Set up Secure Network Communications
Secure Network Communications (SNC) enhances the security of your SAP integration with Power Platform by encrypting the data between an on-premises data gateway and a SAP system. This article walks you through setting up SNC as a proof of concept.
Important
The settings and recommendations presented in this article are not intended for production use. Consult your security team, internal policies, and Microsoft Partner for guidance in setting up SNC in a production environment.
Prerequisites
- You have a SAP connection that uses the SAP ERP connector.
- You have access to a SAP instance that you can restart and administer.
- The SAP GUI is installed and set up.
- You're familiar with public and private key technologies.
- OpenSSL is installed and set up. If you have Git for Windows, add
C:\Program Files\Git\usr\bin\to your system PATH so that you can use theopensslcommand.
Install SAP Common Crypto Library
SAP Common Crypto Library enables the SAP Connector for Microsoft .NET (NCo) to encrypt communications between the on-premises data gateway and SAP. To extract the library, you need a proprietary decompression utility called SAPCAR.
Get SAPCAR
- Go to the SAP Software Download Center and sign in with your SAP credentials.
- Search for SAPCAR and select the latest non-archived version.
- Select your operating system.
- Download the .EXE file to
C:\sap\SAR.
Get SAP Common Crypto Library
- In the SAP Software Download Center, search for "COMMONCRYPTOLIB" and select the latest version.
- Select your operating system.
- Download the .SAR file with the most recent release date to
C:\sap\SAR.
Extract SAP Common Crypto Library
Open PowerShell and go to
C:\sap\SAR.Enter the following command, replacing
xxxxwith your values:.\SAPCAR_xxxx.EXE -xvf .\SAPCRYPTOLIBP_xxxx.SAR -R .\..\libs\sapcryptolibConfirm that
sapgenpse.exeis in theC:\sap\libs\sapcryptolibdirectory.
Generate certificates
Now that you've installed SAP Common Crypto Library, you can generate certificates to establish trust and encryption between your on-premises data gateway and the SAP system.
Warning
This method is for demonstration purposes only and is not recommended for production systems. For production systems, consult your internal PKI guidance or security team.
In this example, our certificates are structured as shown in the following diagram. Root CA [O=Contoso, CN=Root CA] signs the SNC encryption certificate [O=Contoso, CN=SNC] and the user certificates [O=Contoso, CN=UserIDs].
This article focuses on setting up the Root CA and SNC certificates.
Create certificates
Set up the folder structure:
mkdir rootCA mkdir sncCert # Create the necessary serial and index files if they don't exist if (-Not (Test-Path "rootCA\index.txt")) { New-Item -Path "rootCA\index.txt" -ItemType File } if (-Not (Test-Path "rootCA\serial")) { Set-Content -Path "rootCA\serial" -Value "01" }Generate a Root CA:
openssl genpkey -algorithm RSA -out rootCA/ca.key.pem -pkeyopt rsa_keygen_bits:2048 openssl req -x509 -new -key rootCA/ca.key.pem -days 7305 -sha256 -extensions v3_ca -out rootCA/ca.cert.pem -subj "/O=Contoso/CN=Root CA"Generate the SNC certificate:
openssl genrsa -out sncCert/snc.key.pem 2048 openssl req -key sncCert/snc.key.pem -new -sha256 -out sncCert/snc.csr.pem -subj "/O=Contoso/CN=SNC"Create an OpenSSL configuration file,
sncCert/extensions.cnf, for signing:subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer basicConstraints = critical,CA:false keyUsage = critical,digitalSignature,keyEncipherment,dataEncipherment extendedKeyUsage = clientAuth,emailProtectionSign the SNC certificate with the Root CA:
openssl x509 -req ` -in sncCert/snc.csr.pem ` -CA rootCA/ca.cert.pem ` -CAkey rootCA/ca.key.pem ` -CAcreateserial ` -out sncCert/snc.cert.pem ` -days 3650 ` -sha256 ` -extfile sncCert\extensions.cnf ` -extensions v3_leaf
Create a Personal Secure Environment
Create a Personal Secure Environment (PSE) for the on-premises data gateway. The NCo library looks for the SNC certificate inside the PSE.
Create a PKCS#12 container:
openssl pkcs12 -export -out snc.p12 -inkey sncCert\snc.key.pem -in sncCert\snc.cert.pem -certfile rootCA\ca.cert.pemCreate the SECUDIR environment variable:
- Open System Properties: In File Explorer, right-click This PC, and then select Properties > Advanced system settings.
- Select Environment Variables.
- Under System variables, select New.
- Set the variable name to
SECUDIR. - Set the value to
C:\sapsecudir. - Select OK.
Import the PKCS#12 container into a PSE:
C:\sap\libs\sapcryptolib\sapgenpse.exe import_p12 -p SAPSNCSKERB.pse C:\pki-certs\snc.p12
Set up SAP for SNC
Sign in to the SAP GUI.
Go to transaction code
SNC0.Enter E as the work area.
Select New Entry from the top bar and fill in the required information.
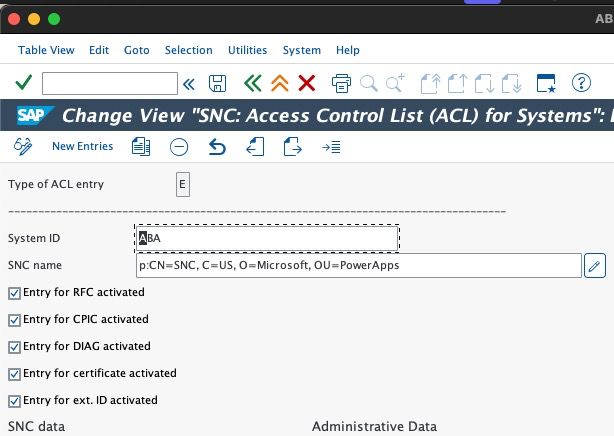
Select the Save.
Return to the SAP GUI home screen.
Go to transaction code
RZ10.Set these profile parameters:
snc/accept_insecure_gui: 1 snc/accept_insecure_rfc: 1 snc/enable: 1 snc/extid_login_diag: 1 snc/extid_login_rfc: 1 snc/gssapi_lib: $(SAPCRYPTOLIB) snc/identity/as: p:CN=ID3, O=Contoso snc/permit_insecure_start: 1 snc/data_protection/max: 3```Save the profile parameters and restart your SAP system.
Exchange certificates between SAP and the on-premises data gateway
You need to exchange certificates between the on-premises data gateway and SAP to establish trust.
Add the gateway SNC certificate to SAP
- In the SAP GUI, go to transaction code
STRUST. - If SNC SAPCryptolib has a red X, right-click it and select Create.
- Otherwise, double-click SNC SAPCryptolib, and then double-click your Own Certificate.
- Select Import Certificate and choose your
sncCert\snc.cert.pempublic certificate. - Select Add to Certificate List.
Add the SAP SNC certificate to the on-premises data gateway
In the SAP GUI, go to transaction code
STRUST.Double-click SNC SAPCryptolib, and then double-click your Own Certificate.
Export the public certificate.
Move the public certificate to your gateway machine (for example,
C:\sap\contoso-public-key.crt).Import the certificate into your gateway's PSE:
C:\sap\libs\sapcryptolib\sapgenpse.exe maintain_pk -p SAPSNCSKERB.pse -v -a C:\pki-certs\sncCert\sapkerb.public.cert
Test the secure connection
Follow the steps to test the secure connection. Once you complete the test successfully, you're ready to implement SNC in your production environment.
Create an instant flow in Power Automate.
Add an
SAP ERP Call Functionaction.Add the following SNC parameters to the SAP Connection string:
{ "AppServerHost": "xxx", "Client": "xx", "SystemNumber": "xx", "LogonType": "ApplicationServer", "SncLibraryPath": "C:\\sap\\libs\\sapcryptolib\\sapcrypto.dll", "SncMyName": "p:CN=SNC, O=Contoso", "SncPartnerName": "p:CN=ID3, O=Contoso", "SncQop": "Default", "UseSnc": "true", "SncSso": "Off" }```Test the connection using the
STFC_CONNECTIONRFC function.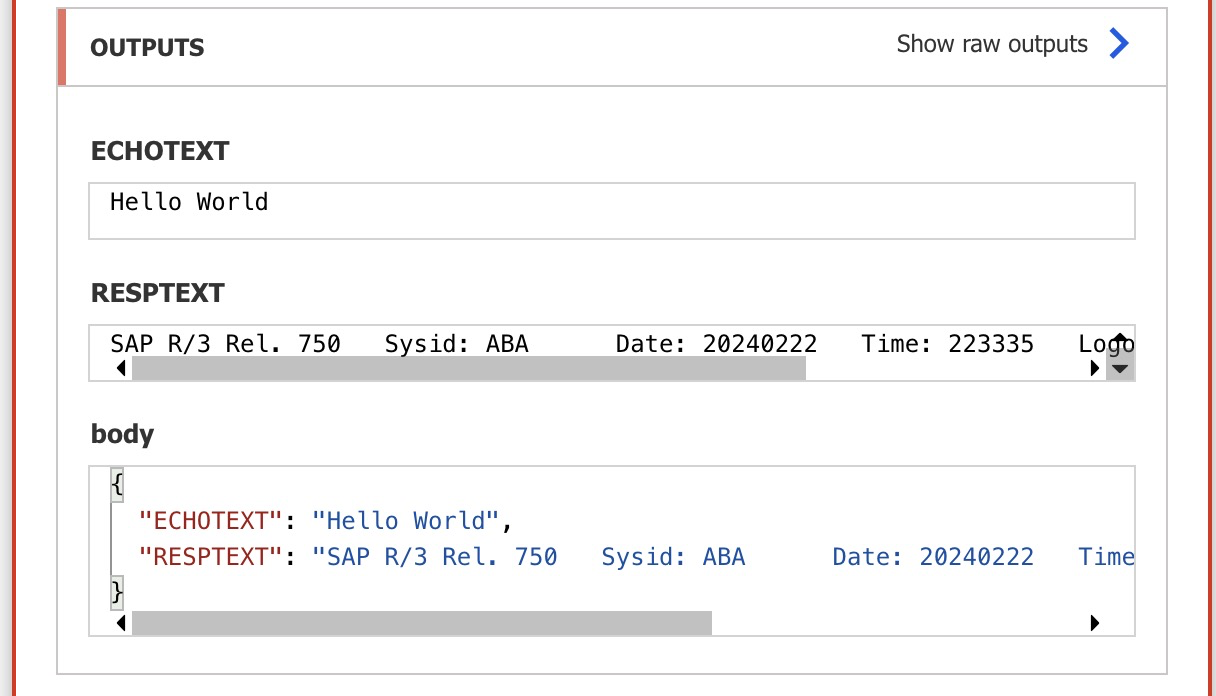
Important
Make sure that you securely handle private keys and delete them on completion of this setup.