Windows 365 architektura
Windows 365 poskytuje model licencí na uživatele za měsíc tím, že hostuje cloudové počítače jménem zákazníků v Microsoft Azure. V tomto modelu není potřeba brát v úvahu úložiště, architekturu výpočetní infrastruktury ani náklady. Architektura Windows 365 také umožňuje využít vaše stávající investice do sítí a zabezpečení Azure. Každý Cloud PC se zřizuje podle konfigurace, kterou definujete v části Windows 365 Centra pro správu Microsoft Intune.
Připojení k virtuální síti
Každý cloudový počítač má v Microsoft Azure virtuální síťovou kartu. Máte dvě možnosti správy síťových adaptérů:
- Pokud používáte Microsoft Entra připojení a síť hostované Microsoftem, nemusíte mít předplatné Azure ani spravovat síťovou kartu.
- Pokud si vytvoříte vlastní síť a použijete síťové připojení Azure (ANC), síťové karty vytvoří Windows 365 ve vašem předplatném Azure.
Síťové karty jsou připojené k azure Virtual Network na základě konfigurace síťového připojení Azure (ANC).
Windows 365 se podporuje v mnoha oblastech Azure. Můžete řídit, která oblast Azure se používá, dvěma způsoby:
- Výběrem sítě hostované Microsoftem a oblasti Azure.
- Výběrem virtuální sítě Azure z předplatného Azure při vytváření ANC.
Oblast virtuální sítě Azure určuje, kde se cloudový počítač vytvoří a hostuje.
Pokud používáte vlastní virtuální síť, můžete rozšířit přístup mezi vašimi aktuálními oblastmi Azure do dalších oblastí Azure podporovaných službou Windows 365. Pokud se chcete rozšířit do dalších oblastí, můžete použít partnerský vztah virtuálních sítí Azure nebo Virtual WAN.
Pomocí vlastní virtuální sítě Azure vám Windows 365 umožňuje používat funkce zabezpečení a směrování Virtual Network, mezi které patří:
- Skupiny zabezpečení sítě Azure
- Směrování definované uživatelem
- Azure Firewall
- Síťová virtuální zařízení
Tip
V případě filtrování webů a ochrany sítě pro cloudové počítače zvažte použití funkcí Ochrana sítě a Webová ochrana Microsoft Defender for Endpoint. Tyto funkce je možné nasadit napříč fyzickými i virtuálními koncovými body pomocí centra pro správu Microsoft Intune.
integrace Microsoft Intune
Microsoft Intune slouží ke správě všech cloudových počítačů. Microsoft Intune a přidružené součásti systému Windows mají různé síťové koncové body, které musí být povoleny prostřednictvím Virtual Network. Pokud ke správě těchto typů zařízení nepoužíváte Microsoft Intune, koncové body Apple a Android se můžou bezpečně ignorovat.
Tip
Nezapomeňte povolit přístup ke službě Windows Notification Services (WNS). Pokud je přístup blokovaný, nemusíte si okamžitě všimnout dopadu. Služba WNS ale umožňuje Microsoft Intune aktivovat akce na koncových bodech Windows okamžitě místo čekání na normální intervaly dotazování zásad na těchto zařízeních nebo dotazování zásad při spouštění nebo přihlašování. Služba WNS doporučuje přímé připojení z klienta Windows ke službě WNS.
Stačí udělit přístup jenom k podmnožině koncových bodů na základě umístění vašeho Microsoft Intune tenanta. Pokud chcete zjistit umístění tenanta (nebo jednotku škálování Azure (ASU)), přihlaste se do centra pro správu Microsoft Intune a zvolte Podrobnosti o správě>tenanta. V části Umístění tenanta se zobrazí něco podobného jako "Severní Amerika 0501" nebo "Evropa 0202". Řádky v dokumentaci Microsoft Intune se liší podle zeměpisné oblasti. Oblasti jsou označeny prvními dvěma písmeny v názvech (na = Severní Amerika, eu = Evropa, ap = Asie a Tichomoří). Vzhledem k tomu, že se tenanti můžou přemísťovat v rámci oblasti, je nejlepší povolit přístup k celé oblasti místo konkrétního koncového bodu v této oblasti.
Další informace o Microsoft Intune oblastech služby a informacích o umístění dat najdete v tématu Ukládání a zpracování dat v Intune.
Služby identit
Windows 365 používá Microsoft Entra ID i místní Active Directory Doménové služby (AD DS). Microsoft Entra ID poskytuje:
- Ověřování uživatelů pro Windows 365 (stejně jako u jakékoli jiné služby Microsoft 365).
- Služby identit zařízení pro Microsoft Intune prostřednictvím Microsoft Entra hybridního připojení nebo Microsoft Entra připojení.
Při konfiguraci cloudových počítačů tak, aby používaly Microsoft Entra hybridní připojení, služba AD DS poskytuje:
- Připojení k místní doméně pro cloudové počítače
- Ověřování uživatelů pro připojení RDP (Remote Desktop Protocol).
Když konfigurujete cloudové počítače tak, aby používaly Microsoft Entra připojení, Microsoft Entra ID poskytuje:
- Mechanismus připojení k doméně pro cloudové počítače.
- Ověřování uživatelů pro připojení RDP.
Další informace o tom, jak služby identit ovlivňují nasazení, správu a používání cloudových počítačů, najdete v tématu Identita a ověřování.
Microsoft Entra ID
Microsoft Entra ID poskytuje ověřování a autorizaci uživatelů pro webový portál Windows 365 i pro klientské aplikace Vzdálené plochy. Obě podporují moderní ověřování, což znamená, Microsoft Entra podmíněný přístup je možné integrovat, aby poskytovaly:
- vícefaktorové ověřování
- omezení na základě umístění
- správa rizik přihlašování
- omezení relací, včetně:
- Frekvence přihlašování klientů Vzdálené plochy a webového portálu Windows 365
- trvalost souborů cookie pro webový portál Windows 365
- ovládací prvky dodržování předpisů zařízením
Další informace o používání Microsoft Entra podmíněného přístupu s Windows 365 najdete v tématu Nastavení zásad podmíněného přístupu.
Active Directory Domain Services
Windows 365 cloudové počítače můžou být Microsoft Entra připojené k hybridnímu nebo Microsoft Entra připojené. Pokud používáte Microsoft Entra hybridní připojení, musí se cloudové počítače připojit k doméně služby AD DS. Tato doména se musí synchronizovat s Microsoft Entra ID. Řadiče domény domény můžou být hostované v Azure nebo místně. Pokud je hostované místně, musí se z Azure navázat připojení k místnímu prostředí. Připojení může mít podobu Azure ExpressRoute nebo vpn typu site-to-site. Další informace o navázání hybridního síťového připojení najdete v tématu Implementace zabezpečené hybridní sítě. Připojení musí umožňovat komunikaci z cloudových počítačů s řadiči domény vyžadovanými službou Active Directory. Další informace najdete v tématu Konfigurace brány firewall pro doménu AD a vztahy důvěryhodnosti.
Možnosti připojení uživatelů
Připojení ke cloudovým počítačům zajišťuje Služba Azure Virtual Desktop. Ke cloudovým počítačům se nenavazují žádná příchozí připojení přímo z internetu. Místo toho se připojení navazují z:
- Cloud PC do koncových bodů služby Azure Virtual Desktop.
- Klienti vzdálené plochy pro koncové body služby Azure Virtual Desktop.
Další informace o těchto portech najdete v seznamu požadovaných adres URL služby Azure Virtual Desktop. Pokud chcete usnadnit konfiguraci ovládacích prvků zabezpečení sítě, použijte k identitě těchto koncových bodů značky služeb pro Azure Virtual Desktop. Další informace o značkách služeb Azure najdete v tématu Přehled značek služeb Azure.
Pro vytváření těchto připojení není nutné konfigurovat cloudové počítače. Windows 365 bezproblémově integruje komponenty připojení ke službě Azure Virtual Desktop do galerie nebo vlastních imagí.
Další informace o síťové architektuře služby Azure Virtual Desktop najdete v tématu Principy síťového připojení služby Azure Virtual Desktop.
Windows 365 cloudové počítače nepodporují zprostředkovatele připojení třetích stran.
Architektura hostovaná jménem
Architektura hostovaná jménem umožňuje službám Microsoftu po delegování odpovídajících a vymezených oprávnění k virtuální síti vlastníkem předplatného připojit hostované služby Azure k předplatnému zákazníka. Tento model připojení umožňuje službě Microsoftu poskytovat služby typu software jako služba a služby licencované uživatelem na rozdíl od standardních služeb založených na spotřebě.
Následující diagramy znázorňují logickou architekturu pro konfiguraci Microsoft Entra připojení pomocí sítě hostované Microsoftem, konfiguraci Microsoft Entra připojení pomocí síťového připojení zákazníka (přineste si vlastní síť) a konfiguraci Microsoft Entra hybridního připojení pomocí ANC.
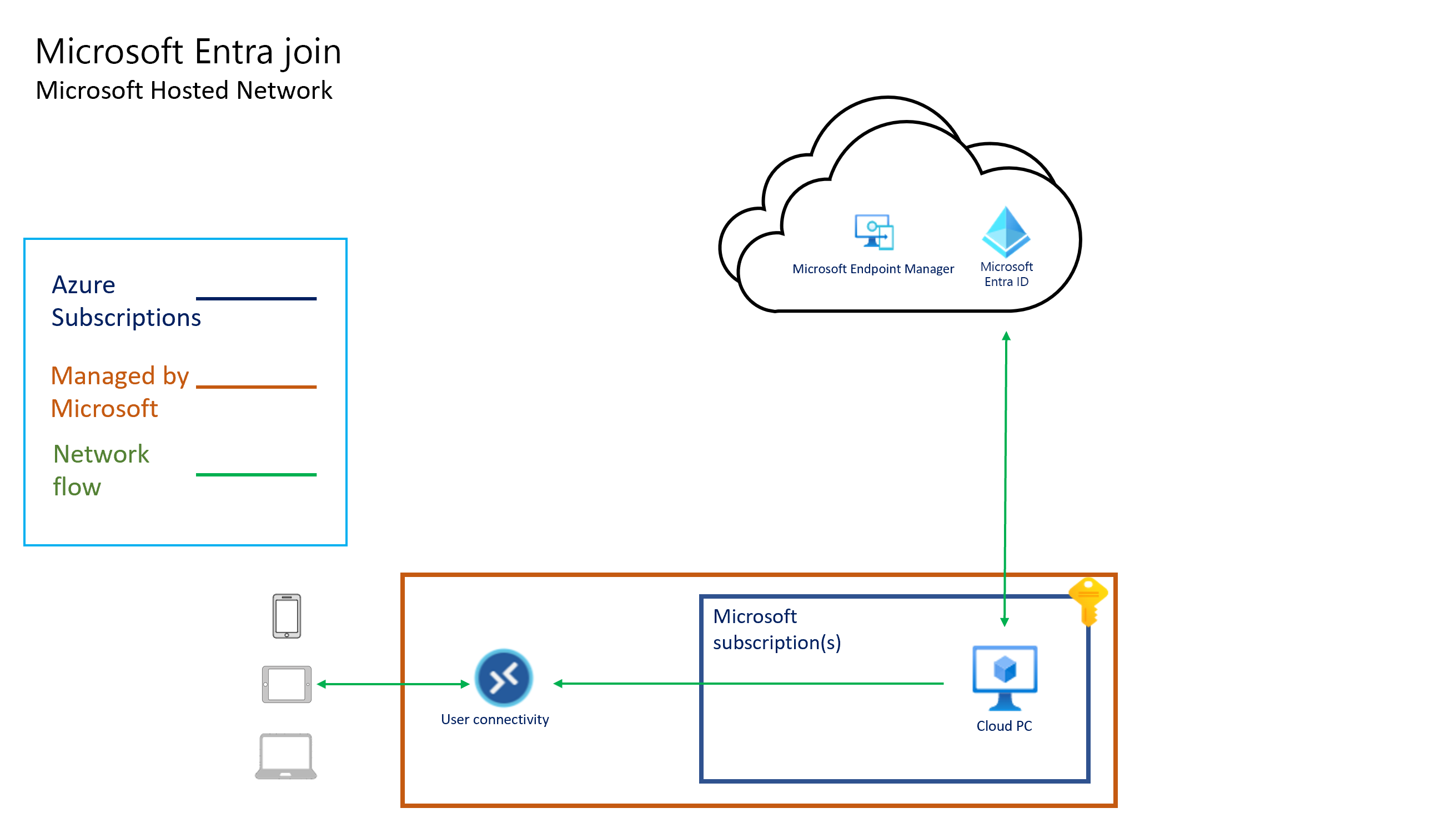
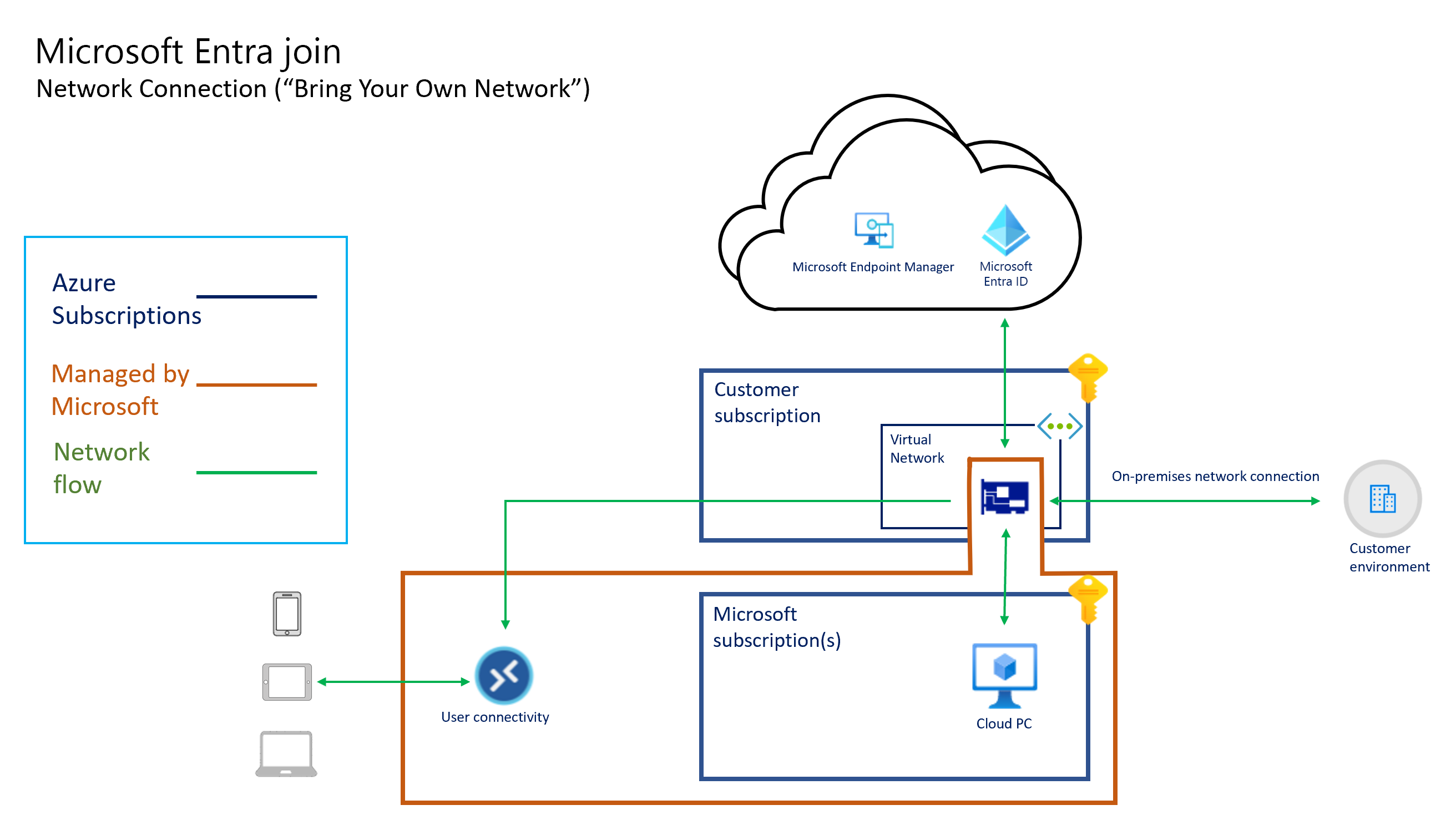
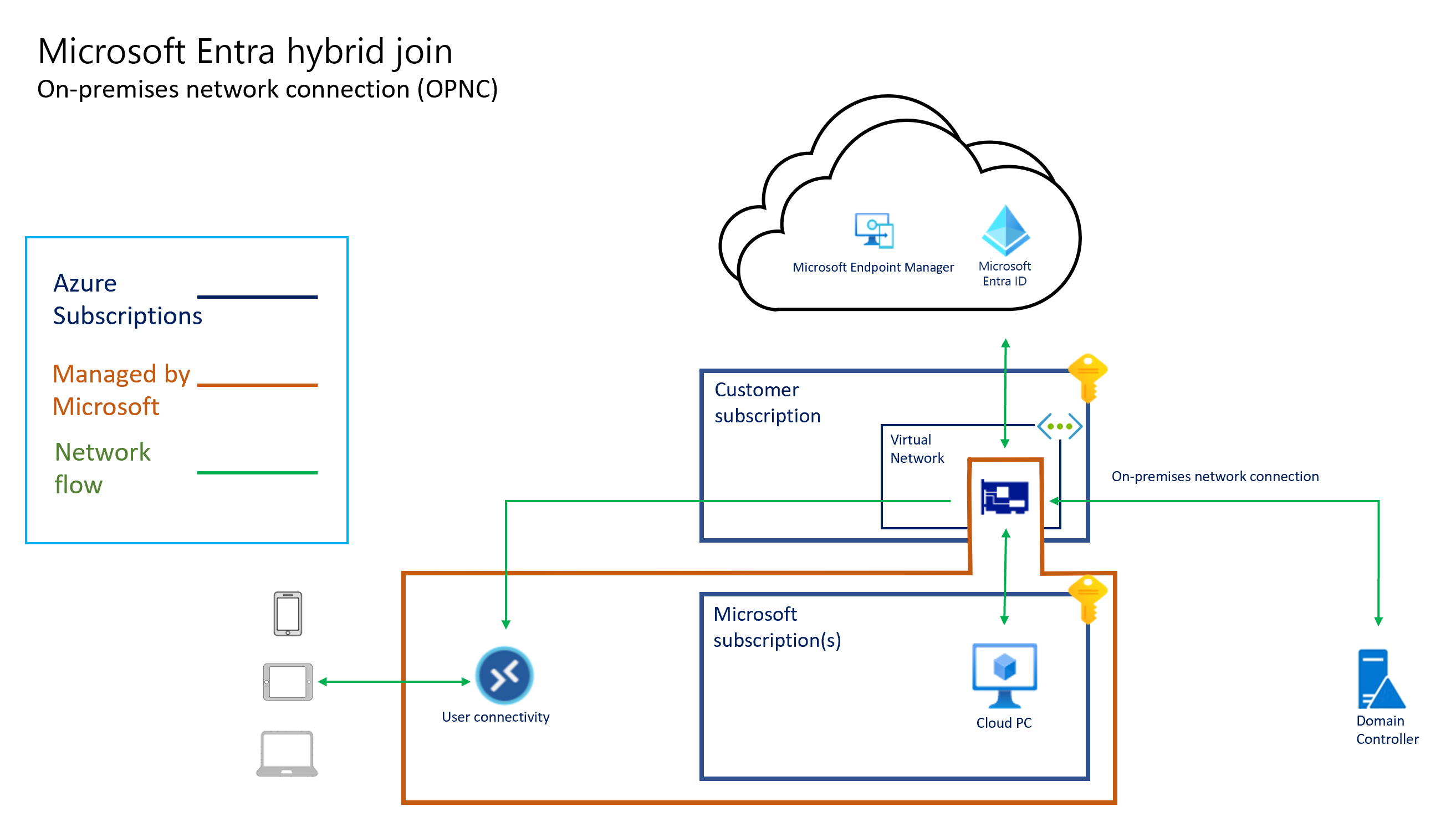
Veškeré připojení ke cloudovým počítačům zajišťuje karta virtuálního síťového rozhraní. Architektura hostovaná jménem znamená, že cloudové počítače existují v předplatném vlastněné Microsoftem. Proto microsoftu vznikají náklady na provoz a správu této infrastruktury.
Windows 365 spravuje kapacitu a dostupnost v oblasti v předplatných Windows 365. Windows 365 určuje velikost a typ virtuálního počítače na základě licence, kterou uživateli přiřadíte. Windows 365 určuje oblast Azure pro hostování cloudových počítačů na základě virtuální sítě, kterou vyberete při vytváření místního síťového připojení.
Windows 365 je v souladu se zásadami ochrany dat Microsoftu 365. Zákaznická data v rámci podnikových cloudových služeb Microsoftu jsou chráněná různými technologiemi a procesy:
- Různé formy šifrování.
- Logicky izolované od ostatních tenantů.
- Přístupná omezené, řízené a zabezpečené skupině uživatelů z konkrétních klientů.
- Zabezpečeno pro přístup pomocí řízení přístupu na základě role.
- Replikuje se na více serverů, koncových bodů úložiště a datových center kvůli redundanci.
- Monitoruje se neoprávněný přístup, nadměrná spotřeba prostředků a dostupnost.
Další informace o šifrování Windows 365 Cloud PC najdete v tématu Šifrování dat v Windows 365.