搜捕勒索軟體
適用於:
- Microsoft Defender XDR
勒索軟體從影響個別計算機用戶的簡單商品惡意代碼快速演進,成為嚴重影響產業和政府機構的企業威脅。 雖然 Microsoft Defender 全面偵測回應 提供許多功能來偵測和封鎖勒索軟體和相關聯的入侵活動,但針對入侵徵兆執行主動式檢查有助於保護您的網路。
使用 Microsoft Defender 全面偵測回應 中的進階搜捕,您可以建立查詢來找出與勒索軟體活動相關聯的個別成品。 您也可以執行更複雜的查詢,以尋找活動徵兆並權衡這些徵兆,以尋找需要立即注意的裝置。
勒索軟體活動的徵兆
Microsoft 安全性研究人員在許多由複雜入侵者所啟動的勒索軟體活動中觀察到各種常見但細微的成品。 這些符號大多牽涉到使用系統工具來準備加密、防止偵測,以及清除鑑識辨識項。
| 勒索軟體活動 | 一般工具 | Intent |
|---|---|---|
| 停止進程 | taskkill.exe,net stop | 確保各種應用程式不會鎖定以加密為目標的檔案。 |
| 關閉服務 | sc.exe | - 確保各種應用程式不會鎖定以加密為目標的檔案。 - 防止安全性軟體中斷加密和其他勒索軟體活動。 - 停止備份軟體建立可復原的複本。 |
| 刪除記錄和檔案 | cipher.exe、 wevtutil、 fsutil.exe | 拿掉鑑識辨識項。 |
| 刪除陰影複製 | vsadmin.exe、 wmic.exe | 拿掉可用來復原加密檔案的磁碟驅動器陰影複製。 |
| 刪除和停止備份 | wbadmin.exe | 刪除現有的備份並停止排程的備份工作,防止加密后復原。 |
| 修改開機設定 | bcdedit.exe | 關閉加密程式可能造成的開機失敗之後的警告和自動修復。 |
| 關閉復原工具 | schtasks.exe、 regedit.exe、 | 關閉 [系統還原] 和其他系統復原選項。 |
檢查勒索軟體活動的個別徵兆
構成勒索軟體行為的許多活動,包括上一節所述的活動,可能是良性的。 使用下列查詢尋找勒索軟體時,請執行多個查詢來檢查相同的裝置是否呈現各種可能勒索軟體活動徵兆。
使用 taskkill.exe 停止多個進程
此查詢會檢查是否嘗試使用taskkill.exe公用程式停止至少10 個不同的 進程。 執行查詢
// Find attempts to stop processes using taskkill.exe
DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "taskkill.exe"
| summarize taskKillCount = dcount(ProcessCommandLine), TaskKillList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 2m)
| where taskKillCount > 10
使用 net stop 停止進程
此查詢會檢查是否嘗試使用 net stop 命令停止至少 10 個不同的進程。 執行查詢
// Find attempts to stop processes using net stop
DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "net.exe" and ProcessCommandLine has "stop"
| summarize netStopCount = dcount(ProcessCommandLine), NetStopList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 2m)
| where netStopCount > 10
使用cipher.exe 刪除多個磁碟驅動器上的數據
此查詢會檢查是否嘗試使用 cipher.exe刪除多個磁碟驅動器上的數據。 勒索軟體通常會執行此活動,以防止在加密后復原數據。 執行查詢
// Look for cipher.exe deleting data from multiple drives
DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "cipher.exe"
// cipher.exe /w flag used for deleting data
| where ProcessCommandLine has "/w"
| summarize CipherCount = dcount(ProcessCommandLine),
CipherList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 1m)
// cipher.exe accessing multiple drives in a short timeframe
| where CipherCount > 1
使用 wevtutil 從事件記錄檔中清除鑑識辨識辨識項
此查詢會檢查是否嘗試使用 wevtutil 從事件記錄檔中清除至少 10 個記錄專案。 執行查詢
// Look for use of wevtutil to clear multiple logs
DeviceProcessEvents
| where Timestamp > ago(1d)
| where ProcessCommandLine has "WEVTUTIL" and ProcessCommandLine has "CL"
| summarize LogClearCount = dcount(ProcessCommandLine), ClearedLogList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 5m)
| where LogClearCount > 10
使用 sc.exe 關閉服務
此查詢會檢查是否嘗試使用sc.exe關閉至少10 個 現有的服務。 執行查詢
// Look for sc.exe disabling services
DeviceProcessEvents
| where Timestamp > ago(1d)
| where ProcessCommandLine has "sc" and ProcessCommandLine has "config" and ProcessCommandLine has "disabled"
| summarize ScDisableCount = dcount(ProcessCommandLine), ScDisableList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 5m)
| where ScDisableCount > 10
關閉系統還原
此查詢會識別停止系統還原並防止系統建立還原點的嘗試,其可用來復原勒索軟體所加密的數據。 執行查詢
DeviceProcessEvents
//Pivoting for rundll32
| where InitiatingProcessFileName =~ 'rundll32.exe'
//Looking for empty command line
and InitiatingProcessCommandLine !contains " " and InitiatingProcessCommandLine != ""
//Looking for schtasks.exe as the created process
and FileName in~ ('schtasks.exe')
//Disabling system restore
and ProcessCommandLine has 'Change' and ProcessCommandLine has 'SystemRestore'
and ProcessCommandLine has 'disable'
備份刪除
此查詢會識別在加密之前使用 wmic.exe 刪除陰影複製快照集。 執行查詢
DeviceProcessEvents
| where FileName =~ "wmic.exe"
| where ProcessCommandLine has "shadowcopy" and ProcessCommandLine has "delete"
| project DeviceId, Timestamp, InitiatingProcessFileName, FileName,
ProcessCommandLine, InitiatingProcessIntegrityLevel, InitiatingProcessParentFileName
檢查勒索軟體活動的多個徵兆
除了個別執行數個查詢,您也可以使用完整的查詢來檢查勒索軟體活動的多個徵兆,以識別受影響的裝置。 下列合併查詢:
- 同時尋找勒索軟體活動的相對具體和細微徵兆
- 權衡這些符號是否存在
- 識別有較高機率成為勒索軟體目標的裝置
執行時,此合併查詢會傳回已呈現多個攻擊徵兆的裝置清單。 也會顯示每種勒索軟體活動的計數。 若要執行此合併查詢,請將它直接複製到 進階搜捕查詢編輯器。
// Find attempts to stop processes using taskkill.exe
let taskKill = DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "taskkill.exe"
| summarize taskKillCount = dcount(ProcessCommandLine), TaskKillList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 2m)
| where taskKillCount > 10;
// Find attempts to stop processes using net stop
let netStop = DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "net.exe" and ProcessCommandLine has "stop"
| summarize netStopCount = dcount(ProcessCommandLine), NetStopList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 2m)
| where netStopCount > 10;
// Look for cipher.exe deleting data from multiple drives
let cipher = DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "cipher.exe"
// cipher.exe /w flag used for deleting data
| where ProcessCommandLine has "/w"
| summarize CipherCount = dcount(ProcessCommandLine),
CipherList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 1m)
// cipher.exe accessing multiple drives in a short timeframe
| where CipherCount > 1;
// Look for use of wevtutil to clear multiple logs
let wevtutilClear = DeviceProcessEvents
| where Timestamp > ago(1d)
| where ProcessCommandLine has "WEVTUTIL" and ProcessCommandLine has "CL"
| summarize LogClearCount = dcount(ProcessCommandLine), ClearedLogList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 5m)
| where LogClearCount > 10;
// Look for sc.exe disabling services
let scDisable = DeviceProcessEvents
| where Timestamp > ago(1d)
| where ProcessCommandLine has "sc" and ProcessCommandLine has "config" and ProcessCommandLine has "disabled"
| summarize ScDisableCount = dcount(ProcessCommandLine), ScDisableList = make_set(ProcessCommandLine) by DeviceId, bin(Timestamp, 5m)
| where ScDisableCount > 10;
// Main query for counting and aggregating evidence
DeviceProcessEvents
| where Timestamp > ago(1d)
| where FileName =~ "vssadmin.exe" and ProcessCommandLine has_any("list shadows", "delete shadows")
or FileName =~ "fsutil.exe" and ProcessCommandLine has "usn" and ProcessCommandLine has "deletejournal"
or ProcessCommandLine has("bcdedit") and ProcessCommandLine has_any("recoveryenabled no", "bootstatuspolicy ignoreallfailures")
or ProcessCommandLine has "wbadmin" and ProcessCommandLine has "delete" and ProcessCommandLine has_any("backup", "catalog", "systemstatebackup")
or (ProcessCommandLine has "wevtutil" and ProcessCommandLine has "cl")
or (ProcessCommandLine has "wmic" and ProcessCommandLine has "shadowcopy delete")
or (ProcessCommandLine has "sc" and ProcessCommandLine has "config" and ProcessCommandLine has "disabled")
| extend Bcdedit = iff(ProcessCommandLine has "bcdedit" and ProcessCommandLine has_any("recoveryenabled no", "bootstatuspolicy ignoreallfailures"), 1, 0)
| extend ShadowCopyDelete = iff (ProcessCommandLine has "shadowcopy delete", 1, 0)
| extend VssAdminShadows = iff(ProcessCommandLine has "vssadmin" and ProcessCommandLine has_any("list shadows", "delete shadows"), 1, 0)
| extend Wbadmin = iff(ProcessCommandLine has "wbadmin" and ProcessCommandLine has "delete" and ProcessCommandLine has_any("backup", "catalog", "systemstatebackup"), 1,0)
| extend Fsutil = iff(ProcessCommandLine has "fsutil" and ProcessCommandLine has "usn" and ProcessCommandLine has "deletejournal", 1, 0)
| summarize FirstActivity = min(Timestamp), ReportId = any(ReportId), Commands = make_set(ProcessCommandLine) by DeviceId, Fsutil, Wbadmin, ShadowCopyDelete, Bcdedit, VssAdminShadows, bin(Timestamp, 6h)
// Joining extra evidence
| join kind=leftouter (wevtutilClear) on $left.DeviceId == $right.DeviceId
| join kind=leftouter (cipher) on $left.DeviceId == $right.DeviceId
| join kind=leftouter (netStop) on $left.DeviceId == $right.DeviceId
| join kind=leftouter (taskKill) on $left.DeviceId == $right.DeviceId
| join kind=leftouter (scDisable) on $left.DeviceId == $right.DeviceId
| extend WevtutilUse = iff(LogClearCount > 10, 1, 0)
| extend CipherUse = iff(CipherCount > 1, 1, 0)
| extend NetStopUse = iff(netStopCount > 10, 1, 0)
| extend TaskkillUse = iff(taskKillCount > 10, 1, 0)
| extend ScDisableUse = iff(ScDisableCount > 10, 1, 0)
// Adding up all evidence
| mv-expand CommandList = NetStopList, TaskKillList, ClearedLogList, CipherList, Commands, ScDisableList
// Format results
| summarize BcdEdit = iff(make_set(Bcdedit) contains "1" , 1, 0), NetStop10PlusCommands = iff(make_set(NetStopUse) contains "1", 1, 0), Wevtutil10PlusLogsCleared = iff(make_set(WevtutilUse) contains "1", 1, 0),
CipherMultipleDrives = iff(make_set(CipherUse) contains "1", 1, 0), Fsutil = iff(make_set(Fsutil) contains "1", 1, 0), ShadowCopyDelete = iff(make_set(ShadowCopyDelete) contains "1", 1, 0),
Wbadmin = iff(make_set(Wbadmin) contains "1", 1, 0), TaskKill10PlusCommand = iff(make_set(TaskkillUse) contains "1", 1, 0), VssAdminShadow = iff(make_set(VssAdminShadows) contains "1", 1, 0),
ScDisable = iff(make_set(ScDisableUse) contains "1", 1, 0), TotalEvidenceCount = count(CommandList), EvidenceList = make_set(Commands), StartofBehavior = min(FirstActivity) by DeviceId, bin(Timestamp, 1d)
| extend UniqueEvidenceCount = BcdEdit + NetStop10PlusCommands + Wevtutil10PlusLogsCleared + CipherMultipleDrives + Wbadmin + Fsutil + TaskKill10PlusCommand + VssAdminShadow + ScDisable + ShadowCopyDelete
| where UniqueEvidenceCount > 2
瞭解並調整查詢結果
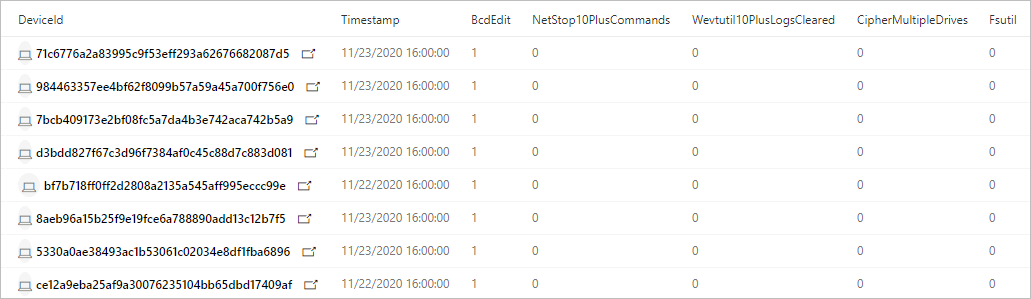
合併查詢會傳回下列結果:
DeviceId— 識別受影響的裝置
TimeStamp— 第一次在裝置上觀察到勒索軟體活動的任何徵兆
特定的活動徵兆— 多個數據行中顯示的每個符號計數,例如 BcdEdit 或 FsUtil
TotalEvidenceCount— 觀察到的符號數目
UniqueEvidenceCount— 觀察到的符號類型數目
顯示受影響裝置和各種勒索軟體活動徵兆計數的查詢結果
根據預設,查詢結果只會列出具有兩種以上勒索軟體活動的裝置。 若要查看具有勒索軟體活動任何標誌的所有裝置,請修改下列 where 運算符,並將數字設定為零 (0) 。 若要查看較少的裝置,請設定較高的數位。
| where UniqueEvidenceCount > 2
更多勒索軟體資源
Microsoft 的重要資訊:
- 勒索軟體的威脅不斷增加,2021 年 7 月 20 日 Microsoft On The Issues 的部落格文章
- 人為操作勒索軟體
- 快速部署勒索軟體防護
- 2021 Microsoft 數位防禦報告 (請參閱第 10-19 頁)
- 勒索軟體:Microsoft Defender 入口網站中普遍且持續的威脅威脅分析報告
Microsoft 365:
- 為您的 Microsoft 365 租用戶部署勒索軟體防護
- 使用 Azure 和 Microsoft 365 最大化勒索軟體復原能力
- 勒索軟體事件回應劇本
- 惡意程式碼與勒索軟體防護
- 保護您的 Windows 電腦免於勒索軟體
- 在 SharePoint Online 中處理勒索軟體
- Microsoft Defender 入口網站中勒索軟體的威脅分析報告
Microsoft Azure:
- 針對勒索軟體攻擊的 Azure 防護
- 使用 Azure 和 Microsoft 365 最大化勒索軟體復原能力
- 防護勒索軟體的備份與還原計劃
- 使用 Microsoft Azure 備份,協助防護勒索軟體 (26 分鐘的影片)
- 從系統性身分識別洩露中復原
- Microsoft Sentinel 中的進階多階段攻擊偵測
- Microsoft Sentinel 中勒索軟體的融合偵測
Microsoft 雲端 App 安全性:
Microsoft 安全性小組部落格文章:
對抗人為操作勒索軟體的指南: 第 1 部分( 2021 年 9 月)
Microsoft 的偵測和回應團隊 (DART) 進行勒索軟體事件調查的主要步驟。
對抗人為操作勒索軟體的指南: 第 2 部分 (2021 年 9 月)
建議和最佳作法。
透過了解網路安全性風險以更具彈性: 第 4 部分—瀏覽目前的威脅 (2021 年 5 月)
請參閱勒索軟體章節。
人為操作的勒索軟體攻擊: 可預防的災難 (2020 年 5 月)
包括實際攻擊的攻擊鏈分析。
提示
想要深入了解? Engage 技術社群中的 Microsoft 安全性社群:Microsoft Defender 全面偵測回應 技術社群。