Sensitivity label configuration for Australian Government compliance with PSPF
This article provides guidance for Australian Government organizations on the configuration of Microsoft Purview sensitivity labeling. Its purpose is to help organizations to strengthen their approaches to data security and to streamline the deployment of Microsoft Purview capabilities. Recommendations in this guide closely align with requirements outlined in the Protective Security Policy Framework (PSPF) and Information Security Manual (ISM).
Sensitivity labels are created from the Microsoft Purview portal, under the Information Protection menu.
To create a sensitivity label, administrators need to provide a label name, a description for users and some other configuration items, which are discussed in this article.
Label naming
Label name is a unique identifier for a sensitivity label. This field isn't visible to users but is visible to administrators when configuring labels.
Label names can't contain special characters. This can mean that administrators need to omit certain characters, such as the : in 'OFFICIAL: Sensitive.' Some special characters like colons are permitted elsewhere such as in sensitivity label content marking. When marking items, it's the content marking which applies, so lack of colon characters in label names has no effect on PSPF compliance.
The label display name is visible to users when selecting a sensitivity label. It doesn't need to be unique and can contain some special characters. As with label name, display name can't contain the colon : character, but visual markings (discussed shortly) can be displayed.
The configuration suggested in this guide makes use of a tiered label taxonomy that includes what are referred to as sublabels. A sublabel is a label that sits below another label. Labels with sublabels are referred to as 'parent labels.' In a PSPF aligned configuration, there can be a clash in labels, as the diagram illustrates.
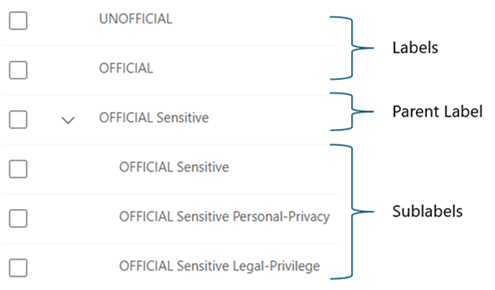
Label naming conflicts
To avoid a label naming conflicts, label names must be unique. This requires to give either the label or sublabel a name that doesn’t align with the label display name. The parent label is only used for the user interface. The sublabel is applied to actual items and seen by users. For simplicity, Microsoft recommends keeping the sublabel name in alignment with label display name, and naming the parent label differently. For example, apply a prefix to the parent label name, such as 'cat_' for category, to indicate that it's the parent. For example:
| Label name (not seen by end user) | Label type | Label purpose | label display name (seen by end user) |
|---|---|---|---|
| cat_OFFICIAL Sensitive | Parent label | Used in sensitivity menu to display a set of sublabels. Not applied to items. | OFFICIAL Sensitive |
| OFFICIAL Sensitive | Sublabel | Is applied to items and contains configuration. | OFFICIAL Sensitive |
Tip
If your organization has previously named and deployed labels carefully consider if re-creating labels to align with the previous example is necessary. Underlying label names are only visible to administrators and only in certain administrative scenarios such as usage reporting and content explorer.
Label descriptions for users
Label descriptions for users field is displayed as 'tooltips' to users, to assist them in their label selection. For example:
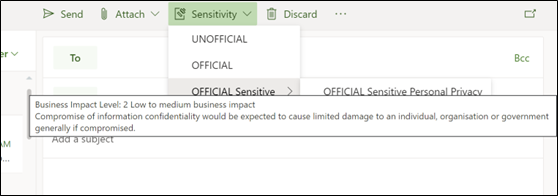
Tip
Make sure that tooltip wording is clearly understandable to users, to help ensure correct application of labels to items. If tooltips are not used or poorly worded, there is a risk users will apply incorrect labels to items, resulting in improper data security controls.
Label descriptions should include information on all elements included in a label, such as (but not limited to):
- Classifications
- Caveats
- Information Management Markers (IMMs)
For example, if marking an item as 'OFFICIAL: Sensitive NATIONAL CABINET', be sure to include descriptions for both 'OFFICIAL: Sensitive' and also 'NATIONAL CABINET' markings. Without both markings, when a user receives an item and moves their mouse over the applied label, they don't see the description for both elements. Both elements label descriptions are required for a user to understand their full obligations with that data.
Label descriptions examples
The following table is an extract from PSPF Policy 8 and provides basic label descriptions suggestions, which can be tailored to a Government organization's requirements:
| Sensitivity label | Label description |
|---|---|
| UNOFFICIAL | No Business Impact This information doesn't form part of official duty. |
| OFFICIAL | Low Business Impact Most official information created or processed by the public sector. This includes routine business operations and services. Compromise of OFFICIAL information would result in no or insignificant damage to individuals, organizations, or government. |
| OFFICIAL Sensitive (Category) | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. |
| OFFICIAL Sensitive | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. |
| OFFICIAL Sensitive Personal Privacy | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. Personal Privacy indicates that the item also contains personal information collected for business purposes. |
| OFFICIAL Sensitive Legal Privilege | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. Legal Privilege indicates that the item also contains information is subject to legal professional privilege. Compromise of the confidentiality of the information is likely to cause at least limited damage to the national interest, organizations, or individuals. |
| OFFICIAL Sensitive Legislative Secrecy | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. Information is also subject to one or more legislative secrecy provisions. Compromise of the confidentiality of this information is likely to cause at least limited damage to the national interest, organizations, or individuals. |
| OFFICIAL Sensitive NATIONAL CABINET | Low to Medium Business Impact OFFICIAL information that due to its sensitive nature requires limited dissemination. Compromise of the information would result in limited damage to an individual, organization, or government. NATIONAL CABINET identifies any information that which has been specifically prepared for National Cabinet or its subcommittees. It's to be handled in accordance with Cabinet conventions and within legal Frameworks and processes such as Freedom of Information, parliamentary inquiries and judicial processes. |
| PROTECTED (Category) | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. |
| PROTECTED | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. |
| PROTECTED Personal Privacy | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. Personal Privacy indicates that the item also contains personal information collected for business purposes. |
| PROTECTED Legal Privilege | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. Legal Privilege indicates that the item also contains information is subject to legal professional privilege. Compromise of the confidentiality of the information is likely to cause at least limited damage to the national interest, organizations, or individuals. |
| PROTECTED Legislative Secrecy | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. Information is also subject to one or more legislative secrecy provisions. Compromise of the confidentiality of this information is likely to cause at least limited damage to the national interest, organizations, or individuals. |
| PROTECTED CABINET | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. The CABINET caveat identifies any information that has been prepared for informing the Cabinet, reveals decision or deliberations of Cabinet, is prepared by departments to brief their ministers on matters proposed for Cabinet or has been created for informing a proposal to be considered by the Cabinet. |
| PROTECTED NATIONAL CABINET | High Business Impact Valuable, important, and sensitive information. Compromise of PROTECTED information would be expected to cause damage to the national interest, organizations, or individuals. NATIONAL CABINET identifies any information that which has been specifically prepared for National Cabinet or its subcommittees. It's to be handled in accordance with Cabinet conventions and within legal Frameworks and processes such as Freedom of Information, parliamentary inquiries and judicial processes. |
Sensitivity label color
Label color options help to improve user awareness of item sensitivity and enhance the user interface of label aware clients. They do this by color coding the shield icon that appears alongside sensitivity labels.
PSPF Policy 8 Requirement 4 states that colors may be used as an alternative to text-based markings for situations where such capabilities aren't available.
| Requirement | Detail |
|---|---|
| PSPF Policy 8 Requirement 4 version 2018.6 | b. If text-based protective markings can't be used, using color-based protective markings, or c. If text or color-based protective markings can't be used (for example, verbal information), applying the entity’s marking scheme for such scenarios. Entities must document a marking scheme for this purpose and train personnel appropriately. |
PSPF Policy 8 also provides detail on the colors that can be used for each marking.
| Security classification | Color-based marking |
|---|---|
| OFFICIAL: Sensitive | Yellow |
| PROTECTED | Blue |
Although not their stated intent, these colors can optionally be used to complement other visual markings capabilities. Label colors have been suggested for each label in configuration examples.
PSPF Policy 8 doesn't define colors for UNOFFICIAL and OFFICIAL markings. However, most organizations seem to be making use grey for the color of these labels.
Note
Microsoft recommends use of both color and word based markings to improve user experience and accessibility.
Label scope
Label scope is used to enable specific configuration options for a sensitivity label. Scope options include:
- Files allowing for this label to be applied to files (office documents & PDFs).
- Emails allowing for emails to be marked via Outlook or other label aware email clients.
- Meetings allowing for Teams meetings or outlook calendar items to be labeled.
- Groups and sites allowing for the label to be applied to SharePoint sites, Microsoft 365 groups, and Teams.
- Schematized data assets (preview) allowing for application of labels to database columns.
The groups and sites and schematized data assets options require enablement before they're available in your tenant. Configuration steps for groups and sites are outlined in enabling groups and sites integration.
Schematized data assets options are out of scope of this guide as most Australian government organizations are more concerned with marking of files and emails at this point. For more information on these capabilities, see labeling in the Microsoft Purview Data Map.
Selecting one of the available scope options is required to continue with label creation. File and email scope options are selected by default.
Enablement of each configuration in a staged approach is recommended, as:
The groups and sites option is less likely to be relevant to labels containing IMMs. Typical use of this scope option seems to be that a label containing an IMM (for example, 'OFFICIAL Sensitive Personal Privacy'), would apply more often to individual items, such as documents. In some organizations, it can apply to specific SharePoint sites. An example is CABINET labels, so organizations need to plan and tailor accordingly.
The configuration suggested in this guide makes use of sublabels, providing a label hierarchy and making label selection easier for users. Use of sublabels will group labels into categories. For example, a category of 'OFFICIAL Sensitive' with sublabels of all required combinations of 'OFFICIAL Sensitive,' caveats and IMMs. Sublabeling affects other configuration options such as label change justification and data out-of-place alerting. Microsoft recommends these configurations are planned before deployment.
Label encryption
The label encryption scope options allow Azure Rights Management to apply encryption to items when they're labeled. Azure Rights Management encryption then ensures that the items can only be accessed by authorized users.
For those that are new to Microsoft Purview, it's recommended that encryption is disabled while building and completing initial testing. This feature may impact usability and integration with other services and often requires a higher level of capability maturity for successful enablement. More information on encryption configuration is provided in sensitivity label encryption.
Sensitivity label content marking
This set of options allows for the application of text-based visual markings to documents and emails. The available options are header, footer, and watermark. These configuration options align with PSPF marking requirements.
| Requirement | Detail |
|---|---|
| PSPF policy 8 requirement 4 (version 2018.6) | Requirement 4 indicates text-based protective markings are the preferred method to identify sensitive and security classified information. |
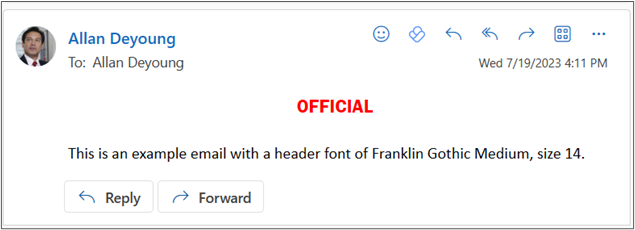
Configurations of label visual markings, font, and bold size can be adjusted with PowerShell. For example, to change the font applied to items in font 'Franklin Gothic Medium,' size 12, along with red text, the following PowerShell script can be used.
`Set-Label -Identity UNOFFICIAL -ApplyContentMarkingHeaderFontName "Franklin Gothic Medium"
This script provides the following visual marking, which aligns closely with the examples provided in PSPF Policy 8:
Content variables
Content variables changes markings based on the application that is in use; Word, Excel, PowerPoint, or Outlook.
To implement content variables, the application that a marking is applied to can be specified via codes entered into the header, footer, or watermark text fields. For example, configuring a footer using the following syntax causes the marking to appear in Word documents but omit it from Outlook emails, PowerPoint, and Excel:
${If.App.Word}UNOFFICIAL ${If.End}
For more information on content variables and examples of marking syntax, see Content markings with variables.
Importance of content marking
Client applications, such as Microsoft 365 Apps, provide inbuilt label indicators to users. Microsoft recommends use of these prominent visual markings because:
Label-based markings are provided by a sensitivity label. Labels only exist within an organizations internal environment. If a labeled item was to be sent to an external organization, such indicators aren't visible, unless addressed via approaches covered in automatic application of sensitivity labels.
Text-based markings are embedded into documents and/or emails and are visible regardless of the client being used to open or edit items. Visible markings means that an external recipient who might not be using a Microsoft 365 Apps client can still see applied text-based markings. Markings are also visible on items that are exported to PDF or printed.
Text-based markings provide useful indicators of item sensitivity and can be valuable in situations where standard indicators, such as email x-headers, are removed by email clients or services. In such situations the marking can act as a backup sensitivity identifier and can be used by auto-labeling to reapply the required sensitivity label. For more information, see service-based auto-labeling.
Auto-labeling
The auto-labeling options configured as part of a sensitivity label's configuration are referred to as client-based auto-labeling. This capability can provide label recommendations to users working in Outlook or Office clients, that prompt the users to raise the sensitivity label based on the detection of sensitive content. For example, a user drafting an UNOFFICIAL email that contains either a sensitive keyword or patterns that align with PROTECTED information, could be prompted to raise the item’s sensitivity to PROTECTED. This capability:
- Helps to ensure label correctness.
- Helps ensure that applied labels are maintained on any downstream items, such as reply emails or Copilot for Microsoft 365 generated content.
- Helps to educate users on correct label application.
Client-based auto-labeling is a more advanced capability, which does require some consideration to be used effectively. Organizations may want to keep these options disabled on initial configuration but enable them as their compliance maturity increases.
For further advice on the configuration of client-based auto-labeling in alignment with Australian government requirements, see client-based auto-labeling recommendations.
Configuration Examples
The following table provides sample configuration, which aligns with PSPF requirements:
| Label name | Label display name | Scope | Label Color | Content marking |
|---|---|---|---|---|
| UNOFFICIAL | UNOFFICIAL | Files, Email, Sites & Teams, Meetings | Green | Header: Color: RED, Size: 12, Align: Center, Text: UNOFFICIAL Footer: Color: RED, Size: 12, Align: Center, Text: UNOFFICIAL |
| OFFICIAL | OFFICIAL | Files, Email, Sites & Teams, Meetings | Grey | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL |
| Cat_OFFICIAL Sensitive | OFFICIAL Sensitive | Files, Email | Yellow | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive |
| OFFICIAL Sensitive | OFFICIAL Sensitive | Files, Email, Sites & Teams, Meetings | N/A | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive |
| OFFICIAL Sensitive Personal Privacy | OFFICIAL Sensitive Personal Privacy | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Personal Privacy Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Personal Privacy |
| OFFICIAL Sensitive Legal Privilege | OFFICIAL Sensitive Legal Privilege | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Legal Privilege Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Legal Privilege |
| OFFICIAL Sensitive Legislative Secrecy | OFFICIAL Sensitive Legislative Secrecy | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Legislative Secrecy Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive Legislative Secrecy |
| OFFICIAL Sensitive NATIONAL CABINET | OFFICIAL Sensitive NATIONAL CABINET | Files, Email, Sites & Teams | N/A | Header: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive//NATIONAL CABINET Footer: Color: RED, Size: 12, Align: Center, Text: OFFICIAL: Sensitive//NATIONAL CABINET |
| Cat_PROTECTED | PROTECTED | Files, Email | Blue | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED |
| PROTECTED | PROTECTED | Files, Email, Sites & Teams, Meetings | N/A | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED |
| PROTECTED Personal Privacy | PROTECTED Personal Privacy | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED Personal Privacy Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED Personal Privacy |
| PROTECTED Legal Privilege | PROTECTED Legal Privilege | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED Legal Privilege Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED Legal Privilege |
| PROTECTED Legislative Secrecy | PROTECTED Legislative Secrecy | Files, Email | N/A | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED Legislative Secrecy Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED Legislative Secrecy |
| PROTECTED CABINET | PROTECTED CABINET | Files, Email, Sites & Teams | N/A | Header: Color: RED, Size: 12, Align: Center, Text: PROTECTED CABINET Footer: Color: RED, Size: 12, Align: Center, Text: PROTECTED CABINET |