Global Secure Access client for Android
The Global Secure Access client can be deployed to compliant Android devices using Microsoft Intune and Microsoft Defender for Endpoint on Android. The Android client is built into the Defender for Endpoint Android app, which streamlines how your end users connect to Global Secure Access. The Global Secure Access Android client makes it easier for your end users to connect to the resources they need without having to manually configure VPN settings on their devices.
This article explains the prerequisites and how to deploy the client onto Android devices.
Prerequisites
- The product requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
- You must enable at least one Global Secure Access traffic forwarding profile.
- Device installation permissions on the device are required for installation.
- Android devices must be running Android 10.0 or later.
- Android devices must be Microsoft Entra registered devices.
- Devices not managed by your organization must have the Microsoft Authenticator app must be installed.
- Devices not managed through Intune must have the Company Portal app installed.
- Device enrollment is required for Intune device compliance policies to be enforced.
Known limitations
This feature has one or more known limitations. For more detailed information about the known issues and limitations of this feature, see Known Limitations for Global Secure Access.
Supported scenarios
Global Secure Access client for Android supports deployment for the legacy Device Administrator and Android Enterprise scenarios. The following Android Enterprise scenarios are supported:
- Corporate-owned, fully managed user devices.
- Corporate-owned devices with a work profile.
- Personal devices with a work profile.
Non-Microsoft mobile device management
Non-Microsoft mobile device management (MDM) scenarios are also supported. In these scenarios, known as Global Secure Access only mode, you only need to enable a traffic forwarding profile and configure the app according to the vendor documentation.
Deploy Microsoft Defender for Endpoint Android
There are several combinations of deployment modes and scenarios for using the Global Secure Access client for Android.
Once you enable a traffic forwarding profile and configure your network, the Global Secure Access Android client appears in the Defender app automatically; however, the Global Secure Access client is disabled by default. Users can enable the client from the Defender app. The steps to enable the client are provided in the Confirm Global Secure Access appears in Defender app section.
This legacy enrollment mode allows you to deploy Defender for Endpoint on Android with Microsoft Intune Company Portal - Device Administrator enrolled devices.
The high level process is as follows:
Deploy Defender to Intune enrolled Android devices.
Enable at least one traffic forwarding profile if Defender is already deployed.
The detailed process for deploying Defender is as follows:
Sign in to the Microsoft Intune admin center as an Intune Administrator.
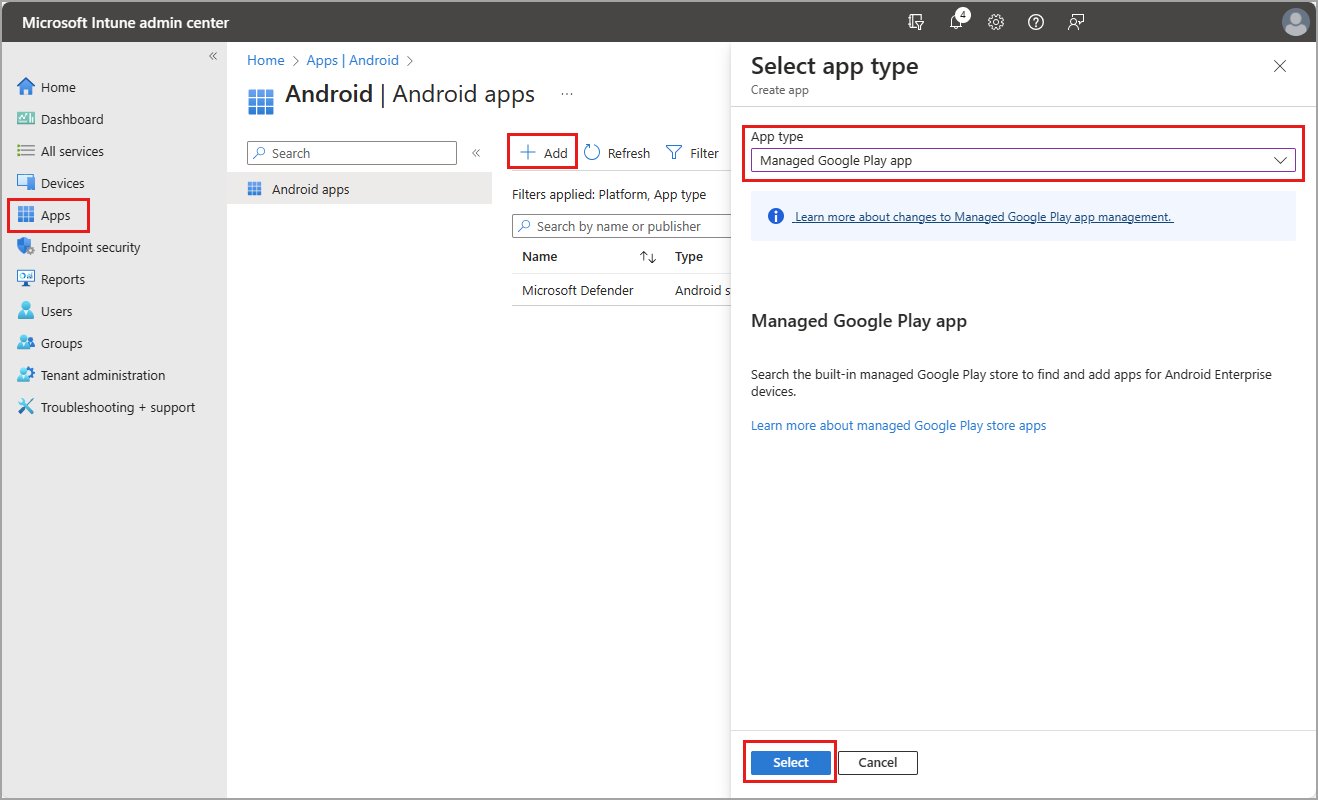
Browse to Apps > Android > Add > Android store app > Select.
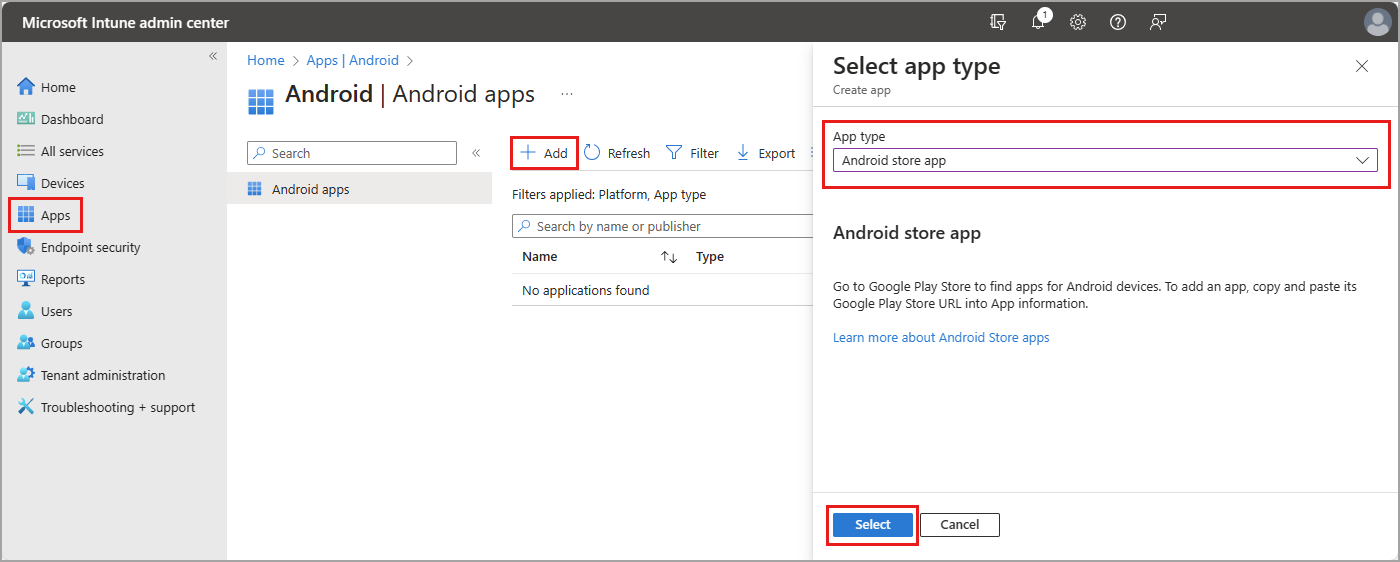
Provide a Name, Description, and Publisher.
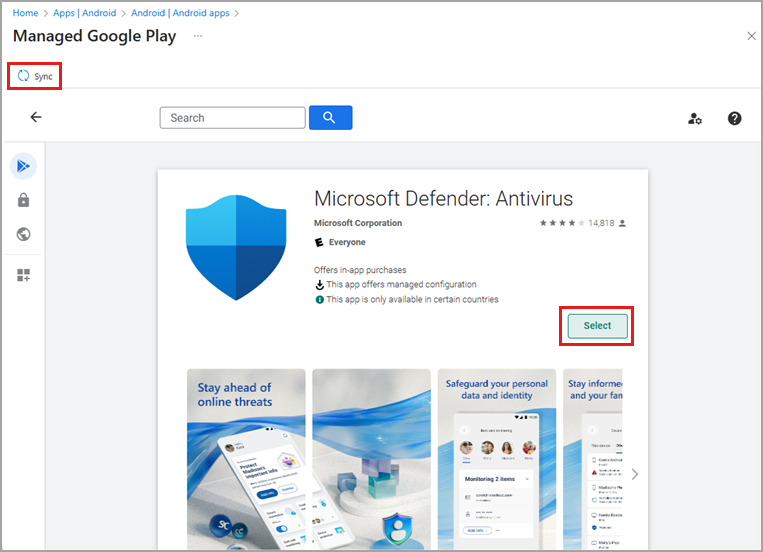
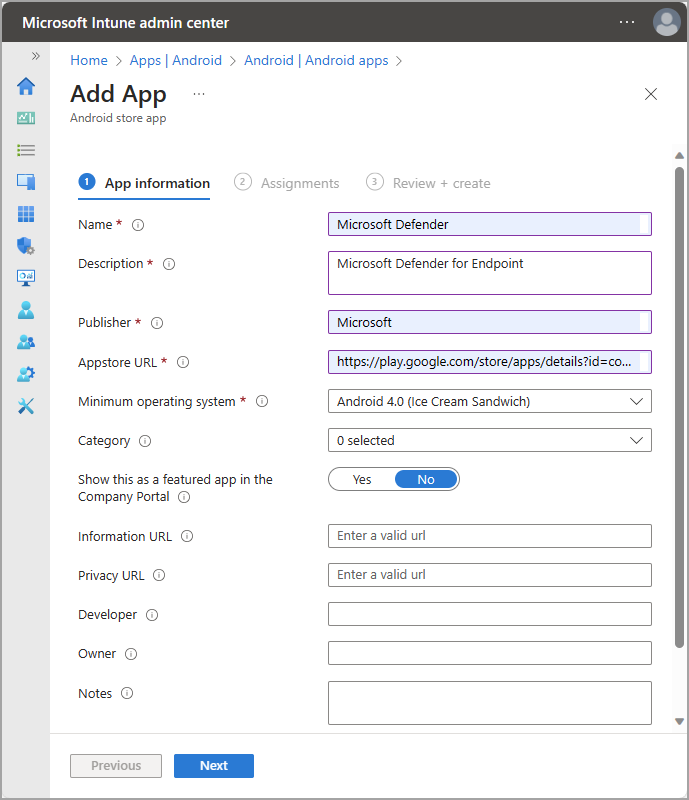
Enter the URL in the Appstore URL field.
https://play.google.com/store/apps/details?id=com.microsoft.scmx
Leave all other fields as their default values and select Next.
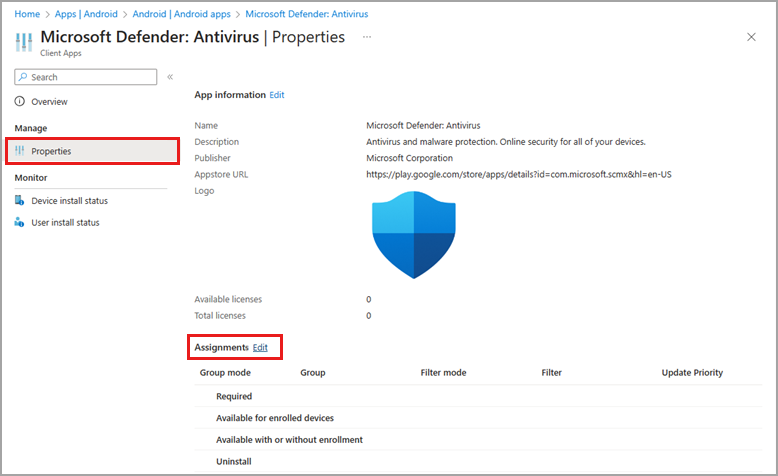
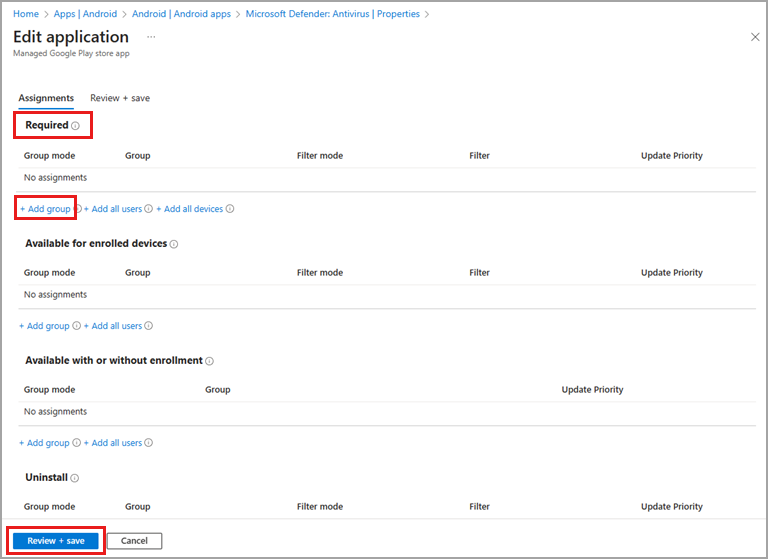
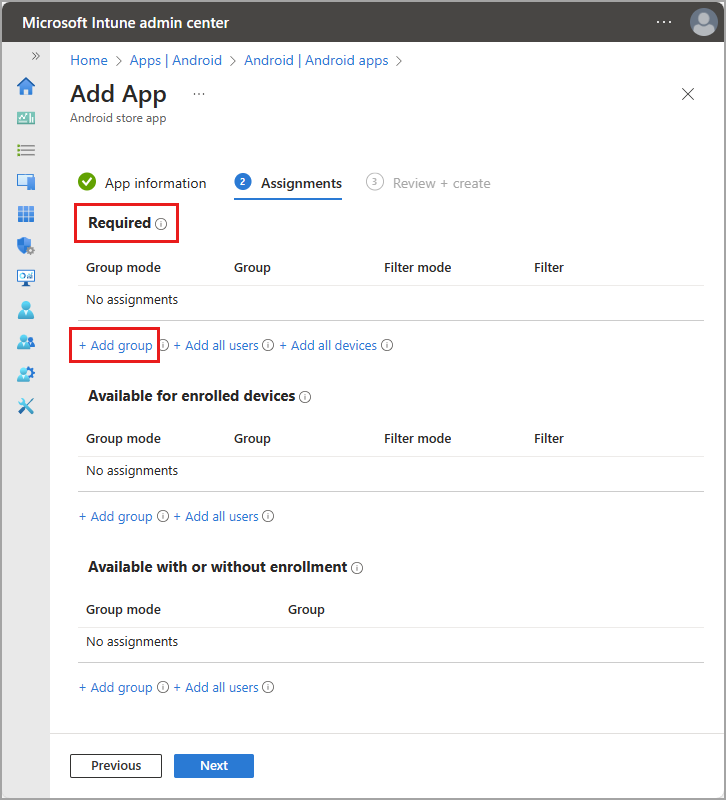
In the Required section, select Add group, then select the groups to assign the app to and select Next.
- The selected group should consist of your Intune enrolled users.
- You can edit or add more groups later.
On the Review + create tab, confirm the information is correct and select Create.
On the new app details page, select Device install status and confirm the app is installed.
Users need to enable the client in the Defender app. It's disabled by default. Proceed to the next section to confirm the app is installed and for how to enable the client.
Confirm Global Secure Access appears in Defender app
Because the Android client is integrated with Defender for Endpoint, it's helpful to understand the end user experience. The client appears in the Defender dashboard after onboarding to Global Secure Access. Onboarding happens by enabling a traffic forwarding profile.
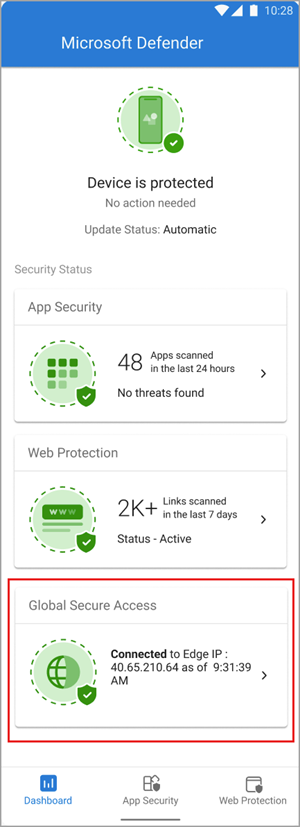
The client is disabled by default when it's deployed to user devices. Users need to enable the client from the Defender app. To enable the client, tap the toggle.
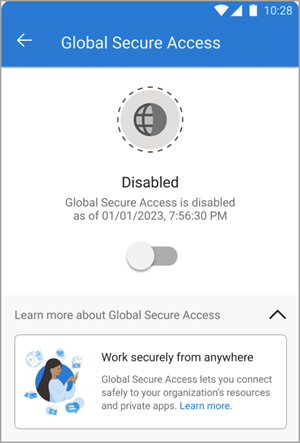
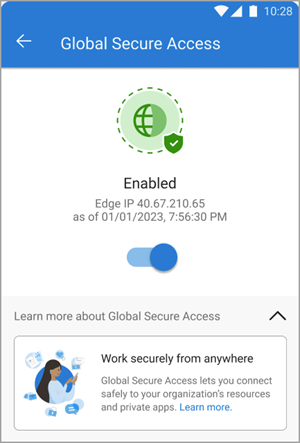
To view the details of the client, tap on the tile on the dashboard. When enabled and working properly, the client displays an "Enabled" message. The date and time for when the client connected to Global Secure Access also appears.
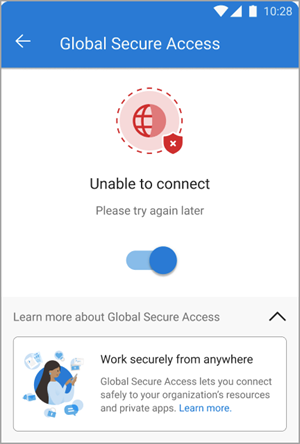
If the client is unable to connect, a toggle appears to disable the service. Users can come back later to try enabling the client.
Troubleshooting
The Global Secure Access tile doesn't appear after onboarding the tenant to the service. Restart the Defender app.
When attempting to access a Private Access application, the connection might time out after a successful interactive sign-in. Reloading the application through a web browser refresh should resolve the issue.
Related content
- About Microsoft Defender for Endpoint on Android
- Deploy Microsoft Defender for Endpoint on Android with Microsoft Intune
- Learn about managed Google Play apps and Android Enterprise devices with Intune
- Global Secure Access client for Microsoft Windows
- Global Secure Access client for macOS
- Global Secure Access client for iOS