Part 4b: Windows Server 2012 R2 AD FS - Federated Web SSO
This is Part 4b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution using Windows Server 2012 R2's AD FS role and the Web Application Proxy. In this part I will deploy FABRIKAM's SharePoint Foundation 2013 SP1 web server. I broke this part into 4a and 4b because installing SharePoint requires so many steps that I broke this post into two parts; CONTOSO's SharePoint installation and FABRIKAM's SharePoint installation. In case you missed it:
Here is Part 1 - Overview
Here is Part 2 - Installing AD DS, AD CS, and DNS Records
Here is Part 3 - Installing SQL Database Services
Here is Part 4a - Installing CONTOSO's SharePoint Services
Topology
The following topology highlights in yellow the two servers that will be built for parts 4a and 4b and where they fit into the overall topology. If you wish to see the full topology click here.
Deploy FABRIKAM's SharePoint Foundation 2013 SP1 Server
The following steps will deploy SharePoint Foundation 2013 SP1 server. If you are deploying a different version of SharePoint consult the documentation of the version you are installing. IMPORTANT: You must use SharePoint Foundation 2013 with SP1 to successfully install SharePoint Foundation 2013 on Windows Server 2012 R2. You can read more about the hardware and software requirements here.
- Log into the FABRIKAM domain controller (FABR-DC01) and create a new Domain User called srv_SP.
- Log into the FABRIKAM SQL server (FABR-SQ01) and give srv_SP sysadmin rights.
- Open SQL Server Management studio > Security > Logins > New Login > Search > Locations > Entire Directory > OK
- Type srv_SP > OK
- Select Server Roles > Check sysadmin > OK
- In a production environment the rights should be modified to give the service account the least permissions necessary after SharePoint is deployed.
- Deploy a Windows Server 2012 R2 workgroup server and configure the IP addess, subnet mask, hostname, and DNS servers. For the purposes of this series the information will be as follows:
- Hostname: FABR-SP01
- IP Address: 192.168.30.22
- Subnet Mask: 255.255.255.0
- DNS Servers: 192.168.30.20
- Join the fabrikam.com domain
- After rebooting, log into the server using FABRIKAM domain credentials (i.e. FABRIKAM\Administrator)
- Disable Internet Explorer Enhanced Security Configuration (IE ESC)
- Open Server Manager > Local Server > IE Enhanced Security Configuration > Administrators > Off. Note: This should only be performed on lab servers for test purposes.
- If you are installing SharePoint Foundation 2013 SP1 to a Virtual Machine I recommend you take a snapshot of the Virtual Machine at this point so that in the event that the SharePoint install fails, you can revert to snapshot and try again vs. having to reinstall the Virtual Machine's Operating System.
- Insert the Windows Server 2012 R2 installation media then run the following command from an elevated PowerShell window: Add-WindowsFeature Net-Framework-Core -Source <driveletter>:\sources\sxs. This will add .NET Framework 3.5 to the server.
- At this point I recommend you temporarily configure the server with an IP address that can reach the Internet since the prerequisite installer will attempt to connect to the Internet for most of the prerequisites. After obtaining the prerequisites or providing a means for the server to reach the Internet proceed to the next step.
- Insert the SharePoint Foundation 2013 SP1 installation media then right click > Run as administrator on the prerequisiteinstaller executable to start the installation.
- Click Next > I Accept > Next > to begin the prerequisites installation.
- Click Finish to reboot the server when prompted.
- The prerequisites installer will install more prerequisites then click Finish to reboot when prompted.
- Click Finish once the prerequisites have successfully installed, the server will reboot again.
- Click Finish to complete the prerequisites installation.
- At this point change the IP address back to the lab subnet if needed. For this blog I changed the IP address back to 192.168.30.22/24 with a DNS server IP address of 192.168.30.20.
- Double click Setup from the SharePoint Foundation 2013 SP1 media to begin the installation SharePoint.
- Click I Accept > Continue > Select Complete > Install Now
- Click Close to run the SharePoint configuration wizard
- Click Next > Yes > Create a new server farm > Next.
- For the Database server type FABR-SQ01
- For the Username type FABRIKAM\srv_SP, enter the Password then click Next
- Enter a passphrase when prompted then click Next.
- Select Negotiate (Kerberos) then click Next
- Click Yes to use Kerberos > Next > after the installation is complete click Finish.
- Select whether you wish to participate in the Customer Experience Improvement Program then click OK.
- You should now be able to view FABRIKAM's Central Admin page as shown in the following Figure.
Configure FABRIKAM's SharePoint Foundation 2013 SP1 Server
The following steps will complete the configuration of FABRIKAM's SharePoint server and will create the SharePoint Application that will later be used by federated users.
- From the Central Administration page shown in the preceding Figure, click Start the Wizard
- Select Use an existing managed account, leave everything else at their defaults then click Next. Note: A new account should be used here for a production environment
- Once the farm is created enter the following information to create a site Collection
- Title: FABRIKAM SharePoint
- Description: FABRIKAM's Portal
- Template: Team Site
- Click OK
- Click Finish
- Click Application Management > Configure Alternate Access Mappings
- Highlight https://fabr-sp01 as shown in the following figure then click Edit Public URLs
- Under Alternate Access Mapping Collection change "No Selection" to SharePoint - 80
- Type https://www.fabrikam.com for the Default URL then click Save.
- Click Application Management > Manage Web Applications > Highlight SharePoint -80 > Authentication Providers
- Click Default then click Enable Anonymous Access
- Ensure Integrated Windows authentication is set to Negotiate (Kerberos) then click Save
- Close the dialogue box then click Anonymous Policy. Select Deny Write - Has no write Access then click Save.
- Open an Elevated PowerShell window and type the following command: Get-Certificate -Template WebServer -DnsName www.fabrikam.com -CertStoreLocation cert:\LocalMachine\My
- You should now have a web server certificate with a subject name of www.fabrikam.com
- Configure IIS Bindings for the new certificate
- Open IIS Manager > Expand Sites > Highlight SharePoint - 80 > Click Bindings
- Click Add > https
- Select the certificate you just obtained then click OK > Close
- Open an elevated PowerShell command prompt and type the following command setspn -S HTTP/www.fabrikam.com srv_SP
- Open a web browser and type the following URL: https://www.fabrikam.com. If you get a username/password prompt enter FABRIKAM\Administrator and the Password then click OK.
- The portal should appear as shown in the following Figure.
- Click the gear icon in the upper right corner > Site Settings > Site Permissions
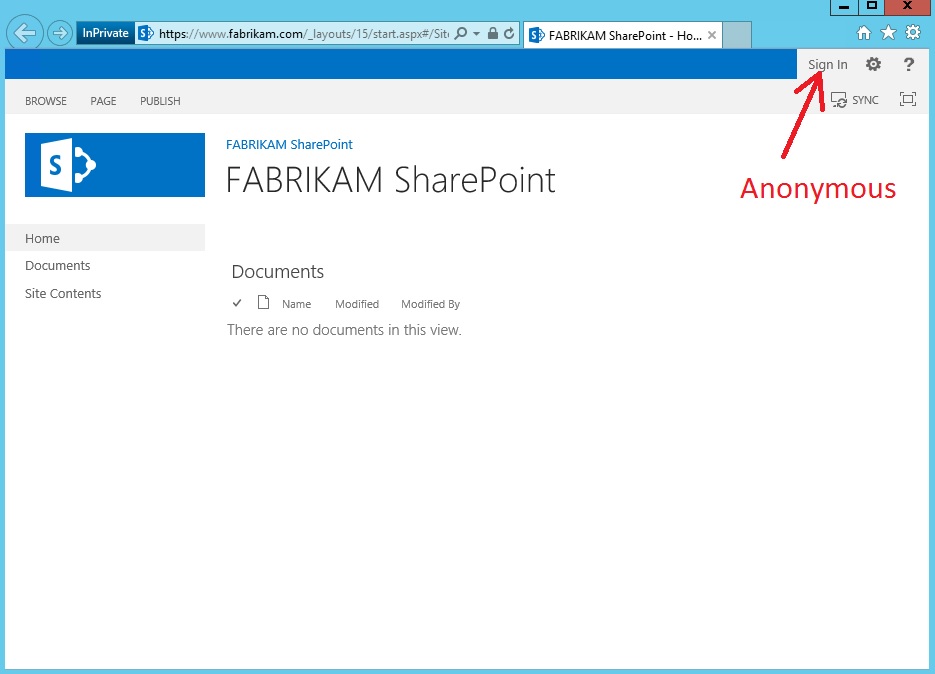
- Click Anonymous Access > Anonymous users can access > Entire Web Site > Click OK
- Clear out all cookies and close and re-open the browser. You should now be able to view FABRIKAM's SharePoint portal anonymously. As shown in the following Figure.
Wrap-Up
You now have two forests one named contoso.com and one named fabrikam.com along with the DNS records, certificate services, database services, CONTOSO's SharePoint Foundation 2013 SP1 services, and FABRIKAM's SharePoint Foundation 2013 SP1 needed to support AD FS. In the upcoming parts the CONTOSO's and FABRIKAM's federation services and Web Application Proxies will be deployed and configured to support federated web SSO.
Troubleshooting
- If you cannot connect to the SQL server and the Windows Firewall is enabled ensure port TCP 1433 is enabled inbound on the Windows Firewall as per the following instructions.
- If SharePoint fails to install with an error stating that it cannot configure the Application IIS server ensure you are installing a version of SharePoint 2013 with SP1 integrated into it.
- If the installation of SharePoint fails half way through the install, verify that the service account has at least DB Owner on the SQL server for the target database
- If you get an error when attempting to obtain a certificate ensure that Domain Computers have rights to read the Web Server template
- If you get an error when attempting to obtain a certificate ensure thatthe CRL has not expired
- If you get repeated password prompts when viewing the portal even after it is set to anonymous, ensure the Web Application is set to Negotiate (Kerberos)
- If the page displays page not found ensure you created an A record for the site in DNS
Comments
- Anonymous
January 01, 2003
thanks - Anonymous
September 16, 2014
This is Part 4a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 16, 2014
Overview
The purpose of this series is to walk you through step-by-step from start to finish setting - Anonymous
September 25, 2014
This is Part 5a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 25, 2014
This is Part 5b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
February 16, 2015
This is Part 6a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 26, 2015
This is Part 6b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 27, 2015
This is Part 7 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 8 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 9 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution