BinSkim gebruiken om binaire bestanden te onderzoeken om beveiligingsproblemen te identificeren
Gebruik BinSkim om binaire bestanden te onderzoeken om coderings- en bouwprocedures te identificeren die het binaire bestand mogelijk kwetsbaar kunnen maken. Het kan worden gebruikt om binaire bestanden te controleren die klaar zijn voor verzending, om te controleren of er niets mis is gegaan in de buildketen.
BinSkim controleert op:
- Gebruik van verouderde compilerhulpprogrammasets: binaire bestanden moeten waar mogelijk worden gecompileerd op basis van de meest recente compilerhulpprogrammasets om het gebruik van huidige beveiligingsbeperking op compilerniveau en door het besturingssysteem geleverde beveiligingsbeperking te maximaliseren.
- Onveilige compilatie-instellingen: binaire bestanden moeten worden gecompileerd met de veiligst mogelijke instellingen om door het besturingssysteem geleverde beveiligingsmaatregelen in te schakelen, compilerfouten te maximaliseren en het rapporteren van waarschuwingen te verbeteren, naast andere zaken.
- Ondertekeningsproblemen: ondertekende binaire bestanden moeten worden ondertekend met cryptografische sterke algoritmen.
BinSkim is een open-source tool en genereert uitvoerbestanden die het Static Analysis Results Interchange Format (SARIF) gebruiken. BinSkim vervangt het voormalige hulpprogramma BinScope.
Zie de BinSkim-gebruikershandleidingvoor meer informatie over BinSkim.
BinSkim installeren en uitvoeren
Volg deze stappen om te controleren of de beveiligingscompilatieopties correct zijn geconfigureerd in de code die u verzendt.
Download en installeer de platformoverschrijdende .NET Core SDK.
Controleer of Visual Studio is geïnstalleerd. Zie Visual Studio installerenvoor meer informatie over het downloaden en installeren van Visual Studio.
Er zijn een aantal opties om BinSkim te downloaden, zoals een NuGet-pakket. In dit voorbeeld gebruiken we de git-kloonoptie om van hieruit te downloaden: https://github.com/microsoft/binskim en installeren op een 64-bits Windows-pc.
Open een Visual Studio Developer-opdrachtpromptvenster en maak een map, bijvoorbeeld
C:\binskim-master.C:\> Md \binskim-masterGa naar die map die u zojuist hebt gemaakt.
C:\> Cd \binskim-masterGebruik de git-kloonopdracht om alle benodigde bestanden te downloaden.
C:\binskim-master> git clone --recurse-submodules https://github.com/microsoft/binskim.gitGa naar de nieuwe
binskimdirectory die door de clone-opdracht is gemaakt.C:\> Cd \binskim-master\binskimVoer BuildAndTest.cmd uit om ervoor te zorgen dat de release-build slaagt en dat alle tests zijn geslaagd.
C:\binskim-master\binskim> BuildAndTest.cmd Welcome to .NET Core 3.1! --------------------- SDK Version: 3.1.101 ... C:\binskim-master\binskim\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\win-x64\BinSkim.Sdk.dll 1 File(s) copied C:\binskim-master\binskim\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\linux-x64\BinSkim.Sdk.dll 1 File(s) copied ...Het buildproces maakt een set mappen met de uitvoerbare BinSkim-bestanden. Ga naar de win-x64 build-uitvoermap.
C:\binskim-master\binskim> Cd \binskim-master\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\win-x64>Help weergeven voor de analyseoptie.
C:\binskim-master\binskim\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\win-x64> BinSkim help analyze
BinSkim PE/MSIL Analysis Driver 1.6.0.0
--sympath Symbols path value, e.g., SRV*http://msdl.microsoft.com/download/symbols or Cache*d:\symbols;Srv*http://symweb. See
https://learn.microsoft.com/windows-hardware/drivers/debugger/advanced-symsrv-use for syntax information. Note that BinSkim will clear the
_NT_SYMBOL_PATH environment variable at runtime. Use this argument for symbol information instead.
--local-symbol-directories A set of semicolon-delimited local directory paths that will be examined when attempting to locate PDBs.
-o, --output File path to which analysis output will be written.
--verbose Emit verbose output. The resulting comprehensive report is designed to provide appropriate evidence for compliance scenarios.
...
Het symboolpad voor BinSkim instellen
Als u alle code bouwt die u analyseert op dezelfde computer waarop u BinSkim uitvoert, hoeft u meestal het symboolpad niet in te stellen. Dit komt doordat uw symboolbestanden beschikbaar zijn in het lokale vak waarin u hebt gecompileerd. Als u een complexer buildsysteem gebruikt of uw symbolen omleidt naar een andere locatie (niet naast het gecompileerde binaire bestand), gebruikt u --local-symbol-directories om deze locaties toe te voegen aan het zoeken naar symbolen.
Als uw code verwijst naar een gecompileerd binair bestand dat geen deel uitmaakt van uw code, kan het windows-foutopsporingsprogramma worden gebruikt om symbolen op te halen om de beveiliging van deze codeafhankelijkheden te controleren. Als u een probleem in deze afhankelijkheden vindt, kunt u deze mogelijk niet oplossen. Maar het kan handig zijn om rekening te houden met mogelijke beveiligingsrisico's die u accepteert door deze afhankelijkheden op te nemen.
Fooi
Wanneer u een symboolpad toevoegt (dat verwijst naar een netwerksymboolserver), voegt u een lokale cachelocatie toe om een lokaal pad op te geven om de symbolen in de cache op te geven. Als je dit niet doet, kan dat de prestaties van BinSkim aanzienlijk beïnvloeden. In het volgende voorbeeld wordt een lokale cache opgegeven bij d:\symbols.
--sympath Cache*d:\symbols;Srv*http://symweb Voor meer informatie over symboolpaden, zie Symboolpad voor Windows-foutopsporingsprogramma's.
Voer de volgende opdracht uit om een binair gecompileerd stuurprogramma te analyseren. Werk het doelpad bij zodat dit naar je gecompileerde driver .sys bestand verwijst.
C:\binskim-master\binskim\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\win-x64> BinSkim analyze "C:\Samples\KMDF_Echo_Driver\echo.sys"Voor meer informatie voegt u de verbose optie als volgt toe.
C:\binskim-master\binskim\bld\bin\AnyCPU_Release\Publish\netcoreapp2.0\win-x64> BinSkim analyze "C:\Samples\KMDF_Echo_Driver\osrusbfx2.sys" --verboseNotitie
De optie --uitgebreid geeft expliciete resultaten voor geslaagde/mislukte controles weer. Als u geen uitgebreide gegevens opgeeft, ziet u alleen de defecten die BinSkim detecteert. De optie --verbose wordt meestal niet aanbevolen voor echte automatiseringssystemen vanwege de toegenomen grootte van logbestanden en omdat het moeilijker wordt om individuele fouten te identificeren wanneer ze zich voordoen, omdat ze zich bevinden te midden van een groot aantal 'pass'-resultaten.
Bekijk de uitvoer van de opdracht om te zoeken naar mogelijke problemen. In deze voorbeelduitvoer ziet u drie tests die zijn geslaagd. Aanvullende informatie over de regels, zoals BA2002, is beschikbaar in de BinSkim-gebruikershandleiding.
Analyzing... Analyzing 'osrusbfx2.sys'... ... C:\Samples\KMDF_Echo_Driver\osrusbfx2.sys\Debug\osrusbfx2.sys: pass BA2002: 'osrusbfx2.sys' does not incorporate any known vulnerable dependencies, as configured by current policy. C:\Samples\KMDF_Echo_Driver\Debug\osrusbfx2.sys: pass BA2005: 'osrusbfx2.sys' is not known to be an obsolete binary that is vulnerable to one or more security problems. C:\Samples\KMDF_Echo_Driver\osrusbfx2.sys: pass BA2006: All linked modules of 'osrusbfx2.sys' generated by the Microsoft front-end satisfy configured policy (compiler minimum version 17.0.65501.17013).Deze uitvoer laat zien dat test BA3001 niet wordt uitgevoerd omdat het hulpprogramma aangeeft dat het stuurprogramma geen BINAIR ELF-bestand is.
... C:\Samples\KMDF_Echo_Driver\Debug\osrusbfx2.sys: notapplicable BA3001: 'osrusbfx2.sys' was not evaluated for check 'EnablePositionIndependentExecutable' as the analysis is not relevant based on observed metadata: image is not an ELF binary.Deze uitvoer toont een fout voor test BA2007.
... C:\Samples\KMDF_Echo_Driver\Debug\osrusbfx2.sys: error BA2007: 'osrusbfx2.sys' disables compiler warning(s) which are required by policy. A compiler warning is typically required if it has a high likelihood of flagging memory corruption, information disclosure, or double-free vulnerabilities. To resolve this issue, enable the indicated warning(s) by removing /Wxxxx switches (where xxxx is a warning id indicated here) from your command line, and resolve any warnings subsequently raised during compilation.
Als u deze waarschuwingen wilt inschakelen in Visual Studio, verwijdert u onder C/C++ op de eigenschappenpagina's voor het project de waarden die u niet wilt uitsluiten in Specifieke waarschuwingen uitschakelen.
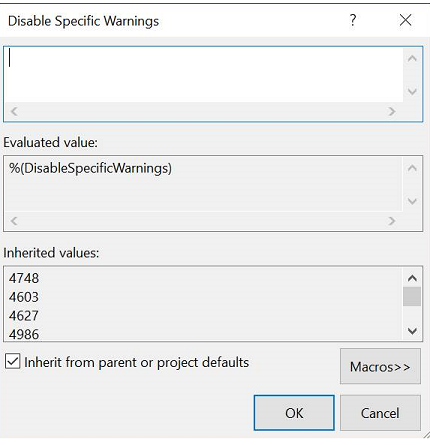
Met de standaardcompilatieopties in Visual Studio voor stuurprogrammaprojecten kunnen waarschuwingen zoals de volgende worden uitgeschakeld. Deze waarschuwingen worden gerapporteerd door BinSkim.
C4627 - 'description': overgeslagen bij het zoeken naar vooraf gecompileerde headers
C4986 - 'declaratie': uitzonderingsspecificatie komt niet overeen met de vorige declaratie
Zie Compilerwaarschuwingen per compilerversievoor meer informatie over de compilerwaarschuwingen.