Servers met Azure Arc beheren met Windows Admin Center in Azure
Belangrijk
Versie 1.36 en 1.35 van de Azure Connected Machine Agent (Arc-agent) verbreken de verbinding met het Windows-beheercentrum. Dit is opgelost in latere versies van de Arc-agent (1.37+) Dit kan hier worden gedownload.
Met het Windows-beheercentrum in Azure Portal kunt u het Windows Server-besturingssysteem van uw servers met Arc beheren, ook wel hybride machines genoemd. U kunt hybride machines vanaf elke locatie veilig beheren zonder dat u een VPN, openbaar IP-adres of andere binnenkomende connectiviteit met uw computer nodig hebt. Voor meer informatie over Azure Arc-ingeschakelde servers, zie Wat zijn Azure Arc-ingeschakelde servers?.
Met de Windows Admin Center-extensie in Azure krijgt u de beheer-, configuratie-, probleemoplossings- en onderhoudsfunctionaliteit voor het beheren van uw servers met Arc in Azure Portal. Windows Server-infrastructuur en workloadbeheer vereist niet langer dat u line-of-sight of Remote Desktop Protocol (RDP) tot stand brengt. Het kan allemaal systeemeigen worden uitgevoerd vanuit Azure Portal. Het Windows-beheercentrum biedt hulpprogramma's die u normaal gesproken kunt vinden in Serverbeheer, Apparaatbeheer, Taakbeheer, Hyper-V Manager en de meeste andere MMC-hulpprogramma's (Microsoft Management Console).
Dit artikel bevat een overzicht van het gebruik van Windows Admin Center in Azure Portal, vereisten en het installeren van Windows Admin Center in Azure Portal en het gebruiken voor het beheren van uw hybride machine. Het beantwoordt ook veelgestelde vragen en bevat een lijst met bekende problemen en tips voor probleemoplossing voor het geval iets niet werkt.
Overzicht van Het Windows-beheercentrum in Azure
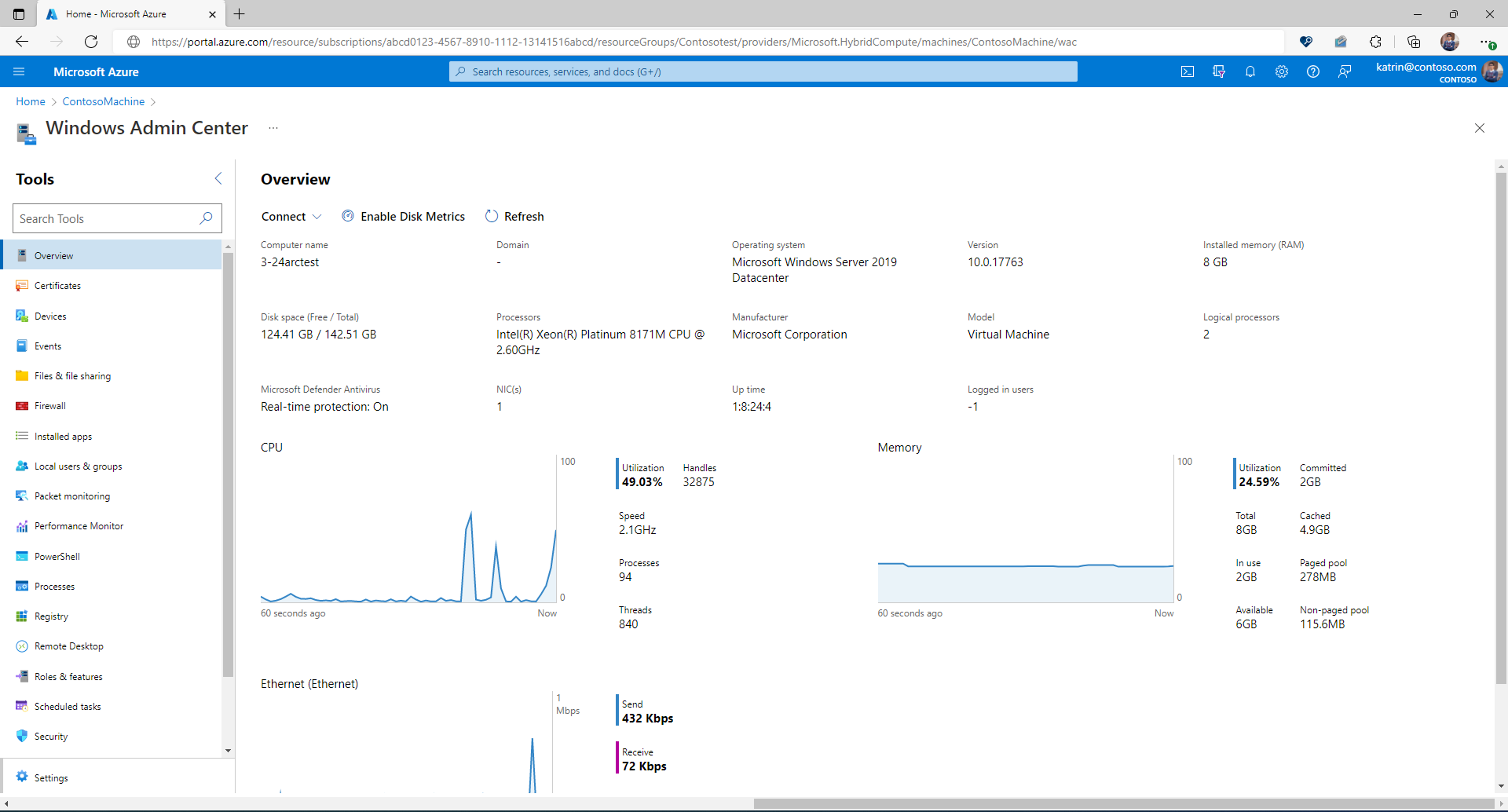
Windows Admin Center in Azure Portal biedt essentiële hulpprogramma's voor het beheren van Windows Server die wordt uitgevoerd op één hybride machine. U kunt hybride machines beheren zonder dat u binnenkomende poorten op uw firewall hoeft te openen.
Met behulp van Het Windows-beheercentrum in Azure Portal kunt u het volgende beheren:
- Certificaten
- Apparaten
- Gebeurtenissen
- Bestanden en bestanden delen
- Brandmuur
- Geïnstalleerde apps
- Lokale gebruikers en groepen
- Prestatiemeter
- PowerShell
- Processen
- Register
- Extern bureaublad
- Rollen en onderdelen
- Geplande taken
- Diensten
- Opslag
- Updates
- Virtuele machines
- Virtuele switches
Op dit moment wordt geen ondersteuning geboden voor andere extensies voor Het Windows-beheercentrum in Azure Portal.
Waarschuwing
Als u Windows Admin Center handmatig hebt geïnstalleerd op uw hybride machine om meerdere systemen te beheren, vervangt het inschakelen van Windows Admin Center in Azure uw bestaande exemplaar van Het Windows-beheercentrum en verwijdert u de mogelijkheid om andere computers te beheren. U hebt geen toegang meer tot uw eerder geïmplementeerde exemplaar van het Windows-beheercentrum.
Eisen
Deze sectie bevat de vereisten voor het gebruik van Het Windows-beheercentrum in Azure Portal voor het beheren van een hybride machine:
- Azure-account met een actief abonnement
- Azure-machtigingen
- beschikbaarheid van Azure-regio's
- vereisten voor hybride machines
- netwerkvereisten
Azure-account met een actief abonnement
U hebt een Azure-account met een actief abonnement nodig om Windows Admin Center te implementeren. Als u er nog geen hebt, kunt u gratis een account maken.
Tijdens de implementatie van Het Windows-beheercentrum proberen we de Microsoft.HybridConnectivity resourceprovider voor uw abonnement te registreren.
Belangrijk
U moet gemachtigd zijn om een resourceprovider te registreren. Hiervoor is de */register/action bewerking vereist. Dit is inbegrepen als u de rol van inzender of eigenaar hebt toegewezen gekregen voor uw abonnement.
Notitie
Registratie van resourceproviders is een eenmalige taak per abonnement.
Ga als volgende te werk om de status van de resourceprovider te controleren en u indien nodig te registreren:
- Meld u aan bij de Azure Portal.
- Selecteer abonnementen.
- Selecteer de naam van uw abonnement.
- Selecteer resourceproviders.
- Zoek naar Microsoft.HybridConnectivity.
- Controleer of de status van Microsoft.HybridConnectivity is Geregistreerd.
- Als de status is NotRegistered, selecteert u Microsoft.HybridConnectivityen selecteert u registreren.
Azure-machtigingen
Als u de Windows-beheercentrumextensie wilt installeren voor een serverresource met Arc, moet aan uw account de rol Eigenaar, Contributor, of Windows-beheercentrumbeheerder in Azure worden verleend.
Voor verbinding met het Windows-beheercentrum moet u Reader- en beheerdersaanmeldingsrechten voor het Windows-beheercentrum hebben op de Arc-ingeschakelde serverresource.
Meer informatie over het toewijzen van Azure-rollen met behulp van de Azure-portal
Beschikbaarheid van Azure-regio's
Windows Admin Center wordt ondersteund in de volgende Azure-regio's:
- Australië - oost
- Brazilië - zuid
- Canada - centraal
- Canada Oost
- Centraal India
- Centraal-VS
- Oost-Azië
- Oost-VS
- Oost-Verenigde Staten 2
- Frankrijk - centraal
- Japan Oost
- Centraal Korea
- VS - noord-centraal
- Europa - noord
- Zuid-Afrika - noord
- Zuid-Centraal VS
- Zuidoost-Azië
- Zweden - centraal
- Zwitserland - noord
- UAE - noord
- VK-Zuid
- VK West
- West-centraal Verenigde Staten
- West-Europa
- West-VS
- West US 2
- West-US 3
Notitie
Windows-beheercentrum wordt niet ondersteund in Azure China 21Vianet, Azure Government of andere niet-openbare clouds
Vereisten voor hybride machines
Als u Windows Admin Center wilt gebruiken in Azure Portal, moet de Windows Admin Center-agent zijn geïnstalleerd op elke hybride machine die u wilt beheren via een Azure VM-extensie. Zorg ervoor dat uw computer is verbonden met Azure Arc voordat u doorgaat. Zie Windows Server-machines verbinden met Azure via Azure Arc Setupvoor meer informatie over het onboarden van uw machine naar Azure Arc. De hybride machine moet voldoen aan de volgende vereisten:
- Windows Server 2016 of hoger
- 3 GB RAM-geheugen of meer
- Azure Arc-agent versie 1.13.21320.014 of hoger
- U moet Windows Server-licenties van het type Pay-as-you-go of de Software Assurance-licentie gebruiken.
Belangrijk
Vanaf 1 november 2024 vereist Windows Admin Center voor Azure Arc dat uw hybride machine een Pay-as-you-go- of Software Assurance-licentietype heeft om te gebruiken. Alle nieuwe installaties van de Windows Admin Center-agent moeten aan deze vereiste voldoen. Machines met Windows Admin Center voor Azure Arc die vóór 1 november 2024 zijn geïnstalleerd, kunnen windows-beheercentrum voor Azure Arc tot 12 maanden blijven gebruiken zonder updates tot 1 november 2025.
Netwerkvereisten
De hybride machine moet voldoen aan de volgende netwerkvereisten:
Uitgaande internettoegang of een regel voor uitgaande poorten die HTTPS-verkeer naar de volgende eindpunten toestaat:
-
*service.waconazure.comof deWindowsAdminCenter-servicetag pas.windows.net*.servicebus.windows.net
-
Notitie
Er zijn geen binnenkomende poorten vereist om Het Windows-beheercentrum te kunnen gebruiken.
De beheercomputer waarop Azure Portal wordt uitgevoerd, moet voldoen aan de volgende netwerkvereisten:
- Uitgaande internettoegang via poort
443
Controleer de ondersteunde apparaten en aanbevolen browsers voordat u de Azure-portal opent vanaf de beheercomputer of het systeem.
Windows Admin Center installeren in Azure Portal
Voordat u Windows Admin Center in Azure Portal kunt gebruiken, moet u de VM-extensie van het Windows-beheercentrum implementeren met behulp van de volgende stappen:
- Open Azure Portal en navigeer naar uw server met Arc.
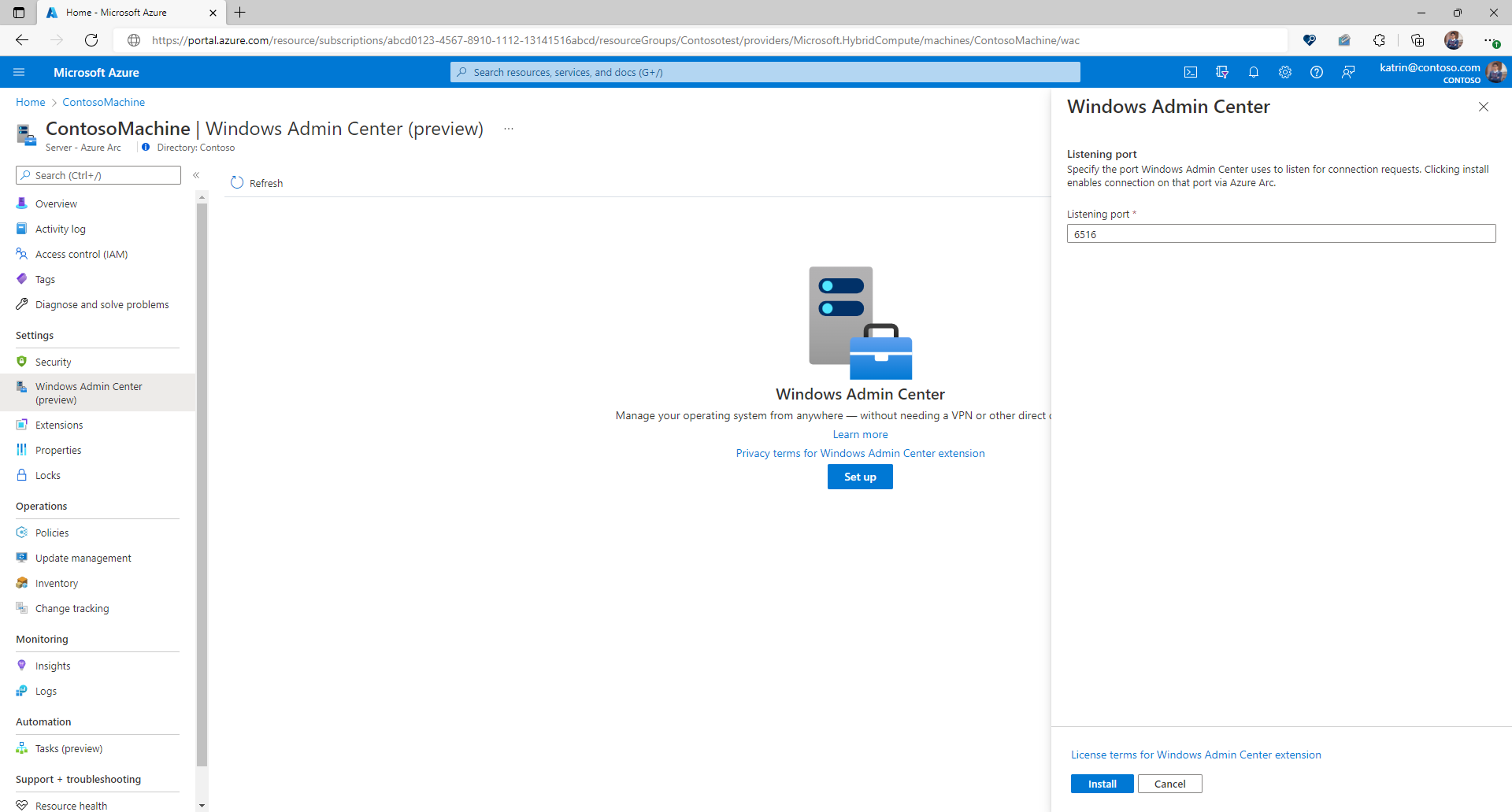
- Selecteer in de groep InstellingenWindows Admin Center.
- Geef de poort op waarop u Windows Admin Center wilt installeren en selecteer vervolgens Installeren.
Verbinding maken met het Windows-beheercentrum in Azure Portal
Nadat u Windows Admin Center op uw hybride computer hebt geïnstalleerd, voert u de volgende stappen uit om er verbinding mee te maken en deze te gebruiken om Windows Server te beheren:
- Open de Azure-portal en navigeer naar uw Arc-ingeschakelde server. Selecteer vervolgens onder de Instellingen groep Windows-beheercentrum (preview).
- Selecteer Maak verbinding.
Notitie
Vanaf augustus 2022 kunt u in het Windows-beheercentrum nu verificatie op basis van Microsoft Entra ID gebruiken voor uw hybride machine. U wordt niet langer gevraagd om de aanmeldgegevens van een lokaal beheerdersaccount.
Het Windows-beheercentrum wordt geopend in de portal, zodat u toegang hebt tot dezelfde hulpprogramma's waarmee u mogelijk bekend bent met het gebruik van Het Windows-beheercentrum in een on-premises implementatie.
Roltoewijzingen configureren
Toegang tot Windows Admin Center wordt beheerd door de Windows Admin Center-beheerdersaanmelding Azure-rol.
Notitie
De rol Administrator Login van het Windows Admin Centrum maakt gebruik van dataActions en kan daarom niet worden toegewezen op het niveau van de beheergroep. Deze rollen kunnen momenteel alleen worden toegewezen op het abonnementsniveau, de resourcegroep of het resourcebereik.
Roltoewijzingen configureren voor uw hybride machines met behulp van de Microsoft Entra-beheercentrumervaring:
Open de hybride machine die u wilt beheren met behulp van het Windows-beheercentrum.
Selecteer Toegangsbeheer (IAM).
Selecteer >Roltoewijzing toevoegen om de pagina Roltoewijzing toevoegen te openen.
Wijs de volgende rol toe. Zie Azure-rollen toewijzen met behulp van de Azure-portalvoor gedetailleerde stappen.
Instelling Waarde Rol beheerdersaanmelding voor Windows-beheercentrum Toegang toewijzen aan Gebruiker, groep, service-principal of beheerde identiteit
Zie de volgende artikelen voor meer informatie over het gebruik van Azure RBAC voor het beheren van de toegang tot uw Azure-abonnementsresources:
- Azure-rollen toewijzen met behulp van Azure CLI
- Azure-rollen toewijzen met behulp van de Azure CLI-voorbeelden. Azure CLI kan ook worden gebruikt in de Azure Cloud Shell-ervaring.
- Azure-rollen toewijzen met behulp van azure Portal
- Azure-rollen toewijzen met behulp van Azure PowerShell.
Proxyconfiguratie
Als de computer verbinding maakt via een proxyserver om via internet te communiceren, raadpleegt u de volgende vereisten om inzicht te hebben in de vereiste netwerkconfiguratie.
De Windows Admin Center-extensie kan communiceren via een proxyserver met behulp van het HTTPS-protocol. Gebruik de instellingen voor extensies voor configuratie, zoals beschreven in de volgende stappen. Geverifieerde proxy's worden niet ondersteund.
Notitie
Proxyconfiguratie wordt alleen ondersteund voor extensieversies die groter zijn dan 0.0.0.321.
Gebruik dit stroomdiagram om de waarden van de
Settingsparameters te bepalen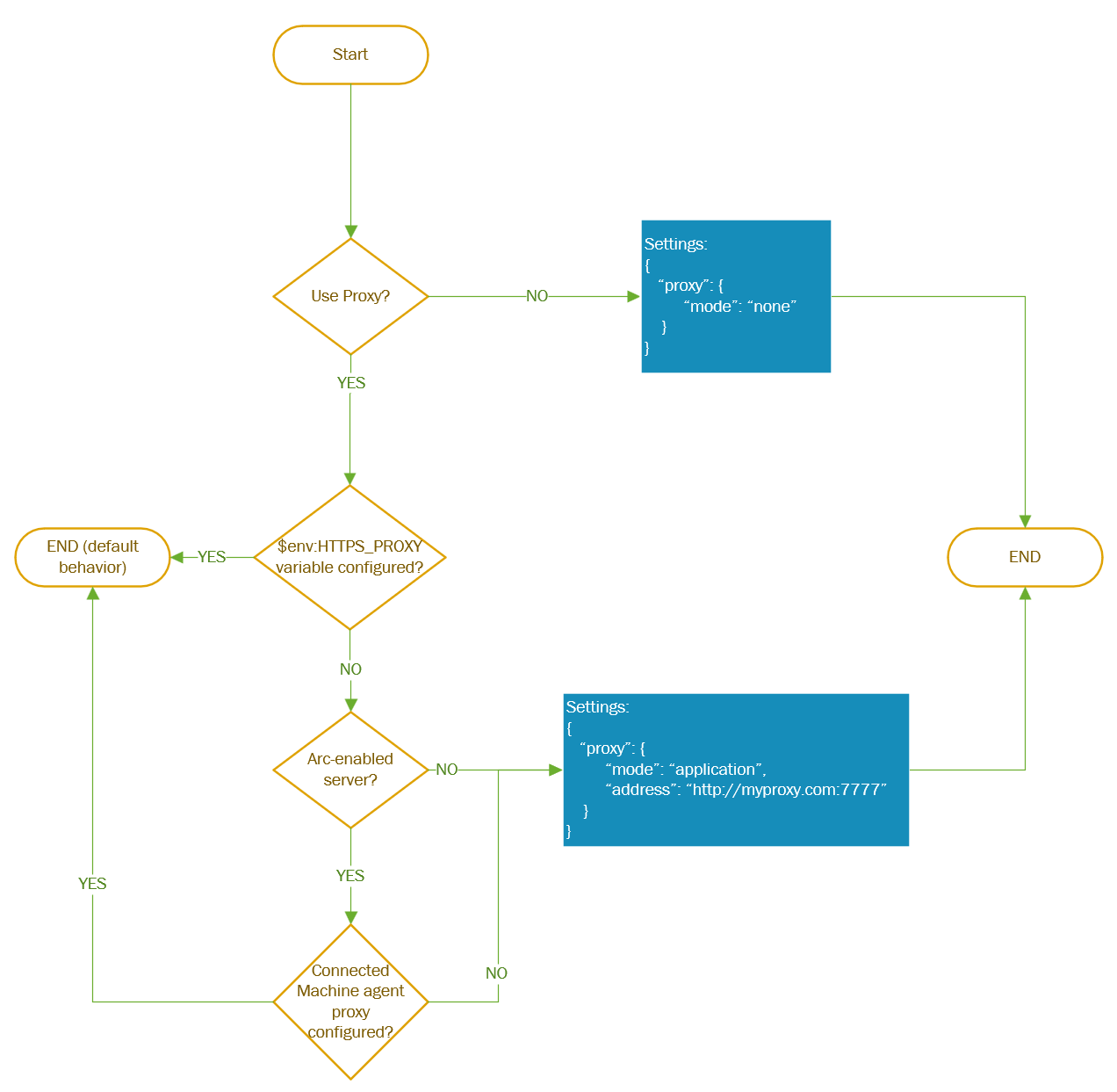
Nadat u de
Settingsparameterwaarden hebt vastgesteld, geeft u deze andere parameters op wanneer u de AdminCenter-agent implementeert. Gebruik PowerShell-opdrachten, zoals wordt weergegeven in het volgende voorbeeld:
$wacPort = "6516"
$settings = @{"port" = $wacPort; "proxy" = @{"mode" = "application"; "address" = "http://[address]:[port]";}}
New-AzConnectedMachineExtension -Name AdminCenter -ExtensionType AdminCenter -Publisher Microsoft.AdminCenter -ResourceGroupName <resource-group-name> -MachineName <arc-server-name> -Location <arc-server-location> -Setting $settings -SubscriptionId <subscription-id>
Hoe het werkt
Met behulp van Het Windows-beheercentrum in Azure kunt u verbinding maken met uw hybride machine zonder dat er een binnenkomende poort moet worden ingeschakeld op de firewall. Windows Admin Center, via de Arc-agent, kan veilig een omgekeerde proxysessieverbinding tot stand brengen met de Azure Arc-service op een uitgaande manier.
Voor elke hybride machine die u wilt beheren met Windows Admin Center in Azure Portal, moet u een agent implementeren op elke computer.
De agent communiceert met een externe service die certificaten beheert, zodat u eenvoudig verbinding kunt maken met uw hybride machine.
Als u op Install klikt, worden de volgende acties uitgevoerd:
- Registreert de Microsoft.HybridConnectivity resourceprovider voor uw abonnement. De resourceprovider fungeert als host voor de proxy die wordt gebruikt voor communicatie met uw server met Arc.
- Hiermee wordt een Azure -eindpunt-resource bovenop uw Arc ingeschakelde resource geïmplementeerd, waarmee een omgekeerde proxyverbinding op een opgegeven poort mogelijk wordt gemaakt. Dit is gewoon een logische resource in Azure en implementeert niets op uw server zelf.
- Installeert de Windows Admin Center-agent op uw hybride machine met een geldig TLS-certificaat.
Notitie
Als u Het Windows-beheercentrum verwijdert, wordt de logische Azure-eindpuntresource niet verwijderd. Dit wordt bewaard voor andere ervaringen die gebruikmaken van deze resource, zoals SSH.
Als u op Connect klikt, worden de volgende acties uitgevoerd:
- Azure Portal vraagt de Microsoft.HybridConnectivity resourceprovider voor toegang tot de server met Arc.
- De resourceprovider communiceert met een Layer 4 SNI-proxy om een kortstondige, sessiespecifieke toegang tot uw Arc-ingeschakelde server via de poort van het Windows Beheercentrum tot stand te brengen.
- Er wordt een unieke URL met een korte levensduur gegenereerd en er wordt verbinding gemaakt met het Windows-beheercentrum vanuit Azure Portal.
De verbinding met Windows Admin Center is end-to-end versleuteld met SSL-terminatie die plaatsvindt op uw hybride machine.
Windows Admin Center-implementatie automatiseren met Behulp van PowerShell
U kunt de implementatie van Het Windows-beheercentrum in Azure Portal automatiseren met behulp van dit PowerShell-voorbeeldscript.
$location = "<location_of_hybrid_machine>"
$machineName = "<name_of_hybrid_machine>"
$resourceGroup = "<resource_group>"
$subscription = "<subscription_id>"
$port = "6516"
$portint = 6516
#Deploy Windows Admin Center
$Setting = @{"port" = $port; "proxy" = @{"mode" = "application"; "address" = "http://[address]:[port]";}} #proxy configuration is optional
New-AzConnectedMachineExtension -Name "AdminCenter" -ResourceGroupName $resourceGroup -MachineName $machineName -Location $location -Publisher "Microsoft.AdminCenter" -Settings $Setting -ExtensionType "AdminCenter" -SubscriptionId $subscription
#Allow connectivity
$putPayload = "{'properties': {'type': 'default'}}"
Invoke-AzRestMethod -Method PUT -Uri "https://management.azure.com/subscriptions/${subscription}/resourceGroups/${resourceGroup}/providers/Microsoft.HybridCompute/machines/${machineName}/providers/Microsoft.HybridConnectivity/endpoints/default?api-version=2023-03-15" -Payload $putPayload
$patch = @{ "properties" = @{ "serviceName" = "WAC"; "port" = $portint}}
$patchPayload = ConvertTo-Json $patch
Invoke-AzRestMethod -Method PUT -Path /subscriptions/${subscription}/resourceGroups/${resourceGroup}/providers/Microsoft.HybridCompute/machines/${machineName}/providers/Microsoft.HybridConnectivity/endpoints/default/serviceconfigurations/WAC?api-version=2023-03-15 -Payload $patchPayload
Probleemoplossing
Hier volgen enkele tips om te proberen voor het geval er iets niet werkt. Zie Problemen met het Windows-beheercentrum oplossenvoor algemene probleemoplossing voor Windows Admin Center (niet specifiek in Azure).
Kan geen verbinding maken met '404-eindpunt niet gevonden'
- Versie 1.36 en 1.35 van de Azure Connected Machine Agent (Arc-agent) verbreken de verbinding met het Windows-beheercentrum. Dit is opgelost in latere versies van de Arc-agent (1.37+) Dit kan hier worden gedownload.
Verbindingsfout
Start de HIMDS-service opnieuw op.
RDP naar uw server.
Open PowerShell als beheerder en voer het volgende uit:
Restart-Service -Name himds
Controleer of uw extensieversie 0.0.0.169 of hoger is.
- Ga naar Extensies
- Controleer of de extensieversie 'AdminCenter' 0.0.0.169 of hoger is.
- Als dat niet het is, verwijdert u de extensie en installeert u deze opnieuw
Zorg ervoor dat de Windows Admin Center-service wordt uitgevoerd op uw computer.
- RDP naar uw server.
- Open Taakbeheer (Ctrl+Shift+Esc) en navigeer naar Services.
- Zorg ervoor dat ServerManagementGateway/Windows Admin Center wordt uitgevoerd.
- Als de service niet wordt uitgevoerd, start u deze.
Controleer of de poort is ingeschakeld voor een omgekeerde proxysessie.
Log via RDP in op uw server.
Open PowerShell als beheerder en voer het volgende uit:
azcmagent config listHiermee wordt een lijst met poorten geretourneerd onder de configuratie van incomingconnections.ports (preview) die zijn ingeschakeld om verbinding te maken vanuit Azure. Controleer of de poort waarop u Windows Admin Center hebt geïnstalleerd, in deze lijst staat. Als het Windows-beheercentrum bijvoorbeeld is geïnstalleerd op poort 443, is het resultaat:
Local configuration setting incomingconnections.ports (preview): 443Als het zich niet op deze lijst bevindt, voer
azcmagent config set incomingconnections.ports <port>Als u een andere ervaring (zoals SSH) gebruikt met deze oplossing, kunt u meerdere poorten opgeven, gescheiden door een komma.
Zorg ervoor dat u uitgaande connectiviteit hebt met de benodigde poorten
- De hybride machine moet uitgaande connectiviteit hebben met de volgende eindpunten:
-
*.wac.azure.com,*.waconazure.comof de ServiceTag van Windows Admin Center pas.windows.net*.servicebus.windows.net
-
- De hybride machine moet uitgaande connectiviteit hebben met de volgende eindpunten:
Een van de Hulpprogramma's van het Windows-beheercentrum wordt niet geladen of geeft een fout
Navigeer naar een ander hulpprogramma in het Windows-beheercentrum en ga terug naar het hulpprogramma dat niet wordt geladen.
Als er geen ander hulpprogramma wordt geladen, is er mogelijk een probleem met uw netwerkverbinding. Probeer het mes te sluiten en vervolgens opnieuw verbinding te maken. Als dit niet werkt, opent u een ondersteuningsticket.
De Windows Admin Center-extensie kan niet worden geïnstalleerd
Controleer of de hybride machine voldoet aan de vereisten.
Zorg ervoor dat uitgaand verkeer naar het Windows-beheercentrum is toegestaan op uw hybride machine
Test de connectiviteit door de volgende opdracht uit te voeren met behulp van PowerShell in uw virtuele machine:
Invoke-RestMethod -Method GET -Uri https://<your_region>.service.waconazure.comMicrosoft Certificate and DNS service for Windows Admin Center in the Azure Portal
Als u al het uitgaande verkeer hebt toegestaan en een foutmelding krijgt van de bovenstaande opdracht, controleert u of er geen firewallregels zijn die de verbinding blokkeren.
Als er niets mis lijkt en Windows Admin Center nog steeds niet wordt geïnstalleerd, opent u een ondersteuningsaanvraag met de volgende informatie:
Logboeken vanuit Azure Portal. Windows Admin Center-logboeken vindt u onder Instellingen>Extensies>AdminCenter>Gedetailleerde status weergeven.
Registreert zich op de hybride machine. Voer de volgende PowerShell-opdracht uit en deel het resulterende .zip-bestand.
azcmagent logsNetwerktracering, indien van toepassing. Netwerktraceringen kunnen klantgegevens en gevoelige beveiligingsdetails bevatten, zoals wachtwoorden, dus we raden u aan de tracering te controleren en gevoelige details te verwijderen voordat u deze deelt.
Bekende problemen
- De incognitomodus van Chrome wordt niet ondersteund.
- De bureaublad-app van Azure Portal wordt niet ondersteund.
- Gedetailleerde foutberichten voor mislukte verbindingen zijn nog niet beschikbaar.
- Vanaf 1 november 2024 kunnen sommige bestaande klanten geen Windows Admin Center voor Azure Arc gebruiken.
- Vanaf 1 november 2024 kunnen sommige klanten Windows Admin Center voor Azure Arc niet installeren of gebruiken, zelfs niet met de juiste licentieverklaring.
Veelgestelde vragen
Vind antwoorden op de veelgestelde vragen over het gebruik van Windows Admin Center in Azure.
Hoeveel kost het om Het Windows-beheercentrum te gebruiken?
Er zijn geen kosten verbonden aan het Windows-beheercentrum in Azure Portal.
Kan ik Windows Admin Center gebruiken om de virtuele machines te beheren die op mijn server worden uitgevoerd?
U kunt de Hyper-V-rol installeren met behulp van de extensie Functies en onderdelen. Nadat u de browser hebt geïnstalleerd, vernieuwt u uw browser en worden in het Windows-beheercentrum de extensies voor virtuele machines en switchen weergegeven.
Welke servers kan ik beheren met deze extensie?
U kunt de mogelijkheid gebruiken om Windows Server 2016 en hoger met Arc te beheren. U kunt ook windows-beheercentrum in Azure gebruiken om lokale Azure-te beheren.
Hoe verwerkt Het Windows-beheercentrum de beveiliging?
Verkeer van Azure Portal naar Het Windows-beheercentrum is end-to-end versleuteld. Uw server met Arc wordt beheerd met behulp van PowerShell en WMI via WinRM.
Heb ik een binnenkomende poort nodig om Het Windows-beheercentrum te kunnen gebruiken?
Er is geen binnenkomende verbinding vereist voor het gebruik van het Windows-beheercentrum.
Waarom moet ik een uitgaande poortregel maken?
Er is een regel voor uitgaande poorten vereist voor de service die we hebben gebouwd om te communiceren met uw server. Onze service geeft u gratis een certificaat uit voor uw exemplaar van het Windows-beheercentrum. Deze service zorgt ervoor dat u altijd verbinding kunt maken met uw exemplaar van Windows Admin Center vanuit Azure Portal door uw WAC-certificaat up-to-date te houden.
Bovendien vereist toegang tot het Windows-beheercentrum vanuit Azure geen binnenkomende poort en alleen uitgaande connectiviteit via een reverse proxy-oplossing. Deze uitgaande regels zijn vereist om de verbinding tot stand te brengen.
Hoe vind ik de poort die wordt gebruikt voor de installatie van het Windows-beheercentrum?
Volg deze stappen om de waarde van de registerinstelling SmePort te controleren:
- RDP naar uw server
- Open de Registereditor
- Ga naar de sleutel
\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ServerManagementGateway - Lees de waarde van
SmePortom de gebruikte poort te vinden
Kan ik PowerShell of de Azure CLI gebruiken om de extensie op mijn VM te installeren?
Ja, als u de extensie wilt installeren met behulp van de Azure CLI, voert u de volgende opdracht uit vanaf een opdrachtprompt:
az connectedmachine extension create
U kunt de extensie ook installeren met behulp van PowerShell. Meer informatie over het automatiseren van de implementatie van Windows Admin Center met PowerShell.
Ik heb windows-beheercentrum al geïnstalleerd op mijn Arc-server. Kan ik deze openen vanuit de portal?
Ja. U kunt dezelfde stappen volgen die in dit document worden beschreven.
Waarschuwing
Als u deze mogelijkheid inschakelt, vervangt u uw bestaande exemplaar van het Windows-beheercentrum en verwijdert u de mogelijkheid om andere computers te beheren. Uw eerder geïmplementeerde exemplaar van het Windows-beheercentrum kan niet meer worden gebruikt. Doe dit niet als u uw exemplaar van het beheercentrum gebruikt om meerdere servers te beheren.
Volgende stappen
- Meer informatie over Windows-beheercentrum
- Meer informatie over het beheren van servers met Windows Admin Center
- Meer informatie over Azure Arc