Korrigieren von Defender for Endpoint-Fehlkonfigurationen (ohne Agent)
Microsoft Defender for Cloud ist nativ in Defender for Endpoint integriert, um Erkennung und Reaktion am Endpunkt (EDR) für Computer bereitzustellen, die mit Defender for Cloud verbunden sind.
Im Rahmen dieser integrierten EDR-Funktionen überprüft Defender for Cloud Computer agentlos, um zu beurteilen, ob sie eine EDR-Lösung ausführen. Darüber hinaus überprüft Defender for Servers agentlos Computer, die Defender for Endpoint als EDR verwenden, mit Sicherheitsüberprüfungen, die bewerten, ob Defender for Endpoint ordnungsgemäß konfiguriert ist. Zu den Überprüfungen gehören:
Both full and quick scans are out of 7 daysSignature out of dateAnti-virus is off or partially configured
Wenn Fehlkonfigurationen gefunden werden, gibt Defender for Cloud Empfehlungen, um sie zu beheben. In diesem Artikel wird beschrieben, wie Sie diese Empfehlungen umsetzen.
Hinweis
- Defender for Cloud verwendet die Überprüfung ohne Agent, um EDR-Einstellungen zu bewerten.
- Die Überprüfung ohne Agent ersetzt den Log Analytics-Agent (auch bekannt als Microsoft Monitoring Agent (MMA)), der zuvor zum Sammeln von Computerdaten verwendet wurde.
- Der MMA wird eingestellt. Die Überprüfung mit dem MMA wird seit November 2024 nicht mehr unterstützt.
Voraussetzungen
| Anforderung | Details |
|---|---|
| Planen |
Defender for Cloud muss im Azure-Abonnement verfügbar sein, und einer dieser Pläne muss aktiviert sein: - Defender für Server-Plan 2 - Defender Cloud Security Posture Management (CSPM) |
| Überprüfung ohne Agent | Die Überprüfung ohne Agent für Computer muss aktiviert sein. Sie ist in den Plänen standardmäßig aktiviert, aber wenn Sie sie manuell aktivieren müssen, folgen Sie diesen Anweisungen. |
| Computer | Defender for Endpoint muss als EDR-Lösung auf virtuellen Computern ausgeführt werden. |
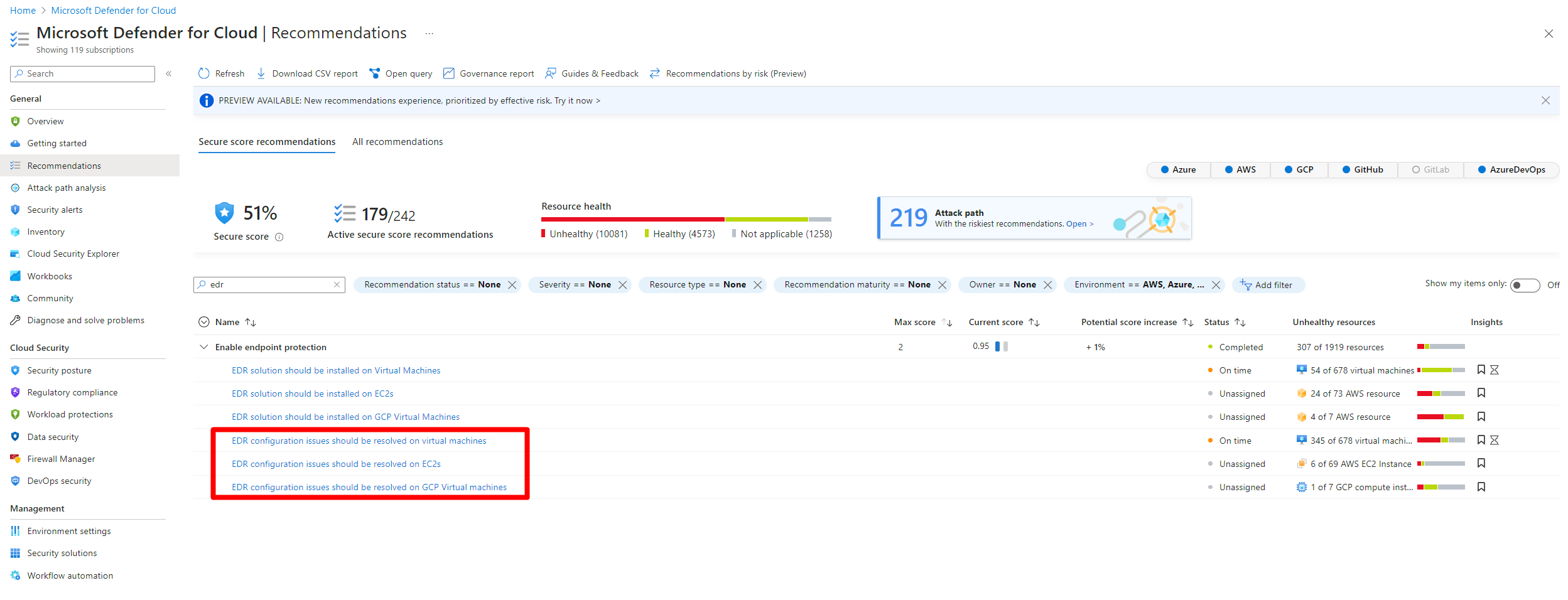
Untersuchen von Empfehlungen zu Fehlkonfigurationen
Unter Defender for Cloud>Empfehlungen.
Suchen Sie nach einer der folgenden Empfehlungen, und wählen Sie eine aus:
EDR configuration issues should be resolved on virtual machinesEDR configuration issues should be resolved on EC2sEDR configuration issues should be resolved on GCP virtual machines
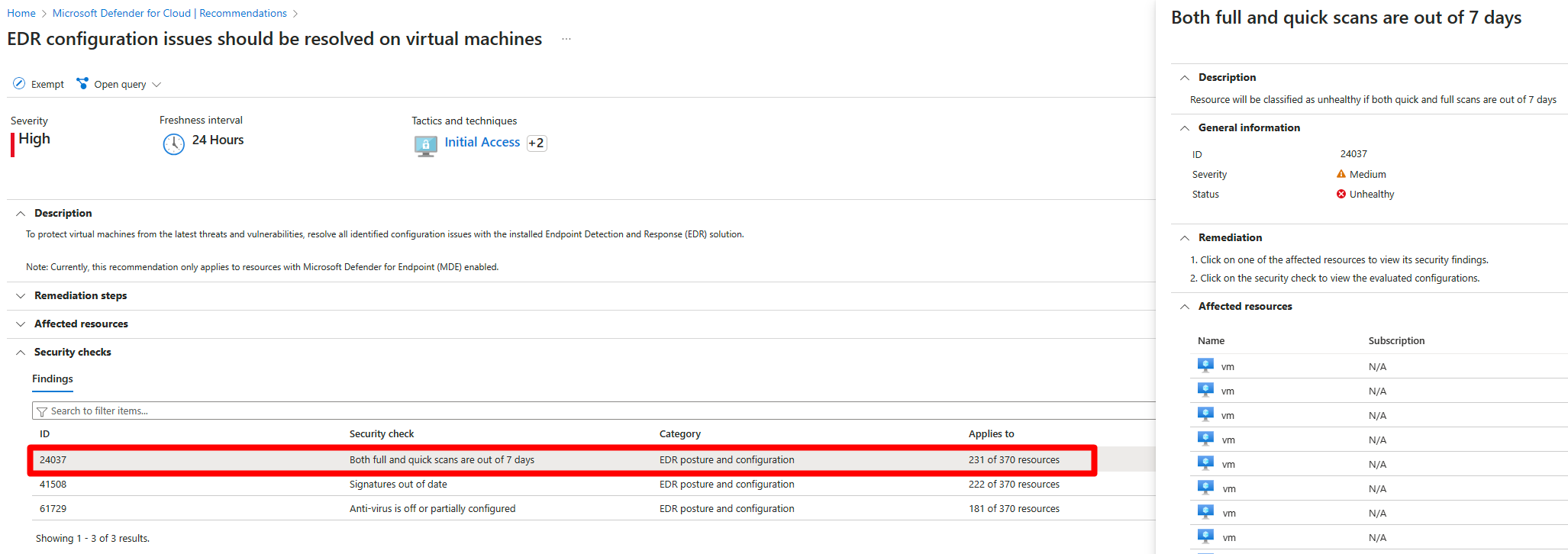
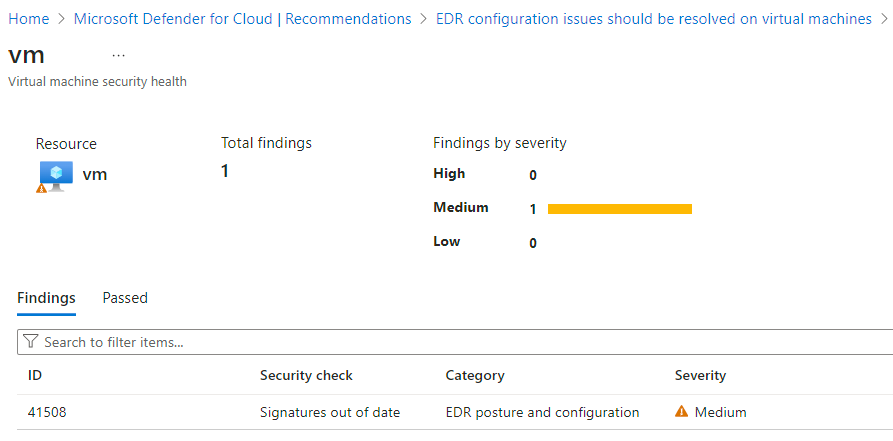
Wählen Sie jede der Sicherheitsprüfungen aus, um die betroffenen Ressourcen zu überprüfen.
Erweitern Sie den Abschnitt Betroffene Ressourcen.
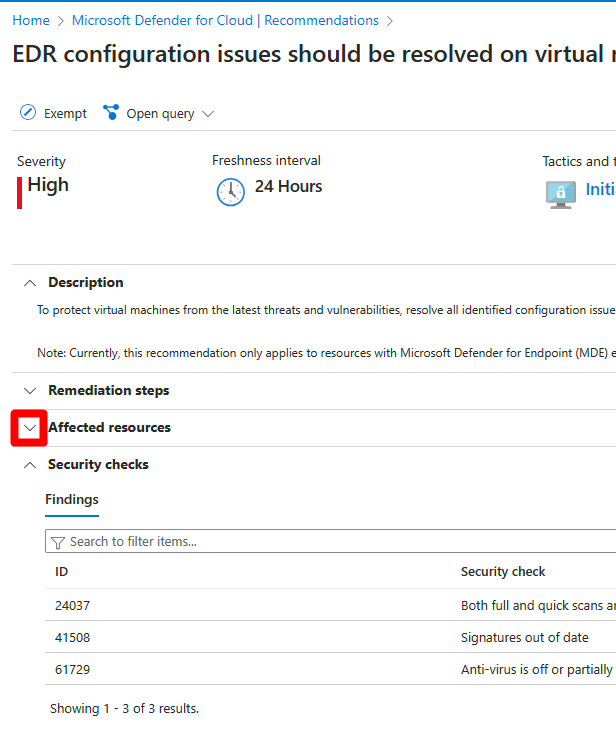
Führen Sie einen Drilldown in die Sicherheitsüberprüfung durch, und führen Sie die Korrekturschritte aus.
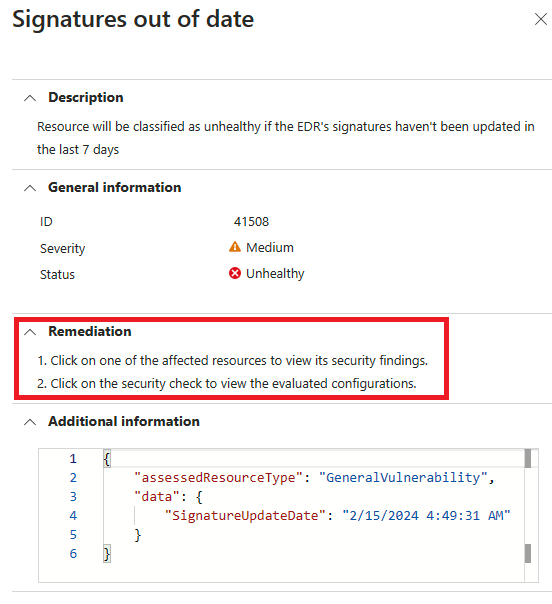
Nach Abschluss des Vorgangs kann es bis zu 24 Stunden dauern, bis Ihr Computer auf der Registerkarte Fehlerfreie Ressourcen angezeigt wird.
Zugehöriger Inhalt
Stellen Sie sicher, dass Computer eine EDR-Lösung konfiguriert haben.