Network Security Perimeter for Azure SQL Database and Azure Synapse Analytics
Applies to:
Azure SQL Database
Azure Synapse Analytics (dedicated SQL pools only)
Network Security Perimeter (preview) secures both inbound and outbound network traffic between Azure SQL Database and other Platform as a Service (PaaS) resources (for example, Azure Storage and Azure Key Vault). Any attempts made to communicate with Azure resources that aren't inside the perimeter is blocked.
Important
- This article applies to both Azure SQL Database and dedicated SQL pool (formerly SQL DW) in Azure Synapse Analytics. These settings apply to all SQL Database and dedicated SQL pool (formerly SQL DW) databases associated with the server. For simplicity, the term 'database' refers to both databases in Azure SQL Database and Azure Synapse Analytics. Likewise, any references to 'server' is referring to the logical SQL server that hosts Azure SQL Database and dedicated SQL pool (formerly SQL DW) in Azure Synapse Analytics. This article does not apply to Azure SQL Managed Instance or dedicated SQL pools in Azure Synapse Analytics workspaces.
Associate SQL Database with a Network Security Perimeter in the Azure portal
Search for Network Security Perimeter in the Azure portal search bar and then select the Create button and create the resource.
Provide a Name and Region and choose the subscription.
Under the Resources section, select the Associate button and navigate to the SQL Database you want to add.
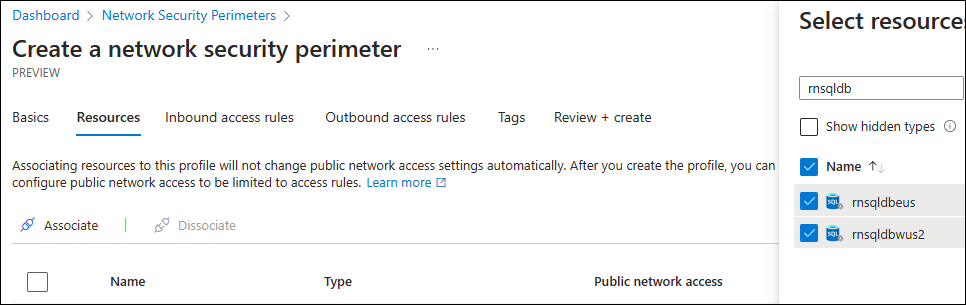
Go through the rest of the creation process without entering anything in Inbound access rules or Outbound access rules.
Using SQL Database with a Network Security Perimeter
By default, Network Security Perimeter uses Learning Mode, which can be used to log all traffic to and from SQL Database. The network traffic can be logged to a Log Analytics Workspace or Azure Storage account using Diagnostic logging for Azure Network Security Perimeter. Finally, Network Security Perimeter can be switched to Enforced mode. In Enforced mode, any access denied shows the following error:
Error 42118
Login failed because the network security perimeter denied inbound access.