Global Secure Access client for macOS (Preview)
Important
The Global Secure Access client for macOS is currently in PREVIEW. This information relates to a prerelease product that might be substantially modified before release. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
The Global Secure Access client, an essential component of Global Secure Access, helps organizations manage and secure network traffic on end-user devices. The client's main role is to route traffic that needs to be secured by Global Secure Access to the cloud service. All other traffic goes directly to the network. The Forwarding Profiles, configured in the portal, determine which traffic the Global Secure Access client routes to the cloud service.
This article describes how to download and install the Global Secure Access client for macOS.
Prerequisites
- A Mac device with an Intel, M1, M2, M3, or M4 processor, running macOS version 13 or newer.
- A device registered to Microsoft Entra tenant using Company Portal.
- A Microsoft Entra tenant onboarded to Global Secure Access.
- Deployment of the Microsoft Enterprise single sign-on (SSO) plug-in for Apple devices is recommended for SSO experience based on the user who is signed in to the company portal.
- An internet connection.
Download the client
The most current version of the Global Secure Access client is available to download from the Microsoft Entra admin center.
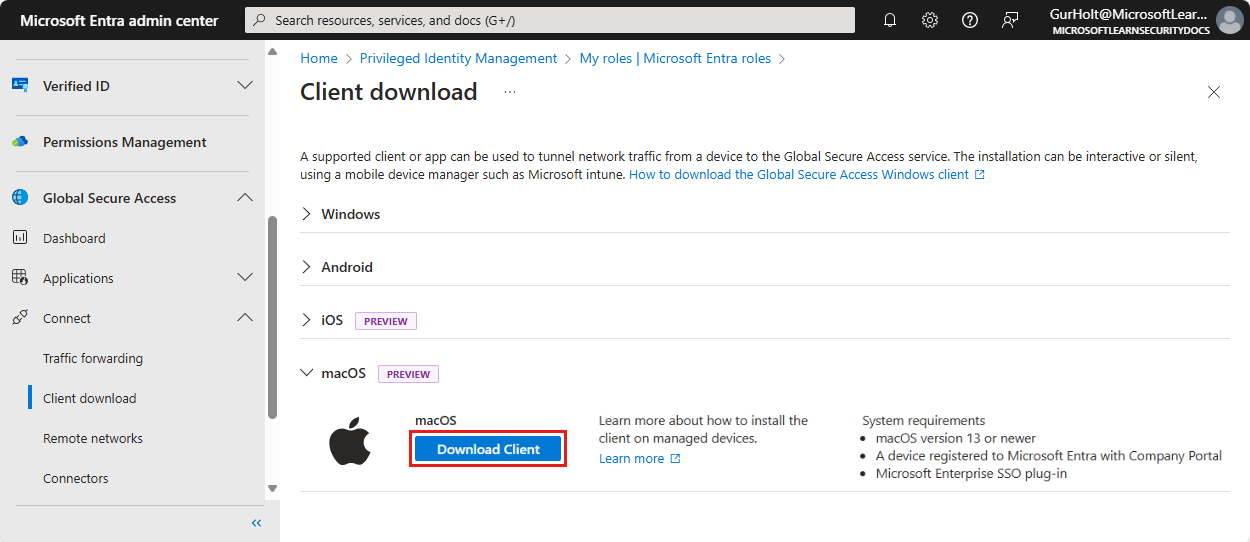
- Sign in to the Microsoft Entra admin center as a Global Secure Access Administrator.
- Browse to Global Secure Access > Connect > Client download.
- Select Download Client.
Install the Global Secure Access client
Automated installation
Use the following command for silent installation. Substitute your file path according to the download location of the .pkg file.
sudo installer -pkg ~/Downloads/GlobalSecureAccessClient.pkg -target / -verboseR
The client uses system extensions and a transparent application proxy that need to be approved during the installation. For a silent deployment without prompting the end user to allow these components, you can deploy a policy to automatically approve the components with mobile device management.
Allow system extensions through mobile device management (MDM)
The following instructions are for Microsoft Intune and you can adapt them for different MDMs:
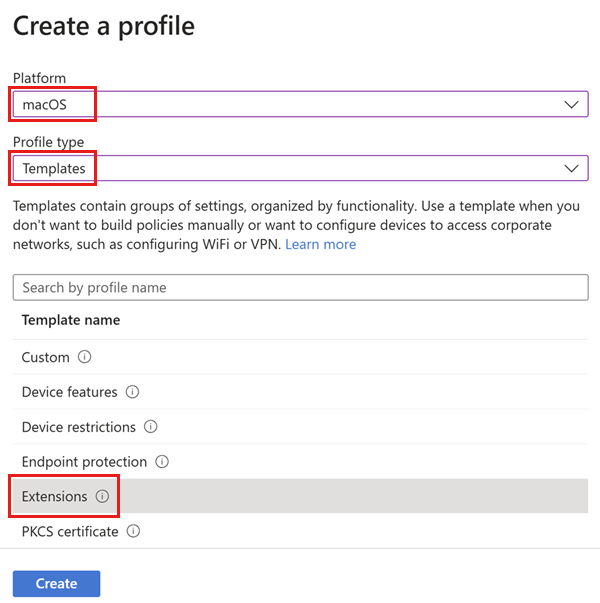
- In the Microsoft Intune admin center, select Devices > Manage devices > Configuration > Policies > Create > New policy.
- Create a profile with a Platform of macOS and a Profile type set to Settings catalog. Select Create.
- On the Basics tab, enter a name for the new profile and select Next.
- On the Configuration settings tab, select + Add settings.
- In the Settings picker, expand the System Configuration category and select System Extensions.
- From the System Extensions subcategory, select Allowed System Extensions.
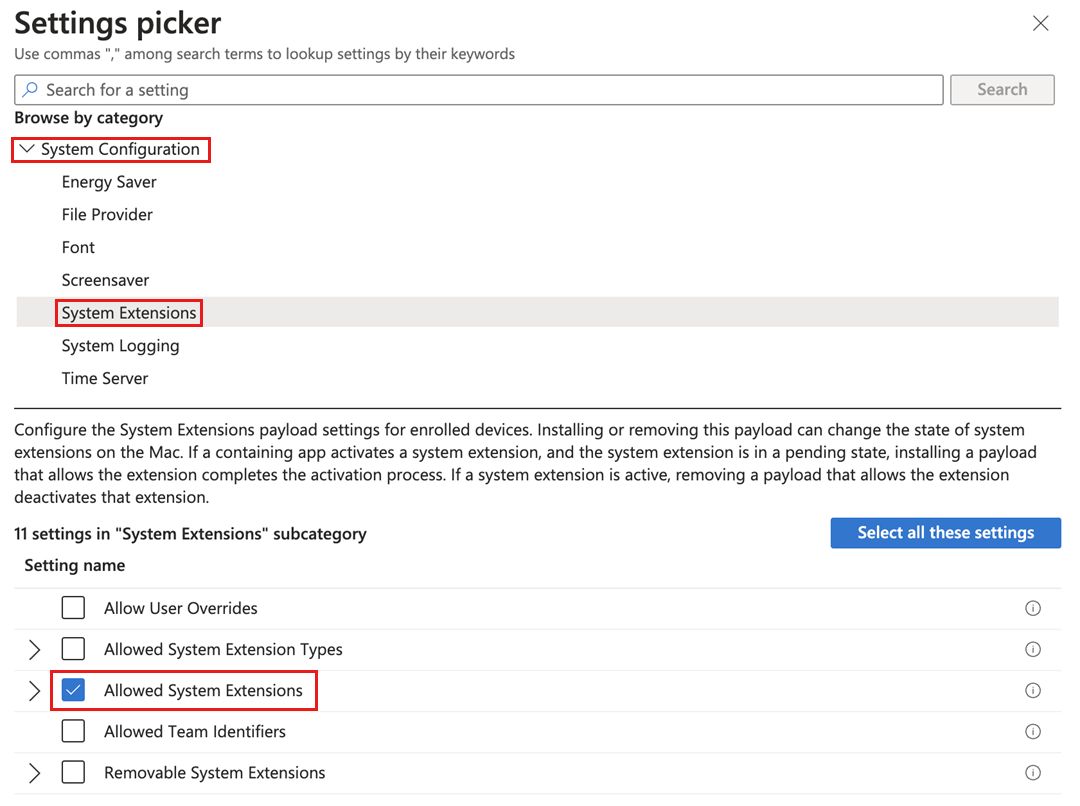
- Close the Settings picker.
- In the list of Allowed System Extensions, select + Edit instance.
- In the Configure instance dialog, configure the System Extensions payload settings with the following entries:
| Bundle identifier | Team identifier |
|---|---|
| com.microsoft.naas.globalsecure.tunnel-df | UBF8T346G9 |
| com.microsoft.naas.globalsecure-df | UBF8T346G9 |
- Select Save and Next.
- On the Scope tags tab, add tags as appropriate.
- On the Assignments tab, assign the profile to a group of macOS devices or users.
- On the Review + create tab, review the configuration and select Create.
Allow transparent application proxy through MDM
The following instructions are for Microsoft Intune and you can adapt them for different MDMs:
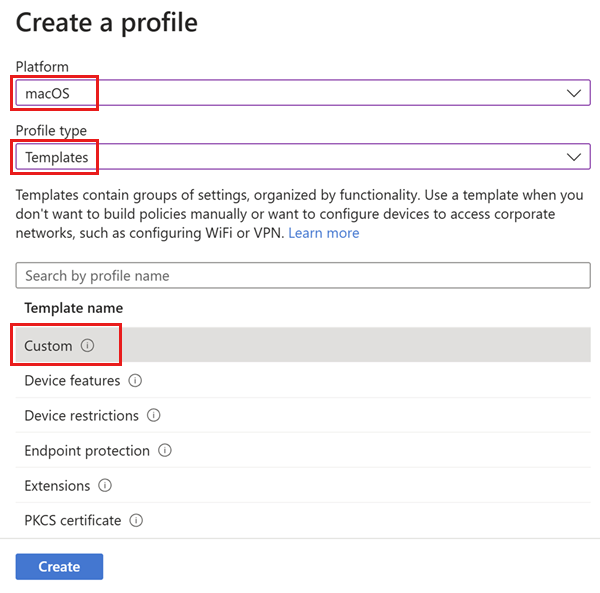
- In the Microsoft Intune admin center, select Devices > Manage devices > Configuration > Policies > Create > New policy.
- Create a profile for the macOS platform based on a template of type Custom and select Create.
- On the Basics tab, enter a Name for the profile.
- On the Configuration settings tab, enter a Custom configuration profile name.
- Keep Deployment channel set to "Device channel."
- Upload an .xml file that contains the following data:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadUUID</key>
<string>87cbb424-6af7-4748-9d43-f1c5dda7a0a6</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.naas.globalsecure-df</string>
<key>PayloadDisplayName</key>
<string>Global Secure Access Proxy Configuration</string>
<key>PayloadDescription</key>
<string>Add Global Secure Access Proxy Configuration</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>04e13063-2bb8-4b72-b1ed-45290f91af68</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.naas.globalsecure-df</string>
<key>PayloadDisplayName</key>
<string>Global Secure Access Proxy Configuration</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>TransparentProxy</key>
<dict>
<key>AuthenticationMethod</key>
<string>Password</string>
<key>Order</key>
<integer>1</integer>
<key>ProviderBundleIdentifier</key>
<string>com.microsoft.naas.globalsecure.tunnel-df</string>
<key>ProviderDesignatedRequirement</key>
<string>identifier "com.microsoft.naas.globalsecure.tunnel-df" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string>
<key>ProviderType</key>
<string>app-proxy</string>
<key>RemoteAddress</key>
<string>100.64.0.0</string>
</dict>
<key>UserDefinedName</key>
<string>Global Secure Access Proxy Configuration</string>
<key>VPNSubType</key>
<string>com.microsoft.naas.globalsecure-df</string>
<key>VPNType</key>
<string>TransparentProxy</string>
</dict>
</array>
</dict>
</plist>
- Complete the creation of the profile by assigning users and devices according to your needs.
Manual interactive installation
To manually install the Global Secure Access client:
Run the GlobalSecureAccessClient.pkg setup file. The Install wizard launches. Follow the prompts.
On the Introduction step, select Continue.
On the License step, select Continue and then select Agree to accept the license agreement.
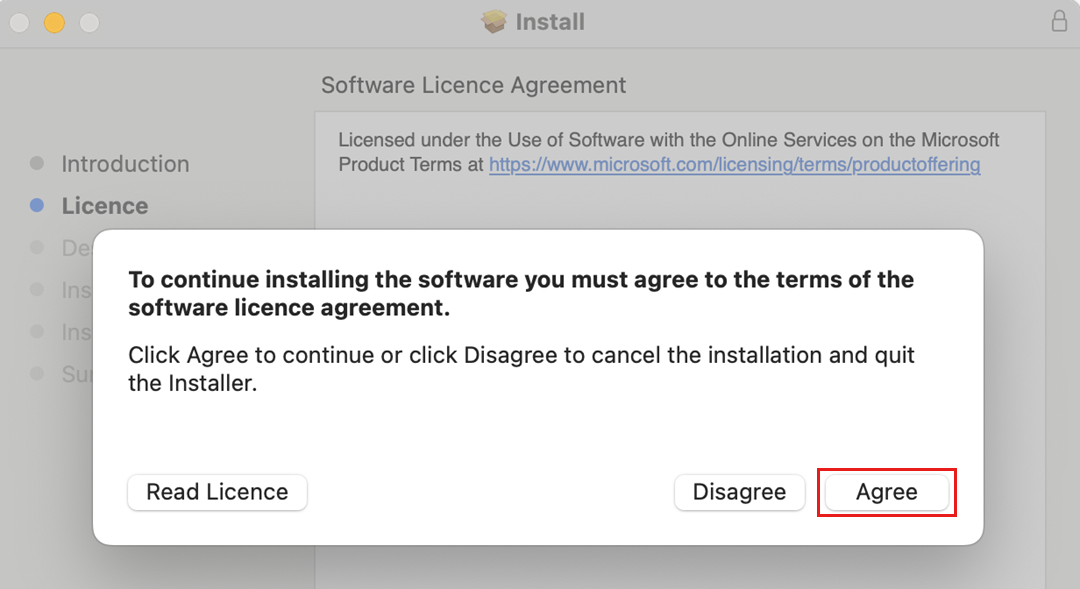
On the Installation step, select Install.
On the Summary step, when the installation is complete, select Close.
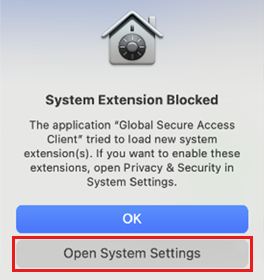
Allow the Global Secure Access system extension.
In the System Extension Blocked dialog, select Open System Settings.
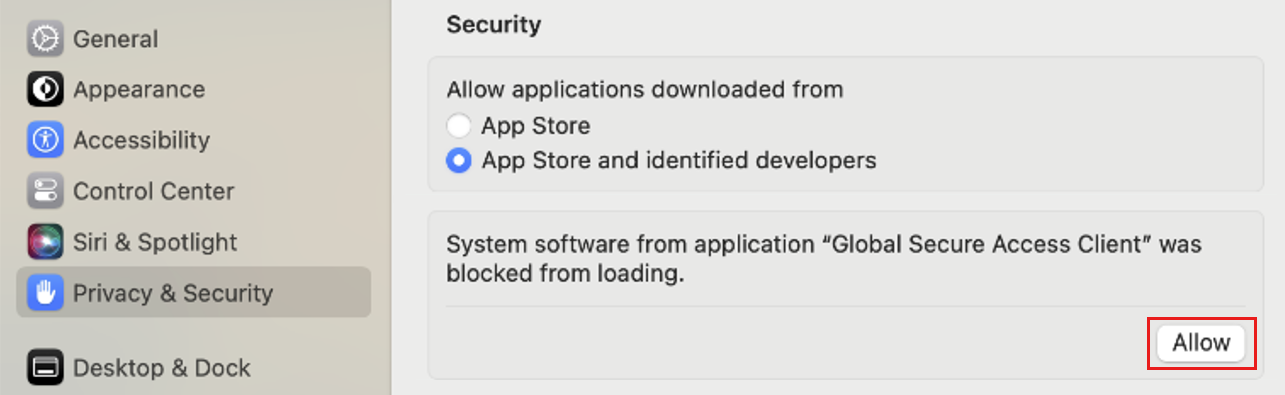
Allow the Global Secure Access client system extension by selecting Allow.
In the Privacy & Security dialog, enter your username and password to validate the approval of the system extension. Then select Modify Settings.
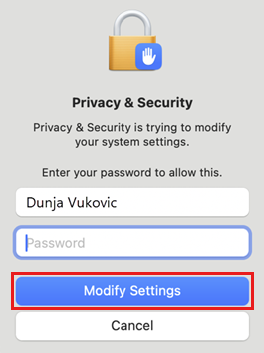
Complete the process by selecting Allow to enable the Global Secure Access client to add proxy configurations.
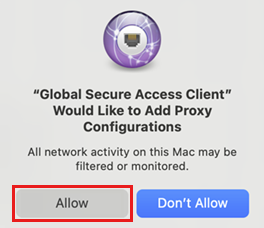
After the installation is complete, you might be prompted to sign in to Microsoft Entra.
Note
If the Microsoft Enterprise SSO plug-in for Apple devices is deployed, the default behavior is to use single sign-on with the credentials entered in the company portal.
- The Global Secure Access - Connected icon appears in the system tray, indicating a successful connection to Global Secure Access.

Upgrade the Global Secure Access client
The client installer supports upgrades. You can use the installation wizard to install a new version on a device that is currently running a previous client version.
For a silent upgrade, use the following command.
Substitute your file path according to the download location of the .pkg file.
sudo installer -pkg ~/Downloads/GlobalSecureAccessClient.pkg -target / -verboseR
Uninstall the Global Secure Access client
To manually uninstall the Global Secure Access client, use the following command.
sudo /Applications/Global\ Secure\ Access\ Client.app/Contents/Resources/install_scripts/uninstall
If you're using an MDM, uninstall the client with the MDM.
Client actions
To view the available client menu actions, right-click the Global Secure Access system tray icon.
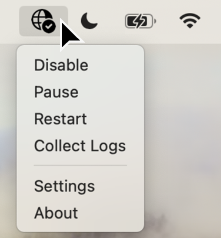
| Action | Description |
|---|---|
| Disable | Disables the client until the user enables it again. When the user disables the client, they're prompted to enter a business justification and reenter their sign-in credentials. The business justification is logged. |
| Enable | Enables the client. |
| Pause | Pauses the client for either 10 minutes, until the user resumes the client, or until the device is restarted. When the user pauses the client, they're prompted to enter a business justification and reenter their sign-in credentials. The business justification is logged. |
| Resume | Resumes the paused client. |
| Restart | Restarts the client. |
| Collect logs | Collects client logs and archives them in a zip file to share with Microsoft Support for investigation. |
| Settings | Opens the Settings and Advanced diagnostics tool. |
| About | Shows information regarding the product's version. |
Client statuses in system tray icon
| Icon | Message | Description |
|---|---|---|
| Global Secure Access Client | The client is initializing and checking its connection to Global Secure Access. | |
| Global Secure Access Client - Connected | The client is connected to Global Secure Access. | |
| Global Secure Access Client - Disabled | The client is disabled because services are offline or the user disabled the client. | |
| Global Secure Access Client - Disconnected | The client failed to connect to Global Secure Access. | |
| Global Secure Access Client - Some channels are unreachable | The client is partially connected to Global Secure Access (that is, the connection to at least one channel failed: Microsoft Entra, Microsoft 365, Private Access, Internet Access). | |
| Global Secure Access Client - Disabled by your organization | Your organization disabled the client (that is, all traffic forwarding profiles are disabled). | |
| Global Secure Access - Private Access is disabled | The user disabled Private Access on this device. | |
| Global Secure Access - could not connect to the Internet | The client couldn't detect an internet connection. The device is either connected to a network that doesn't have an Internet connection or a network that requires captive portal sign in. |
Settings and troubleshooting
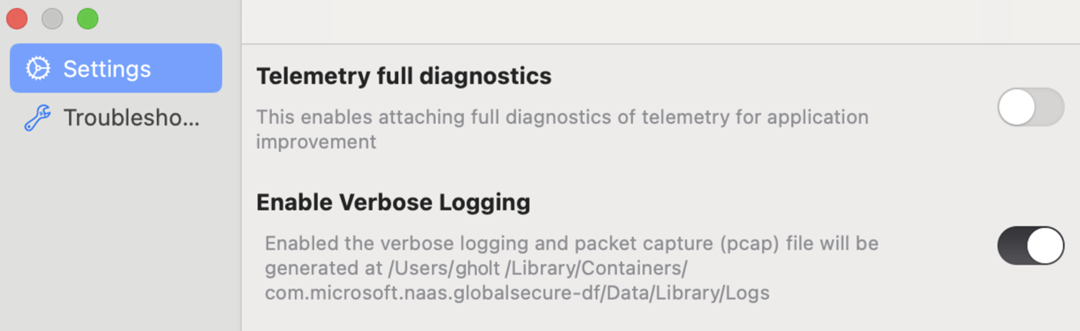
The Settings window allows you to set different configurations and do some advanced actions. The settings window contains two tabs:
Settings
| Option | Description |
|---|---|
| Telemetry full diagnostics | Sends full telemetry data to Microsoft for application improvement. |
| Enable Verbose Logging | Enables verbose logging and network capture to be collected when exporting the logs to a zip file. |
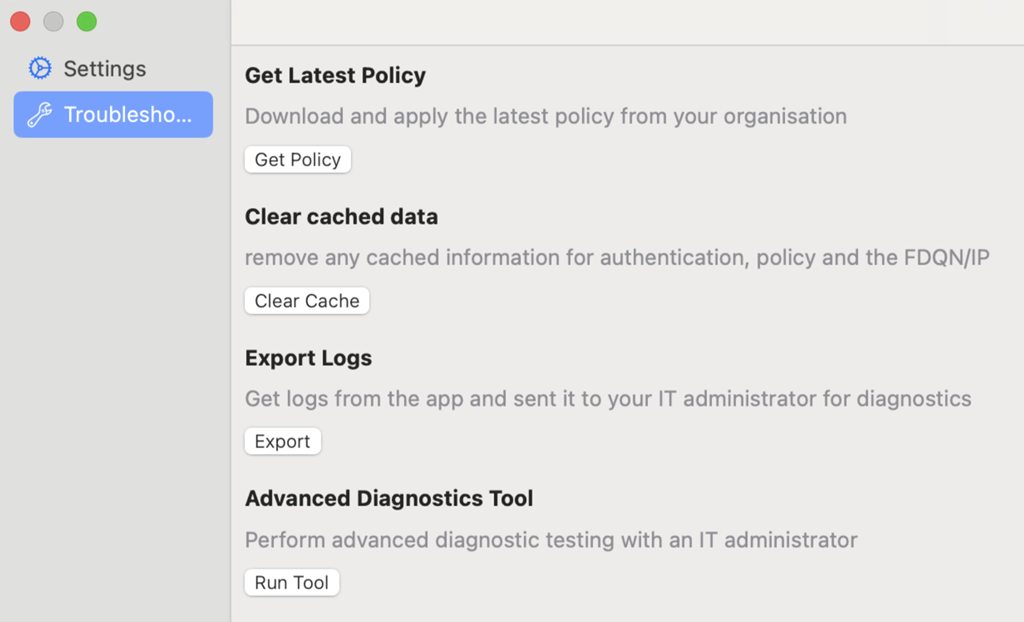
Troubleshooting
| Action | Description |
|---|---|
| Get Latest Policy | Downloads and applies the latest forwarding profile for your organization. |
| Clear cached data | Deletes the client's internal cached data related to authentication, forwarding profile, FQDNs, and IPs. |
| Export Logs | Exports logs and configuration files related to the client to a zip file. |
| Advanced Diagnostics Tool | An advanced tool to monitor and troubleshoot the client's behavior. |
Known limitations
This feature has one or more known limitations. For more detailed information about the known issues and limitations of this feature, see Known Limitations for Global Secure Access.