File Access Auditing - I Am Not Afraid Of GPO
Security logging and auditing mitigates repudiation threat (the "R" in STRIDE, see also Auditing and Logging threats). The lesser coding the better security. Here is the no coding auditing for file access using Group Policy
From https://support.microsoft.com/kb/324739
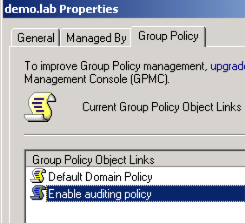
Create a Group Policy Object
To create a Group Policy object (GPO) that you can use to turn on auditing in a domain, follow these steps:
1. Click Start, point to Administrative Tools, and then click Active Directory Users and Computers.
2. Right-click your domain, and then click Properties.
3. Click the Group Policy tab, and then click New.
4. Type the name that you want to use for this policy (for example, Enable auditing policy), and then press ENTER.
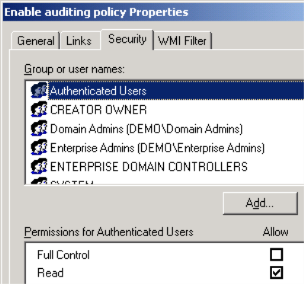
5. Click Properties, and then click the Security tab.
6. Click to clear the Allow check box next to Apply Group Policy for the security groups that you want to prevent from having this policy applied.
7. Click to select the Allow check box next to Apply Group Policy for the groups to which you want to apply this policy, and then click OK.
8. Click OK, click OK again, and then quit Active Directory Users and Computers.
Turn On Auditing on a Domain Controller
1. Click Start, point to Administrative Tools, and then click Active Directory Users and Computers.
2. Right-click your domain, and then click Properties.
3. Click the Group Policy tab, click the Group Policy object that you want to use, and then click Edit.
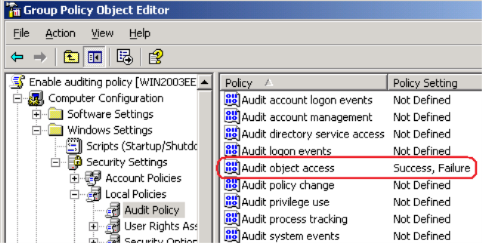
4. Under Computer Configuration, expand Windows Settings, expand Security Settings, expand Local Policies, and then click Audit Policy.
5. In the right pane, double-click Audit object access.
6. Click to select the Define these policy settings check box, click to select the Success check box, click to select the Failure check box, and then click OK.
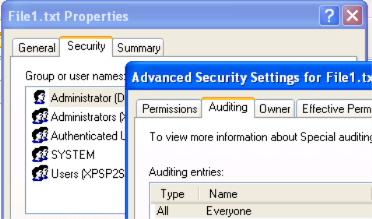
Define auditing on actual file:
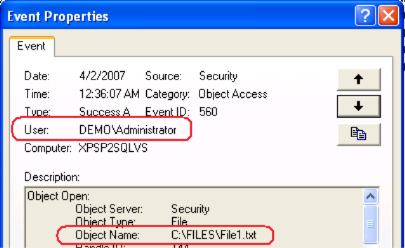
Test auditing by accessing the file, say double clicking it, then open Event Viewer.
Similar entry should be there:
Enjoy
Comments
- Anonymous
April 03, 2007
In my post File Access Auditing - I Am Not Afraid Of GPO I've digested technet documentation on how to - Anonymous
April 05, 2007
Identity story with .Net really rocks, but along with great extensibility it also brings a lots of confusion - Anonymous
April 08, 2007
If these articles: How To: Implement Kerberos Delegation for Windows 2000 How To: Use Impersonation and - Anonymous
April 10, 2007
If these articles: How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0 Using Protocol - Anonymous
April 10, 2007
If these articles: How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0 Using Protocol - Anonymous
January 21, 2008
A few years ago, I recall needing to know (programmatically) which user has accessed a particular file