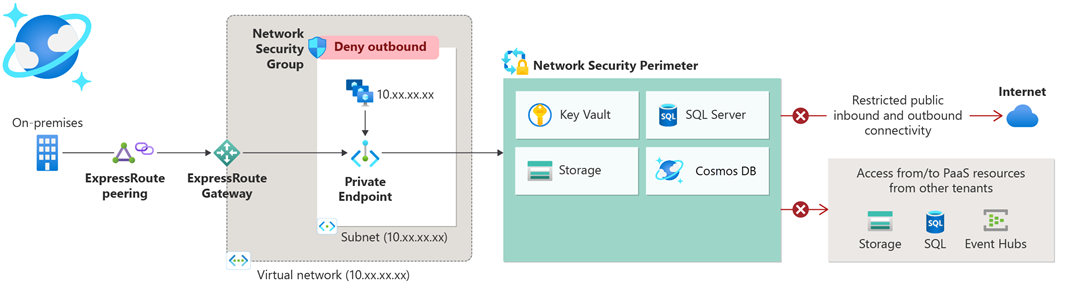
What is a network security perimeter?
Network security perimeter allows organizations to define a logical network isolation boundary for PaaS resources (for example, Azure Storage account and SQL Database server) that are deployed outside your organization’s virtual networks. It restricts public network access to PaaS resources within the perimeter; access can be exempted by using explicit access rules for public inbound and outbound.
For access patterns involving traffic from virtual networks to PaaS resources, see What is Azure Private Link?.
Features of a network security perimeter include:
- Resource to resource access communication within perimeter members, preventing data exfiltration to nonauthorized destinations.
- External public access management with explicit rules for PaaS resources associated with the perimeter.
- Access logs for audit and compliance.
- Unified experience across PaaS resources.
Important
Network Security Perimeter is in public preview and available in all Azure public cloud regions. This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Components of a network security perimeter
A network security perimeter includes the following components:
| Component | Description |
|---|---|
| Network security perimeter | Top level resource defining logical network boundary to secure PaaS resources. |
| Profile | Collection of access rules that apply on resources associated with the profile. |
| Access rule | Inbound and outbound rules for resources in a perimeter to allow access outside the perimeter. |
| Resource association | Perimeter membership for a PaaS resource. |
| Diagnostics settings | Extension resource hosted by Microsoft Insights to collect logs & metrics for all resources in the perimeter. |
Note
For organizational and informational safety, don't include any personally identifiable or sensitive data in the network security perimeter rules or other network security perimeter configurations.
Network security perimeter properties
When creating a network security perimeter, you can specify the following properties:
| Property | Description |
|---|---|
| Name | A unique name within the resource group. |
| Location | A supported Azure region where the resource is located. |
| Resource group name | Name of the resource group where the network security perimeter should be present. |
Access modes in network security perimeter
Administrators add PaaS resources to a perimeter by creating resource associations. These associations can be made in two access modes. The access modes are:
| Mode | Description |
|---|---|
| Learning mode | - Default access mode. - Helps network administrators to understand the existing access patterns of their PaaS resources. - Advised mode of use before transitioning to enforced mode. |
| Enforced mode | - Must be set by the administrator. - By default, all traffic except intra perimeter traffic is denied in this mode unless an Allow access rule exists. |
Learn more on transitioning from learning mode to enforced mode in Transitioning to a network security perimeter article.
Why use a network security perimeter?
Network security perimeter provides a secure perimeter for communication of PaaS services deployed outside the virtual network. It allows you to control network access to Azure PaaS resources. Some of the common use cases include:
- Create a secure boundary around PaaS resources.
- Prevent data exfiltration by associating PaaS resources to the perimeter.
- Enable access rules to grant access outside the secure perimeter.
- Manage access rules for all the PaaS resources within the network security perimeter in a single pane of glass.
- Enable diagnostic settings to generate access logs of PaaS resources within the perimeter for Audit and Compliance.
- Allow private endpoint traffic without other access rules.
How does a network security perimeter work?
When a network security perimeter is created and the PaaS resources are associated with the perimeter in enforced mode, all public traffic is denied by default thus preventing data exfiltration outside the perimeter.
Access rules can be used to approve public inbound and outbound traffic outside the perimeter. Public inbound access can be approved using Network and Identity attributes of the client such as source IP addresses, subscriptions. Public outbound access can be approved using FQDNs (Fully Qualified Domain Names) of the external destinations.
For example, upon creating a network security perimeter and associating a set of PaaS resources with the perimeter like Azure Key Vault and SQL DB in enforced mode, all incoming and outgoing public traffic is denied to these PaaS resources by default. To allow any access outside the perimeter, necessary access rules can be created. Within the same perimeter, profiles can be created to group PaaS resources with similar set of inbound and outbound access requirements.
Onboarded private link resources
A network security perimeter-aware private link resource is a PaaS resource that can be associated with a network security perimeter. Currently the list of onboarded private link resources are as follows:
| Private link resource name | Resource type | Resources |
|---|---|---|
| Azure Monitor | Microsoft.Insights/dataCollectionEndpoints Microsoft.Insights/ScheduledQueryRules Microsoft.Insights/actionGroups Microsoft.OperationalInsights/workspaces |
Log Analytics Workspace, Application Insights, Alerts, Notification Service |
| Azure AI Search | Microsoft.Search/searchServices | - |
| Cosmos DB | Microsoft.DocumentDB/databaseAccounts | - |
| Event Hubs | Microsoft.EventHub/namespaces | - |
| Key Vault | Microsoft.KeyVault/vaults | - |
| SQL DB | Microsoft.Sql/servers | - |
| Storage | Microsoft.Storage/storageAccounts | - |
Note
Refer to the respective private link resource documentation for information on currently unsupported scenarios.
Limitations of a network security perimeter
Regional limitations
Network security perimeter is currently available in all Azure public cloud regions. However, while enabling access logs for network security perimeter, the Log Analytics workspace to be associated with the network security perimeter needs to be located in one of the Azure Monitor supported regions. Currently, those regions are East US, East US 2, North Central US, South Central US, West US, and West US 2.
Note
For PaaS resource logs, use Storage and Event Hub as the log destination for any region associated to the same perimeter.
Scale limitations
Network security perimeter functionality can be used to support deployments of PaaS resources with common public network controls with following scale limitations:
| Limitation | Description |
|---|---|
| Number of network security perimeters | Supported up to 100 as recommended limit per subscription. |
| Profiles per network security perimeters | Supported up to 200 as recommended limit. |
| Number of rule elements per profile | Supported up to 200 as hard limit. |
| Number of PaaS resources across subscriptions associated with the same network security perimeter | Supported up to 1000 as recommended limit. |
Other limitations
Network security perimeter has other limitations as follows:
| Limitation/Issue | Description |
|---|---|
| Resource group move operation cannot be performed if multiple network security perimeters are present | If there are multiple network security perimeters present in the same resource group, then the network security perimeter cannot be moved across resource groups/subscriptions. |
| Associations must be removed before deleting network security perimeter | Forced delete option is currently unavailable. Thus all associations must be removed before deleting a network security perimeter. Only remove associations after taking precautions for allowing access previously controlled by network security perimeter. |
| Resource names cannot be longer than 44 characters to support network security perimeter | The network security perimeter resource association created from the Azure portal has the format {resourceName}-{perimeter-guid}. To align with the requirement name field can't have more than 80 characters, resources names would have to be limited to 44 characters. |
| Service endpoint traffic is not supported. | It's recommended to use private endpoints for IaaS to PaaS communication. Currently, service endpoint traffic can be denied even when an inbound rule allows 0.0.0.0/0. |
Note
Refer to individual PaaS documentation for respective limitations for each service.