Tutorial: Add Security Headers with Rules Engine
Important
Azure Front Door (classic) will be retired on March 31, 2027. To avoid any service disruption, it is important that you migrate your Azure Front Door (classic) profiles to Azure Front Door Standard or Premium tier by March 2027. For more information, see Azure Front Door (classic) retirement.
This tutorial demonstrates how to implement security headers to prevent browser-based vulnerabilities such as HTTP Strict-Transport-Security (HSTS), X-XSS-Protection, Content-Security-Policy, and X-Frame-Options. Security attributes can also be defined with cookies.
The example below shows how to add a Content-Security-Policy header to all incoming requests that match the path defined in the route associated with your Rules Engine configuration. In this scenario, only scripts from the trusted site https://apiphany.portal.azure-api.net are allowed to run on the application.
In this tutorial, you will learn how to:
- Configure a Content-Security-Policy within Rules Engine.
Prerequisites
- An Azure subscription.
- An Azure Front Door. To complete this tutorial, you must have an Azure Front Door configured with Rules Engine. For more information, see Quickstart: Create an Azure Front Door and Configure your Rules Engine.
Add a Content-Security-Policy header in Azure portal
In your Azure Front Door resource, go to Settings and select Rules engine configuration. Choose the rules engine where you want to add the security header.
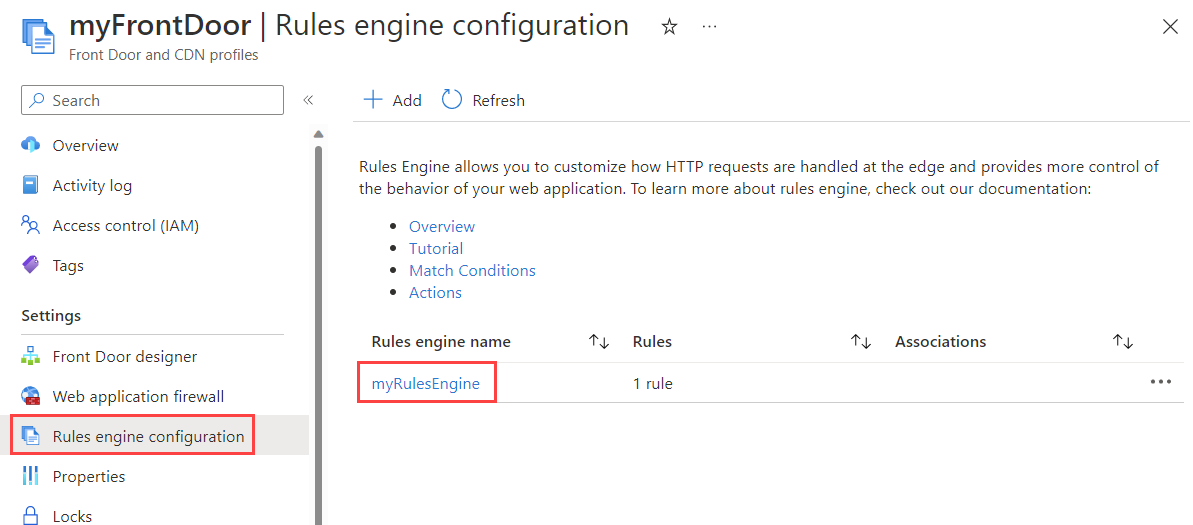
Click Add rule to create a new rule. Name the rule and then select Add an Action > Response Header.
Set the Operator to Append to add this header to all incoming requests for this route.
Enter the header name: Content-Security-Policy and specify the values for this header. In this example, use
script-src 'self' https://apiphany.portal.azure-api.net. Click Save.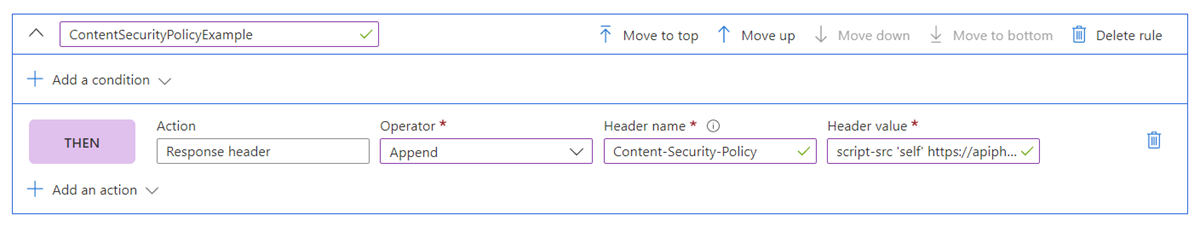
Note
Header values are limited to 640 characters.
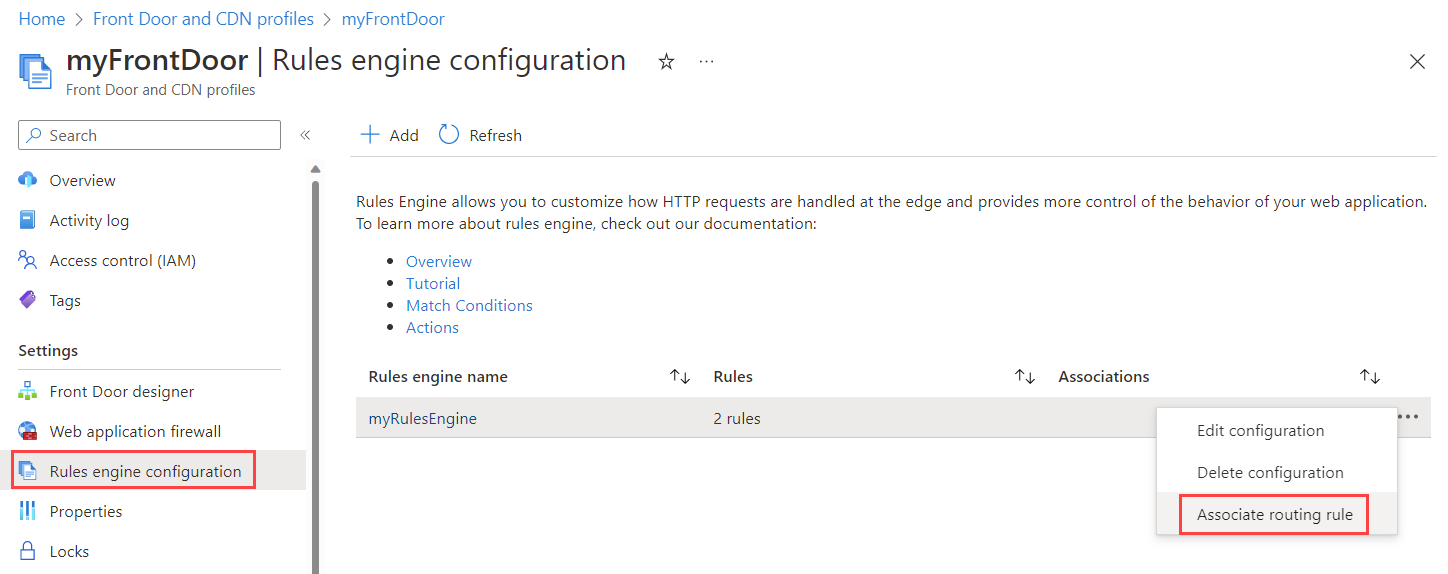
After adding the rules, associate your Rules engine configuration with the Route Rule of your chosen route. This step is necessary for the rule to take effect.
Note
In this example, no match conditions were added to the rule. The rule will apply to all incoming requests that match the path defined in the Route Rule. To apply it to a subset of requests, add specific match conditions to the rule.
Clean up resources
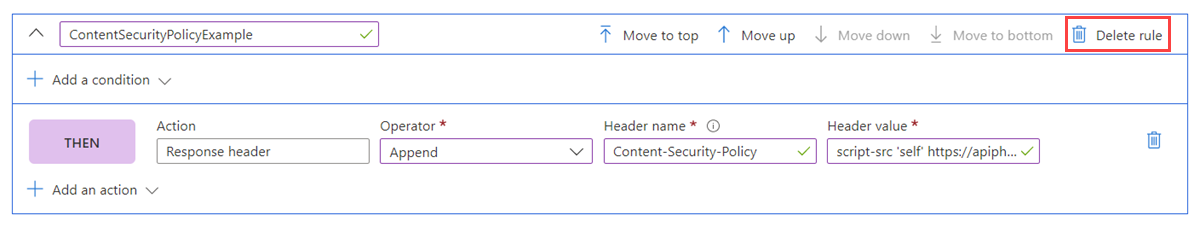
If you no longer need the security header rule configured in the previous steps, you can remove it. To do this, go to the rules engine in your Azure Front Door resource and select Delete rule.
Next steps
To learn how to configure a Web Application Firewall for your Azure Front Door, proceed to the next tutorial.