Blocking Internet Explorer 7 Installations
Wednesday, January 10, 2007 12:21 PM
One of the more common questions IT Admins and Managers ask us when they call in is "How do we prevent IE7 from installing on our client machines?" Although it seems like a fairly straightforward question there are several scenarios to consider:
Scenario 1: If a user gets the update from Windows Update through an Automatic Download, they must have Local Administrator rights to approve the install. Many environments without centralized patch management allow Windows Update to automatically update their client machines. If the install is not approved by a user with Administrative rights, IE7 does not install.
Scenario 2: For environments with centralized client management, you can use the IE Blocker Toolkit to set a Policy on the client machines. This is targeted for environments without a central patch management system such as WSUS or SMS. However, the caveat here is that the Blocker Toolkit does not prevent users with Local Admin rights from downloading IE7 manually and installing it either via the Microsoft site or from a branded version (such as an IE7 package offered by their ISP). The Registry entry is as follows:
Location: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Setup\7.0
Name: DoNotAllowIE70
Type: REG_DWORD
Value: 1 (this blocks the installation. Setting the value to 0 unblocks the installation)
Scenario 3: For organizations with WSUS etc, their challenge is preventing users with Administrative rights from installing IE7 manually. This can be achieved most effectively via a Software Restriction Hash Policy. The administrator creating the Group Policy will need to download each of the installer packages for the versions he wants to block and create individual Hash Rules (see KB Article 324036). You should also review the following Technet Article: Using Software Restrictions to Protect Against Unauthorized Software.
The names of the executables for each version of IE7 that you can download from Microsoft:
- XPSP2 (x86): IE7-WindowsXP-x86-enu.exe
- XP Pro x64: IE7-WindowsServer2003-x64-enu.exe
- Windows Server 2003 x64: IE7-WindowsServer2003-x64-enu.exe
- Windows Server 2003 SP1: IE7-WindowsServer2003-x86-enu.exe
- Windows Server 2003 ia64 Edition: IE7-WindowsServer2003-ia64-enu.exe
Even if the actual file name is changed after download, the hash value of the file is used to create the block.
Creating the Hash Rule
Open GPEdit.MSC, browse to Computer Configuration --> Windows Settings --> Security Settings --> Software Restriction Policies --> Additional Rules
Right Click and Select New Hash Rule …
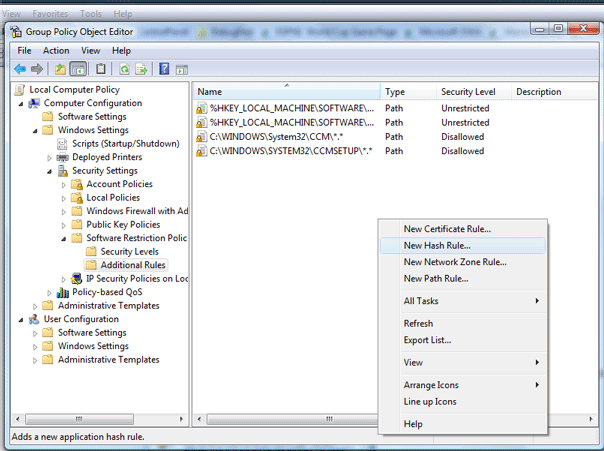
Click Browse to browse to the file you want to block. The information about the file is automatically populated.

Set the Security Level to Disallowed to prevent the file from installing and click OK.
NOTE: If you are concerned about branded versions of IE7 (such as an ISP provided version) being installed, you need to take the Hashing step to the next level. Extract the IESetup.EXE out of the branded package and hash each version. That way the actual installer is blocked.
Useful Links:
- Toolkit to Disable Automatic Delivery of Internet Explorer 7
- Blocker Toolkit FAQ
- How to Use Software Restriction Policies in W2K3
- Software Restriction Policies for Windows XP Clients
- Using Software Restriction Policies to Protect Against Unauthorized Software
- Creating a Hash Rule
- IE9: How to set IE 9 Blocker policy
- IE9: Pilot and Deploy Internet Explorer 9
- IE9: Internet Explorer 9 Blocker Toolkit: Frequently Asked Questions
- IE9: IE to Start Automatic Upgrades across Windows XP, Windows Vista, and Windows 7
- IE8: How to set IE 8 Blocker Policy
- IE8: Using and trouble-shooting the IE 8 Blocker Toolkit
- IE8: Internet Explorer 8 Blocker Toolkit: Frequently Asked Questions
- IE7: Blocking Internet Explorer 7 Installation
Regards,
The IE Support Team