How to configure Global Secure Access web content filtering
Web content filtering empowers you to implement granular Internet access controls for your organization based on website categorization.
Microsoft Entra Internet Access's first Secure Web Gateway (SWG) features include web content filtering based on domain names. Microsoft integrates granular filtering policies with Microsoft Entra ID and Microsoft Entra Conditional Access, which results in filtering policies that are user-aware, context-aware, and easy to manage.
The web filtering feature is currently limited to user- and context-aware Fully Qualified Domain Name (FQDN)-based web category filtering and FQDN filtering.
Prerequisites
Administrators who interact with Global Secure Access features must have one or more of the following role assignments depending on the tasks they're performing.
- The Global Secure Access Administrator role role to manage the Global Secure Access features.
- The Conditional Access Administrator to create and interact with Conditional Access policies.
Complete the Get started with Global Secure Access guide.
Install the Global Secure Access client on end user devices.
You must disable Domain Name System (DNS) over HTTPS (Secure DNS) to tunnel network traffic. Use the rules of the fully qualified domain names (FQDNs) in the traffic forwarding profile. For more information, see Configure the DNS client to support DoH.
Disable built-in DNS client on Chrome and Microsoft Edge.
IPv6 traffic isn't acquired by the client and is therefore transferred directly to the network. To enable all relevant traffic to be tunneled, set the network adapter properties to IPv4 preferred.
User Datagram Protocol (UDP) traffic (that is, QUIC) isn't supported in the current preview of Internet Access. Most websites support fallback to Transmission Control Protocol (TCP) when QUIC can't be established. For an improved user experience, you can deploy a Windows Firewall rule that blocks outbound UDP 443:
@New-NetFirewallRule -DisplayName "Block QUIC" -Direction Outbound -Action Block -Protocol UDP -RemotePort 443.Review web content filtering concepts. For more information, see web content filtering.
High level steps
There are several steps to configuring web content filtering. Take note of where you need to configure a Conditional Access policy.
- Enable internet traffic forwarding.
- Create a web content filtering policy.
- Create a security profile.
- Link the security profile to a Conditional Access policy.
- Assign users or groups to the traffic forwarding profile.
Enable internet traffic forwarding
The first step is to enable the Internet Access traffic forwarding profile. To learn more about the profile and how to enable it, see How to manage the Internet Access traffic forwarding profile.
Create a web content filtering policy
- Browse to Global Secure Access > Secure > web content filtering policy.
- Select Create policy.
- Enter a name and description for the policy and select Next.
- Select Add rule.
- Enter a name, select a web category or a valid FQDN, and then select Add.
- Valid FQDNs in this feature can also include wildcards using the asterisk symbol, *.
- Select Next to review the policy and then select Create policy.
Important
Changes to web content filtering can take up to one hour to deploy.
Create a security profile
Security profiles are a grouping of filtering policies. You can assign, or link, security profiles with Microsoft Entra Conditional Access policies. One security profile can contain multiple filtering policies. And one security profile can be associated with multiple Conditional Access policies.
In this step, you create a security profile to group filtering policies. Then you assign, or link, the security profiles with a Conditional Access policy to make them user or context aware.
Note
To learn more about Microsoft Entra Conditional Access policies, see Building a Conditional Access policy.
- Browse to Global Secure Access > Secure > Security profiles.
- Select Create profile.
- Enter a name and description for the policy and select Next.
- Select Link a policy and then select Existing policy.
- Select the web content filtering policy you already created and select Add.
- Select Next to review the security profile and associated policy.
- Select Create a profile.
- Select Refresh to refresh the profiles page and view the new profile.
Create and link Conditional Access policy
Create a Conditional Access policy for end users or groups and deliver your security profile through Conditional Access Session controls. Conditional Access is the delivery mechanism for user and context awareness for Internet Access policies. To learn more about session controls, see Conditional Access: Session.
- Browse to Identity > Protection > Conditional Access.
- Select Create new policy.
- Enter a name and assign a user or group.
- Select Target resources and All internet resources with Global Secure Access.
- Select Session > Use Global Secure Access security profile and choose a security profile.
- Select Select.
- In the Enable policy section, ensure On is selected.
- Select Create.
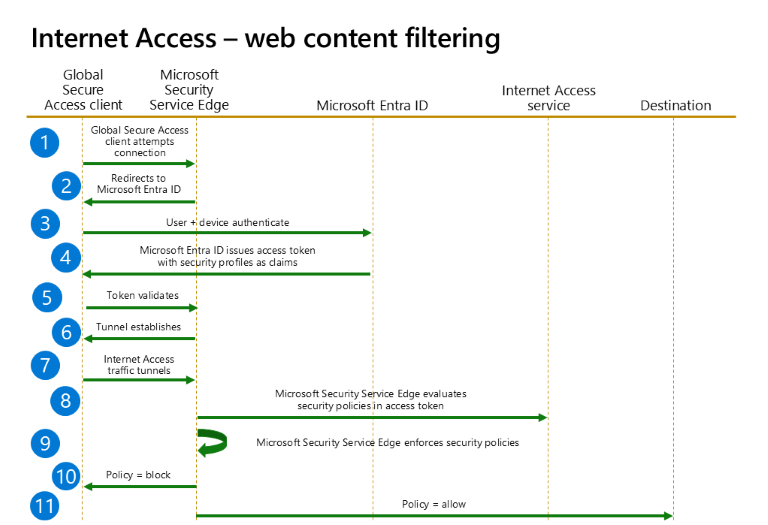
Internet Access flow diagram
This example demonstrates the flow of Microsoft Entra Internet Access traffic when you apply web content filtering policies.
The following flow diagram illustrates web content filtering policies blocking or allowing access to internet resources.
| Step | Description |
|---|---|
| 1 | The Global Secure Access client attempts to connect to Microsoft's Security Service Edge solution. |
| 2 | The client redirects to Microsoft Entra ID for authentication and authorization. |
| 3 | The user and device authenticate. Authentication happens seamlessly when the user has a valid Primary Refresh Token (PRT). |
| 4 | After the user and device authenticate, Conditional Access matches on Internet Access Conditional Access rules and adds applicable security profiles to the token. It enforces applicable authorization policies. |
| 5 | Microsoft Entra ID presents the token to Microsoft Security Service Edge for validation. |
| 6 | The tunnel establishes between the Global Secure Access client and Microsoft Security Service Edge. |
| 7 | Traffic starts being acquired and tunnels through the Internet Access tunnel. |
| 8 | Microsoft Security Service Edge evaluates the security policies in the access token in priority order. After it matches on a web content filtering rule, web content filtering policy evaluation stops. |
| 9 | Microsoft Security Service Edge enforces the security policies. |
| 10 | Policy = block results in an error for HTTP traffic or a connection reset exception occurs for HTTPS traffic. |
| 11 | Policy = allow results in traffic forwarding to the destination. |
Note
Applying a new security profile can take up to 60-90 minutes due to security profile enforcement with access tokens. The user must receive a new access token with the new security profile ID as a claim before it takes effect. Changes to existing security profiles start being enforced much more quickly.
User and group assignments
You can scope the Internet Access profile to specific users and groups. To learn more about user and group assignment, see How to assign and manage users and groups with traffic forwarding profiles.
Verify end user policy enforcement
When traffic reaches Microsoft's Secure Service Edge, Microsoft Entra Internet Access performs security controls in two ways. For unencrypted HTTP traffic, it uses the Uniform Resource Locator (URL). For HTTPS traffic encrypted with Transport Layer Security (TLS), it uses the Server Name Indication (SNI).
Use a Windows device with the Global Secure Access client installed. Sign in as a user that is assigned the Internet traffic acquisition profile. Test that navigating to websites is allowed or restricted as expected.
Right-click on the Global Secure Access client icon in the task manager tray and open Advanced Diagnostics > Forwarding profile. Ensure that the Internet access acquisition rules are present. Also, check if the hostname acquisition and flows for the users Internet traffic are being acquired while browsing.
Navigate to allowed and blocked sites and check if they behave properly. Browse to Global Secure Access > Monitor > Traffic logs to confirm traffic is blocked or allowed appropriately.
The current blocking experience for all browsers includes a plaintext browser error for HTTP traffic and a "Connection Reset" browser error for HTTPS traffic.
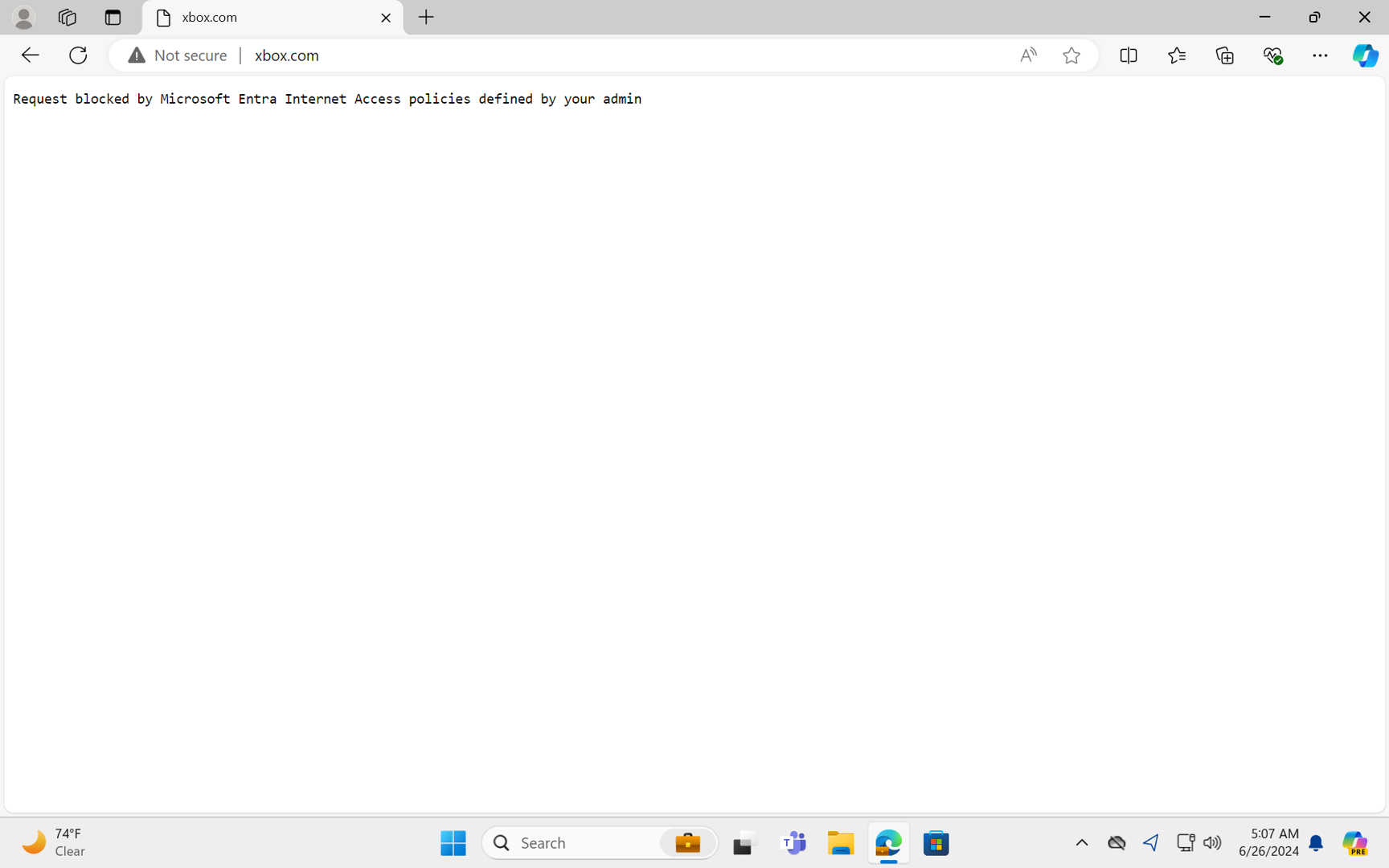
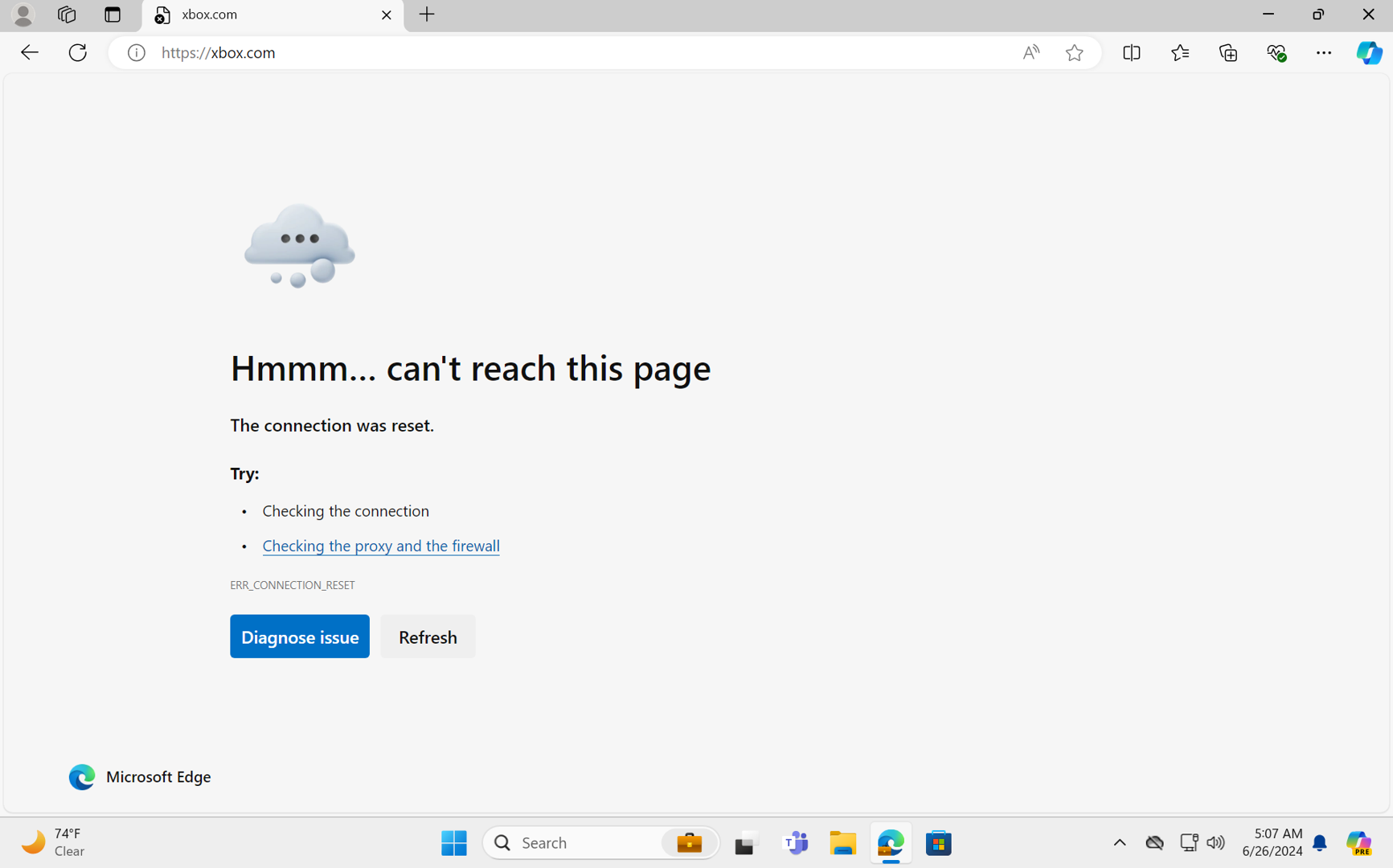
Note
Configuration changes in the Global Secure Access experience related to web content filtering typically take effect in less than 5 minutes. Configuration changes in Conditional Access related to web content filtering take effect in approximately one hour.