Troubleshoot problems installing the private network connector
Microsoft Entra private network connector is an internal domain component that uses outbound connections to establish the connectivity from the cloud available endpoint to the internal domain. The connector is used by both Microsoft Entra Private Access and Microsoft Entra application proxy.
General problem areas with connector installation
When the installation of a connector fails, the root cause is usually one of the following areas. As a precursor to any troubleshooting, be sure to reboot the connector.
- Connectivity – to complete a successful installation, the new connector needs to register and establish future trust properties. Trust is established by connecting to the Microsoft Entra application proxy cloud service.
- Trust Establishment – the new connector creates a self-signed cert and registers to the cloud service.
- Authentication of the admin – during installation, the user must provide admin credentials to complete the connector installation.
Note
The connector installation logs can be found in the %TEMP% folder and can help provide additional information on what is causing an installation failure.
Verify connectivity to the cloud application proxy service and Microsoft sign in page
Objective: Verify that the connector machine can connect to the application proxy registration endpoint and the Microsoft sign-in page.
On the connector server, run a port test by using telnet or other port testing tool to verify that ports 443 and 80 are open.
Verify that the Firewall or backend proxy has access to the required domains and ports see, configure connectors.
Open a browser tab and enter:
https://login.microsoftonline.com. Make sure you can sign in.
Verify machine and backend component certificate support
Objective: Verify that the connector machine, backend proxy, and firewall can support the certificate created by the connector. Also, verify the certificate is valid.
Note
The connector tries to create a SHA512 cert that is supported by Transport Layer Security (TLS) 1.2. If the machine or the backend firewall and proxy does not support TLS 1.2, the installation fails.
Review the prerequisites required:
Verify the machine supports Transport Layer Security (TLS) 1.2 – All Windows versions after 2012 R2 should support TLS 1.2. If your connector machine is from a version of 2012 R2 or prior, make sure that the required updates are installed.
Contact your network admin and ask to verify that the backend proxy and firewall don't block
SHA512outgoing traffic.
To verify the client certificate:
Verify the thumbprint of the current client certificate. The certificate store can be found in %ProgramData%\microsoft\Microsoft AAD private network connector\Config\TrustSettings.xml.
<?xml version="1.0" encoding="utf-8"?>
<ConnectorTrustSettingsFile xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<CloudProxyTrust>
<Thumbprint>4905CC64B2D81BBED60962ECC5DCF63F643CCD55</Thumbprint>
<IsInUserStore>false</IsInUserStore>
</CloudProxyTrust>
</ConnectorTrustSettingsFile>
The possible IsInUserStore values are true and false. A value of true means the certificate is automatically renewed and stored in the personal container in the user certificate store of the Network Service. A value of false means the client certificate is created during the installation or registration initiated by Register-MicrosoftEntraPrivateNetworkConnector. The certificate is stored in the personal container in the certificate store of the local machine.
If the value is true, follow these steps to verify the certificate:
- Download PsTools.zip.
- Extract PsExec from the package and run psexec -i -u "nt authority\network service" cmd.exe from an elevated command prompt.
- Run certmgr.msc in the newly appeared command prompt.
- In the management console, expand the Personal container and select on Certificates.
- Locate the certificate issued by connectorregistrationca.msappproxy.net.
If the value is false, follow these steps to verify the certificate:
- Run certlm.msc.
- In the management console, expand the Personal container and select on Certificates.
- Locate the certificate issued by connectorregistrationca.msappproxy.net.
To renew the client certificate:
If a connector isn't connected to the service for several months, its certificates could be outdated. The failure of the certificate renewal leads to an expired certificate. The expired certificate causes the connector service to stop working. The event 1000 is recorded in the admin log of the connector:
Connector re-registration failed: The Connector trust certificate expired. Run the PowerShell cmdlet Register-MicrosoftEntraPrivateNetworkConnector on the computer on which the Connector is running to re-register your Connector.
In this case, uninstall and reinstall the connector to trigger registration or you can run the following PowerShell commands:
Import-module MicrosoftEntraPrivateNetworkConnectorPSModule
Register-MicrosoftEntraPrivateNetworkConnector
To learn more about the Register-MicrosoftEntraPrivateNetworkConnector command, see Create an unattended installation script for the Microsoft Entra private network connector.
Verify admin is used to install the connector
Objective: Verify that the user who tries to install the connector is an administrator with correct credentials. Currently, the user must be at least an Application Administrator for the installation to succeed.
To verify the credentials are correct:
Connect to https://login.microsoftonline.com and use the same credentials. Make sure the sign in is successful. You can check the user role by going to Microsoft Entra ID -> Users and Groups -> All Users.
Select your user account, then Directory Role in the resulting menu. Verify that the selected role is Application Administrator. If you're unable to access any of the pages along these steps, you don't have the required role.
Connector errors
If registration fails during the connector wizard installation, there are two ways to view the reason for the failure. Either look in the event log under Windows Logs\Application (filter by Source = "Microsoft Entra private network connector" , or run the following Windows PowerShell command:
Get-EventLog application –source "Microsoft Entra private network connector" –EntryType "Error" –Newest 1
Once you find the connector error from the event log, use this table of common errors to resolve the problem:
| Error | Recommended steps |
|---|---|
Connector registration failed: Make sure you enabled application proxy in the Azure Management Portal and that you entered your Active Directory user name and password correctly. Error: 'One or more errors occurred.' |
If you closed the registration window without signing in to Microsoft Entra ID, run the connector wizard again and register the connector. If the registration window opens and then immediately closes without allowing you to sign in, you get the error. The error occurs when there's a networking error on your system. Make sure you can connect from a browser to a public website and that the ports are open as specified in configure connectors. |
Clear error is presented in the registration window. Cannot proceed |
If you see the error and then the window closes, you entered the wrong username or password. Try again. |
Connector registration failed: Make sure you enabled application proxy in the Azure Management Portal and that you entered your Active Directory user name and password correctly. Error: 'AADSTS50059: No tenant-identifying information found in either the request or implied by any provided credentials and search by service principal URI has failed. |
You're trying to sign in using a Microsoft Account and not a domain that is part of the organization ID of the directory you're trying to access. The admin must be part of the same domain name as the tenant domain. For example, if the Microsoft Entra domain is contoso.com, the admin should be admin@contoso.com. |
Failed to retrieve the current execution policy for running PowerShell scripts. |
If the connector installation fails, check to make sure that PowerShell execution policy isn't disabled. 1. Open the Group Policy Editor. 2. Go to Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell and double-click Turn on Script Execution. 3. The execution policy can be set to either Not Configured or Enabled. If set to Enabled, make sure that under Options, the Execution Policy is set to either Allow local scripts and remote signed scripts or to Allow all scripts. |
Connector failed to download the configuration. |
The connector’s client certificate, which is used for authentication, expired. The issue occurs if you have the connector installed behind a proxy. In this case, the connector can't access the internet and isn't able to provide applications to remote users. Renew trust manually using the Register-MicrosoftEntraPrivateNetworkConnector cmdlet in Windows PowerShell. If your connector is behind a proxy, it's necessary to grant internet access to the connector accounts network services and local system. Granting access is accomplished by granting access to the proxy or bypassing the proxy. |
Connector registration failed: Make sure you are an Application Administrator of your Active Directory to register the connector. Error: 'The registration request was denied.' |
The alias you're trying to sign in with isn't an admin on this domain. Your connector is always installed for the directory that owns the user’s domain. Make sure that the admin account you're trying to sign in with has at least Application Administrator permissions to the Microsoft Entra tenant. |
The connector was unable to connect to the service due to networking issues. The connector tried to access the following URL. |
The connector is unable to connect to the application proxy cloud service. The issue happens if you have a firewall rule blocking the connection. Allow access to the correct ports and URLs listed in configure connectors. |
Flowchart for connector issues
This flowchart walks you through the steps for debugging some of the more common connector issues. For details about each step, see the table following the flowchart.
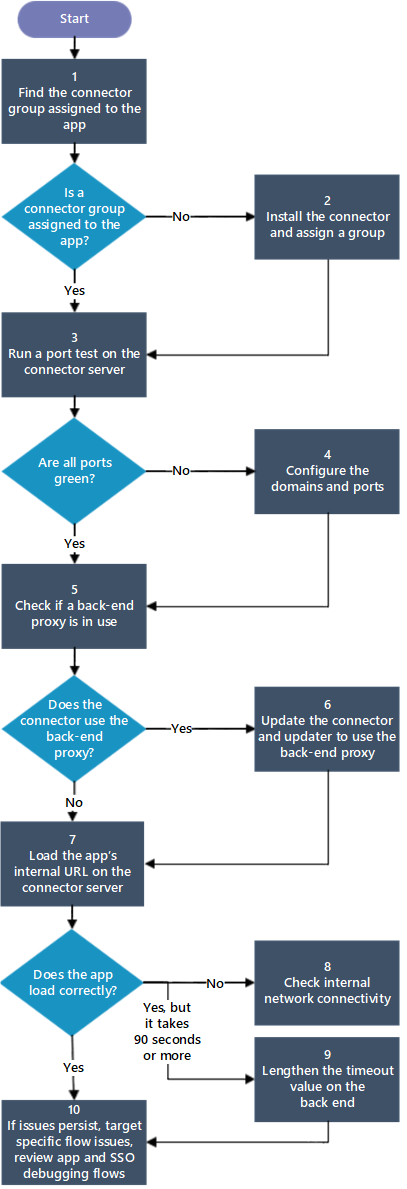
| Step | Action | Description |
|---|---|---|
| 1 | Find the connector group assigned to the app | You probably have a connector installed on multiple servers, in which case the connectors should be assigned to a connector group. To learn more about connector groups, see Understand Microsoft Entra private network connector groups. |
| 2 | Install the connector and assign a group | If you don't have a connector installed, see configure connectors). If the connector isn't assigned to a group, see Assign the connector to a group. If the application isn't assigned to a connector group, see Assign the application to a connector group. |
| 3 | Run a port test on the connector server | On the connector server, run a port test by using telnet or other port testing tool to check if ports are configured correctly. To learn more, see configure connectors. |
| 4 | Configure the domains and ports | Configure connectors for the connector. Certain ports must be open and URLs that your server must be able to access. For more information, see configure connectors. |
| 5 | Check if a back-end proxy is in use | Check to see if the connectors are using back-end proxy servers or bypassing them. For details, see Troubleshoot connector proxy problems and service connectivity issues. |
| 6 | Update the connector and updater settings with the back-end proxy information | If a back-end proxy is in use, make sure the connector is using the same proxy. For details about troubleshooting and configuring connectors to work with proxy servers, see Work with existing on-premises proxy servers. |
| 7 | Load the app's internal URL on the connector server | On the connector server, load the app's internal URL. |
| 8 | Check internal network connectivity | There's a connectivity issue in your internal network that this debugging flow is unable to diagnose. The application must be accessible internally for the connectors to work. You can enable and view connector event logs as described in private network connectors. |
| 9 | Lengthen the time-out value on the back end | In the Additional Settings for your application, change the Backend Application Timeout setting to Long. See Add an on-premises app to Microsoft Entra ID. |
| 10 | If issues persist, debug applications. | Debug application proxy application issues. |
Frequently asked questions
Why is my connector still using an older version and not auto-upgraded to latest version?
This may be due to either the updater service not working correctly or if there are no new updates available that the service can install.
The updater service is healthy if it’s running and there are no errors recorded in the event log (Applications and Services logs -> Microsoft -> Microsoft Entra private network -> Updater -> Admin).
Important
Only major versions are released for auto-upgrade. We recommend updating your connector manually only if it's necessary. For example, you cannot wait for a major release, because you must fix a known problem or you want to use a new feature. For more information on new releases, the type of the release (download, auto-upgrade), bug fixes and new features see, Microsoft Entra private network connector: Version release history.
To manually upgrade a connector:
- Download the latest version of the connector. (Find it in the Microsoft Entra admin center at Global Secure Access > Connect > Connectors)
- The installer restarts the Microsoft Entra private network connector services. In some cases, a reboot of the server might be required if the installer cannot replace all files. Therefore we recommend closing all applications (that is, Event Viewer) before you start the upgrade.
- Run the installer. The upgrade process is quick and does not require providing any credentials and the connector is not re-registered.
Can private network connector services run in a different user context than the default?
No, this scenario isn't supported. The default settings are:
- Microsoft Entra private network connector - WAPCSvc - Network Service
- Microsoft Entra private network connector Updater - WAPCUpdaterSvc - NT Authority\System
Can a guest user with an active administrator role assignment register the connector for the (guest) tenant?
No, currently, this isn't possible. The registration attempt is always made on the user's home tenant.
My back-end application is hosted on multiple web servers and requires user session persistence (stickiness). How can I achieve session persistence?
For recommendations, see High availability and load balancing of your private network connectors and applications.
Is TLS termination (TLS/HTTPS inspection or acceleration) on traffic from the connector servers to Azure supported?
The private network connector performs certificate-based authentication to Azure. TLS Termination (TLS/HTTPS inspection or acceleration) breaks this authentication method and isn't supported. Traffic from the connector to Azure must bypass any devices that are performing TLS Termination.
Is TLS 1.2 required for all connections?
Yes. To provide the best-in-class encryption to our customers, the application proxy service limits access to only TLS 1.2 protocols. These changes were gradually rolled out and effective since August 31, 2019. Make sure that all your client-server and browser-server combinations are updated to use TLS 1.2 to maintain connection to application proxy service. These include clients your users are using to access applications published through application proxy. See Preparing for TLS 1.2 in Office 365 for useful references and resources.
Can I place a forward proxy device between the connector server(s) and the back-end application server?
Yes, this scenario is supported starting from the connector version 1.5.1526.0. See Work with existing on-premises proxy servers.
Should I create a dedicated account to register the connector with Microsoft Entra application proxy?
There's no reason to create a dedicated account. Any account with the Application Administrator role works. The credentials entered during installation aren't used after the registration process. Instead, a certificate is issued to the connector, which is used for authentication from that point on.
How can I monitor the performance of the Microsoft Entra private network connector?
There are Performance Monitor counters that are installed along with the connector. To view them:
- Select Start, type "Perfmon", and press ENTER.
- Select Performance Monitor and click the green + icon.
- Add the Microsoft Entra private network connector counters you want to monitor.
Does the Microsoft Entra private network connector have to be on the same subnet as the resource?
The connector isn't required to be on the same subnet. However, it needs name resolution (DNS, hosts file) to the resource and the necessary network connectivity (routing to the resource, ports open on the resource, and so on). For recommendations, see Network topology considerations when using Microsoft Entra application proxy.
Why is the connector still showing in Microsoft Entra admin center after I uninstalled the connector from the Server?
When a connector is running, it remains active as it connects to the service. Uninstalled or unused connectors are tagged as inactive and are removed after 10 days of inactivity from the portal. There is no way to remove the Inactive connector manually from the Microsoft Entra admin center.