Architecture Windows 365
Windows 365 fournit un modèle de licence par utilisateur et par mois en hébergeant des PC cloud pour le compte de clients dans Microsoft Azure. Dans ce modèle, il n’est pas nécessaire de tenir compte du stockage, de l’architecture de l’infrastructure de calcul, ni des coûts. L’architecture Windows 365 vous permet également d’utiliser vos investissements existants en matière de réseau et de sécurité Azure. Chaque PC cloud est approvisionné en fonction de la configuration que vous définissez dans la section Windows 365 du centre d’administration Microsoft Intune.
Connectivité de réseau virtuel
Chaque PC cloud dispose d’une carte d’interface réseau virtuelle dans Microsoft Azure. Vous avez deux options de gestion de la carte réseau :
- Si vous utilisez Microsoft Entra rejoindre et un réseau hébergé par Microsoft, vous n’avez pas besoin d’apporter un abonnement Azure ou de gérer la carte réseau.
- Si vous apportez votre propre réseau et utilisez une connexion réseau Azure (ANC), les NIC sont créées par Windows 365 dans votre abonnement Azure.
Les cartes réseau sont rattachées à un réseau virtuel Azure en fonction de la configuration de votre connexion réseau Azure (ANC).
Windows 365 est pris en charge dans de nombreuses régions Azure. Vous pouvez contrôler la région Azure utilisée de deux manières :
- En sélectionnant le réseau hébergé par Microsoft et une région Azure.
- En sélectionnant un réseau virtuel Azure à partir de votre abonnement Azure lors de la création d'un ANC.
La région du réseau virtuel Azure détermine où l’ordinateur cloud est créé et hébergé.
Lorsque vous utilisez votre propre réseau virtuel, vous pouvez étendre l’accès entre vos régions Azure actuelles à d’autres régions Azure prises en charge par Windows 365. Pour l’étendre à d’autres régions, vous pouvez utiliser l’appairage de réseaux virtuels Azure ou Virtual WAN.
En utilisant votre propre réseau virtuel Azure, Windows 365 vous permet d’utiliser les fonctionnalités de routage et de sécurité du réseau virtuel, notamment :
- Groupes de sécurité réseau Azure
- Routage défini par l’utilisateur
- Pare-feu Azure
- Appliances virtuelles réseau (NVA)
Conseil
Pour le filtrage web et la protection réseau pour les PC cloud, envisagez d’utiliser les fonctionnalités de protection réseau et de protection web de Microsoft Defender pour point de terminaison. Ces fonctionnalités peuvent être déployées sur des points de terminaison physiques et virtuels à l’aide du centre d’administration Microsoft Intune.
intégration Microsoft Intune
Microsoft Intune est utilisé pour gérer tous vos PC cloud. Microsoft Intune et les composants Windows associés ont différents points de terminaison réseau qui doivent être autorisés via le Réseau virtuel. Les points de terminaison Apple et Android peuvent être ignorés en toute sécurité si vous n’utilisez pas Microsoft Intune pour gérer ces types d’appareils.
Conseil
Veillez à autoriser l’accès à Windows Notification Services (WNS). Vous ne remarquerez peut-être pas immédiatement un impact si l’accès est bloqué. Toutefois, WNS permet à Microsoft Intune de déclencher immédiatement des actions sur les points de terminaison Windows au lieu d’attendre des intervalles d’interrogation de stratégie normaux sur ces appareils ou une interrogation de stratégie au démarrage/ouverture de session. WNS recommande la connectivité directe du client Windows à WNS.
Vous devez uniquement accorder l’accès à un sous-ensemble de points de terminaison en fonction de l’emplacement de votre locataire Microsoft Intune. Pour trouver l’emplacement de votre locataire (ou Azure Scale Unit (ASU)), connectez-vous au centre d’administration Microsoft Intune, choisissez Administration du locataire>Détails du locataire. Sous Emplacement du locataire, vous verrez un nom semblable à « Amérique du Nord 0501 » ou « Europe 0202 ». Les lignes de la documentation Microsoft Intune sont différenciées par région géographique. Les régions sont indiquées par les deux premières lettres dans les noms (na = Amérique du Nord, eu = Europe, ap = Asie-Pacifique). Étant donné que les locataires peuvent être déplacés dans une région, il est préférable d’autoriser l’accès à une région entière plutôt qu’à un point de terminaison spécifique dans cette région.
Pour plus d’informations sur les régions de service Microsoft Intune et les informations d’emplacement des données, consultez Stockage et traitement des données dans Intune.
Services d’identité
Windows 365 utilise Microsoft Entra ID et Active Directory local Domain Services (AD DS). Microsoft Entra ID fournit :
- Authentification utilisateur pour Windows 365 (comme avec tout autre service Microsoft 365).
- Services d’identité d’appareil pour Microsoft Intune via Microsoft Entra jointure hybride ou jointure Microsoft Entra.
Lors de la configuration des PC cloud pour utiliser Microsoft Entra jointure hybride, AD DS fournit :
- Jonction de domaine locale pour les PC Cloud.
- Authentification utilisateur pour les connexions RDP (Protocole Bureau à distance).
Lors de la configuration des PC cloud pour utiliser Microsoft Entra jointure, Microsoft Entra ID fournit :
- Le mécanisme de jonction de domaine pour les PC Cloud.
- Authentification utilisateur pour les connexions RDP.
Pour plus d’informations sur l’impact des services d’identité sur le déploiement, la gestion et l’utilisation des PC Cloud, consultez Identité et d’authentification.
Identifiant Microsoft Entra
Microsoft Entra ID fournit l’authentification et l’autorisation de l’utilisateur pour le portail web Windows 365 et pour les applications clientes Bureau à distance. Les deux prennent en charge l’authentification moderne, ce qui signifie que Microsoft Entra accès conditionnel peut être intégré pour fournir :
- Authentification multifacteur
- restrictions basées sur l’emplacement
- gestion des risques de connexion
- limites de session, y compris :
- fréquence de connexion pour les clients Bureau à distance et le portail web Windows 365
- persistance des cookies pour le portail web Windows 365
- contrôles de conformité des appareils
Pour plus d’informations sur l’utilisation de l’accès conditionnel Microsoft Entra avec Windows 365, consultez Définir des stratégies d’accès conditionnel.
Services de domaine Active Directory
Windows 365 PC cloud peuvent être joints Microsoft Entra hybrides ou Microsoft Entra joints. Lorsque vous utilisez Microsoft Entra jointure hybride, les PC cloud doivent joindre un domaine à un domaine AD DS. Ce domaine doit être synchronisé avec Microsoft Entra ID. Les contrôleurs de domaine du domaine peuvent être hébergés dans Azure ou localement. S’ils sont hébergés localement, la connectivité doit être établie à partir d’Azure vers l’environnement local. La connectivité peut se présenter sous la forme d’Azure Express Route ou d’un VPN de site à site. Pour plus d’informations sur l’établissement d’une connectivité réseau hybride, consultez Implémenter un réseau hybride sécurisé. La connectivité doit autoriser la communication à partir des PC cloud vers les contrôleurs de domaine requis par Active Directory. Pour plus d’informations, consultez Configurer le pare-feu pour le domaine AD et les approbations.
Connectivité des utilisateurs
La connectivité des PC Cloud est assurée par Azure Virtual Desktop. Aucune connexion entrante directe à partir d’Internet n’est effectuée au PC cloud. Au lieu de cela, les connexions sont réalisées à partir de :
- Les PC Cloud vers les points de terminaison Azure Virtual Desktop.
- Les clients Bureau à distance vers les points de terminaison Azure Virtual Desktop.
Pour plus d’informations sur ces ports, consultez Liste des URL requises par Azure Virtual Desktop. Pour faciliter la configuration des contrôles de sécurité réseau, utilisez des étiquettes de service pour Azure Virtual Desktop afin d’identifier ces points de terminaison. Pour plus d’informations sur les balises de service Azure, voir Vue d’ensemble des balises de service Azure.
Il n’est pas nécessaire de configurer vos PC Cloud pour établir ces connexions. Windows 365 intègre en toute transparence les composants de connectivité Azure Virtual Desktop dans la galerie ou dans des images personnalisées.
Pour plus d’informations sur l’architecture réseau d’Azure Virtual Desktop, consultez Compréhension de la connectivité réseau d’Azure Virtual Desktop.
Les PC Cloud Windows 365 ne prennent pas en charge les courtiers de connexion tiers.
Architecture « hébergé pour le compte de »
L’architecture « hébergé pour le compte de » permet aux services Microsoft, une fois que les autorisations appropriées et étendues à un réseau virtuel leur ont été déléguées par le propriétaire d’un abonnement, d’attacher les services Azure hébergés à un abonnement client. Ce modèle de connectivité permet à un service Microsoft de fournir des logiciels en tant que service et des services avec licence associée à un utilisateur, par opposition à des services standard basés sur la consommation.
Les diagrammes suivants illustrent l’architecture logique d’une configuration de jointure Microsoft Entra à l’aide d’un réseau hébergé par Microsoft, une configuration de jointure Microsoft Entra à l’aide de la connexion réseau d’un client (« apportez votre propre réseau ») et une configuration de jointure hybride Microsoft Entra à l’aide d’un ANC, respectivement.
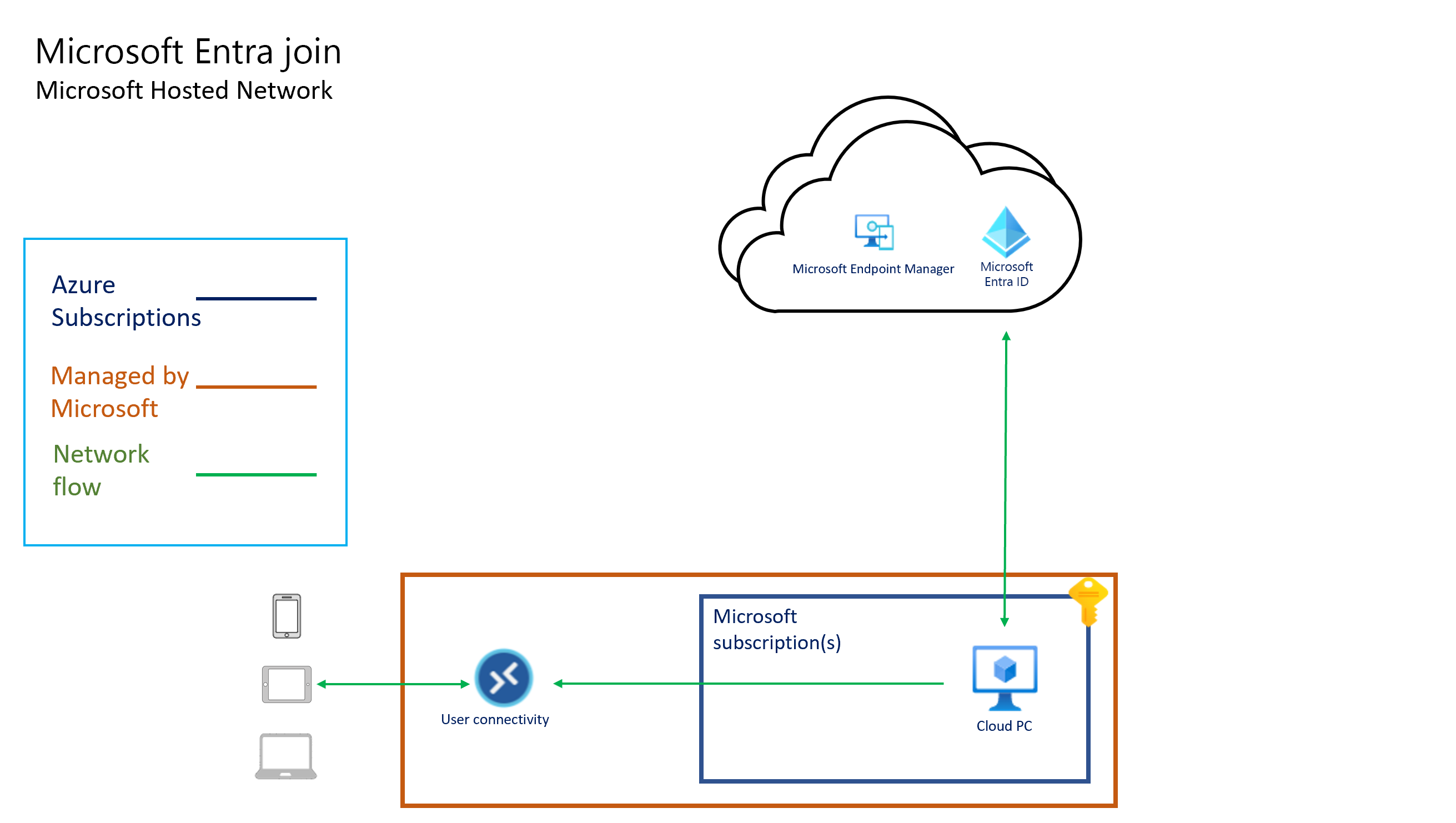
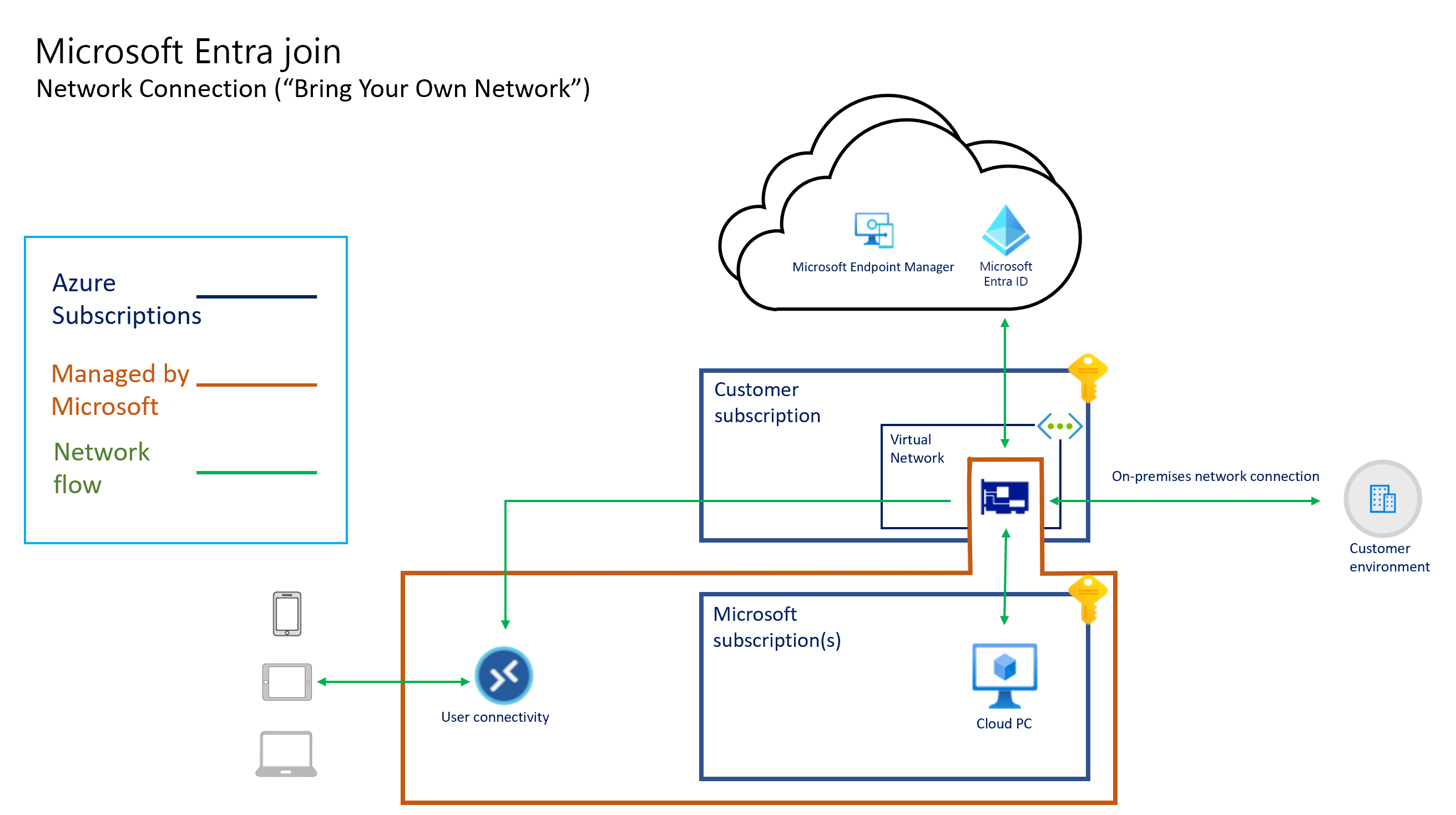
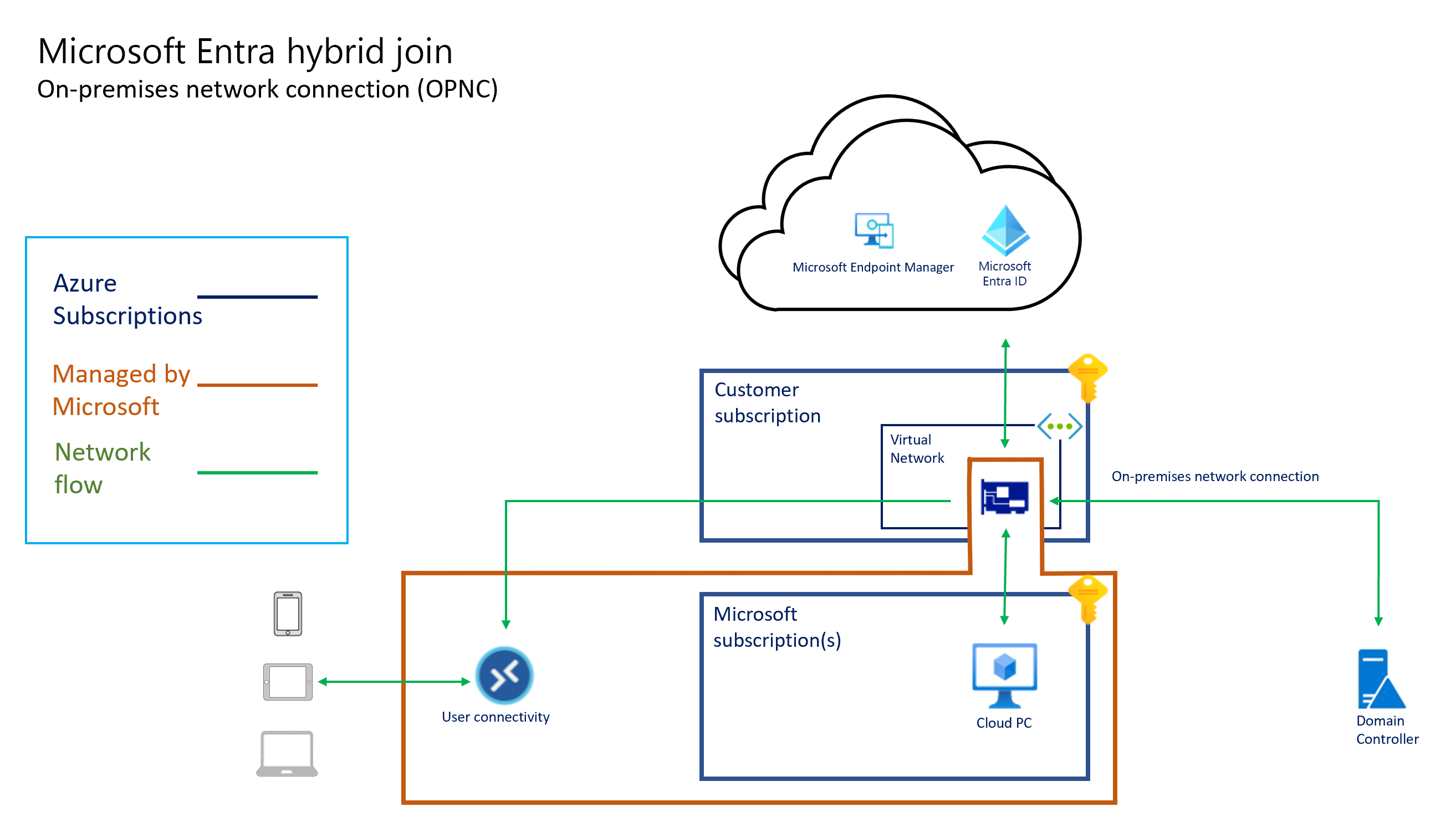
Toute la connectivité des PC cloud est assurée par la carte d’interface réseau virtuelle. L’architecture « hébergée pour le compte de » signifie que les PC cloud existent dans l’abonnement détenu par Microsoft. Par conséquent, Microsoft induit les coûts d’exécution et de gestion de cette infrastructure.
Windows 365 gère la capacité et la disponibilité en région des abonnements Windows 365. Windows 365 détermine la taille et le type de machine virtuelle en fonction de la licence que vous attribuez à l’utilisateur. Windows 365 détermine la région Azure dans laquelle héberger vos PC Cloud en fonction du réseau virtuel que vous sélectionnez lors de la création d’une connexion réseau locale.
Windows 365 s’aligne sur les stratégies de protection des données Microsoft 365. Les données client dans les services cloud d’entreprise de Microsoft sont protégées par divers technologies et processus :
- Différentes formes de chiffrement.
- Isolement logique par rapport aux autres locataires.
- Accessibilité à un ensemble limité, contrôlé et sécurisé d’utilisateurs, à partir de clients spécifiques.
- Sécurisation pour un accès à l’aide de contrôles d’accès basés sur les rôles.
- Réplication vers plusieurs serveurs, points de terminaison de stockage et centres de données pour assurer la redondance.
- Surveillance des accès non autorisés, de la consommation excessive des ressources et de la disponibilité.
Pour plus d’informations Windows chiffrement de PC Cloud Windows 365, consultez Chiffrement des données dans Windows 365.
Prochaines étapes
En savoir plus sur l’identité et l’authentification Windows 365.