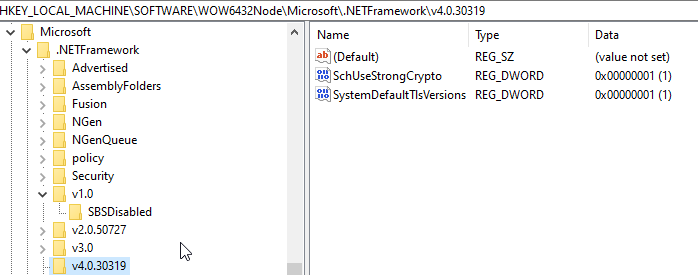
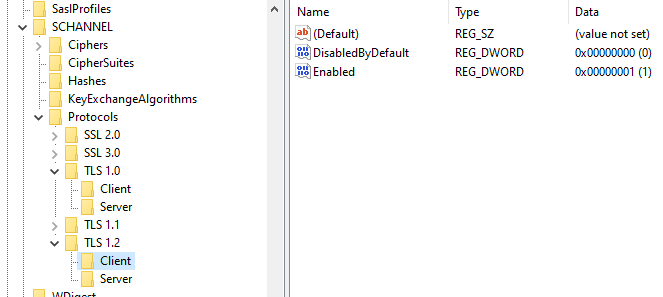
There is an issue with the Microsoft documentation on enabling TLS and other security protocols.
Older documentation shows setting via registry key needs a DWORD enabled = 1
later documentation shows the DWORD enabled = ffffffff
I have tested it recently and enabled =1 did not work it had to be ffffffff.
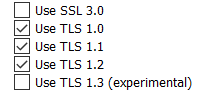
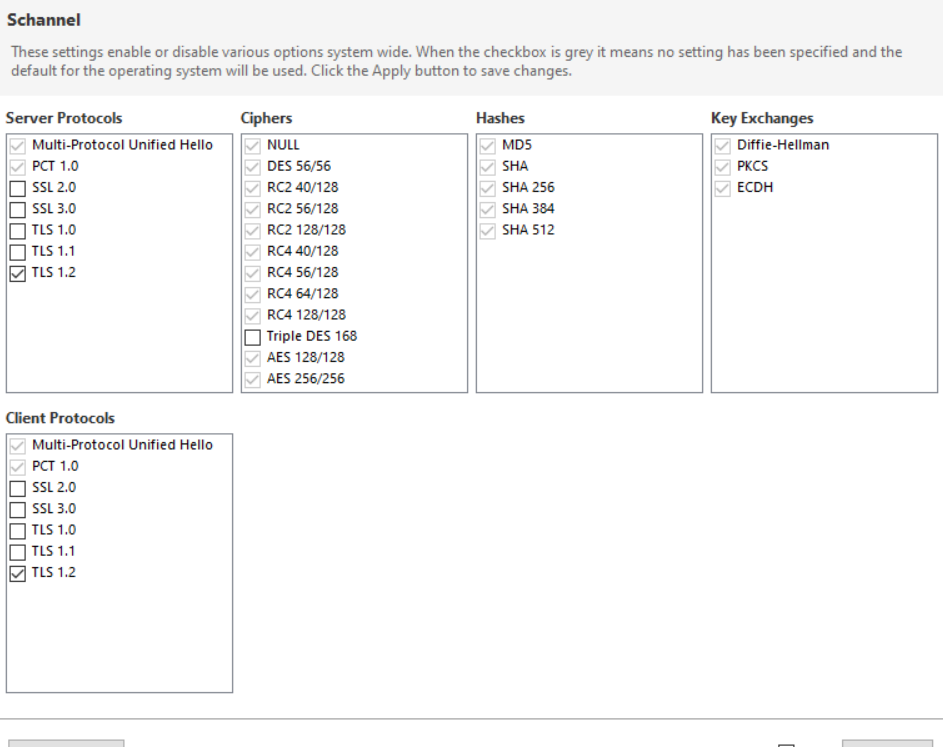
Nartac's IIS Crypto GUI app also sets ffffffff . Try using that app https://www.nartac.com/Products/IISCrypto/Download
to set your servers and clients to Best Practices and rebooting. See if that helps.
However, I am finding some articles online that show the errors can also be logged when a slow network response causes the client to fall back to a deprecated version of TLS before 1.2 despite TLS 1.2 being correctly enabled.
Note
By default, an OS that supports TLS 1.2 (for example, Windows 10) also supports legacy versions of the TLS protocol. When a connection is made by using TLS 1.2 and it doesn't get a timely response, or when the connection is reset, the OS might try to connect to the target web service by using an older TLS protocol (such as TLS 1.0 or 1.1). This usually occurs if the network is busy, or if a packet drops in the network. After the temporary fallback to the legacy TLS, the OS will try again to make a TLS 1.2 connection.
What will be the status of such fallback traffic after Microsoft stops supporting the legacy TLS? The OS might still try to make a TLS connection by using the legacy TLS protocol. But if the Microsoft service is no longer supporting the older TLS protocol, the legacy TLS-based connection won't succeed. This will force the OS to try the connection again by using TLS 1.2 instead.