Configure your Microsoft 365 tenant for increased security
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
Your organizational needs require security.
Specifics are up to your business.
This article walks you through the manual configuration of tenant-wide settings that affect the security of your Microsoft 365 environment. Use these recommendations as a starting point.
Tune EOP and Defender for Office 365 protection policies in the Microsoft Defender portal
The Microsoft Defender portal has capabilities for both protection and reporting. It has dashboards you can use to monitor and take action when threats arise.
As an initial step, you need to configure email authentication records in DNS for all custom email domains in Microsoft 365 (SPF, DKIM, and DMARC). Microsoft 365 automatically configures email authentication for the *.onmicrosoft.com domain. For more information, see Step 1: Configure email authentication for your Microsoft 365 domains.
Note
For non-standard deployments of SPF, hybrid deployments, and troubleshooting: Set up SPF to help prevent spoofing.
Most protection features in Exchange Online Protection (EOP) and Defender for Office 365 come with default policy configurations. For more information, see the table here.
We recommend turning on and using the Standard and/or Strict preset security policies for all recipients. For more information, see the following articles:
- Turn on and configure preset security policies: Preset security policies in EOP and Microsoft Defender for Office 365.
- Difference in settings between Standard and Strict preset security policies: Policy settings in preset security policies.
- Complete list of all features and settings in default policies, Standard preset security policies, and Strict preset security policies: Recommended settings for EOP and Microsoft Defender for Office 365 security.
Custom policies are required if the business needs of your organization require policy settings that are different than or aren't defined in preset security policies. Or, if your organization requires a different user experience for quarantined messages (including notifications). For more information, see Determine your protection policy strategy.
View dashboards and reports in the Microsoft Defender portal
In the Defender portal at https://security.microsoft.com select Reports. Or, to go directly to the Reports page, use https://security.microsoft.com/securityreports.
On the Reports page, you can view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
The data in these reports becomes richer as your organization uses Office 365 services (keep this point in mind if you're piloting or testing). For now, be familiar with what you can monitor and take action on.
On the Reports page at https://security.microsoft.com/securityreports, select Email & collaboration > Email & collaboration reports.
On the Email & collaboration reports page that opens, note the cards that are available. In any card, select View details to dig into the data. For more information, see the following articles:
- View email security reports in the Microsoft Defender portal
- View Defender for Office 365 reports in the Microsoft Defender portal
Mail flow reports and insights are available in the Exchange admin center (EAC). For more information, see Mail flow reports and Mail flow insights.
|If you're investigating or experiencing an attack against your tenant, use Threat Explorer (or real-time detections) to analyze threats. Explorer (and the real-time detections report) shows you the volume of attacks over time, and you can analyze this data by threat families, attacker infrastructure, and more. You can also mark any suspicious email for the Incidents list.
Additional considerations
For information about ransomware protection, see the following articles:
- Protect against ransomware
- Malware and Ransomware Protection in Microsoft 365
- Ransomware incident response playbooks
Configure tenant-wide sharing policies in SharePoint admin center
Microsoft recommendations for configuring SharePoint team sites at increasing levels of protection, starting with baseline protection. For more information, see Policy recommendations for securing SharePoint sites and files.
SharePoint team sites configured at the baseline level allow sharing files with external users by using anonymous access links. This approach is recommended instead of sending files in email.
To support the goals for baseline protection, configure tenant-wide sharing policies as recommended here. Sharing settings for individual sites can be more restrictive than this tenant-wide policy, but not more permissive.
| Area | Includes a default policy | Recommendation |
|---|---|---|
| Sharing (SharePoint Online and OneDrive for Business) | Yes | External sharing is enabled by default. These settings are recommended:
More information: External sharing overview |
SharePoint admin center and OneDrive for Business admin center include the same settings. The settings in either admin center apply to both.
Configure settings in Microsoft Entra ID
Be sure to visit these two areas in Microsoft Entra ID to complete tenant-wide setup for more secure environments.
Configure named locations (under conditional access)
If your organization includes offices with secure network access, add the trusted IP address ranges to Microsoft Entra ID as named locations. This feature helps reduce the number of reported false positives for sign-in risk events.
See: Named locations in Microsoft Entra ID
Block apps that don't support modern authentication
Multi-factor authentication requires apps that support modern authentication. Apps that don't support modern authentication can't be blocked by using conditional access rules.
For secure environments, be sure to disable authentication for apps that don't support modern authentication. You can do this in Microsoft Entra ID with a control that is coming soon.
In the meantime, use one of the following methods to block access for apps in SharePoint Online and OneDrive for Business that don't support modern authentication:
SharePoint admin center:
- In the SharePoint admin center at https://admin.microsoft.com/sharepoint, go to Policies > Access control.
- On the Access control page, select Apps that don't use modern authentication.
- In the Apps that don't use modern authentication flyout that opens, select Block access, and then select Save.
PowerShell: See Block apps that don't use modern authentication.
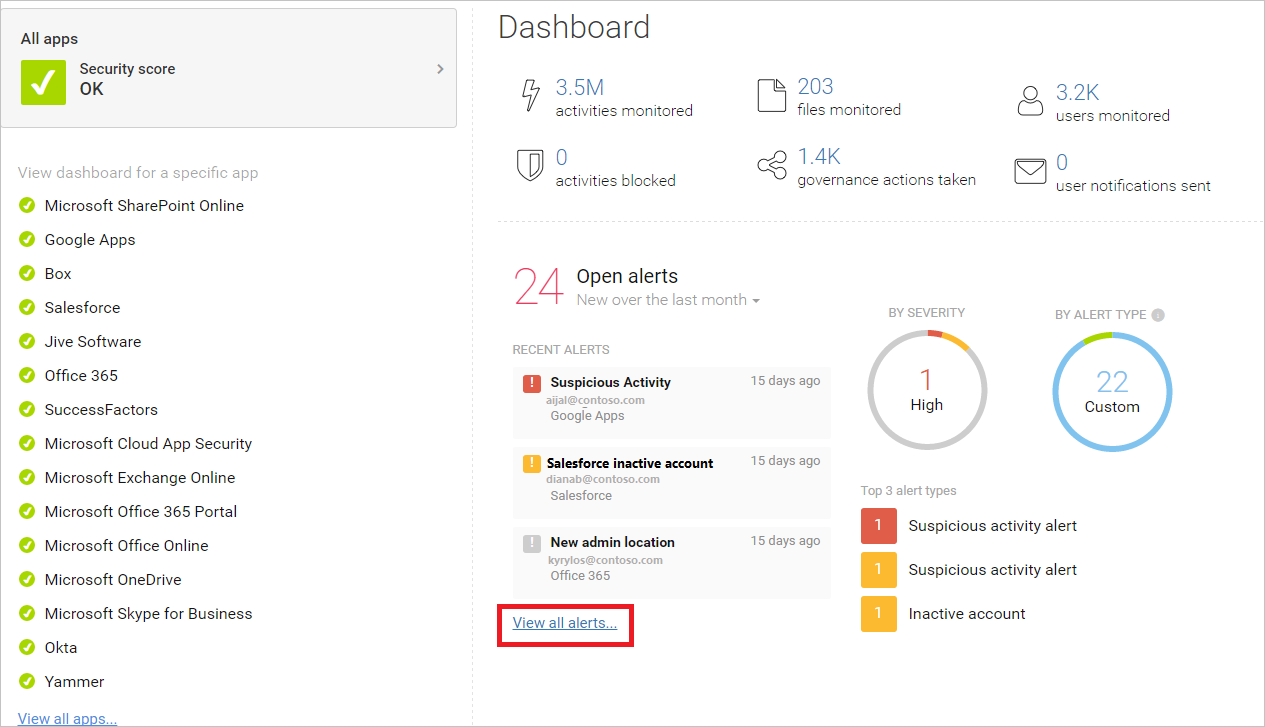
Get started with Defender for Cloud Apps or Office 365 Cloud App Security
Use Microsoft 365 Cloud App Security to evaluate risk, to alert on suspicious activity, and to automatically take action. Requires Office 365 E5 plan.
Or, use Microsoft Defender for Cloud Apps to obtain deeper visibility even after access is granted, comprehensive controls, and improved protection for all your cloud applications, including Office 365.
Because this solution recommends the EMS E5 plan, we recommend you start with Defender for Cloud Apps so you can use it with other SaaS applications in your environment. Start with default policies and settings.
More information:
- Deploy Defender for Cloud Apps
- More information about Microsoft Defender for Cloud Apps
- What is Defender for Cloud Apps?
Additional resources
These articles and guides provide additional prescriptive information for securing your Microsoft 365 environment:
Microsoft security guidance for political campaigns, nonprofits, and other agile organizations (you can use these recommendations in any environment, especially cloud-only environments)
Recommended security policies and configurations for identities and devices (these recommendations include help for AD FS environments)