualized environments, which means that the insider risk management solution supports virtualized environments through endpoint DLP. Learn more about support for virtualized environments in endpoint DLP
Step 2: Onboard devices
You must enable device checking and onboard your endpoints before you can detect insider risk management activities on a device. Both actions are done in Microsoft Purview.
When you want to enable devices that haven't been onboarded yet, you need to download the appropriate script and deploy it as outlined in this article.
If you already have devices onboarded into Microsoft Defender for Endpoint, they appear in the managed devices list.
Onboard devices
In this deployment scenario, you enable devices that haven't been onboarded yet, and you just want to detect insider risk activities on Windows devices.
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
Select Settings in the upper-right corner of the page.
Under Device onboarding, select Devices. The list is empty until devices are onboarded.
Select Turn on device onboarding.
Note
While it usually takes about 60 seconds for device onboarding to be enabled, allow up to 30 minutes before engaging with Microsoft support.
Select the way you want to deploy to these devices from the Deployment method list, and then select Download package.
Follow the appropriate procedures in Onboarding tools and methods for Windows machines. This link takes you to a landing page where you can access Microsoft Defender for Endpoint procedures that match the deployment package you selected in step 5:
- Onboard Windows machines using Group Policy
- Onboard Windows machines using Microsoft Endpoint Configuration Manager
- Onboard Windows machines using Mobile Device Management tools
- Onboard Windows machines using a local script
- Onboard non-persistent virtual desktop infrastructure (VDI) machines
When you're done and the endpoint device is onboarded, it should be visible in the devices list, and the endpoint device will start reporting audit activity logs to insider risk management.
Note
This experience is under license enforcement. Without the required license, data won't be visible or accessible.
If devices are already onboarded to Microsoft Defender for Endpoint
If Microsoft Defender for Endpoint is already deployed and endpoint devices are reporting in, the endpoint devices appear in the managed devices list. You can continue to onboard new devices into insider risk management to expand coverage by going to Step 2: Onboarding devices.
Enable device indicators and onboard macOS devices
macOS devices (Catalina 10.15 or later) can be onboarded into Microsoft 365 to support insider risk management policies using either Intune or JAMF Pro. For more information and configuration guidance, see Onboard macOS devices into Microsoft 365 overview (preview).
Indicator level settings
When creating a policy using the policy workflow, you can configure how the daily number of risk events should influence the risk score for insider risk alerts. These indicator settings help you control how the number of occurrences of risk events in your organization affect the risk score (and the associated alert severity) for these events.
For example, let's say that you decide to enable SharePoint indicators in the insider risk policy settings and select custom thresholds for SharePoint events when configuring indicators for a new insider risk Data leaks policy. In the insider risk policy workflow, you would configure three different daily event levels for each SharePoint indicator to influence the risk score for alerts associated with these events.
For the first daily event level, you set the threshold to:
- 10 or more events per day for a lower impact to the risk score for the events
- 20 or more events per day for a medium impact to the risk score for the events
- 30 or more events per day for a higher impact to the risk score for the events
These settings effectively mean:
- If there are 1-9 SharePoint events that take place after the triggering event, risk scores are minimally impacted and would tend not to generate an alert.
- If there are 10-19 SharePoint events that take place after a triggering event, the risk score is inherently lower and alert severity levels would tend to be at a low level.
- If there are 20-29 SharePoint events that take place after a triggering event, the risk score is inherently higher and alert severity levels would tend to be at a medium level.
- If there are 30 or more SharePoint events that take place after a triggering event, the risk score is inherently higher and alert severity levels would tend to be at a high level.
Another option for policy thresholds is to assign the policy triggering event to risk management activity that is above the typical daily number of users. Instead of being defined by specific threshold settings, each threshold is dynamically customized for anomalous activities detected for in-scope policy users. If threshold activity for anomalous activities is supported for an individual indicator, you can select Activity is above user's usual activity for the day in the policy workflow for that indicator. If this option isn't listed, anomalous activity triggering isn't available for the indicator. If the Activity is above user's usual activity for the day option is listed for an indicator, but isn't selectable, you need to enable this option in Insider risk settings > Policy indicators.
Use real-time analytics recommendations to set thresholds
You can use real-time analytics (preview) to take advantage of a guided (data-driven) threshold configuration experience that enables you to quickly select the appropriate thresholds for policy indicators. This guided experience can help you efficiently adjust the selection of indicators and thresholds of activity occurrence so that you don't have too few or too many policy alerts.
When analytics is turned on:
The Apply thresholds specific to your users' activity option is enabled on the Indicators page of the policy workflow. Select this option if you want to have insider risk management provide indicator threshold recommendations based on the previous 10 days of user activity in your organization.
Note
To use this option, you must select at least one built-in policy indicator. Insider risk management doesn't provide recommended thresholds for custom indicators or variants of built-in indicators.
If you select the Choose your own thresholds option on the Indicators page of the policy workflow, the defaults for the thresholds settings are based on recommended threshold values (based on activity in your organization) instead of the built-in default values. You'll also see a gauge, a list of the top five indicators, and insights for each indicator.
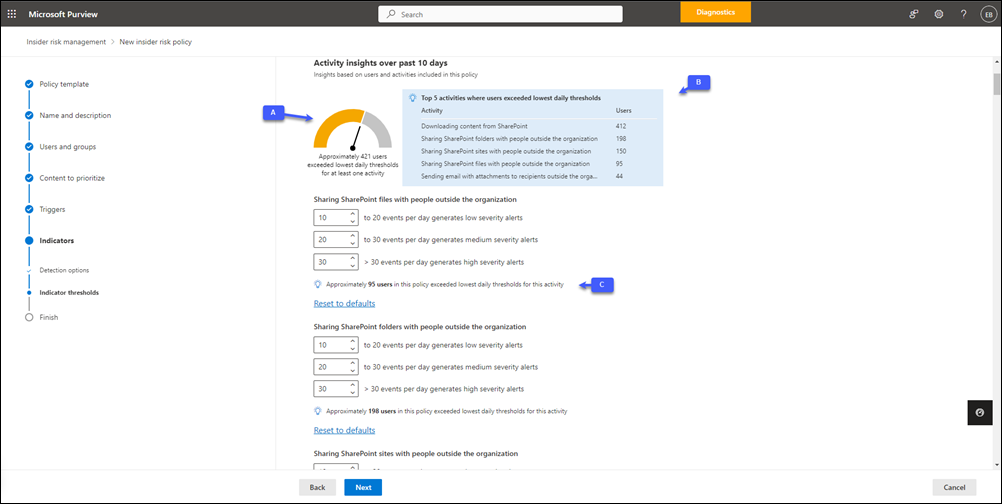
A. The gauge shows the approximate number of scoped users whose activities from the previous 10 days exceeded the lowest daily thresholds for at least one of the selected built-in indicators for the policy. This gauge can help you estimate the number of alerts that might be generated if all users included in the policy were assigned risk scores.
B. The top five indicators list is sorted by the number of users exceeding the lowest daily thresholds. If your policies are generating too many alerts, these are the indicators you might want to focus on to reduce "noise."
C. Insights for each indicator are displayed below the set of threshold settings for that indicator. The insight shows the approximate number of users whose activities from the previous 10 days exceeded the specified low thresholds for the indicator. For example, if the low threshold setting for Downloading content from SharePoint is set to 100, the insight shows the number of users in the policy who performed more than 100 download activities on average in the previous 10 days.
Note
Global exclusions (intelligent detections) are taken into account for real-time analytics.
Adjust threshold settings manually
If you select the Choose your own thresholds option and manually adjust a threshold setting for a specific indicator, the insight below the indicator updates in real time. This helps you configure the appropriate thresholds for each indicator to achieve the highest level of alert effectiveness before activating your policies.
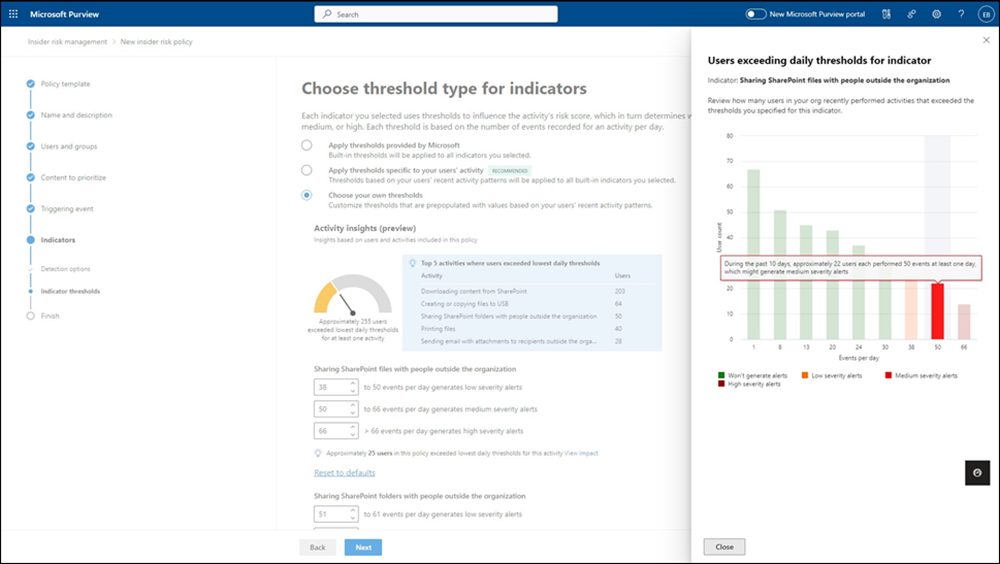
To save time, and to make it easier to understand the impact of manual changes to threshold values, select the View impact link in the insight to display the Users exceeding daily thresholds for indicator graph. This graph provides sensitivity analysis for each policy indicator.
Important
This graph isn't available if you select the Include specific users option when you create the policy. You must select the Include all users and groups option.
You can use this graph to analyze the activity patterns of users in your organization for the selected indicator. For example, in the preceding illustration, the threshold indicator for Sharing SharePoint files with people outside the organization is set to 38. The graph shows how many users performed actions that exceeded that threshold value and the distribution of low, medium, and high severity alerts for those actions. Select a bar to see insights for each value. For example, in the previous illustration, the bar for the 50 value is selected and the insight shows that at that threshold value, approximately 22 users each performed at least 50 events on at least one day in the past 10 days.
Prerequisites for using real-time analytics
To use real-time analytics (preview), you must enable insider risk analytics insights. After analytics is enabled, it can take 24 to 48 hours for insights and recommendations to appear.