Hi,
I've created a new VM in Azure of type "Windows Server 2022 Datacenter Azure Edition" - Core - and disabled weak cipher suites using PowerShells Disable-TlsCipherSuite.
The VM is behind an azure LoadBalancer.
Afterwards I checked with ssllabs.com. But it showed me, that there are still some weak cipher suites active.
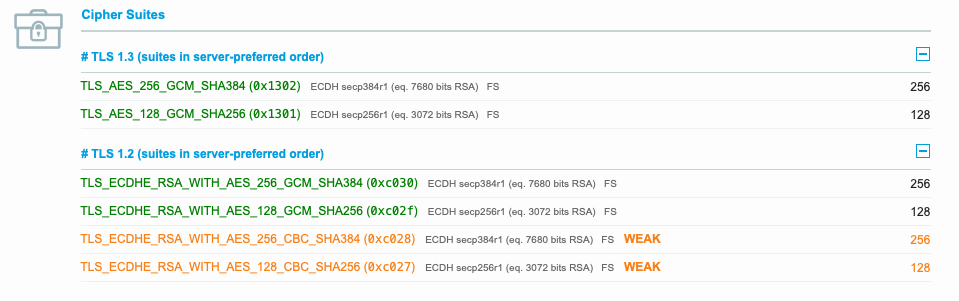
So I went ahead and tried to explicitly disable the two weak cipher suites again using Disable-TlsCipherSuite.
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027)
But PowerShell showed me, that these are already disabled.
When doing this in Server 2019 we had no problems at all. What am I missing here?
Any help appreciated.

