Screencast: Mad About MED-V Part 1 of 4, Concept and Architecture

Microsoft Enterprise Desktop Virtualization, or MED-V, is a desktop virtualization solution providing a self-contained computing environment including the OS, intended applications, and customized settings, if any. Desktop virtualization allows an application to run in a specific OS environment different from the OS running the hosting computer. MED-V uses Virtual PC 2007 to provide a virtualized and customizable computing environment required by an intended application, yet incompatible or conflicting with that in the hosting computer. In other words, MED-V allows computing environments which are incompatible, conflicting, or with different requirements to run currently in the same physical device. For instance, running a legacy or line-of-business application requiring Windows XP SP2 in a Vista SP1 desktop or deploying a managed computing environment (like a corporate-managed desktop) to a non-managed (like a personal or home) desktop are some of the business challenges MED-V addresses.
MDOP now includes 6 tools and solutions as below and is available to Software Assurance customers.
- Diagnostics and Recovery Toolset
- Asset Inventory Service (AIS)
- Advanced Group Policy Management
- System Center Desktop Error Monitoring
- Application Virtualization (App-V)
- Enterprise Desktop Virtualization (MED-V)
Customers interested in MDOP should review the faq and contact their software vendor or Microsoft for additional information. For a comprehensive guide on Microsoft Virtualization from data center to desktop, download it here. I have produced the 4-part Mad About MED-V screencast series to offer a quick review of MED-V solutions including the following. I will update each link, once the associated screencast is published.
- Part 1, Concept and Architecture (this posting)
- Part 2, User Experience
The following is the part 1 screencast with a focus on the MED-V fundamentals to establish a baseline for subsequent discussions in the series. The remaining of this post highlights the key concept, architecture, and pertinent information of a MED-V solution.
Desktop and Application Virtualization Concepts
MED-V is perhaps the least understood piece in Microsoft Virtualization Solutions. A desktop virtualization solution MED-V is as opposed to App-V, an application virtualization. This distinction is an important one since they solve two different areas of business problems. Desktop virtualization addresses the incompatibility between a target application and the host operating system by virtualizing an entire desktop, i.e. a self-contained runtime environment including the operating system and the application. Such that a target application requiring, for instance, Windows XP SP2 and incompatible with Windows Vista can still be deployed to a Vista desktop by running the application in a hidden Virtual PC running Windows XP SP2 while using MED-V to seamlessly make the application accessible from the Start-All Programs menu on the host computer. App-V, on the other hand solves the incompatibility between two applications by offering a virtualized application runtime environment, the so-called bubble, while allowing these applications running on the same operating system instance. The following illustrates the concept.
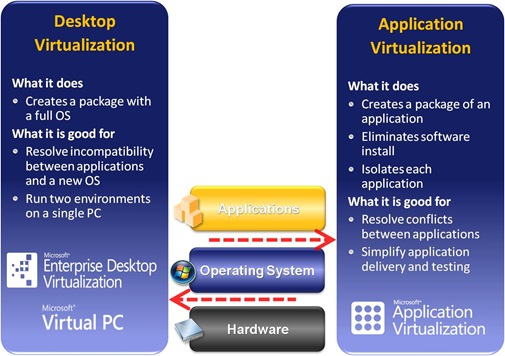
Conceptually desktop virtualization using Virtual PC is easy to understand. Nevertheless to deploy desktop virtualization to enterprise, system administration and scalability are rather challenging. In essence, a Virtual PC lifecycle management solution is the key to make enterprise desktop virtualization a reality, and this is where MED-V comes in. MED-V makes Virtual PC deployable and saleable with a centralized lifecycle management solution including: image creation, delivery, monitoring, and maintenance.
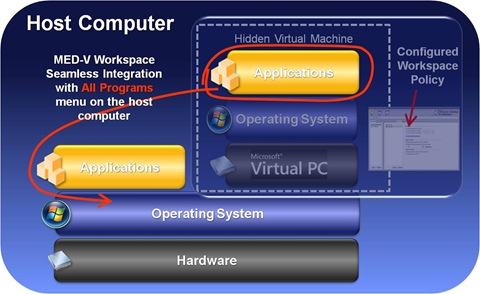
MED-V Conceptual Model
To run a MED-V application the associated workspace must be first started. And if a user tries to start a MED-V application while the workspace is not in place, the workspace will start on demand and once the workspace is loaded, the application will start. A workspace is a Virtual PC image with a usage policy defined by a MED-V administrator. An administrator will use MED-V management console to configure usage policy which is a set of settings defining how MED-V applications will behave for a target Active Directory users or groups. Notice that the Virtual PC is where a MED-V application is configured, and the Virtual PC is also running in the background. MED-V workspace policy allows a MED-V application to seamlessly integrate into the All Programs menu on the host computer and runs transparently with the locally installed applications. A conceptual model of the integration is shown below.
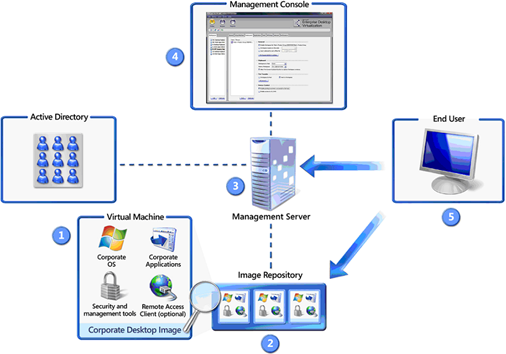
MDE-V Architecture
The high level MED-V architecture as shown below starts with: (1) and (2) to create, test and upload Virtual PC images encapsulating a target computing environment of an OS, applications and optional management and security tools to the image repository by administrator; (3) MED-V Management Server, the brain of the whole system, enabling an administrator to control image repository which is an IIS virtual directory and (4) provision images for targeted Active Directory Users and Groups along with usage policies; and finally (5) delivering the images and usage policies to clients. And a client starts a MED-V application, the client will authenticate against the management server, retrieve the workspace policy, and acquire the workspace image.
Notice a MED-V Management Server also aggregates clients' events, and stores them in an external database (MS SQL) for monitoring and reporting purposes. Also a MED-V client has two functional components – the first connecting to the server and retrieving the usage policy and an associated image form the repository, while the second offering the end-user experience and managing the Virtual PC from user experience and troubleshooting aspects.
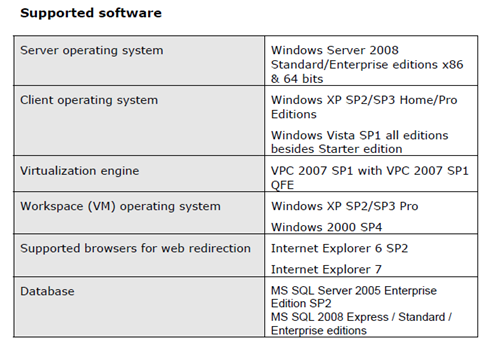
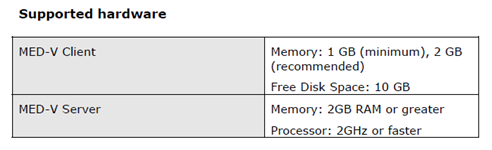
System Requirements
The information provided here is as of March of 2009.
Antivirus/Backup Software
In order to prevent antivirus activity from affecting the performance of the virtual desktop, it is recommended where possible to exclude the following Virtual Machine file types from any antivirus or backup processing running on the host:
*.VHD
*.VUD
*.VSV
*.CKM
*.VMC
*.INDEX
MED-V Trim Transfer™ Technology
One very interesting piece of MED-V solution is the Trim Transfer technology as illustrated below. Trim Transfer accelerates the download of initial and updated Virtual Machine images over the LAN or WAN, thereby reducing the network bandwidth needed to transport a Workspace Virtual Machine to multiple end-users. It uses existing local data to build the Virtual Machine image, leveraging the fact that in many cases, much of the Virtual Machine (e.g., system and application files) already exists on the end-user's disk. For example, if a Virtual Machine containing Microsoft Windows XP is delivered to a client running a local copy of Windows XP, MED-V will automatically remove the redundant Windows XP elements from the transfer. To ensure a valid and functional Workspace, the MED-V Client cryptographically verifies the integrity of local data before it is utilized, guaranteeing that the local blocks of data are absolutely bit-by-bit identical to those in the desired Virtual Machine image. Blocks that do not match are not used.
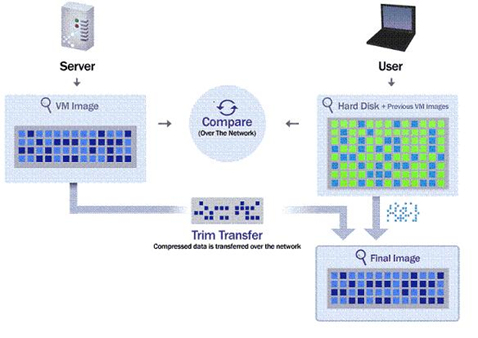
The process is bandwidth efficient and transparent, and transfers run in the background, utilizing unused network and CPU resources. When updating to a new image version (e.g., when administrators want to distribute a new application or patch), only the elements that have changed ("deltas") are downloaded, and not the entire Virtual Machine, significantly reducing the required network bandwidth and delivery time.
You can configure which folders are indexed on the host as part of the Trim Transfer protocol according to the host OS. These setting are configured in the ClientSettings.xml file which can be found in the Servers\Configuration Server\ folder.