Virtualization-based security (VBS) enclaves
Applies to: ✅ Windows 11 Build 26100.2314 or later ✅ Windows Server 2025 or later
A Virtualization-based security (VBS) Enclave is a software-based trusted execution environment inside the address space of a host application. VBS Enclaves leverage underlying VBS technology to isolate the sensitive portion of an application in a secure partition of memory. VBS Enclaves enable isolation of sensitive workloads from both the host application and the rest of the system.
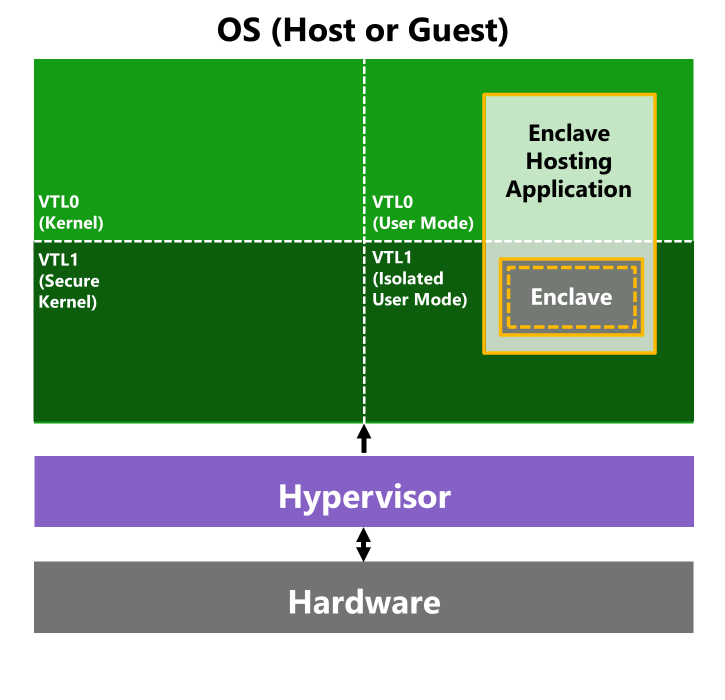
By planning ahead and isolating the sensitive part of your workload, you can isolate it in a VBS Enclave, as illustrated in the following diagram:
Device requirements
The following are required to run VBS Enclaves:
- VBS/HVCI must be enabled. This should be enabled on Windows 11 or later by default. See Enable virtualization-based protection of code integrity for more information.
- Windows 11 Build 26100.2314 or later or Windows Server 2025 or later.
Development prerequisites
In addition to the device requirements, the following are required to develop VBS Enclaves:
- Visual Studio 2022 version 17.9 or later - The Microsoft Visual C++ compiler (MSVC) is required. Installing Visual Studio simplifies this.
- The Windows Software Development Kit (SDK) version 10.0.22621.3233 or later, which provides
veiid.exe(the VBS Enclave import ID binding utility) andsigntool.exe. - A Trusted Signing account.
Related content
- VBS Enclaves development guide
- APIs available in VBS enclaves
- Securing your sensitive workloads with VBS Enclaves
- Secure Enclaves (Trusted Execution) overview
- Always Encrypted with secure enclaves documentation
- Virtualization-based Security (VBS) | Windows Hardware Developer
- New Windows 11 features strengthen security to address evolving cyberthreat landscape