Linter rule: Secure secrets in parameters
This rule finds parameters whose names look like secrets but without the secure decorator. For example, a parameter name contains the following keywords:
passwordpwdsecretaccountkeyacctkey
Linter rule code
To customize rule settings, use the following value in the Bicep configuration file:
secure-secrets-in-params
Solution
Use the secure decorator for the parameters that contain secrets. The secure decorator marks the parameter as secure. The value for a secure parameter isn't saved to the deployment history and isn't logged.
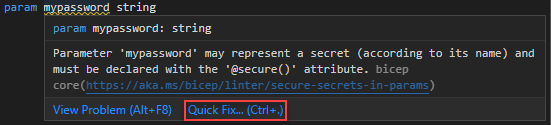
The following example fails this test because the parameter name might contain secrets.
param mypassword string
You can fix it by adding the secure decorator:
@secure()
param mypassword string
Optionally, you can use Quick Fix to add the secure decorator.
Silence false positives
Sometimes this rule alerts on parameters that don't contain secrets. In these cases, disable the warning for this line by adding #disable-next-line secure-secrets-in-params before the line with the warning. For example:
#disable-next-line secure-secrets-in-params // Doesn't contain a secret
param mypassword string
It's good practice to add a comment that explains why the rule doesn't apply to this line.
Related content
For more information about the linter, see Use Bicep linter.