About Azure Arc gateway for Azure Local (preview)
Applies to: Azure Local 2411.1 and later
Important
Azure Stack HCI is now part of Azure Local. Learn more.
This article provides an overview of the Azure Arc gateway for Azure Local. The Arc gateway can be enabled on new deployments of Azure Local running software version 2408 and later. This article also describes how to create and delete the Arc gateway resource in Azure.
You can use the Arc gateway to significantly reduce the number of required endpoints needed to deploy and manage Azure Local instances. Once you create the Arc gateway, you can connect to and use it for new deployments of Azure Local.
For information on how to deploy the Azure Arc gateway for standalone servers (not Azure Local machines), see Simplify network configuration requirements through Azure Arc gateway.
Important
This feature is currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
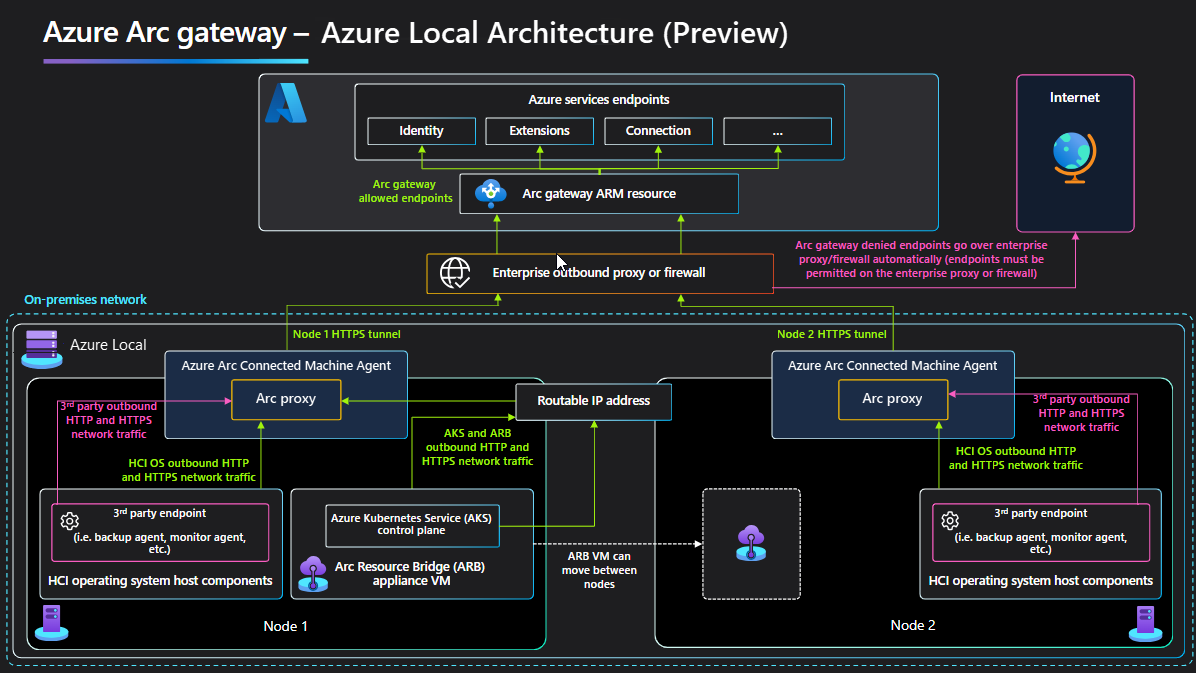
How it works
The Arc gateway works by introducing the following components:
Arc gateway resource – An Azure resource that acts as a common entry point for Azure traffic. This gateway resource has a specific domain or URL that you can use. When you create the Arc gateway resource, this domain or URL is a part of the success response.
Arc proxy – A new component that is added to the Arc Agentry. This component runs as a service (Called the Azure Arc Proxy) and works as a forward proxy for the Azure Arc agents and extensions. The gateway router doesn't need any configuration from your side. This router is part of the Arc core agentry and runs within the context of an Arc-enabled resource.
Once you integrate the Arc gateway with release 2411 of Azure Local deployments, each machine gets Arc proxy along with other Arc Agents.
When Arc gateway is used, the http and https traffic flow changes as follows:
Traffic flow for Azure Local host operating system components
OS proxy settings are used to route all HTTPS host traffic through Arc proxy.
From Arc proxy, the traffic is forwarded to Arc gateway.
Based on the configuration in the Arc gateway, if allowed, the traffic is sent to target services. If not allowed, Arc proxy redirects this traffic to the enterprise proxy (or direct outbound if no proxy set). Arc proxy automatically determines the right path for the endpoint.
Traffic flow for Arc appliance Arc Resource Bridge (ARB) and AKS control plane
The routable IP (failover clustered IP resource as of now) is used to forward the traffic through Arc proxy running on the Azure Local host machines.
ARB and AKS forward proxy are configured to use the routable IP.
With the proxy settings in place, ARB, and AKS outbound traffic is forwarded to Arc Proxy running on one of the Azure Local machines over the routable IP.
Once the traffic reaches Arc proxy, the remaining flow takes the same path as described. If traffic to the target service is allowed, it is sent to Arc gateway. If not, it is sent to the enterprise proxy (or direct outbound if no proxy set). Note that for AKS specifically, this path is used for downloading docker images for Arc Agentry and Arc Extension Pods.
Traffic flow for Arc VMs
Http and https traffic are forwarded to the enterprise proxy. Arc proxy inside the Arc VM is not yet supported in this version.
Traffic flows are illustrated in the following diagram:
Supported and unsupported scenarios
You can use the Arc gateway in the following scenario for Azure Local versions 2411.1 or later:
- Enable Arc gateway during deployment of new Azure Local instances running versions 2411.1 or later.
Unsupported scenarios for Azure Local, versions 2408, 2411 and 2411.1 include:
Azure Local instances updated from versions 2402 or 2405 to versions 2408 or 2411 can't take advantage of all the new endpoints supported by this Arc gateway preview. Host components, Arc extensions, ARB, and AKS required endpoints are only supported when enabling the Arc gateway as part of a new version 2408 deployment.
Enabling Arc gateway after deployment cannot take advantage of all the new endpoints supported by this Arc gateway preview. Host, Arc extensions, ARB, and AKS required endpoints are only supported when enabling the Arc gateway as part of a new deployment.
Azure Local endpoints not redirected
As part of the Azure Local version 2411.1 preview update, the endpoints from the table are required and must be allowlisted in your proxy or firewall to deploy the Azure Local instance. These version 2408 and 2411 endpoints are not redirected via the Arc gateway:
| Endpoint # | Required endpoint | Component |
|---|---|---|
| 1 | http://go.microsoft.com:443 |
Arc registration |
| 2 | http://login.microsoftonline.com:443 |
Arc registration |
| 3 | http://<region>.login.microsoft.com:443 |
Arc registration |
| 4 | http://download.microsoft.com:443 |
Arc registration |
| 5 | http://management.azure.com:443 |
Arc registration |
| 6 | http://gbl.his.arc.azure.com:443 |
Arc registration |
| 7 | http://<region>.his.arc.azure.com:443 |
Arc registration |
| 8 | http://dc.services.visualstudio.com:443 |
Arc registration |
| 9 | https://<region>.obo.arc.azure.com:8084 |
AKS extensions |
| 10 | http://<yourarcgatewayId>.gw.arc.azure.com:443 |
Arc gateway |
| 11 | http://<yourkeyvaultname>.vault.azure.net:443 |
Azure Key Vault |
| 12 | http://<yourblobstorageforcloudwitnessname>.blob.core.windows.net:443 |
Cloud Witness Storage Account |
| 13 | http://files.pythonhosted.org:443 |
Microsoft On-premises Cloud/ARB/AKS |
| 14 | http://pypi.org:443 |
Microsoft On-premises Cloud/ARB/AKS |
| 15 | http://raw.githubusercontent.com:443 |
Microsoft On-premises Cloud/ARB/AKS |
| 16 | http://pythonhosted.org:443 |
Microsoft On-premises Cloud/ARB/AKS |
| 17 | http://ocsp.digicert.com |
Certificate Revocation List for Arc extensions |
| 18 | http://s.symcd.com |
Certificate Revocation List for Arc extensions |
| 19 | http://ts-ocsp.ws.symantec.com |
Certificate Revocation List for Arc extensions |
| 20 | http://ocsp.globalsign.com |
Certificate Revocation List for Arc extensions |
| 21 | http://ocsp2.globalsign.com |
Certificate Revocation List for Arc extensions |
| 22 | http://oneocsp.microsoft.com |
Certificate Revocation List for Arc extensions |
| 23 | http://dl.delivery.mp.microsoft.com |
Windows Update |
| 24 | http://*.tlu.dl.delivery.mp.microsoft.com |
Windows Update |
| 25 | http://*.windowsupdate.com |
Windows Update |
| 26 | http://*.windowsupdate.microsoft.com |
Windows Update |
| 27 | http://*.update.microsoft.com |
Windows Update |
Restrictions and limitations
Consider the following limitations of Arc gateway in this release:
- TLS terminating proxies aren't supported with the Arc gateway preview.
- Use of ExpressRoute, Site-to-Site VPN, or Private Endpoints in addition to the Arc gateway (preview) isn't supported.
Create the Arc gateway resource in Azure
You can create an Arc gateway resource using the Azure portal, Azure CLI, or Azure PowerShell.
- Sign in to Azure portal.
- Go to the Azure Arc > Azure Arc gateway page, then select Create.
- Select the subscription and resource group where you want the Arc gateway resource to be managed within Azure. An Arc gateway resource can be used by any Arc-enabled resource in the same Azure tenant.
- For Name, enter the name for the Arc gateway resource.
- For Location, enter the region where the Arc gateway resource should live. An Arc gateway resource can be used by any Arc-enabled resource in the same Azure tenant.
- Select Next.
- On the Tags page, specify one or more custom tags to support your standards.
- Select Review & Create.
- Review your details, and then select Create.
The gateway creation process takes nine to ten minutes to complete.
Detach or change the Arc gateway association from the machine
To detach the gateway resource from your Arc-enabled server, set the gateway resource ID to null. If you want to attach your Arc-enabled server to another Arc gateway resource just update the name and resource ID with the new Arc gateway information:
az arcgateway settings update --resource-group <Resource Group> --subscription <subscription name> --base-provider Microsoft.HybridCompute --base-resource-type machines --base-resource-name <Arc-Server's name> --gateway-resource-id "
Delete the Arc gateway resource
Before deleting an Arc gateway resource, ensure that no machines are attached. To delete the gateway resource, run the following command:
az arcgateway delete --resource group <resource group name> --gateway-name <gateway resource name>
This operation can take a couple of minutes.
Next steps
This feature is available only in Azure Local 2411.1 or later.