Secure by default with Microsoft Purview and protect against oversharing - Phase 1
This guide is divided into four phases:
- Introduction
- Phase 1: Foundational – Start with recommended labels (this page)
- Phase 2: Managed – Address files with highest sensitivity
- Phase 3: Optimized – Expand to your entire Microsoft 365 data estate
- Phase 4: Strategic – Operate, expand, and retroactive actions
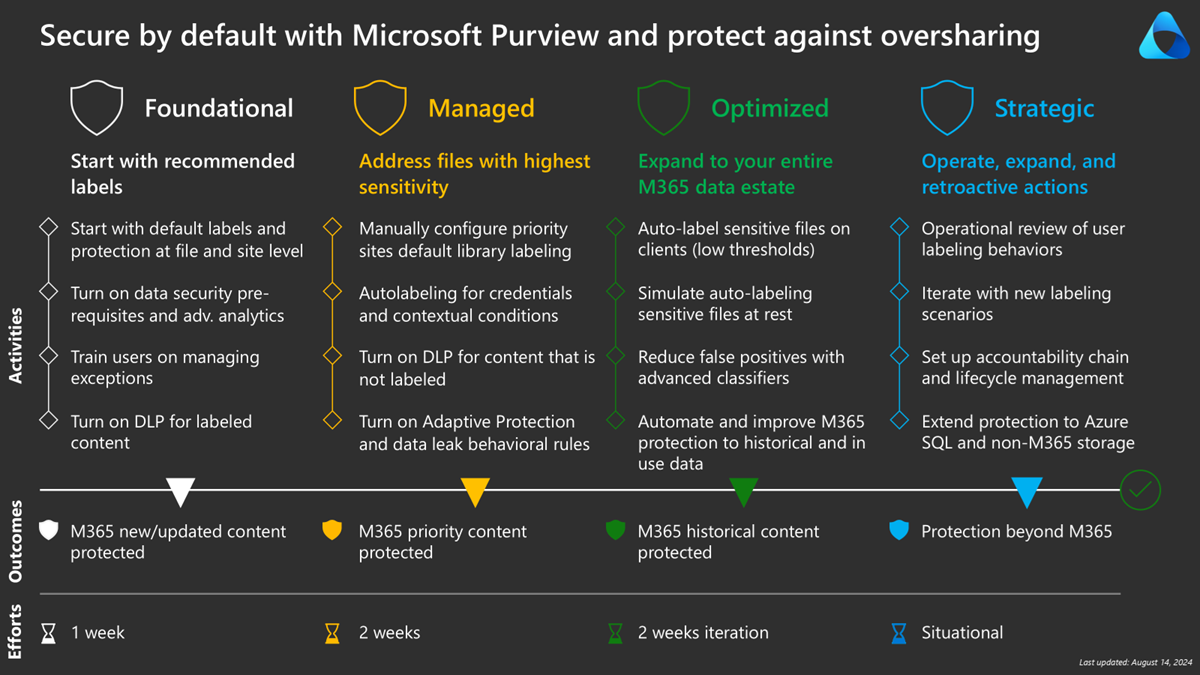
Phase 1: Foundational - Start with recommended labels
Sensitivity labels are organizational tags that are meaningful and intuitive to end users. They're integrated and consistent across Microsoft solutions and non-Microsoft solutions such as Adobe Acrobat Reader.
Protection policies on labels vary based on the data asset. For example:
- Encryption and Dynamic Watermarking on supported file types
- Conditional Access controls and privacy for SharePoint sites and Teams
- Permission control on Azure SQL Databases, Azure Storage and Amazon Web Services (AWS) S3
The strategy for applying labels often starts with manual labeling, then client-side auto-labeling with Sensitive Information Types (SIT), followed by service-side auto-labeling (at rest) with SIT and contextual conditions. SharePoint also offers a contextual default label per library, which we cover in more detail in this guide.
Start with default labels and protection at file and site level
We recommend starting with the following definition for most customers. These recommended labels can be adapted if you have an existing deployment, and iterated later with more scenarios.
At the top level, we recommend starting with the following labels:
- Public - Public data is unrestricted data meant for public consumption, like publicly released source code and announced financials. Share it freely.
- General - Business data that isn't meant for public consumption, such as daily work product. Data that can be shared internally and with trusted partners.
- Confidential - Sensitive business data crucial to achieving your organizational goals. Limited distribution.
- Highly confidential - Your most critical data. Share it only with named recipients.
Note
For organizations accepting personal content on managed devices, we recommend defining a Non-business or Personal label at the lowest priority and without protection.
For Confidential and Highly confidential, we add the following sublabels:
- \All Employees - Data can be accessed by anyone within your organization.
- \Specific People - Data can only be accessed by the specified people.
- \Internal exception - Data can be accessed by anyone internally but prevented from being shared externally. Use this label in situations where encryption is impacting daily operations.
For a complete list of parent/child labels with recommended configurations, refer to this table:
| Label name | Label description for users | Settings |
|---|---|---|
| Public | Business data that is prepared and approved for public consumption. | Scope: Items (File, Email) Content marking: No Auto-labeling: No Data Loss Prevention: None |
| General | Business data that isn't intended for public consumption. However, this can be shared with external partners, as required. | This label is selected as the default label for emails. This label is also selected for sites allowing external partners.Scope: Items (File, Email, Meetings, Sites) Content marking: No Auto-labeling: No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link |
| Confidential \ All Employees |
Confidential data that requires protection, which allows all employees full permissions. Data owners can track and revoke content. | This label is selected as the default label for documents and sites. Scope: Items (File, Email, Meetings, Sites) Encryption: All users and groups in the org: Co-Author Content marking: Footer: Classified as Confidential Auto-labeling: No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link, Block external |
| Confidential \ Specific People |
Confidential data that can be shared with trusted people inside and outside your organization. These people can also reshare the data as needed. | Scope: Items (File, Email, Meetings, Sites) Encryption: Let users assign permissions: - Encrypt-Only for Outlook - Prompt users in Word, PowerPoint, and Excel Content marking: Footer: Classified as Confidential Auto-labeling: No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link |
| Confidential \ Internal exception |
Confidential data that doesn’t need to be encrypted. Use this option with care and appropriate business justification. | This label is selected for confidential information that doesn't need to be encrypted. This can be used as an internal exception when encryption isn't supported with a process or application using this information. Leverage Data Loss Prevention and Insider Risk Management to manage risk and user deviations. Scope: Items (File, Email, Meetings, Sites) Content marking: Footer: Classified as Confidential Auto-labeling:No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link, Block external |
| Highly Confidential \ All Employees |
Highly confidential data that allows all employees view, edit, and reply permissions to this content. Data owners can track and revoke content. | This label is selected for client-side auto-labeling and service-side auto-labeling. Scope: Items (File, Email, Meetings, Sites) Encryption: All users and groups in the org: Co-Author Content marking: Footer: Classified as Highly Confidential Auto-labeling: Automatically apply the label. Consider automatically applying for the highly sensitive All credentials sensitive information types. Site privacy: Private or Public Data Loss Prevention: Block anyone with the link, Block external |
| Highly Confidential \ Specific People |
Highly confidential data that requires protection and can be viewed only by people you specify and with the permission level you choose. | Scope: Items (File, Email, Meetings, Sites) Encryption: Let users assign permissions: - Do Not Forward for Outlook - Prompt users in Word, PowerPoint, and Excel Content marking: Footer: Classified as Highly Confidential Auto-labeling: No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link, Block external |
| Highly Confidential \ Internal exception |
Highly confidential data that doesn’t need to be encrypted. Use this option with care and appropriate business justification. | This label is selected for highly confidential information that doesn't need to be encrypted. This can be used as an internal exception when encryption isn't supported with a process or application using this information. Leverage Data Loss Prevention and Insider Risk Management to manage risk and user deviations. Scope: Items (File, Email, Meetings, Sites) Content marking: Footer: Classified as Confidential Auto-labeling: No Site privacy: Private or Public Data Loss Prevention: Block anyone with the link, Block external |
Secure by default
The recommended labels in this deployment model have a few differences compared to the traditional crawl/walk/run approach or the Default labels and policies to protect your data article:
- Set the default label to Confidential\All Employees for files. For existing files, leverage service-side auto-labeling with contextual condition file extension is for all PPTX/DOCX/XLSX/PDF files for all relevant SharePoint sites.
- Set the default label to General for emails. This reduces deployment friction with users able to function normally, with the exception that confidential files attached to an email inherit the label of the file.
- Controls for default sharing and DLP limits
- Auto-labeling use cases centered around Highly Confidential
- Specific People label, intuitively named and self explanatory
- Internal Exception addresses edge cases where encryption is preventing end users from their daily work.
Highlights and recommendations
- Labels should be intuitively named.
- Avoid mixing terms such as Confidential, Restricted, or Internal together – understanding the different meanings of the terms can be challenging to users.
- We recommend keeping the list of labels to 5x5 whenever possible, that is: up to five parent labels and up to five child labels under a parent.
- Where applicable, labels are used for both files and SharePoint sites.
- Highly Confidential is most often done with auto-labeling and contextual defaults and provides more controls and restrictions.
- Use labels to set your SharePoint sites and Teams privacy to Private by default.
- For organizations using public privacy settings extensively in SharePoint/Teams, we recommend updating to Private and use company-shareable links instead.
- Private SharePoint sites with company-shareable links provide the same collaboration flexibility but reduces the risks of unintended discovery in search and Copilot.
- For more protection, set default sharing to Specific people.
- Create a chain of accountability with site owners. Use reporting and Graph API to identify deviations of use and behaviors.
- Turn on DLP on labeled content, blocking anyone with link and external where applicable. Existing shared content matching those condition blocks, DLP alerts are raised, and policy tips visible to end users.
- Turn on email label inheritance. For more information, see Configure label inheritance from email attachments.
Turn on data security prerequisites and advanced analytics
Microsoft Purview has many capabilities. To reduce impacts to users, some capabilities aren't activated by default. We recommend reviewing the following settings:
- Turn on ability to process content in Office Online: Enable sensitivity labels for files in SharePoint and OneDrive
- Turn on labeling for Microsoft Teams and SharePoint Sites: Use sensitivity labels with Microsoft Teams, Microsoft 365 Groups, and SharePoint sites
- We recommend keeping the label mismatch email label. This feature sends an email to the document owner and site owner about a document that have a higher sensitivity than the site’s sensitivity label. You can confirm it’s not disabled by verifying '-BlockSendLabelMismatchEmail' is set to $False
- Include a help link with '-LabelMismatchEmailHelpLink'
- Enable support for PDF files in OneDrive and SharePoint: Enable sensitivity labels for files in SharePoint and OneDrive
- Mark files as sensitive by default: Prevent guest access to files while DLP rules are applied - SharePoint in Microsoft 365
- DLP analytics: Get started with data loss prevention analytics
- Turn on co-authoring for files with sensitivity labels: Enable co-authoring for encrypted documents
- Turn on Insider Risk Management Indicators: Configure policy indicators in insider risk management
- Turn on Purview audits: Get started with auditing solutions
- Enable integration with Microsoft Entra B2B: SharePoint and OneDrive integration with Microsoft Entra B2B
Company-shareable links or links for specific people
OneDrive and SharePoint sharing is configured via shareable links. Learn more here: How shareable links work in OneDrive and SharePoint in Microsoft 365
For organizations using SharePoint sites with privacy settings set to public, we recommend moving to private with default shareable links set to People in your organization. Open collaboration is available to users, but it reduces automatic content discoverability in enterprise search and Copilot.
Tip
To further reduce risks, we recommend configuring Specific people as your default.
Microsoft Purview Sensitivity Labels allow you to configure the shareable links based on the SharePoint site sensitivity label. For example, this setting greatly facilitates the granular configurations between General and Confidential sites. Learn more here: Use sensitivity labels to configure the default sharing link type
Train users on managing exceptions
With the secure by default approach, training focuses on:
- Making your organization aware of how important it is to secure information by default.
- The importance of labeling at SharePoint sites and how labels affect protection to files and sharing.
- How users can change labels when working with trusted external partners.
- How users can change labels when a line of business application or an add-in doesn't work correctly with encryption.
- Whether to share from OneDrive or SharePoint with trusted external partners, and how to select the appropriate site label.
- Justification required when downgrading labels.
Deriving file labeling from SharePoint site labeling reduces the number of times users must change their label. For example:
- John is sharing a file externally via OneDrive. He then reviews the content and determines that it’s not confidential and changes the label to General. John then shares externally.
- Jane is working with a partner and sharing multiple files. Jane uses SharePoint and labels the site to General. All files within the site can be shared. But if a Confidential file gets uploaded on the site, that file is protected, a notification is sent to Jane about the higher sensitivity file and she can move the file or change the label.
- Jack works in Excel with a partner using an add-in important to business operations. If this add-in is incompatible with encryption, Jack must change the label to Confidential\Internal exception.
Important
There’s an important trade-off to consider between label priority, downgrade and justification, and defaults. For example, assuming General is lower priority than Confidential\All employees, and if your Office client is defaulting to Confidential\All employees, a SharePoint default library label set to General will not apply. Similarly, Confidential\Internal exception set at a higher priority will not require justification. It’s important to review label priorities and justification requirements.
Turn on DLP for labeled content
Microsoft Purview Data Loss Prevention (DLP) provides integration with sensitivity labels, quickly addressing DLP requirements with limited configurations.
As an example, with the recommended labels and default set to Confidential\All employees, we recommend including a DLP rule to block sharing to external and block Anyone with the link. Refer to the recommended label table and the DLP limits column for details at each label.
To learn more about this functionality:
- Use sensitivity labels as conditions in DLP policies
- Data Loss Prevention policy reference
- Data loss prevention Exchange conditions and actions reference
Phase 1 - Summary
At the end of this phase, your organization has:
- Labels available for end users to use manually.
- Default labeling for any new/updated documents and emails.
- User communications and training on about how to manage exceptions, either when sharing or if encryption is causing challenges with their business files.
- DLP preventing the sharing of confidential files.
See also
- Apply encryption using sensitivity labels
- Manage sensitivity labels in Office apps
- End User Training for Sensitivity Labels
- Learn about the default labels and policies to protect your data
Next step: Phase 2: Managed – Address files with highest sensitivity