Part 1: Windows Server 2012 R2 AD FS - Federated Web SSO
Overview
The purpose of this series is to walk you through step-by-step from start to finish setting up Federated Web Single Sign On (SSO) between two organizations using Windows Server 2012 R2's AD FS role, Windows Server 2012 R2's Web Application Proxy role, and SharePoint 2013. Additionally the end result will be a highly available AD FS deployment with fault tolerance and load balancing for the AD FS and Web Application Proxy (WAP) components. In case you missed it;
Part 2 - Deploying Domain Controllers, Certificate Services, DNS Records
Part 3 - Installing SQL 2014
Part 4a - Installing CONTOSO's SharePoint Services
Part 4b - Installing FABRIKAM's SharePoint Services
Part 5a - Installing CONTOSO's Federation Services
Part 5b - Installing FABRIKAM's Federation Services
Part 6a - Installing CONTOSO's Web Application Proxy Services
Part 6b - Installing FABRIKAM's Web Application Proxy Services
Part 7 - Installing External DNS and Workstations
Part 8 - Creating the circle of trust
Part 9 - Completed Configuration / Testing / Troubleshooting
Background
AD FS provides simplified, secured identity federation and Web single sign-on (SSO) capabilities for end users who want to access applications within an AD FS-secured enterprise, in federation partner organizations, or in the cloud (TechNet, 2014).
In Windows Server® 2012 R2, AD FS includes a federation service role service that acts as an identity provider (authenticates users to provide security tokens to applications that trust AD FS) or as a federation provider (consumes tokens from other identity providers and then provides security tokens to applications that trust AD FS) (TechNet, 2014).
The function of providing extranet access to applications and services that are secured by AD FS is now performed by a new Remote Access role service called Web Application Proxy. This is a departure from the prior versions of Windows Server in which this function was handled by an AD FS federation server proxy. Web Application Proxy is a server role designed to provide access for the AD FS-related extranet scenario and other extranet scenarios (TechNet, 2014).
For additional reading on Windows Server 2012 R2 AD FS see the following links:
Active Directory Federation Services Overview: https://technet.microsoft.com/en-us/library/hh831502.aspx
Web Application Proxy: https://technet.microsoft.com/en-us/library/dn584107.aspx
Intended Audience
This series is mainly intended for system administrators who want to build a Windows Server 2012 R2 AD FS lab environment for the purposes of learning how to deploy Windows Server 2012 R2's AD FS in a lab or production environment. It may also prove useful for system administrators when they are troubleshooting a production deployment of Windows Server 2012 R2's AD FS.
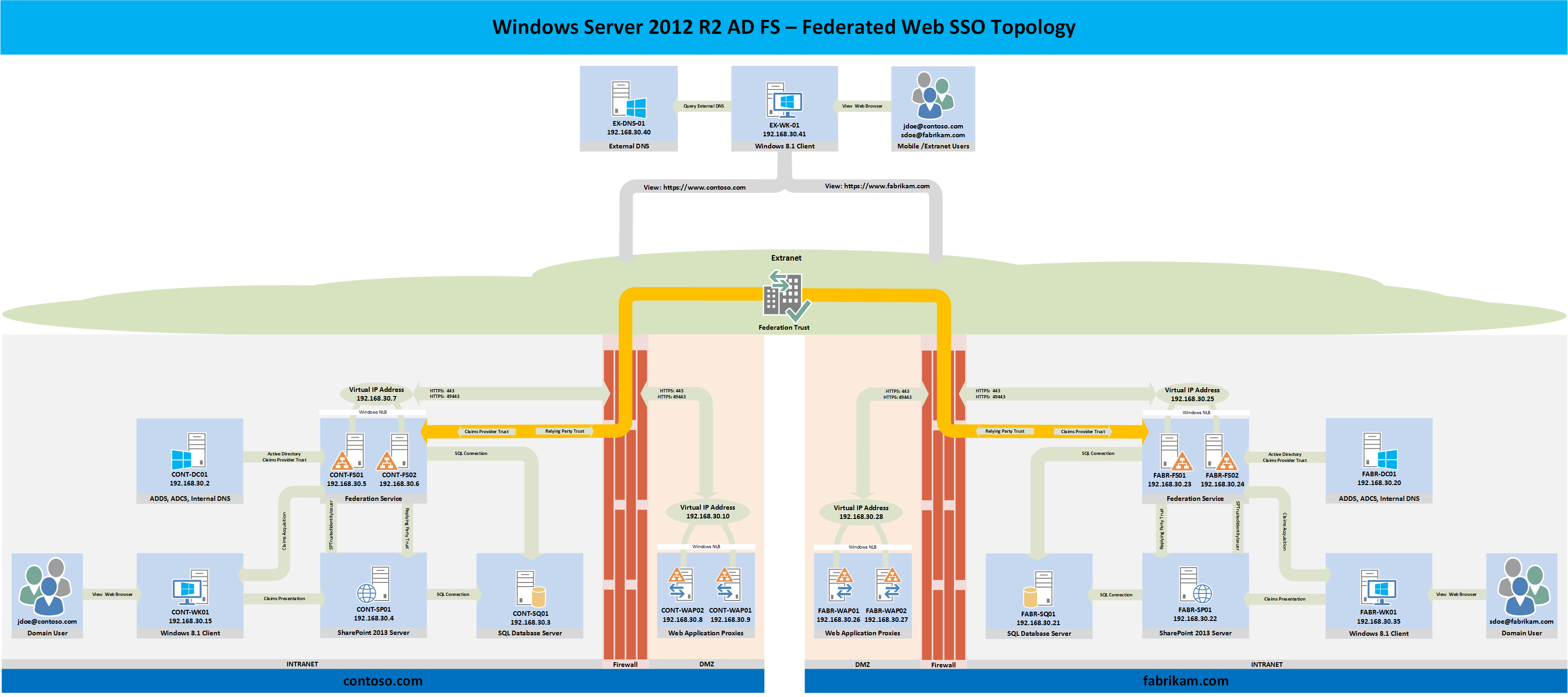
Topology
There are many components to a successful AD FS Federated Web SSO deployment and I find it useful to first draw out the planned deployment's topology prior to the deployment. As such the reference topology for this blog series is below. Every component in the following diagram will be built from the ground up as a part of this series with the exception of the firewalls. If you are integrating AD FS into an existing Windows Server 2012 R2 lab or production environment, some of the components that are shown in the following diagram will probably already exist in the planned environment.
Although firewalls are shown in the following topology diagram, they will not be deployed as a part of this series due to the fact that there are many firewall vendors to choose from so it would be unproductive to cover the steps necessary to deploy a specific firewall for this specific topology. The firewall ports necessary to publish the Web Application Proxy and Federation Service through a firewall are shown. Port 49443 is only necessary if the solution must support client certificate credentials. More information regarding port 49443 can be found here.
All of the Windows Server 2012 R2 AD FS role servers and the Web Application Proxy services in the topology below are deployed in a highly available configuration. The rest of the services are deployed in a minimal capacity to support the main focus of this series which is AD FS. For production environments, it is important to deploy each service based on the organization's specific service availability requirements.
CONTOSO Configuration
The following Tables illustrate the planned CONTOSO configuration.
FABRIKAM Configuration
The following Tables illustrate the planned FABRIKAM configuration.
Conclusion
In the upcoming parts, each component of the topology will be built, tested, and verified to be working before moving to the next component. As you can see, Windows Server 2012 R2 AD FS has a lot of components which are needed to support an end-to-end Federated Web SSO deployment. Some of the information in the preceding tables may change as the topology is built.
Here is Part 7 - Installing External DNS and Workstations
Here is Part 8 - Creating the circle of trust
Comments
- Anonymous
January 01, 2003
good article, thanks. - Anonymous
August 29, 2014
This is Part 2 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 02, 2014
This is Part 3 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 11, 2014
Thanks - Anonymous
September 16, 2014
This is Part 4a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 16, 2014
This is Part 4b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 25, 2014
This is Part 5a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
September 25, 2014
This is Part 5b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
February 16, 2015
This is Part 6a of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
July 06, 2015
Hi, would you share you topology diagram is Visio format? - Anonymous
October 26, 2015
This is Part 6b of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 27, 2015
This is Part 7 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 8 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution - Anonymous
October 28, 2015
This is Part 9 of a multi-part series on how to deploy a complete end-to-end Federated Web SSO solution