Configure full roles and permissions
The Microsoft Defender portal allows granular access to features and data based on user roles and the permissions given to each user with Role-Based Access Control (RBAC).
Microsoft Defender for IoT is part of the Defender portal and user access permissions for alerts, incidents, device inventory, device groups and vulnerabilities should already be configured. Nevertheless, with the added features of Defender for IoT you might want to check, adjust or add to the existing roles and permissions of your team in the Defender portal.
This article shows you how to make general changes to RBAC roles and permissions that relate to all areas of Defender for IoT in the Defender portal. To set up roles and permissions specifically for site security, see set up RBAC permissions for site security.
Important
This article discusses Microsoft Defender for IoT in the Defender portal (Preview).
If you're an existing customer working on the classic Defender for IoT portal (Azure portal), see the Defender for IoT on Azure documentation.
Learn more about the Defender for IoT management portals.
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Prerequisites
- Review the general prerequisites for Microsoft Defender for IoT.
- Details of all users to be assigned updated roles and permissions for the Defender portal.
Access management options
There are two ways to manage user access to the Defender portal, depending on the type of tenent you're using. Each system has different named permissions that allow access for Defender for IoT. The two systems are:
- Global Microsoft Entra roles.
- Microsoft Defender XDR Unified RBAC: Use Microsoft Defender XDR Unified role-based access control (RBAC) to manage access to specific data, tasks, and capabilities in the Defender portal.
The instructions and permission settings listed in this article apply to Defender XDR Unified RBAC.
RBAC for version 1 or 2 only
Depending on your tenant, you might have access to RBAC version 1 or 2 instead of Defender XDR Unified RBAC. Assign RBAC permissions and roles, based on the summary table, to give users access to general Defender for IoT features. However, follow the instructions listed here for RBAC version 1, or here for RBAC version 2.
If you're using the Defender portal for the first time, you need to set up all of your roles and permissions. For more information, see manage portal access using role-based access control.
Defender XDR Unified RBAC roles for features in Defender for IoT
Assign RBAC permissions and roles, based on the summary table, to give users access to general Defender for IoT features:
In the Defender portal, either:
Select Settings > Microsoft XDR > Permissions and roles.
- Enable Endpoints & Vulnerability Management.
- Select Go to Permissions and roles.
Select Permissions > Microsft Defender XDR (1) > Roles.
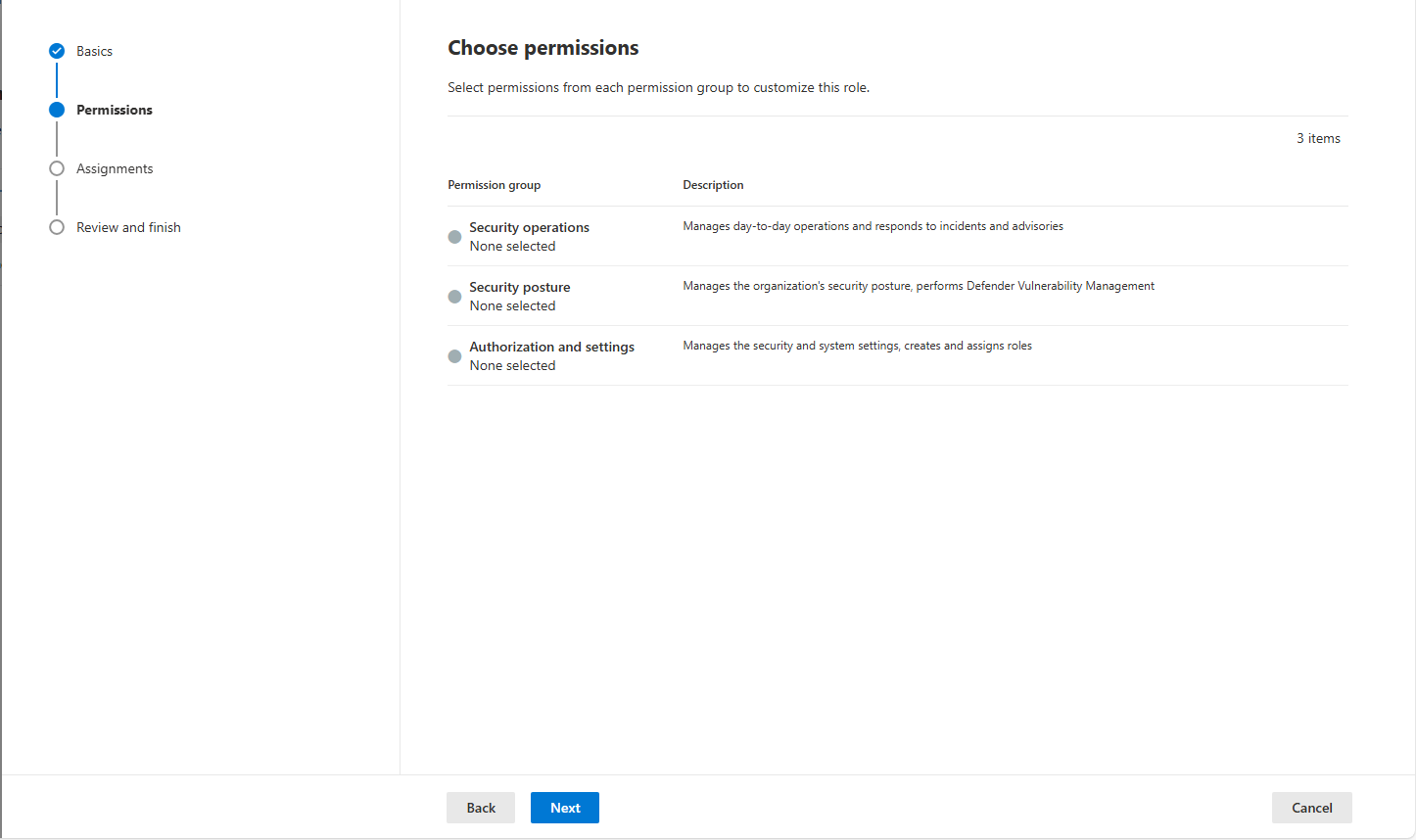
Select Create custom role.
Type a Role name, and select Next for Permissions.
Select Security operations, select the permissions as needed, and select Apply.
Select Security posture, select the permissions as needed, and select Apply.
Select Authorization and settings, select the permissions as needed, and select Apply.
Select Next for Assignments.
Select Add assignment.
- Type a name.
- Choose users and groups.
- Select the Data sources.
- Select Add.
Select Next for Review and finish.
Select Submit.
Summary of roles and permissions for all Defender for IoT features
| Feature | Write permissions | Read permissions |
|---|---|---|
| Alerts and incidents | Defender Permissions: Alerts (manage) Entra ID roles: Global Administrator, Security Administrator, Security Operator |
Write roles Defender Permissions: Security data basics Entra ID roles: Global Reader, Security Reader |
| Vulnerabilities | Defender Permissions: Response (manage)/ Security operations / Security data Entra ID roles: Global Administrator, Security Administrator, Security Operator |
Write roles Defender Permissions: Vulnerability management (read) Entra ID roles: Global Reader, Security Reader |
| Inventory | Defender Permissions: Onboard offboard device: Detection tuning (manage) Manage device tags: Alerts (manage) Entra ID roles: Global Administrator, Security Administrator, Security Operator |
Write roles Defender Permissions: Security data basics/Security operations / Security data Entra ID roles: Global Reader, Security Reader |
| Device group | Defender Permissions: Authorization (Read and manage) Entra ID roles: Global Administrator, Security Administrator |
Defender Permissions: Authorization (write roles, Read-only) |
To assign roles and permissions for other Microsoft Defender for Endpoint features, such as alerts, incidents and inventory, see assign roles and permissions for Defender for Endpoint.
For more information, see map Defender XDR Unified RBAC permissions.