Identity Flow Through Physical Tiers
Identity story with .Net really rocks, but along with great extensibility it also brings a lots of confusion (One Identity - Many Faces :IIdentity).
I am building now workshop for developers that concentrates on authentication only. It talks about concepts, implementation, scenarios, and of course a bit of hacking exposed - entertaining part never hurts :)
I plan to allocate some time for .Net identity implementation, based on IIdentity, in conjunction with what Windows System provides.
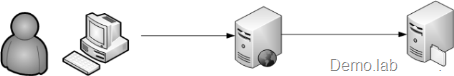
My first scenario is simple one where user sits behind her machine A access simple ASPX page on box B that access file on share on box C, like this:
Everything is managed by Windows 2003 Active Directory Domain - Demo.lab
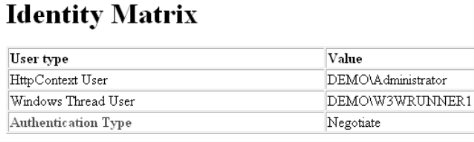
User name is DEMO\Administrator.
Web application runs under DEMO\W3WRUNNER1 service account, specified in application pool configuration.
Web site is set to use Window authentication in web.config and IIS is configured for Windows authentication.
What user runs the app's security context?
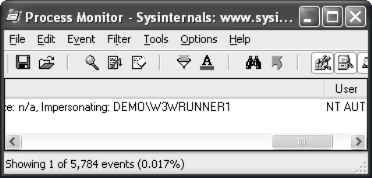
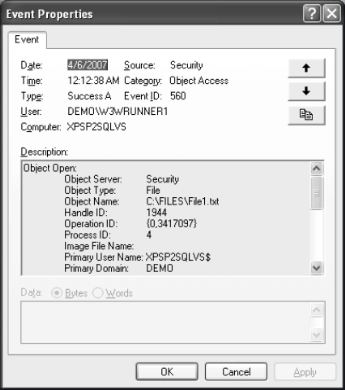
Under what account the file on box C is accessed?
To answer the first question I echo back the following data (meaning there is no single answer for it)
lblHttpCoontextUser.Text = User.Identity.Name;
lblWindowsThreadUser.Text = WindowsIdentity.GetCurrent().Name;
lblAuthType.Text = User.Identity.AuthenticationType;
And to answer the second question I use techniques described in File Access Auditing - I Am Not Afraid Of GPO and Who Access My File?
and/or
Enjoy
Comments
- Anonymous
April 06, 2007
There are scenarios where actual windows identity of end user needs to be flowed to the server so that - Anonymous
April 08, 2007
If these articles: How To: Implement Kerberos Delegation for Windows 2000 How To: Use Impersonation and - Anonymous
April 10, 2007
If these articles: How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0 Using Protocol - Anonymous
April 11, 2007
Windows Authentication Identity Flow Through Physical Tiers Identity Flow Through Physical Tiers - Impersonation