gMSA를 사용하여 Defender for Identity에 대한 디렉터리 서비스 계정 구성
이 문서에서는 Defender for Identity DSA 항목으로 사용할 gMSA(그룹 관리 서비스 계정) 를 만드는 방법을 설명합니다.
자세한 내용은 Microsoft Defender for Identity 대한 디렉터리 서비스 계정을 참조하세요.
참고
다중 포리스트 다중 도메인 환경에서 gMSA를 사용해야 하는 센서는 gMSA가 만들어진 도메인에서 해당 컴퓨터 계정을 신뢰해야 합니다. 모든 센서가 gMSA의 암호를 검색하고 도메인 간 인증을 수행할 수 있도록 모든 센서의 컴퓨터 계정을 포함하는 유니버설 그룹을 각 도메인에 만드는 것이 좋습니다. 또한 각 포리스트 또는 도메인에 대해 고유한 이름으로 gMSA를 만드는 것이 좋습니다.
필수 구성 요소: gMSA 계정의 암호를 검색할 수 있는 권한 부여
gMSA 계정을 만들기 전에 계정의 암호를 검색할 수 있는 권한을 할당하는 방법을 고려합니다.
gMSA 항목을 사용하는 경우 센서는 Active Directory에서 gMSA의 암호를 검색해야 합니다. 이 작업은 각 센서에 할당하거나 그룹을 사용하여 수행할 수 있습니다.
단일 포리스트 단일 도메인 배포에서 AD FS/AD CS 서버에 센서를 설치할 계획이 없는 경우 기본 제공 도메인 컨트롤러 보안 그룹을 사용할 수 있습니다.
여러 도메인이 있는 포리스트에서 단일 DSA 계정을 사용하는 경우 유니버설 그룹을 만들고 각 도메인 컨트롤러 및 AD FS/AD CS 서버를 유니버설 그룹에 추가하는 것이 좋습니다.
컴퓨터가 Kerberos 티켓을 받은 후 범용 그룹에 컴퓨터 계정을 추가하는 경우 새 Kerberos 티켓을 받을 때까지 gMSA의 암호를 검색할 수 없습니다. Kerberos 티켓에는 티켓이 발급된 경우 엔터티가 멤버인 그룹 목록이 있습니다.
이러한 시나리오에서 다음 중 하나를 수행합니다.
새 Kerberos 티켓이 발급될 때까지 기다립니다. Kerberos 티켓은 일반적으로 10시간 동안 유효합니다.
서버를 다시 부팅합니다. 서버를 다시 부팅하면 새 그룹 멤버 자격으로 새 Kerberos 티켓이 요청됩니다.
기존 Kerberos 티켓을 제거합니다. 이렇게 하면 도메인 컨트롤러가 새 Kerberos 티켓을 요청합니다.
티켓을 제거하려면 도메인 컨트롤러의 관리자 명령 프롬프트에서 다음 명령을 실행합니다.
klist purge -li 0x3e7
gMSA 계정 만들기
이 섹션에서는 계정의 암호를 검색하고, gMSA 계정을 만든 다음, 계정이 사용할 준비가 되었는지 테스트할 수 있는 특정 그룹을 만드는 방법을 설명합니다.
참고
이전에 gMSA 계정을 사용한 적이 없는 경우 Active Directory 내에서 Microsoft 그룹 키 배포 서비스(KdsSvc)에 대한 새 루트 키를 생성해야 할 수 있습니다. 이 단계는 포리스트당 한 번만 필요합니다.
즉시 사용할 새 루트 키를 생성하려면 다음 명령을 실행합니다.
Add-KdsRootKey -EffectiveImmediately
다음 코드를 환경에 대한 변수 값으로 업데이트합니다. 그런 다음, 관리자 권한으로 PowerShell 명령을 실행합니다.
# Variables:
# Specify the name of the gMSA you want to create:
$gMSA_AccountName = 'mdiSvc01'
# Specify the name of the group you want to create for the gMSA,
# or enter 'Domain Controllers' to use the built-in group when your environment is a single forest, and will contain only domain controller sensors.
$gMSA_HostsGroupName = 'mdiSvc01Group'
# Specify the computer accounts that will become members of the gMSA group and have permission to use the gMSA.
# If you are using the 'Domain Controllers' group in the $gMSA_HostsGroupName variable, then this list is ignored
$gMSA_HostNames = 'DC1', 'DC2', 'DC3', 'DC4', 'DC5', 'DC6', 'ADFS1', 'ADFS2'
# Import the required PowerShell module:
Import-Module ActiveDirectory
# Set the group
if ($gMSA_HostsGroupName -eq 'Domain Controllers') {
$gMSA_HostsGroup = Get-ADGroup -Identity 'Domain Controllers'
} else {
$gMSA_HostsGroup = New-ADGroup -Name $gMSA_HostsGroupName -GroupScope DomainLocal -PassThru
$gMSA_HostNames | ForEach-Object { Get-ADComputer -Identity $_ } |
ForEach-Object { Add-ADGroupMember -Identity $gMSA_HostsGroupName -Members $_ }
}
# Create the gMSA:
New-ADServiceAccount -Name $gMSA_AccountName -DNSHostName "$gMSA_AccountName.$env:USERDNSDOMAIN" `
-PrincipalsAllowedToRetrieveManagedPassword $gMSA_HostsGroup
필요한 DSA 권한 부여
DSA에는 삭제된 개체 컨테이너를 포함하여 Active Directory의 모든 개체에 대한 읽기 전용 권한이 필요합니다.
삭제된 개체 컨테이너에 대한 읽기 전용 권한을 사용하면 Defender for Identity가 Active Directory에서 사용자 삭제를 검색할 수 있습니다.
다음 코드 샘플을 사용하여 gMSA 계정을 사용하는지 여부에 관계없이 삭제된 개체 컨테이너에 필요한 읽기 권한을 부여할 수 있습니다.
팁
권한을 부여하려는 DSA가 gMSA(그룹 관리 서비스 계정)인 경우 먼저 보안 그룹을 만들고, gMSA를 멤버로 추가하고, 해당 그룹에 권한을 추가해야 합니다. 자세한 내용은 gMSA를 사용하여 Defender for Identity에 대한 디렉터리 서비스 계정 구성을 참조하세요.
# Declare the identity that you want to add read access to the deleted objects container:
$Identity = 'mdiSvc01'
# If the identity is a gMSA, first to create a group and add the gMSA to it:
$groupName = 'mdiUsr01Group'
$groupDescription = 'Members of this group are allowed to read the objects in the Deleted Objects container in AD'
if(Get-ADServiceAccount -Identity $Identity -ErrorAction SilentlyContinue) {
$groupParams = @{
Name = $groupName
SamAccountName = $groupName
DisplayName = $groupName
GroupCategory = 'Security'
GroupScope = 'Universal'
Description = $groupDescription
}
$group = New-ADGroup @groupParams -PassThru
Add-ADGroupMember -Identity $group -Members ('{0}$' -f $Identity)
$Identity = $group.Name
}
# Get the deleted objects container's distinguished name:
$distinguishedName = ([adsi]'').distinguishedName.Value
$deletedObjectsDN = 'CN=Deleted Objects,{0}' -f $distinguishedName
# Take ownership on the deleted objects container:
$params = @("$deletedObjectsDN", '/takeOwnership')
C:\Windows\System32\dsacls.exe $params
# Grant the 'List Contents' and 'Read Property' permissions to the user or group:
$params = @("$deletedObjectsDN", '/G', ('{0}\{1}:LCRP' -f ([adsi]'').name.Value, $Identity))
C:\Windows\System32\dsacls.exe $params
# To remove the permissions, uncomment the next 2 lines and run them instead of the two prior ones:
# $params = @("$deletedObjectsDN", '/R', ('{0}\{1}' -f ([adsi]'').name.Value, $Identity))
# C:\Windows\System32\dsacls.exe $params
자세한 내용은 삭제된 개체 컨테이너에 대한 권한 변경을 참조하세요.
gMSA 계정에 필요한 권한이 있는지 확인합니다.
Defender for Identity 센서 서비스인 Azure Advanced Threat Protection 센서는 LocalService 로 실행되며 DSA 계정의 가장을 수행합니다. 서비스로 로그온 정책이 구성되었지만 gMSA 계정에 권한이 부여되지 않은 경우 가장이 실패합니다. 이러한 경우 다음과 같은 상태 문제가 표시됩니다. 디렉터리 서비스 사용자 자격 증명이 올바르지 않습니다.
이 경고가 표시되면 서비스로 로그온 정책이 구성되어 있는지 확인하는 것이 좋습니다. 서비스로 로그온 정책을 구성해야 하는 경우 그룹 정책 설정 또는 로컬 보안 정책에서 로그온합니다.
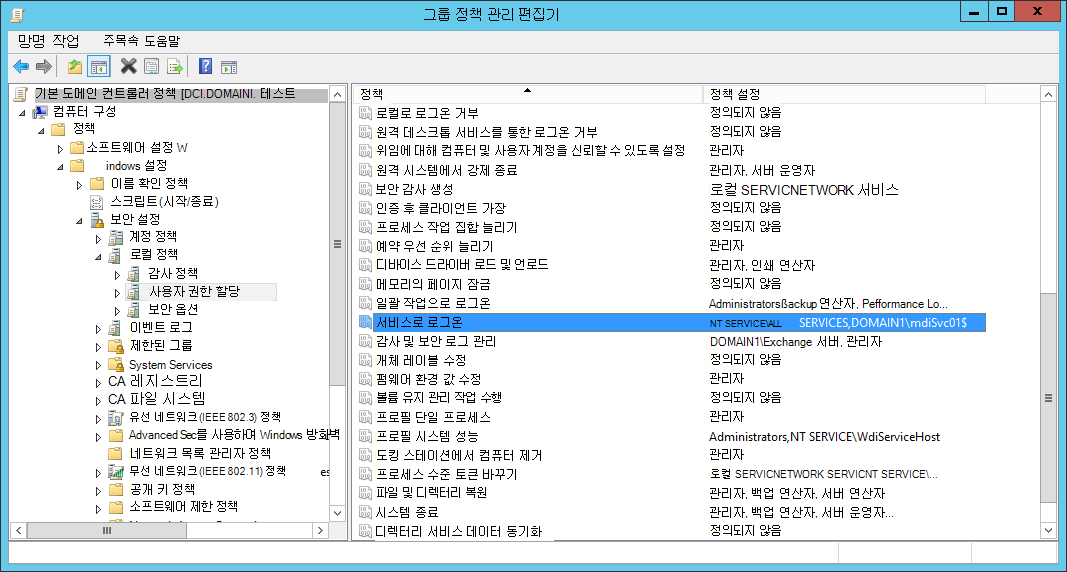
로컬 정책을 검사 로컬 정책을 실행하고
secpol.msc선택합니다. 사용자 권한 할당에서 서비스로 로그온 정책 설정으로 이동합니다. 예시: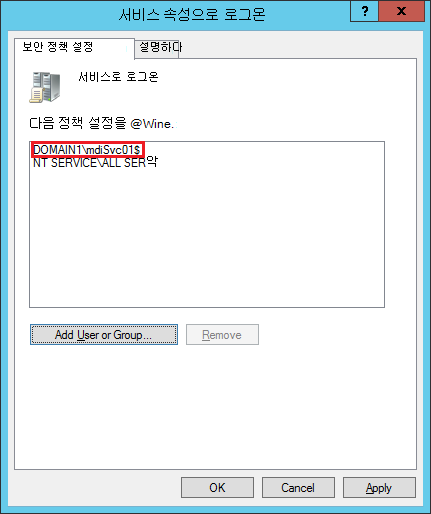
정책을 사용하는 경우 gMSA 계정을 서비스로 로그온할 수 있는 계정 목록에 추가합니다.
설정이 그룹 정책 구성된 경우 검사: 를 실행하고
rsop.msc컴퓨터 구성 - Windows 설정 -> 보안 설정 -> 로컬 정책 -> 사용자 권한 할당 ->> 서비스 정책으로 로그온이 선택되어 있는지 확인합니다. 예시:설정이 구성된 경우 gMSA 계정을 그룹 정책 Management 편집기 서비스로 로그온할 수 있는 계정 목록에 추가합니다.
참고
그룹 정책 관리 편집기 사용하여 서비스로 로그온 설정을 구성하는 경우 NT Service\All Services 및 만든 gMSA 계정을 모두 추가해야 합니다.
Microsoft Defender XDR 디렉터리 서비스 계정 구성
센서를 Active Directory 도메인에 연결하려면 Microsoft Defender XDR 디렉터리 서비스 계정을 구성해야 합니다.
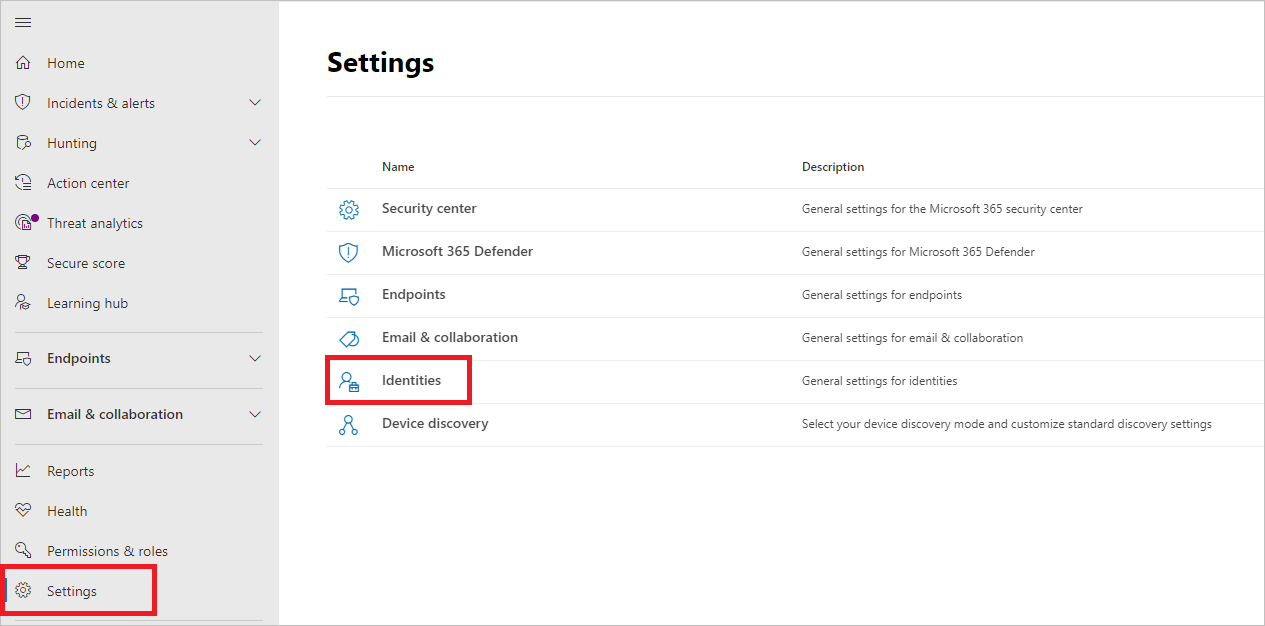
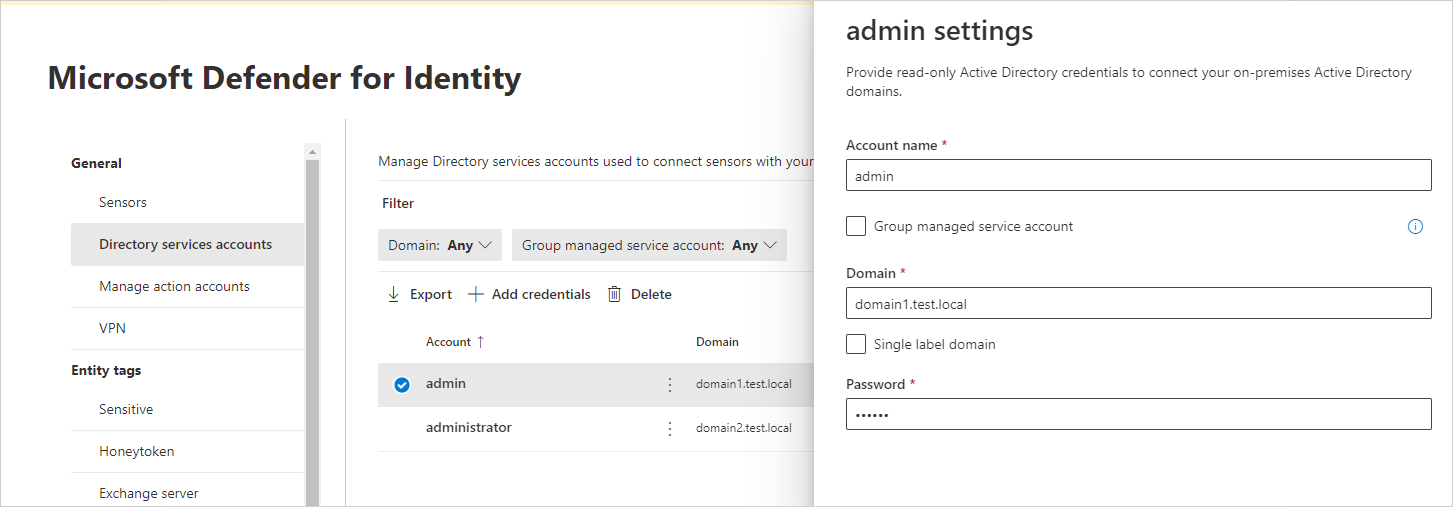
Microsoft Defender XDR설정 > ID로 이동합니다. 예시:
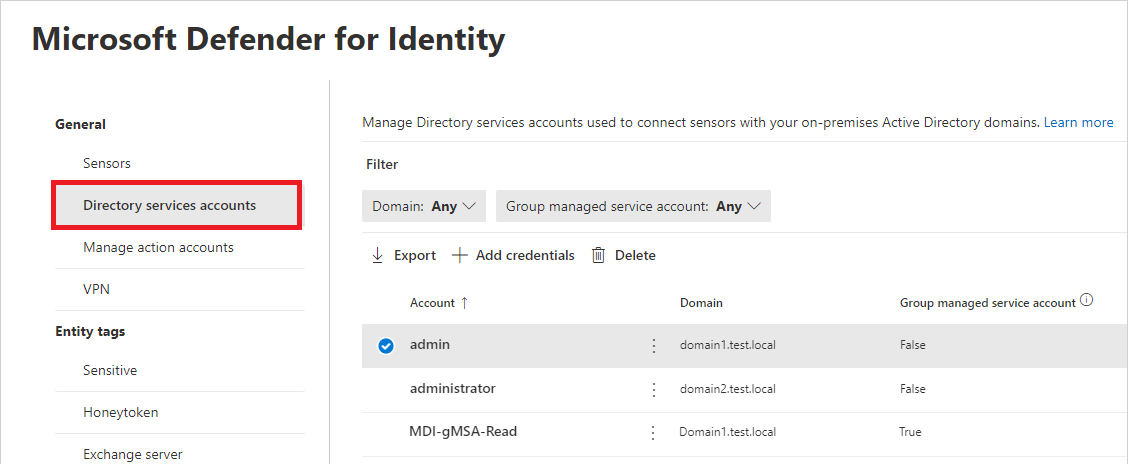
디렉터리 서비스 계정을 선택합니다. 어떤 계정이 어떤 도메인과 연결되어 있는지 확인할 수 있습니다. 예시:
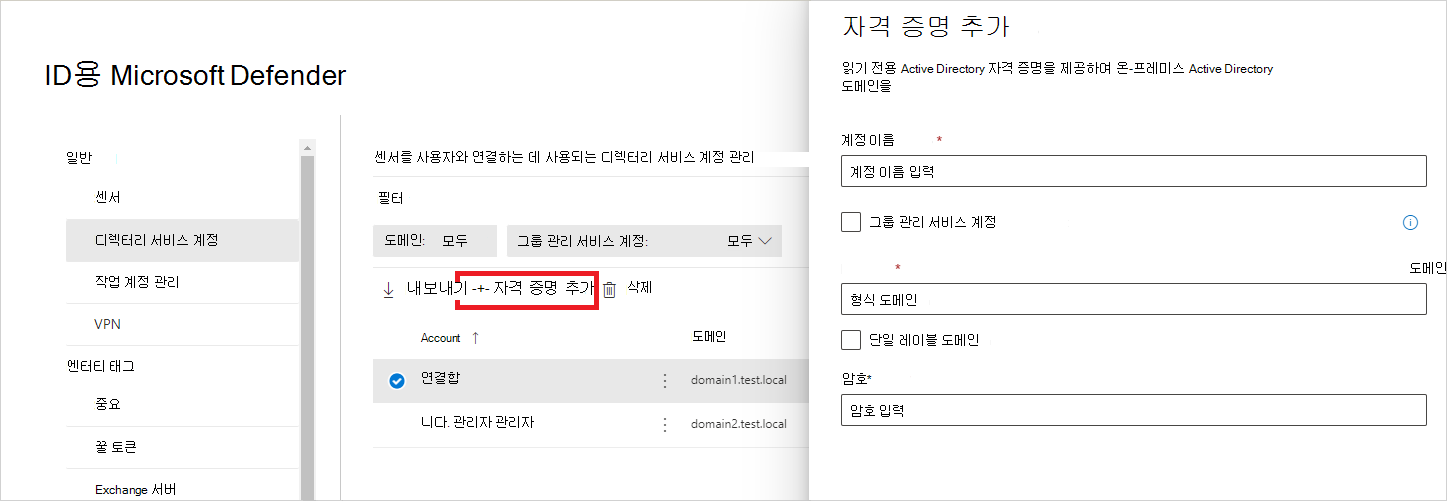
디렉터리 서비스 계정 자격 증명을 추가하려면 자격 증명 추가 를 선택하고 이전에 만든 계정의 계정 이름, 도메인 및 암호를 입력합니다. gMSA( 그룹 관리 서비스 계정 )인지, 단일 레이블 도메인에 속하는지 선택할 수도 있습니다. 예시:
필드 설명 계정 이름 (필수) 읽기 전용 AD 사용자 이름을 입력합니다. 예: DefenderForIdentityUser.
- 표준 AD 사용자 또는 gMSA 계정을 사용해야 합니다.
- 사용자 이름에 UPN 형식을 사용하지 마세요.
- gMSA를 사용하는 경우 사용자 문자열은 기호로$끝나야 합니다. 예:mdisvc$
메모: 특정 사용자에게 할당된 계정을 사용하지 않는 것이 좋습니다.암호 (표준 AD 사용자 계정에 필요) AD 사용자 계정의 경우에만 읽기 전용 사용자에 대한 강력한 암호를 생성합니다. 예: PePR!BZ&}Y54UpC3aB그룹 관리 서비스 계정 (gMSA 계정에 필요) gMSA 계정만의 경우 그룹 관리 서비스 계정을 선택합니다. 도메인 (필수) 읽기 전용 사용자의 도메인을 입력합니다. 예: contoso.com.
사용자가 있는 도메인의 전체 FQDN을 입력하는 것이 중요합니다. 예를 들어 사용자의 계정이 도메인 corp.contoso.com 있는 경우 이 아닌contoso.com를 입력corp.contoso.com해야 합니다.
자세한 내용은 단일 레이블 도메인에 대한 Microsoft 지원을 참조하세요.저장을 선택합니다.
(선택 사항) 계정을 선택하면 해당 계정에 대한 설정과 함께 세부 정보 창이 열립니다. 예시:
참고
이 동일한 절차를 사용하여 표준 Active Directory 사용자 계정의 암호를 변경할 수 있습니다. gMSA 계정에 대한 암호 집합이 없습니다.
문제 해결
자세한 내용은 센서가 gMSA 자격 증명을 검색하지 못했음을 참조하세요.