Microsoft Defender portal
Microsoft's unified security SecOps platform combines Microsoft security services in the Microsoft Defender portal.
The portal provides a single location to monitor, manage, and configure pre-breach and post-breach security across on-premises and multicloud assets.
- Pre-breach security: Proactively visualize, assess, remediate, and monitor organizational security posture to reduce security risk and attack surfaces.
- Post-breach security: Continuously monitor, detect, investigate, and respond to real-time and emerging cybersecurity threats against organizational assets.
Portal services
The Defender portal combines many Microsoft security services.
| Service | Details |
|---|---|
| Microsoft Defender XDR Detect and respond to cybersecurity threats. |
Defender XDR includes a suite of services that come together in the Defender portal to provide unified threat protection across the enterprise. Defender XDR services collect, correlate, and analyze threat data and signals across endpoints and devices, identities, email, apps, and OT/IoT assets. In the portal you can review, investigate, and respond to security alerts and incidents, automatically disrupt attacks, and proactively hunt for threats. Learn more about Defender XDR in the Defender portal. |
| Microsoft Sentinel Collect, analyze, and manage security data at scale using automation and orchestration. |
Microsoft Sentinel fully integrates with Defender XDR in the Defender portal, providing additional threat protection capabilities such as attack disruption, unified entities and incidents, and SOC optimization. For more information, see Microsoft Sentinel in the Defender portal. |
| Microsoft Defender Threat Intelligence Integrate threat intelligence into SOC operations. |
The Defender Threat Intelligence platform extends the threat intelligence capabilities that are included in Defender XDR and Microsoft Sentinel. Gather data from multiple sources to provide a pool of threat intelligence signals and data. Security teams use this data to understand adversary activities, analyze attacks, and hunt for security threats. |
| Microsoft Security Exposure Management Proactively reduce security risk. |
Use Security Exposure Management to reduce organizational attack surfaces and remediate security posture. Continuously discover assets and data to get a comprehensive view of security across business assets. With the additional data context that Security Exposure Management provides, you can clearly visualize, analyze, and remediate weak areas of security. |
| Microsoft Defender for Cloud Protect cloud workloads. |
Defender for Cloud improves multicloud security posture, and protects cloud workloads against threats. Defender for Cloud integrates into the Defender portal to provide a unified view of cloud security alerts, and a single location for investigations. |
Accessing the portal
In the Defender portal Permissions page, use the following methods to configure user access:
| Methods | Details |
|---|---|
| Global Microsoft Entra roles | Accounts with the following Global Microsoft Entra roles can access Microsoft Defender XDR functionality and data:
|
| Custom roles | Allow access to specific data, tasks, and features using custom roles. Custom roles control granular access, and can be used together with Microsoft Entra global roles. |
| Unified RBAC | Unified role-based access control (RBAC) provides a permissions management model for controlling user permissions in the Defender portal, and across services within the portal. |
Microsoft Sentinel permissions
When you're onboarded to Microsoft's unified SecOps platform, existing Azure RBAC permissions are used to work with Microsoft Sentinel features in the Defender portal.
- Manage roles and permissions for Microsoft Sentinel users in the Azure portal.
- Any Azure RBAC changes are reflected in the Defender portal.
For more information, see Roles and permissions in Microsoft Sentinel.
Working in the portal
On the Home page, your view is determined by the services included in your subscriptions. Access settings are based on your portal permissions.
| Feature | Details |
|---|---|
| Home page | The Home page provides a view of your environment's security state. Review active threats, resources at risk, and a summary of all-up security posture. Use the dashboard for an up-to-date snapshot, and drill down to details as needed. |
| Portal notifications | Portal notifications keep you up-to-date with important information, including updates, events, complete or in-progress actions, and warnings and errors. Notifications are sorted by their generated time in the notification panel, with the most recent displayed first. For more information, see Configure alert notifications. |
| Search | As you search the portal, results are categorized by sections related to your search terms. Search provides results from within the portal, from the Microsoft Tech Community, and from Microsoft Learn documentation. Search history is stored in your browser and is accessible for 30 days. |
| Guided tour | Get a guided tour of managing endpoint security, or managing email and collaboration security. |
| What's new | Learn about the latest updates from the Microsoft Defender XDR blog. |
| Community | Learn from others in Microsoft security discussion spaces on Tech Community. |
| Add cards | Customize the Home page to get information that's most important to you. |
Exposure management
In Exposure management, review the overall state of your security posture, exposure, and risk.
| Feature | Details |
|---|---|
| Exposure management overview | This dashboard provides a quick view of devices and cloud resources, including internet-facing devices and critical assets. Learn how well your key security initiatives are doing and drill down into top metrics for high-value vulnerabilities. Get exposure levels for different types of resources, and track security progress over time. |
| Attack surfaces | Visualize exposure data with the attack surface map. Explore resources and connections on the map, and drill down to focus on specific assets. In the Attack path management dashboard, review potential attack paths across your organization that attackers might exploit, together with choke points and critical assets in the path. |
| Exposure insights | Review and explore aggregated security posture data and insights across resources and workloads. Assess posture and readiness for your most important security projects, and track project metrics over time. Get security recommendations to remediate exposure issues. |
| Secure score | Review posture metrics based on Microsoft Secure Score. |
| Data connectors | Connect third-party products to Security Exposure Management, and request new connectors. |
For more information, see Microsoft Security Exposure Management.
Investigation and response
The Investigation and response section provides a single location for investigating security incidents, and responding to threats across the enterprise.
Investigate incidents and alerts
Manage and investigate security incidents in a single location and from a single queue in the Defender portal. The Incidents and Alerts queues shows current security incidents and alerts across your services.
| Feature | Details |
|---|---|
| Incidents | On the Incidents dashboard, review a list of the latest incidents and prioritize those marked as high severity. Each incident groups correlated alerts and associated data that makes up an attack. Drill down in an incident to get a full attack story, including information about associated alerts, devices, users, investigations, and evidence. |
| Alerts | In the Alerts dashboard, review alerts. Alerts are signals issued by portal services in response to threat detection activity. The unified alerts queue displays new and in progress alerts from the last seven days, with the most recent alerts at the top. Filter on alerts to investigate as needed. |
For more information, see Incidents and alerts in the Microsoft Defender portal.
Hunt for threats
The Hunting area allows you to proactively inspect security events and data to locate known and potential threats.
| Feature | Details |
|---|---|
| Advanced hunting | Explore and query up to 30 days of raw data. You can query using a guided query tool, use sample queries, or use Kusto Query Language (KQL) to build your own queries. |
| Custom detection rules | Create custom detection rules to proactively monitor and respond to events and system states. Use custom detection rules to trigger security alerts or automatic response actions. |
For more information, see Proactively hunt for threats with advanced hunting and Custom detections overview.
Review pending threat remediations
Threat protection activity results in actions to remediate threats. Actions can be automated or manual. Actions that need approval or manual intervention are available in the Action center.
| Feature | Details |
|---|---|
| Action center | Review the list of actions that need attention. Approve or reject actions one at a time, or in bulk. You can review action history to track remediation. |
| Submissions | Submit suspect spam, URLs, email issues and more to Microsoft. |
For more information, see Automated investigation and response and The Action center.
Partner catalog
The Partner catalog section provides information about Defender partners.
The Defender portal supports the following types of partner integrations:
- Third-party integrations to help secure users with effective threat protection.
- Professional services that enhance detection, investigation, and threat intelligence capabilities.
Threat intelligence
In the Threat intelligence section of the portal, get direct visibility into active and ongoing threat campaigns, and access threat intelligence information provided by the Defender Threat Intelligence platform.
| Feature | Details |
|---|---|
| Threat analytics | Learn which threats are currently relevant in your organization. Assess threat severity, drill down into specific threat reports, and identity actions to take. Different types of threat analytics reports are available. |
| Intel profiles | Review curated threat intelligence content organized by threat actors, tools, and known vulnerabilities. |
| Intel Explorer | Review threat intelligence information, and drill down to search and investigate. |
| Intel projects | Review and create projects to organize indicators of interest and indicators of compromise from an investigation. A project includes associated artifacts and a detailed history of names, descriptions, collaborators, and monitoring profiles. |
For more information, see Threat analytics.
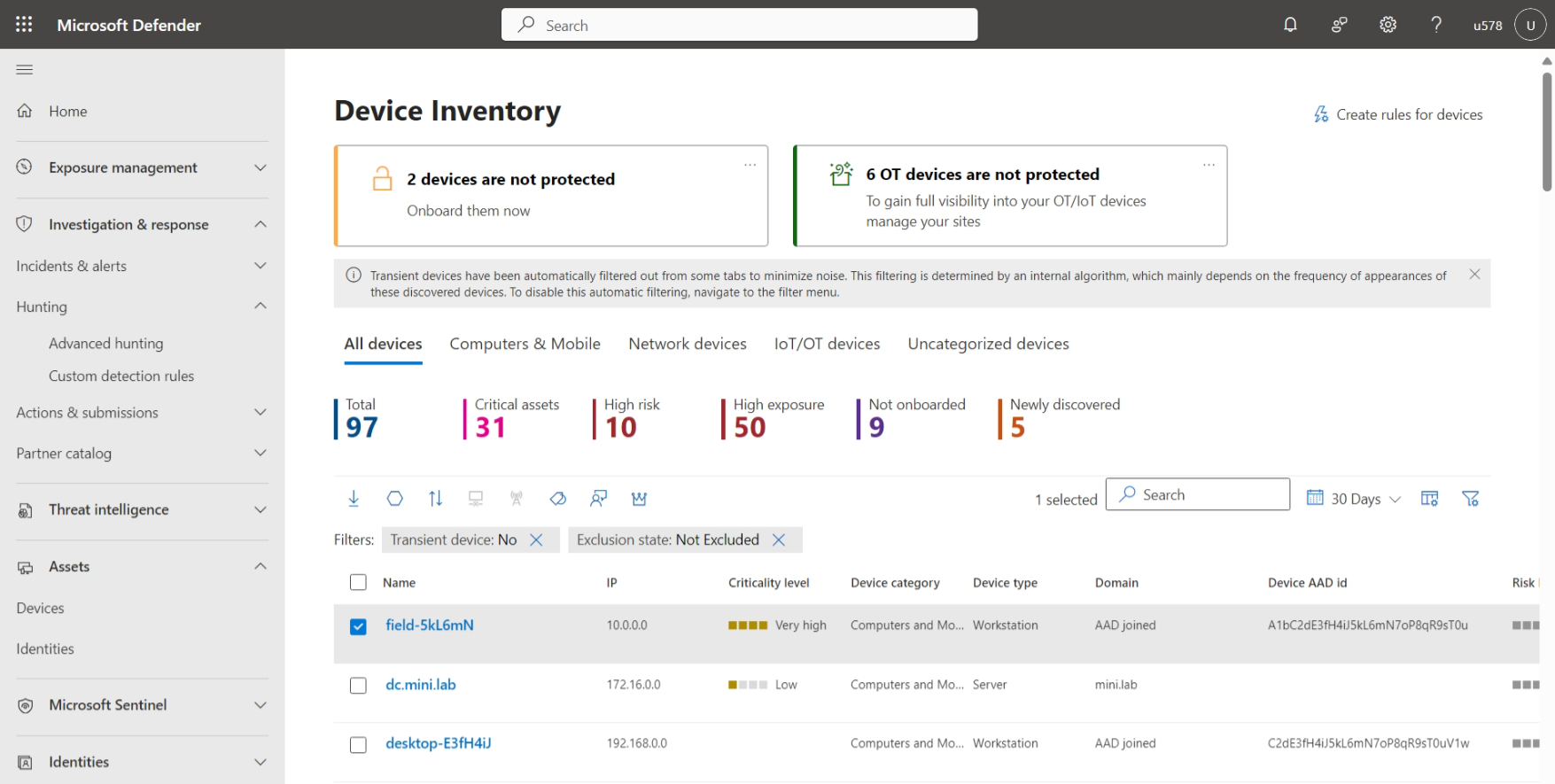
Assets
The Assets page provides a unified view of discovered and protected assets, including devices, users, mailboxes, and apps. Review the total number of assets of each type, and drill down into specific asset details.
| Feature | Details |
|---|---|
| Devices | On the Device Inventory page, get an overview of discovered devices in each tenant to which you have access. Review devices by type, and focus on high risk or critical devices. Group devices logically by adding tags for context, and exclude devices you don't want to assess. Start an automated investigation for devices. |
| Identities | Get a summary of your user and account inventory. |
For more information, see Device entity page and User entity page.
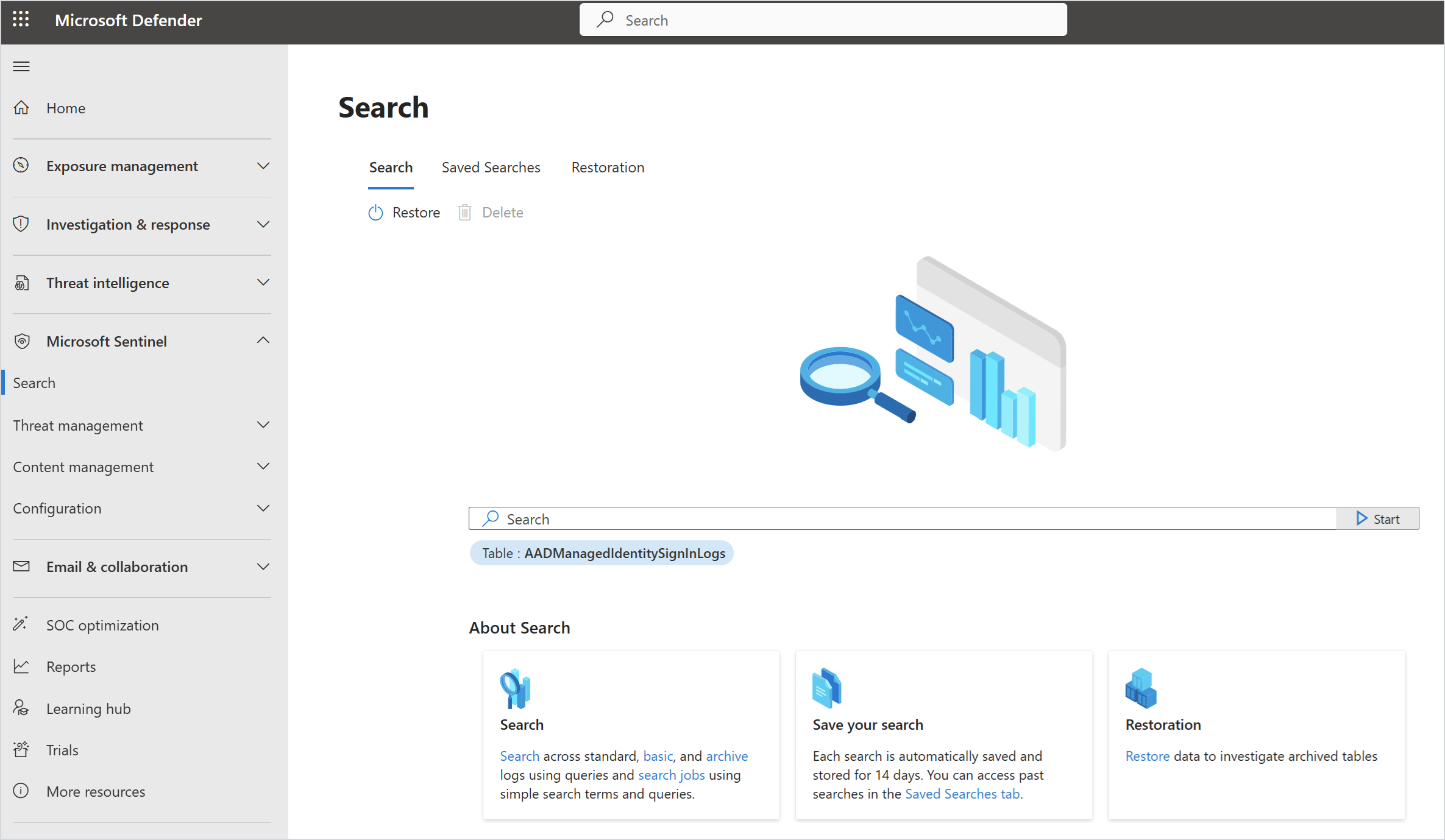
Microsoft Sentinel
Access Microsoft Sentinel capabilities in the Defender portal.
| Feature | Details |
|---|---|
| Search | Search across logs, and access past searches. |
| Threat management | Visualize and monitor connected data with workbooks. Investigate incidents and classify alerts with entities. Proactively hunt for threats and use notebooks to power investigations. Integrate threat intelligence into threat detection, and use the MITRE ATT&CK framework in analytics and incidents. |
| Content management | Discover and install out-of-the-box (OOTB) content from the Content hub. Use Microsoft Sentinel repositories to connect to external source systems for continuous integration and delivery (CI/CD), rather than manually deploying and updating custom content. |
| Configuration | Ingest data by using data connectors. Create watchlists to correlate and organize data sources. Set up analytics rules to query and analyze collected data. Automate threat responses. |
For more information, see Microsoft Sentinel and Microsoft Sentinel in the Microsoft Defender portal.
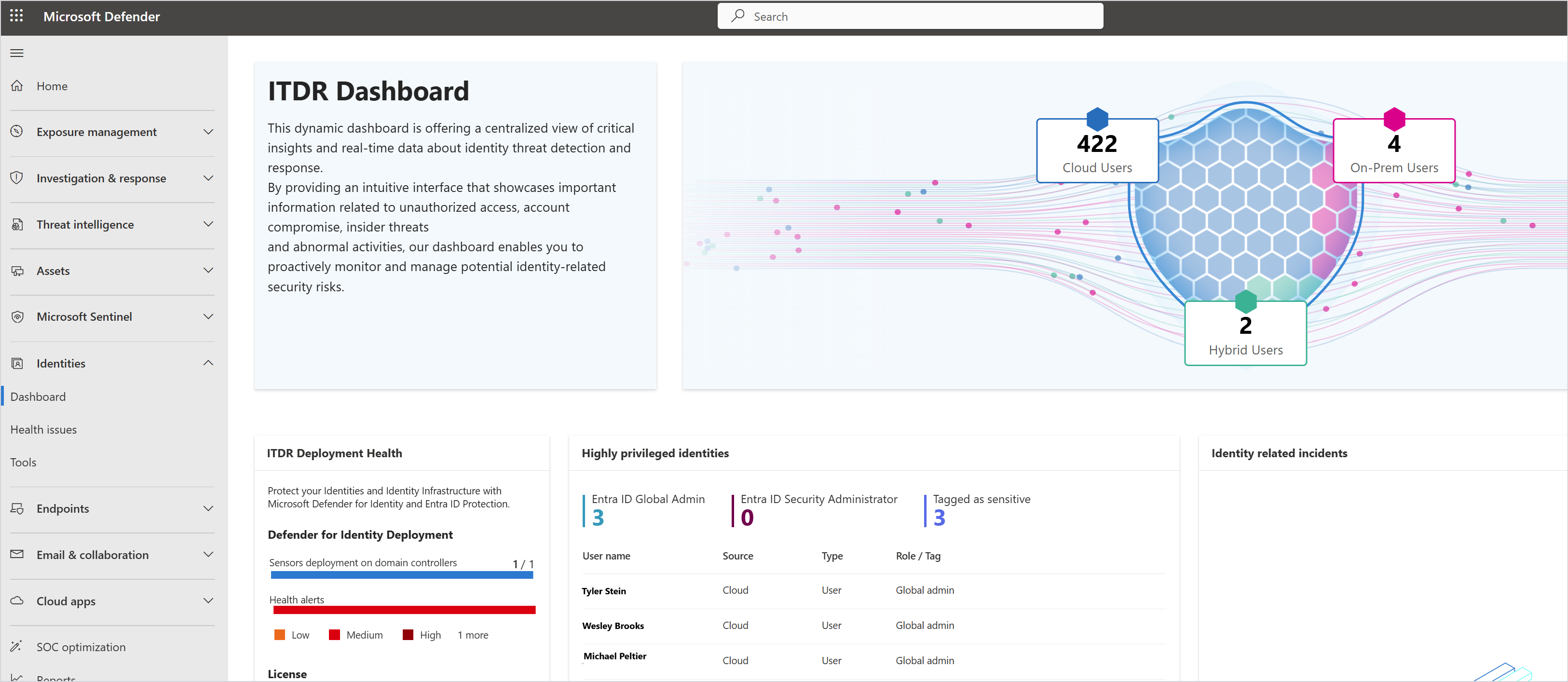
Identities
In the Identities section of the Defender portal, monitor user and account health, and proactively manage identity-related risks with Defender for Identity.
| Feature | Details |
|---|---|
| ITDR dashboard | On the Identity threat detection and response (ITDR) dashboard, get insights and real-time data about the security state of users and accounts. The dashboard includes information about Defender for Identity deployment, information about highly privileged identities, and information about identity-related incidents. If there's a problem with a Defender for Identity workspace, it's raised on the Health issues page. |
| Health issues | Any Defender for Identity global or sensor-based health issues are displayed on this page. |
| Tools | Access common tools to help you manage Defender for Identity. |
For more information, see Microsoft Defender for Identity.
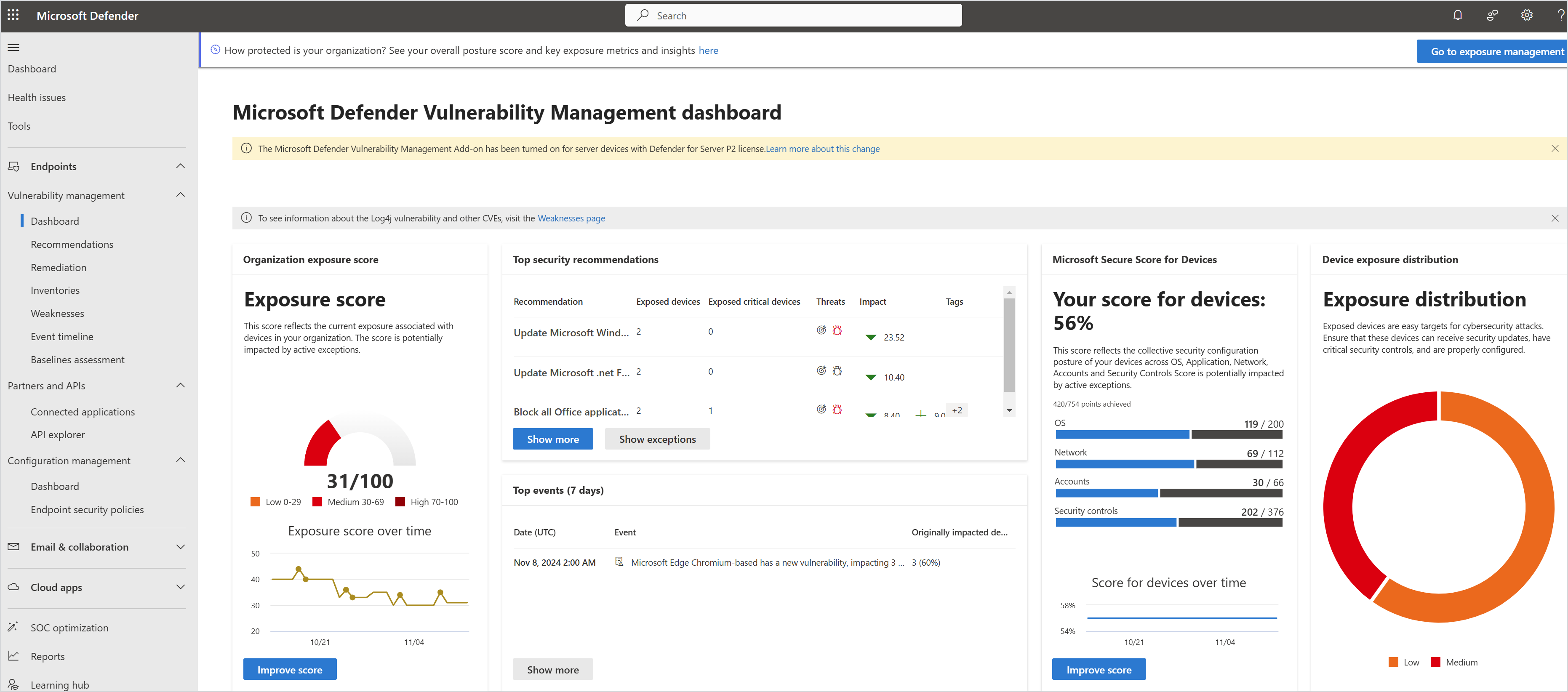
Endpoints
In the Endpoints section of the portal, monitor and manage asset vulnerabilities with Microsoft Defender Vulnerability Management.
| Feature | Details |
|---|---|
| Vulnerability management | Review vulnerability state in the dashboard. Get recommendations based on vulnerability assessment of devices, and remediate as needed. Review your organizational software inventory, including vulnerable components, certificates, and hardware. Review CVEs and security advisories. Review the event timeline to determine the impact of vulnerabilities. Use security baseline assessment to assess devices against security benchmarks. |
| Connected applications | Get information about the Microsoft Entra applications connected to Defender for Endpoint. |
| API explorer | Use the API explorer to construct and run API queries, test, and sent requests for available Defender for Endpoint API endpoints. |
For more information, see Microsoft Defender Vulnerability Management and Microsoft Defender for Endpoint.
Email and collaboration
In the Email & collaboration section, monitor, investigate, and manage security threats and responses to email and collaboration apps with Microsoft Defender for Office 365.
| Feature | Details |
|---|---|
| Investigations | Run and review automated investigations. |
| Explorer | Hunt, investigate, and explore threats to emails and documents. Drill down into specific types of threats, including malware, phishing, and campaigns. |
| Review | Manage quarantined items and restricted senders. |
| Campaigns | Analyze coordinated attacks against your organization. |
| Threat tracker | Review saved and tracked queries, and follow trending campaigns. |
| Policies and rules | Configure and manage security policies to protect against threats, and receive activity alerts. |
For more information, see Microsoft Defender for Office 365.
Cloud apps
In the Cloud apps section, review security to minimize risk and exposure to cloud apps using Microsoft Defender for Cloud Apps.
| Feature | Details |
|---|---|
| Cloud discovery | Get an overview of cloud app security with discovery reports. Review a sample report, and create new reports. |
| Cloud app catalog | Get an overview of well-known cloud apps and their associated risk. You can sanction and unsanction apps as needed. |
| OAuth apps | Get visibility into OAuth apps. Review apps, and filter settings to drill down. |
| Activity log | Review connected app activity by cloud name, IP address, and related devices. |
| Governance log | Review governance actions. |
| Policies | Configure security policies for cloud apps. |
For more information, see Microsoft Defender for Cloud Apps.
SOC optimization
In the SOC optimization page, tighten up security controls to close threat coverage gaps, and tighten data ingestion rates based on high-fidelity and actionable recommendations. SOC optimizations are tailored to your environment and based on your current coverage and threat landscape.
For more information, see Optimize your security operations.
Reports
In the Reports page, review security reports across all areas, assets, and workloads. Available reports depend on the security services you have access to.
Trials
In the Trials page, review trial solutions, designed to help you make decisions about upgrades and purchases.