Adición de un servicio de búsqueda a un perímetro de seguridad de red
Importante
La compatibilidad de Búsqueda de Azure AI con el perímetro de seguridad de red está en versión preliminar pública en los términos de uso complementarios. Está disponible en las regiones que proporcionan la característica. Esta versión preliminar se ofrece sin Acuerdo de Nivel de Servicio y no se recomienda para cargas de trabajo de producción. Es posible que algunas características no sean compatibles o que tengan sus funcionalidades limitadas.
Revise la sección Limitaciones y consideraciones antes de empezar.
En este artículo se explica cómo unir un servicio Búsqueda de Azure AI a un perímetro de seguridad de red para controlar el acceso de red al servicio de búsqueda. Al unir un perímetro de seguridad de red, puede hacer lo siguiente:
- Registre todo el acceso al servicio de búsqueda en contexto con otros recursos de Azure en el mismo perímetro.
- Bloquee cualquier filtración de datos de un servicio de búsqueda a otros servicios fuera del perímetro.
- Permita el acceso al servicio de búsqueda mediante funcionalidades de acceso entrante y saliente del perímetro de seguridad de red.
Puede agregar un servicio de búsqueda a un perímetro de seguridad de red en Azure Portal, como se describe en este artículo. Como alternativa, puede usar la API REST de Azure Virtual Network Manager para unirse a un servicio de búsqueda y usar las API REST de administración de búsquedas para ver y sincronizar las opciones de configuración.
Limitaciones y consideraciones
Para los servicios de búsqueda dentro de un perímetro de seguridad de red, los indexadores deben usar una identidad administrada asignada por el usuario o por el sistema y tener una asignación de roles que permita el acceso de lectura a los orígenes de datos.
Los orígenes de datos del indexador admitidos se limitan actualmente a Azure Blob Storage, Azure Cosmos DB for NoSQL y Azure SQL Database.
Actualmente, dentro del perímetro, las conexiones del indexador a la PaaS de Azure para la recuperación de datos son el caso de uso principal. Para las llamadas API basadas en aptitudes salientes a servicios de Azure AI, Azure OpenAI o el catálogo de modelos de Azure AI Foundry, o para las llamadas entrantes de Azure AI Foundry para escenarios de "chat con los datos", debe configurar reglas de entrada y salida para permitir las solicitudes a través del perímetro. Si necesita conexiones privadas para la fragmentación compatible con la estructura y la vectorización, debe crear un vínculo privado compartido y una red privada.
Requisitos previos
Un perímetro de seguridad de red existente. Puede crear uno para asociarlo al servicio de búsqueda.
Búsqueda de Azure AI, cualquier nivel facturable, en cualquier región.
Asignación de un servicio de búsqueda a un perímetro de seguridad de red
El perímetro de seguridad de red de Azure permite a los administradores definir un límite de aislamiento de red lógico para los recursos PaaS (por ejemplo, Azure Storage y Azure SQL Database) que se implementan fuera de las redes virtuales. Restringe la comunicación a los recursos dentro del perímetro y permite el tráfico público no perimetral a través de reglas de acceso de entrada y salida.
Búsqueda de Azure AI se puede agregar a un perímetro de seguridad de red para que todas las solicitudes de indización y consulta se produzcan dentro del límite de seguridad.
En Azure Portal, busque el servicio de perímetro de seguridad de red de la suscripción.
Seleccione Recursos en el menú izquierdo.
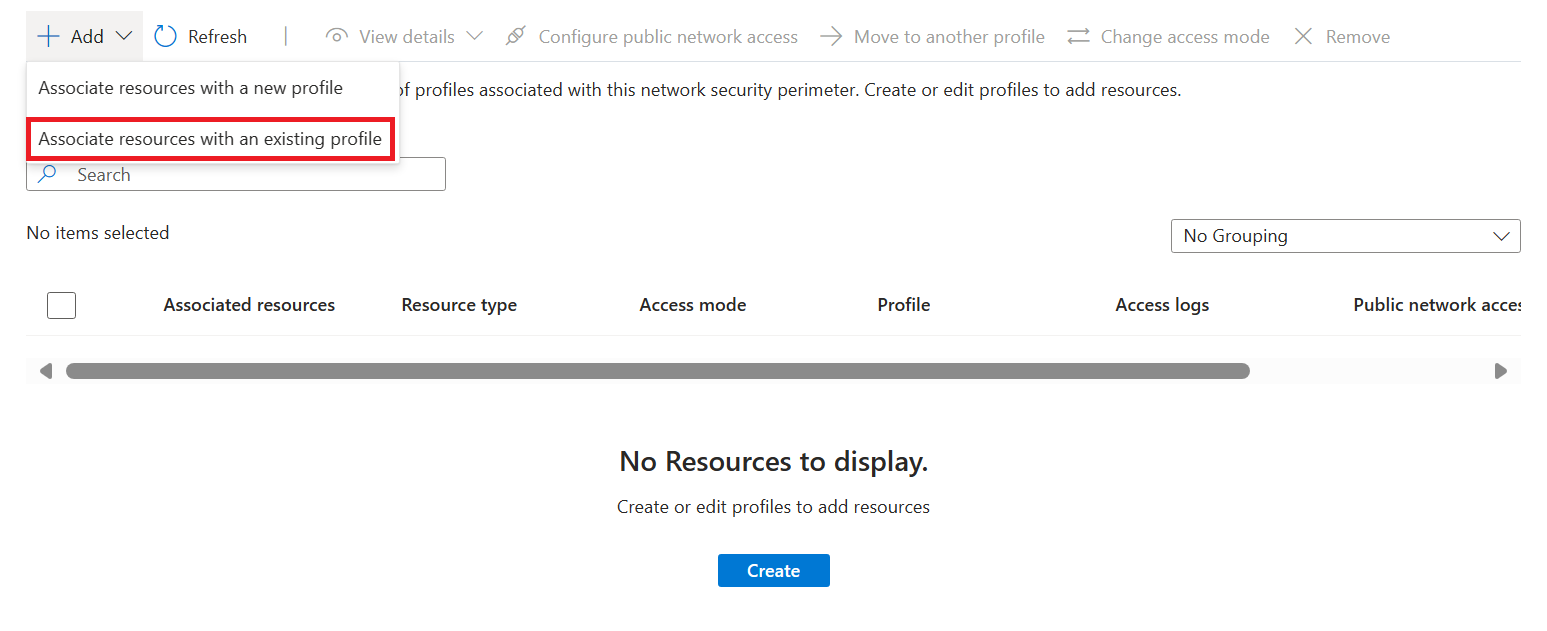
Seleccione Agregar>Asociar recursos con un perfil existente.
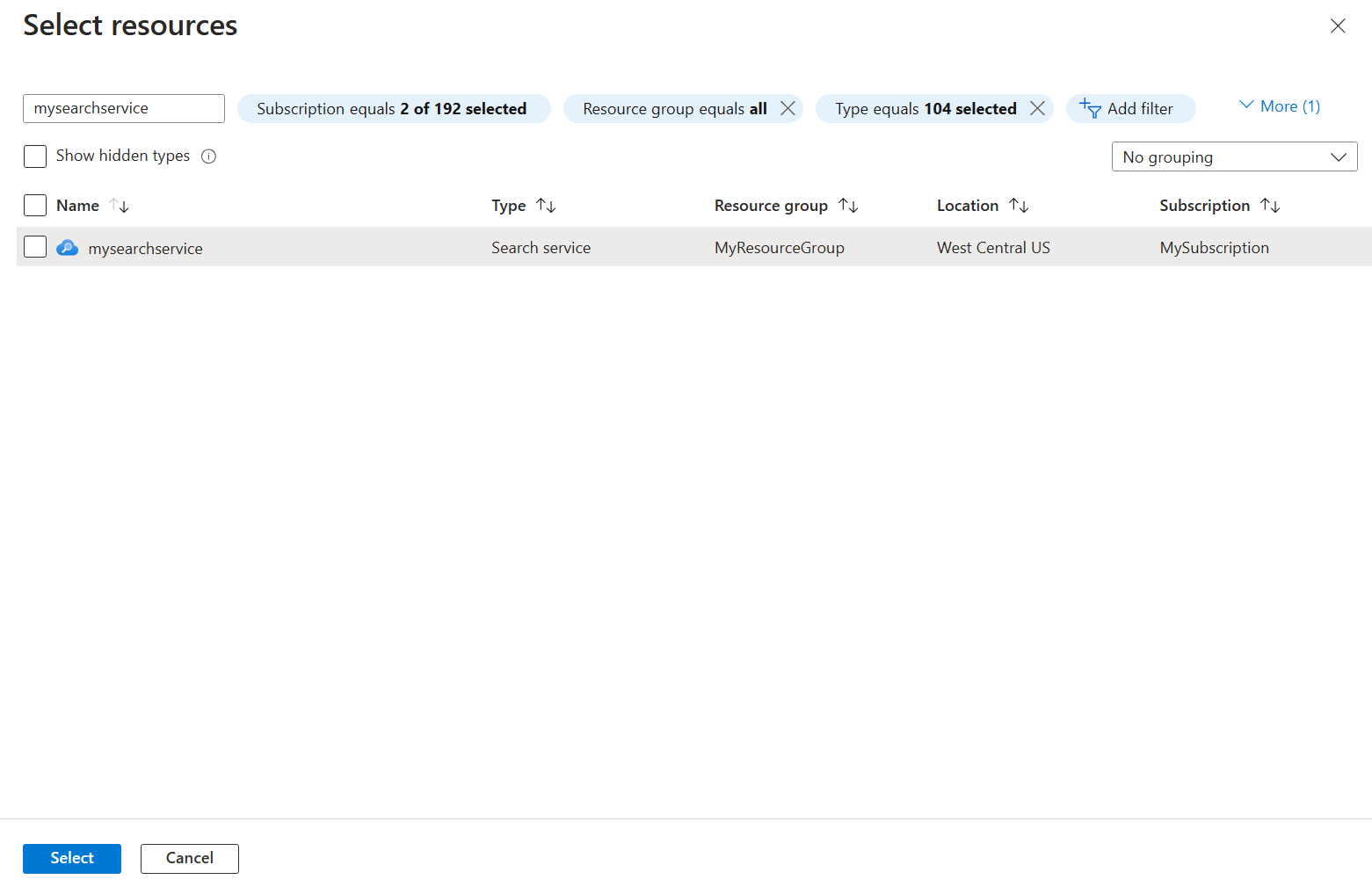
Seleccione el perfil que creó al crear el perímetro de seguridad de red para Perfil.
Seleccione Asociar y, a continuación, seleccione el servicio de búsqueda que creó.
Seleccione Asociar en la sección inferior izquierda de la pantalla para crear la asociación.
Modos de acceso en el perímetro de seguridad de red
El perímetro de seguridad de red admite dos modos de acceso diferentes para los recursos asociados:
| Modo | Descripción |
|---|---|
| Modo de aprendizaje | Este es el modo de acceso predeterminado. En modo de aprendizaje, el perímetro de seguridad de red registra todo el tráfico al servicio de búsqueda que se habría denegado si el perímetro estuviera en modo aplicado. Esto permite a los administradores de red comprender los patrones de acceso existentes del servicio de búsqueda antes de implementar la aplicación de reglas de acceso. |
| Modo aplicado | En modo aplicado, el perímetro de seguridad de red registra y deniega todo el tráfico no permitido explícitamente por las reglas de acceso. |
Configuración de red del servicio de búsqueda y perímetro de seguridad de red
La configuración publicNetworkAccess determina la asociación de servicio de búsqueda con un perímetro de seguridad de red.
En modo de aprendizaje, la configuración
publicNetworkAccesscontrola el acceso público al recurso.En modo aplicado, las reglas de perímetro de seguridad de red reemplazan la configuración
publicNetworkAccess. Por ejemplo, si un servicio de búsqueda con una configuraciónpublicNetworkAccessdeenabledestá asociado a un perímetro de seguridad de red en modo aplicado, las reglas de acceso de perímetro de seguridad de red siguen controlando el acceso al servicio de búsqueda.
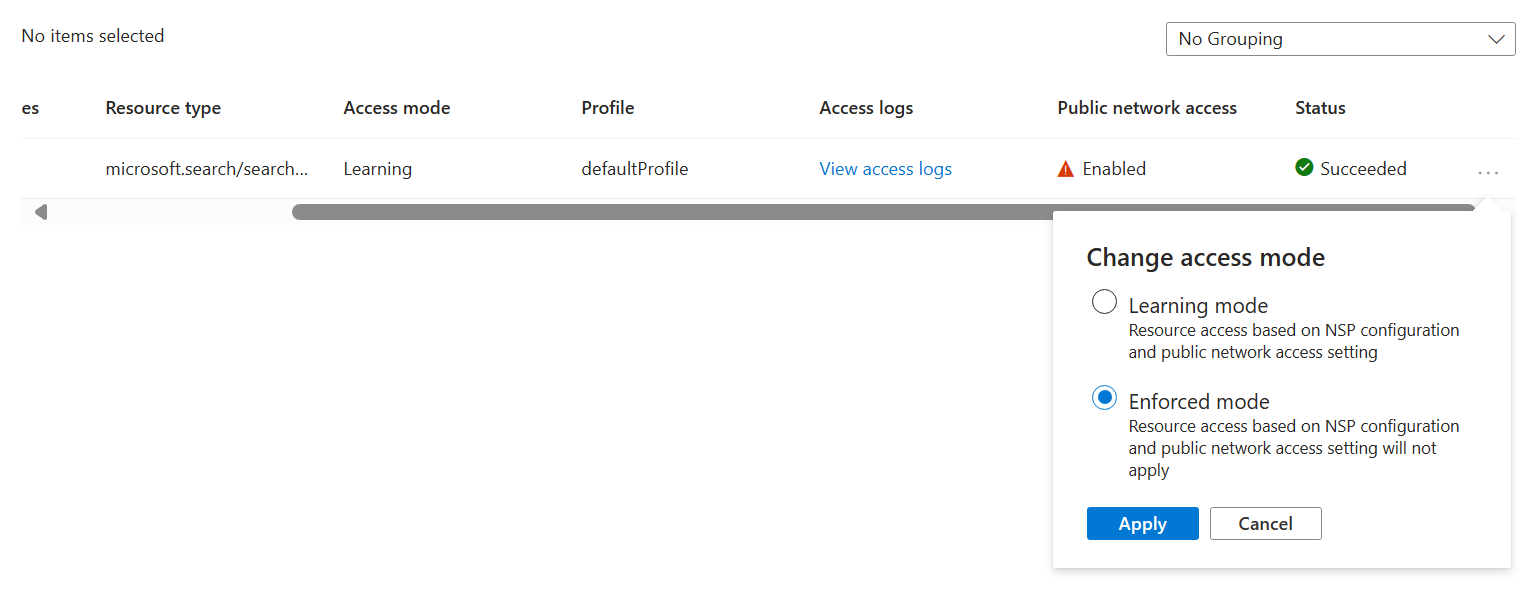
Cambio del modo de acceso en el perímetro de seguridad de red
Vaya al recurso de perímetro de seguridad de red en Azure Portal.
Seleccione Recursos en el menú izquierdo.

Busque el servicio de búsqueda en la tabla.
Seleccione los tres puntos situados en el extremo derecho de la fila del servicio de búsqueda. Seleccione Cambiar modo de acceso en el menú emergente.`
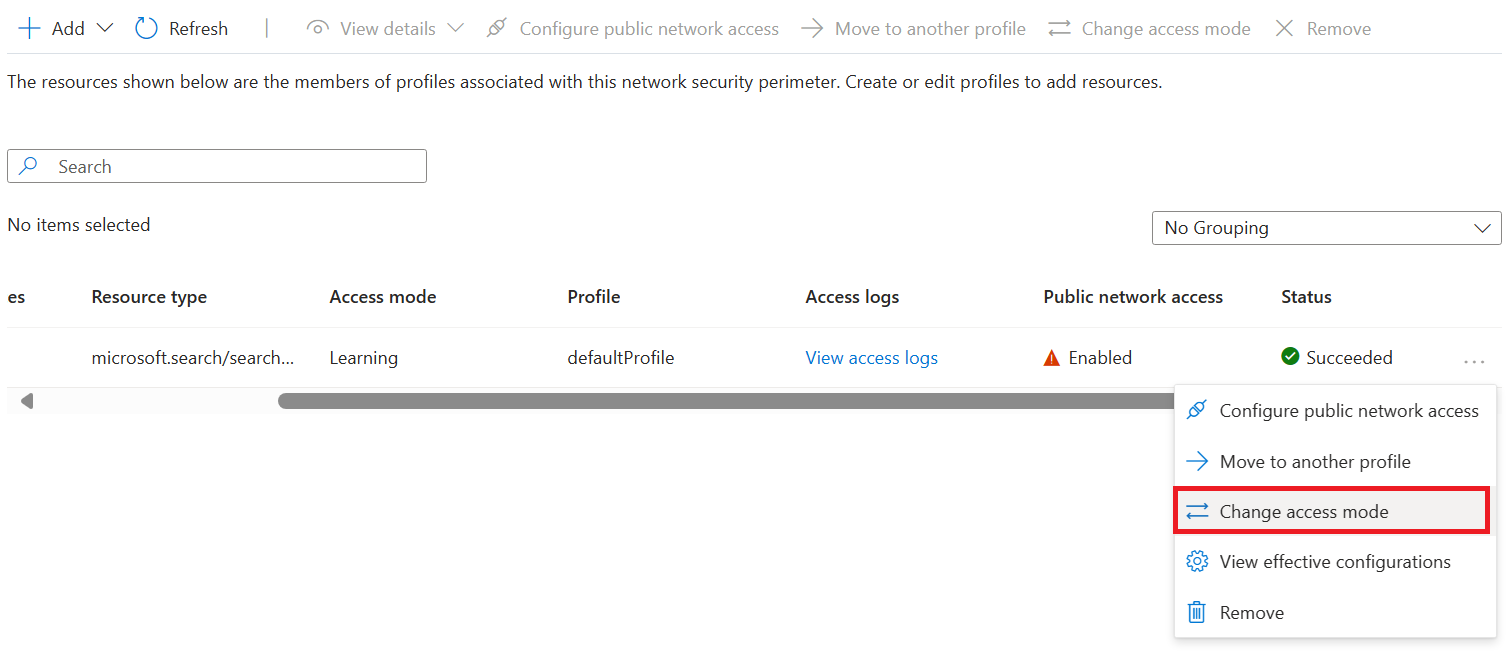
Seleccione el modo de acceso deseado y seleccione Aplicar.
Habilitación del registro del acceso de red
Vaya al recurso de perímetro de seguridad de red en Azure Portal.
Seleccione Configuración de diagnóstico en el menú izquierdo.
Seleccione Agregar configuración de diagnóstico.
Escriba cualquier nombre como "diagnostic" para Nombre de la configuración de diagnóstico.
En Registros, seleccione Todos los registros. allLogs garantiza que se registre todo el acceso de red entrante y saliente a los recursos del perímetro de seguridad de red.
En Detalles de destino, seleccione Archivar en una cuenta de almacenamiento o Enviar al área de trabajo de Log Analytics. La cuenta de almacenamiento debe estar en la misma región que el perímetro de seguridad de red. Puede usar una cuenta de almacenamiento existente o crear una nueva. Un área de trabajo de Log Analytics puede estar en una región diferente a la que usa el perímetro de seguridad de red. También puede seleccionar cualquiera de los otros destinos aplicables.
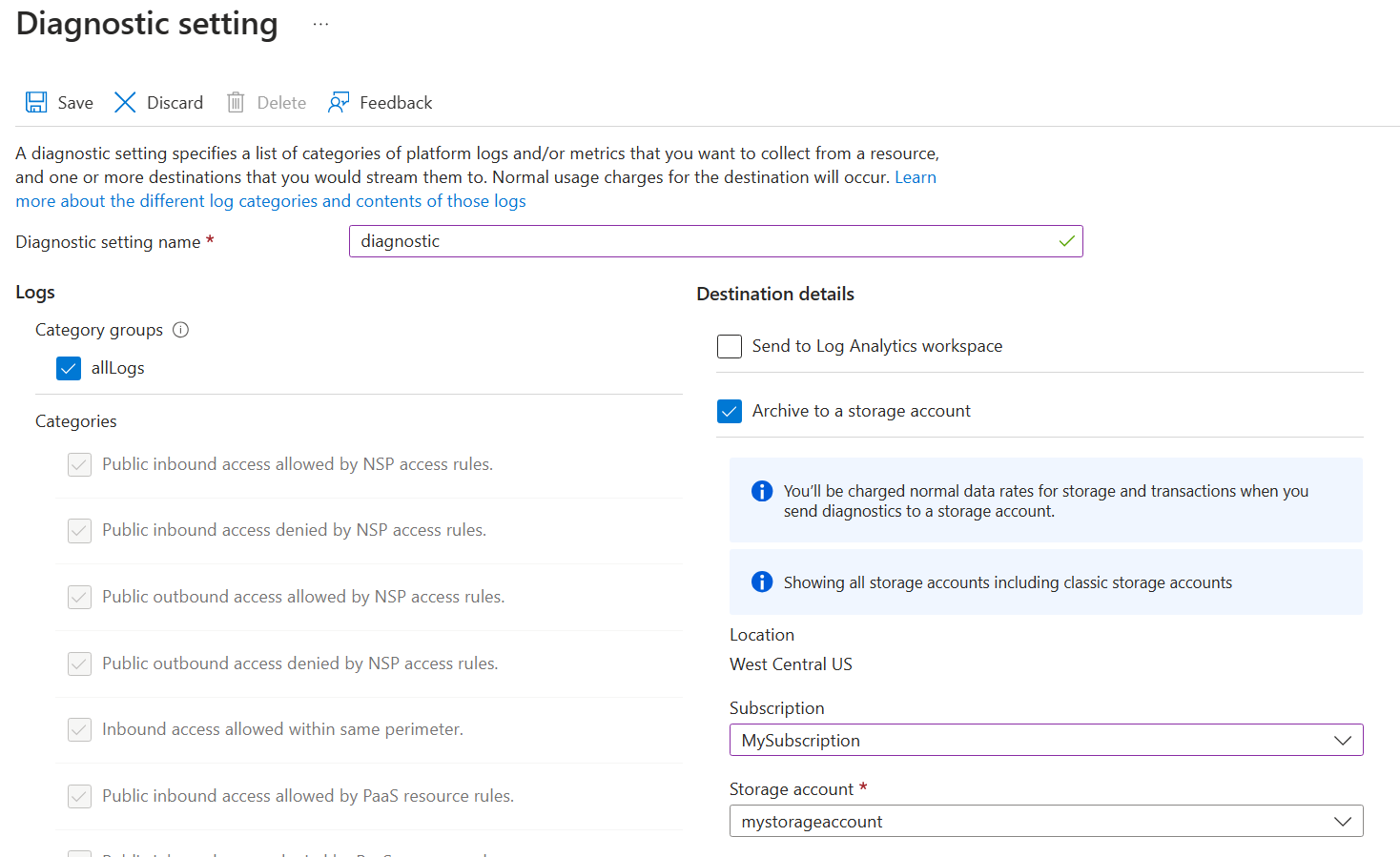
Seleccione Guardar para crear la configuración de diagnóstico y empezar a registrar el acceso a la red.
Lectura de registros de acceso a la red
Área de trabajo de Log Analytics
La tabla network-security-perimeterAccessLogs contiene todos los registros de cada categoría de registro (por ejemplo network-security-perimeterPublicInboundResourceRulesAllowed). Cada registro contiene un registro del acceso de red perimetral de seguridad de red que coincide con la categoría de registro.
Este es un ejemplo del formato de registro network-security-perimeterPublicInboundResourceRulesAllowed:
| Nombre de la columna | Significado | Valor de ejemplo |
|---|---|---|
| ResultDescription | Nombre de la operación de acceso a la red | POST /indexes/my-index/docs/search |
| Perfil | El perímetro de seguridad de red al que estaba asociado el servicio de búsqueda | defaultProfile |
| ServiceResourceId | Identificador de recurso del servicio de búsqueda | search-service-resource-id |
| Regla coincidente | Descripción JSON de la regla con la que coincidió el registro | { "accessRule": "IP firewall" } |
| SourceIPAddress | Dirección IP de origen del acceso de red entrante, si procede | 1.1.1.1 |
| AccessRuleVersion | Versión de las reglas de acceso de perímetro de seguridad de red usadas para aplicar las reglas de acceso a la red | 0 |
Cuenta de almacenamiento
La cuenta de almacenamiento tiene contenedores para cada categoría de registro (por ejemplo insights-logs-network-security-perimeterpublicinboundperimeterrulesallowed). La estructura de carpetas dentro del contenedor coincide con el identificador de recurso del perímetro de seguridad de red y la hora en que se tomaron los registros. Cada línea del archivo de registro JSON contiene un registro del acceso de red perimetral de seguridad de red que coincide con la categoría de registro.
Por ejemplo, el registro de categoría permitido de las reglas de perímetro de entrada usa el siguiente formato:
"properties": {
"ServiceResourceId": "/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/network-security-perimeter/providers/Microsoft.Search/searchServices/network-security-perimeter-search",
"Profile": "defaultProfile",
"MatchedRule": {
"AccessRule": "myaccessrule"
},
"Source": {
"IpAddress": "255.255.255.255",
}
}
Adición de una regla de acceso para el servicio de búsqueda
Un perfil del perímetro de seguridad de red especifica las reglas que permiten o deniegan el acceso a través del perímetro.
Dentro del perímetro, todos los recursos tienen acceso mutuo en el nivel de red. Todavía debe configurar la autenticación y la autorización, pero en el nivel de red, se aceptan solicitudes de conexión desde dentro del perímetro.
En el caso de los recursos fuera del perímetro de seguridad de red, debe especificar reglas de acceso de entrada y salida. Las reglas de entrada especifican qué conexiones permitir y las reglas de salida especifican las solicitudes a las que se permite salir.
Un servicio de búsqueda acepta solicitudes entrantes de aplicaciones como el Portal de la Fundición de IA de Azure, el flujo de avisos de Azure Machine Learning y cualquier aplicación que envíe solicitudes de indexación o consulta. Un servicio de búsqueda envía solicitudes salientes durante la ejecución del conjunto de aptitudes y la indexación realizada con indexador. En esta sección se explica cómo configurar reglas de acceso de entrada y salida para escenarios de Búsqueda de Azure AI.
Nota:
Cualquier servicio asociado a un perímetro de seguridad de red permite implícitamente el acceso entrante y saliente a cualquier otro servicio asociado al mismo perímetro de seguridad de red cuando ese acceso se autentica mediante identidades administradas y asignaciones de roles. Las reglas de acceso solo deben crearse al permitir el acceso fuera del perímetro de seguridad de red, o bien para el acceso autenticado mediante claves de API.
Adición de una regla de acceso de entrada
Las reglas de acceso de entrada pueden permitir que Internet y los recursos fuera del perímetro se conecten con recursos dentro del perímetro.
El perímetro de seguridad de red admite dos tipos de reglas de acceso de entrada:
Intervalos de direcciones IP. Los intervalos o las direcciones IP deben estar en el formato Enrutamiento de interdominios sin clases (CIDR). Un ejemplo de notación CIDR es 192.0.2.0/24, que representa las direcciones IP que van de 192.0.2.0 a 192.0.2.255. Este tipo de regla permite solicitudes entrantes desde cualquier dirección IP dentro del intervalo.
Suscripciones. Este tipo de regla permite el acceso entrante autenticado mediante cualquier identidad administrada de la suscripción.
Para agregar una regla de acceso de entrada en Azure Portal:
Vaya al recurso de perímetro de seguridad de red en Azure Portal.
Seleccione Perfiles en el menú izquierdo.
Seleccione el perfil que usa con el perímetro de seguridad de red
Seleccione Reglas de acceso de entrada en el menú izquierdo.
Seleccione Agregar.
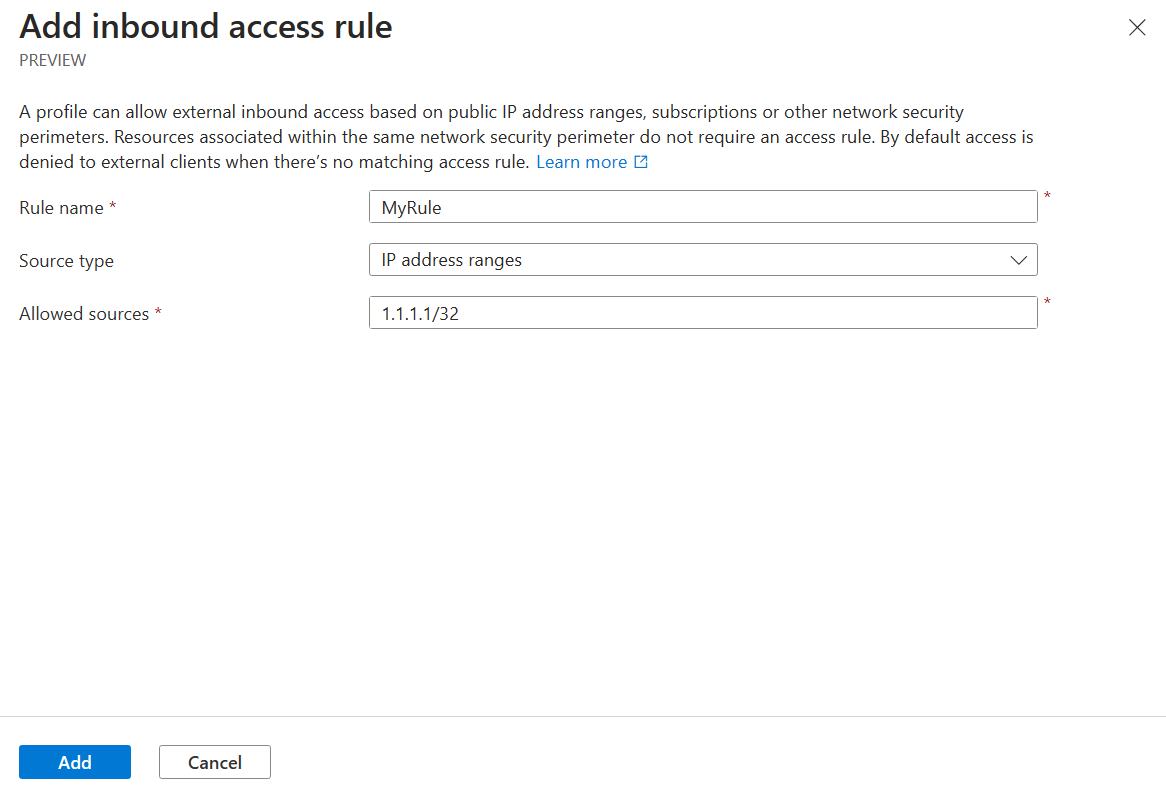
Escriba o seleccione los siguientes valores:
Configuración Value Nombre de la regla Nombre de la regla de acceso de entrada (por ejemplo, "MyInboundAccessRule"). Tipo de origen Las suscripciones y los intervalos de direcciones IP son valores válidos. Orígenes permitidos Si seleccionó intervalos de direcciones IP, escriba el intervalo de direcciones IP en formato CIDR desde el que desea permitir el acceso entrante. Los intervalos IP de Azure están disponibles en este vínculo. Si seleccionó Suscripciones, use la suscripción desde la que desea permitir el acceso entrante. Seleccione Agregar para crear la regla de acceso de entrada.
Adición de una regla de acceso de salida
Un servicio de búsqueda realiza llamadas salientes durante la ejecución del conjunto de aptitudes y la indexación realizada con indexador. Si los orígenes de datos del indexador, los servicios de Azure AI o la lógica de aptitudes personalizadas están fuera del perímetro de seguridad de red, debe crear una regla de acceso de salida que permita al servicio de búsqueda realizar la conexión.
Recuerde que en versión preliminar pública, Búsqueda de Azure AI solo puede conectarse a Azure Storage o Azure Cosmos DB dentro del perímetro de seguridad. Si los indexadores usan otros orígenes de datos, necesita una regla de acceso de salida para admitir esa conexión.
El perímetro de seguridad de red admite reglas de acceso de salida basadas en el nombre de dominio completo (FQDN) del destino. Por ejemplo, puede permitir el acceso saliente desde cualquier servicio asociado al perímetro de seguridad de red a un FQDN, como mystorageaccount.blob.core.windows.net.
Para agregar una regla de acceso de salida en Azure Portal:
Vaya al recurso de perímetro de seguridad de red en Azure Portal.
Seleccione Perfiles en el menú izquierdo.

Seleccione el perfil que usa con el perímetro de seguridad de red

Seleccione Reglas de acceso de salida en el menú izquierdo.
Seleccione Agregar.
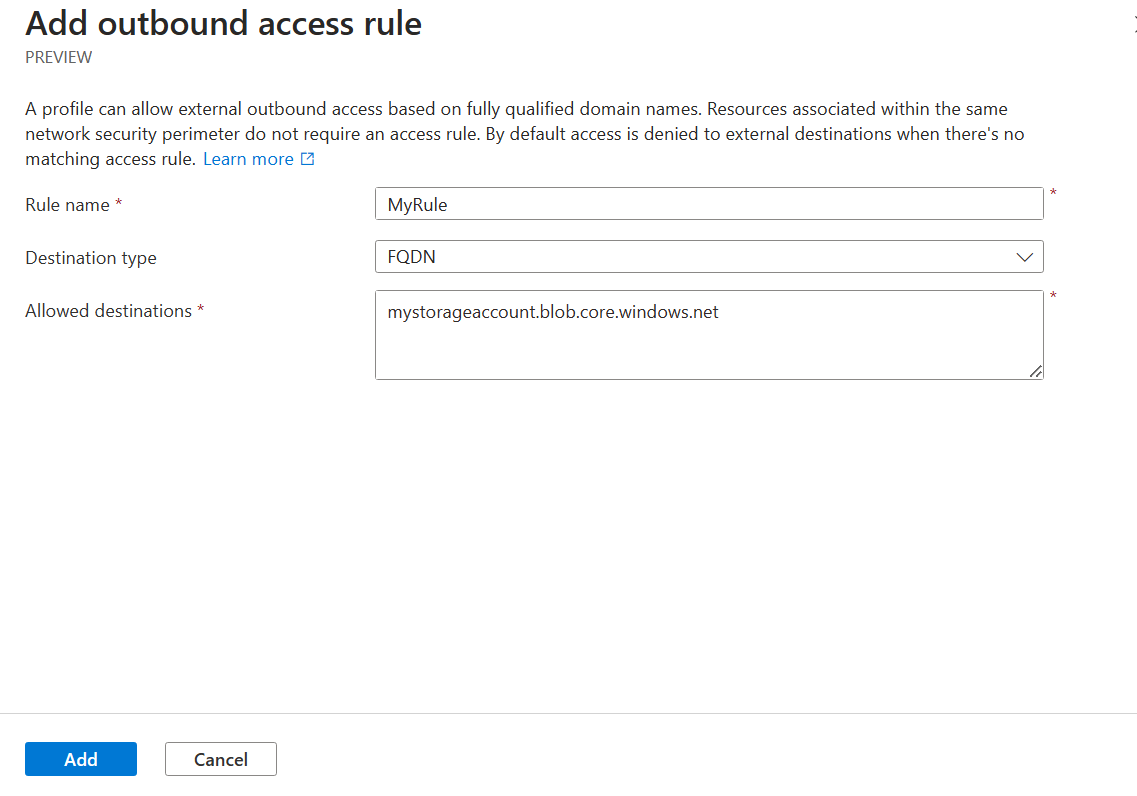
Escriba o seleccione los siguientes valores:
Configuración Value Nombre de la regla Nombre de la regla de acceso de salida (por ejemplo, "MyOutboundAccessRule") Tipo de destino Déjelo como FQDN Destinos permitidos Escriba una lista separada por comas de FQDN a los que desea permitir el acceso saliente Seleccione Agregar para crear la regla de acceso de salida.
Prueba de la conexión a través del perímetro de seguridad de red
Para probar la conexión a través del perímetro de seguridad de red, necesita acceso a un explorador web, ya sea en un equipo local con una conexión a Internet o en una máquina virtual de Azure.
Cambie la asociación del perímetro de seguridad de red al modo aplicado para empezar a aplicar los requisitos del perímetro de seguridad de red para el acceso de red al servicio de búsqueda.
Decida si desea usar un equipo local o una máquina virtual de Azure.
- Si usa un equipo local, debe conocer la dirección IP pública.
- Si usa una máquina virtual de Azure, puede usar un vínculo privado o comprobar la dirección IP mediante Azure Portal.
Con la dirección IP, puede crear una regla de acceso de entrada para que esa dirección IP permita el acceso. Puede omitir este paso si usa un vínculo privado.
Por último, intente acceder al servicio de búsqueda en Azure Portal. Si puede ver los índices correctamente, el perímetro de seguridad de red está configurado correctamente.
Visualización y administración de la configuración del perímetro de seguridad de red
Puede usar las API de REST de configuración del perímetro de seguridad de red para examinar y conciliar las configuraciones perimetrales.
Asegúrese de usar la versión de API predeterminada 2024-06-01-preview.
Obtenga información sobre cómo llamar a las API REST de administración.