Global Secure Access client for Microsoft Windows
The Global Secure Access client, an essential component of Global Secure Access, helps organizations manage and secure network traffic on end-user devices. The client's main role is to route traffic that needs to be secured by Global Secure Access to the cloud service. All other traffic goes directly to the network. The Forwarding Profiles, configured in the portal, determine which traffic the Global Secure Access client routes to the cloud service.
Note
The Global Secure Access Client is also available for macOS, Android, and iOS. To learn how to install the Global Secure Access client on these platforms, see Global Secure Access client for macOS, Global Secure Access client for Android, and Global Secure Access client for iOS.
This article describes how to download and install the Global Secure Access client for Windows.
Prerequisites
- A Microsoft Entra tenant onboarded to Global Secure Access.
- A managed device joined to the onboarded tenant. The device must be either Microsoft Entra joined or Microsoft Entra hybrid joined.
- Microsoft Entra registered devices aren't supported.
- The Global Secure Access client requires a 64-bit version of Windows 10 or Windows 11.
- Azure Virtual Desktop single-session is supported.
- Azure Virtual Desktop multi-session isn't supported.
- Windows 365 is supported.
- Local administrator credentials are required to install or upgrade the client.
- The Global Secure Access client requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
Download the client
The most current version of the Global Secure Access client is available to download from the Microsoft Entra admin center.
- Sign in to the Microsoft Entra admin center as a Global Secure Access Administrator.
- Browse to Global Secure Access > Connect > Client download.
- Select Download Client.
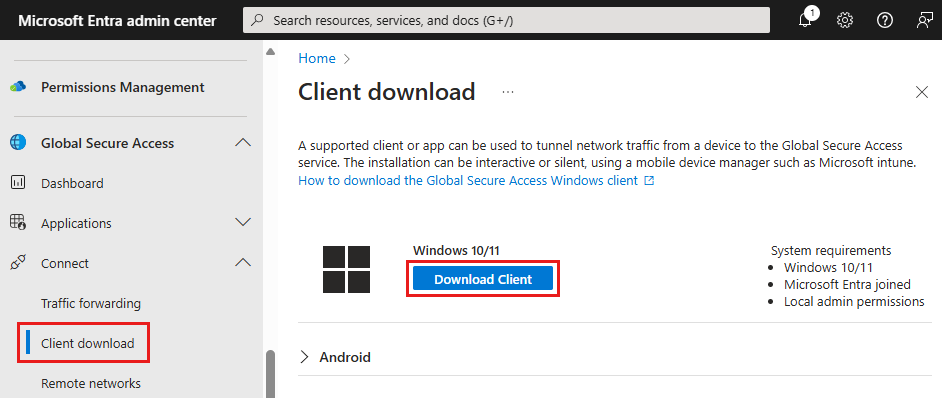
Install the Global Secure Access client
Automated installation
Organizations can install the Global Secure Access client silently with the /quiet switch, or use Mobile Device Management (MDM) solutions, such as Microsoft Intune to deploy the client to their devices.
Deploy Global Secure Access client with Intune
In this section, you learn how to manually install the Global Secure Access client on a Windows 11 client device with Intune.
Prerequisites
- A security group with devices or users to identify where to install the Global Secure Access client
Package the client
Convert the .exe file to a .intunewin file.
Download the Global Secure Access client from the Microsoft Entra admin center > Global Secure Access > Connect > Client download. Select Download client under Windows 11.
Go to Microsoft Win32 Content Prep Tool. Select IntuneWinAppUtil.exe.
In the top right corner, select the three dot menu. Select Download.

Navigate to and run
IntuneWinAppUtil.exe. A command prompt opens.Enter the folder path location of the Global Secure Access
.exefile. Select Enter.Enter the name of the Global Secure Access
.exefile. Select Enter.Enter the folder path in which to place the
.intunewinfile. Select Enter.Enter N. Select Enter.

The .intunewin file is ready for you to deploy Microsoft Intune.
Deploy Global Secure Access client with Intune
Reference detailed guidance to Add and assign Win32 apps to Microsoft Intune.
Navigate to https://intune.microsoft.com.
Select Apps > All apps > Add.
On Select app type, under Other app types, select Windows app (Win32).
Select Select. The Add app steps appear.
Select Select app package file.
Select the folder icon. Open the
.intunewinfile you created in the previous section.
Select OK.
Configure these fields:
- Name: Enter a name for the client app.
- Description: Enter a description.
- Publisher: Enter Microsoft.
- App Version (optional): Enter the client version.
You can use the default values in the remaining fields. Select Next.

Configure these fields:
- Install command: Use the original name of the
.exefile for"OriginalNameOfFile.exe" /install /quiet /norestart. - Uninstall command: Use the original name of the
.exefile for"OriginalNameOfFile.exe" /uninstall /quiet /norestart. - Allow available uninstall: Select No.
- Install behavior: Select System.
- Device restart behavior: Select Determine behavior based on return codes.
- Install command: Use the original name of the
| Return code | Code type |
|---|---|
| 0 | Success |
| 1707 | Success |
| 3010 | Success |
| 1641 | Success |
| 1618 | Retry |
Note
The Return codes populate with default Windows exit codes. In this case, we changed two of the code types to Success to avoid unnecessary device reboots.

Select Next.
Configure these fields:
- Operating system architecture: Select your minimum requirements.
- Minimum operating system: Select your minimum requirements.

Leave the remaining fields blank. Select Next.
Under Rules format, select Manually configure detection rules.
Select Add.
Under Rule type, select File.
Configure these fields:
- Path: Enter
C:\Program Files\Global Secure Access Client\TrayApp. - File or folder: Enter
GlobalSecureAccessClient.exe. - Detection method: Select String (version).
- Operator: Select Greater than or equal to.
- Value: Enter the client version number.
- Associated with a 32-bit app on 64-bit client: Select No.

- Path: Enter
Select OK. Select Next.
Select Next two more times to get to Assignments.
Under Required, select +Add group. Select a group of users or devices. Select Select.
Select Next. Select Create.
Update the client to a newer version
To update to the newest client version, follow the Update a line-of-business app steps. Be sure to update the following settings in addition to uploading the new .intunewin file:
- Client version
- Install and uninstall commands
- Detection rule value set to the new client version number
In a production environment, it's best practice to deploy new client versions in a phased deployment approach:
- Leave the existing app in place for now.
- Add a new app for the new client version, repeating the previous steps.
- Assign the new app to a small group of users to pilot the new client version. It's okay to assign these users to the app with the old client version for an in-place upgrade.
- Slowly increase the membership of the pilot group until you deploy the new client to all desired devices.
- Delete the app with the old client version.
Manual installation
To manually install the Global Secure Access client:
- Run the GlobalSecureAccessClient.exe setup file. Accept the software license terms.
- The client installs and silently signs you in with your Microsoft Entra credentials. If the silent sign-in fails, the installer prompts you to sign in manually.
- Sign in. The connection icon turns green.
- Hover over the connection icon to open the client status notification, which should show as Connected.
Client actions
To view the available client menu actions, right-click the Global Secure Access system tray icon.
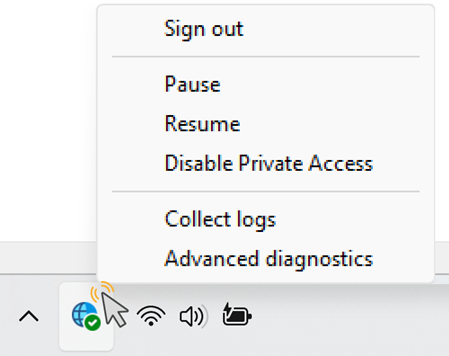
Tip
The Global Secure Access client menu actions will vary according to your Client registry keys configuration.
| Action | Description |
|---|---|
| Sign out | Hidden by default. Use the Sign out action when you need to sign in to the Global Secure Access client with a Microsoft Entra user other than the one used to sign in to Windows. To make this action available, update the appropriate Client registry keys. |
| Disable | Select the Disable action to disable the client. The client remains disabled until you either enable the client or restart the machine. |
| Enable | Enables the Global Secure Access client. |
| Disable Private Access | Hidden by default. Use the Disable Private Access action when you wish to bypass Global Secure Access whenever you connect your device directly to the corporate network to access private applications directly through the network rather than through Global Secure Access. To make this action available, update the appropriate Client registry keys. |
| Collect logs | Select this action to collect client logs (information about the client machine, the related event logs for the services, and registry values) and archive them in a zip file to share with Microsoft Support for investigation. The default location for the logs is C:\Program Files\Global Secure Access Client\Logs. You can also collect client logs on Windows by entering the following command in the Command Prompt: C:\Program Files\Global Secure Access Client\LogsCollector\LogsCollector.exe" <username> <user>. |
| Advanced diagnostics | Select this action to launch the Advanced diagnostics utility and access an assortment of troubleshooting tools. |
Client status indicators
Status notification
Double-click the Global Secure Access icon to open the client status notification and view the status of each channel configured for the client.
Client statuses in system tray icon
| Icon | Message | Description |
|---|---|---|
| Global Secure Access | The client is initializing and checking its connection to Global Secure Access. | |
| Global Secure Access - Connected | The client is connected to Global Secure Access. | |
| Global Secure Access - Disabled | The client is disabled because services are offline or the user disabled the client. | |
| Global Secure Access - Disconnected | The client failed to connect to Global Secure Access. | |
| Global Secure Access - Some channels are unreachable | The client is partially connected to Global Secure Access (that is, the connection to at least one channel failed: Microsoft Entra, Microsoft 365, Private Access, Internet Access). | |
| Global Secure Access - Disabled by your organization | Your organization disabled the client (that is, all traffic forwarding profiles are disabled). | |
| Global Secure Access - Private Access is disabled | The user disabled Private Access on this device. | |
| Global Secure Access - could not connect to the Internet | The client couldn't detect an internet connection. The device is either connected to a network that doesn't have an Internet connection or a network that requires captive portal sign in. |
Known limitations
This feature has one or more known limitations. For more detailed information about the known issues and limitations of this feature, see Known Limitations for Global Secure Access.
Troubleshooting
To troubleshoot the Global Secure Access client, right-click the client icon in the taskbar and select one of the troubleshooting options: Collect logs or Advanced diagnostics.
Tip
Administrators can modify the Global Secure Access client menu options by revising the Client registry keys.
For more detailed information on troubleshooting the Global Secure Access client, see the following articles:
- Troubleshoot the Global Secure Access client: advanced diagnostics
- Troubleshoot the Global Secure Access client: Health check tab
Client registry keys
The Global Secure Access client uses specific registry keys to enable or disable different functionalities. Administrators can use a Mobile Device Management (MDM) solutions, such as Microsoft Intune or Group Policy to control the registry values.
Caution
Don't change other registry values unless instructed by Microsoft Support.
Restrict nonprivileged users
The administrator can prevent nonprivileged users on the Windows device from disabling or enabling the client by setting the following registry key:
Computer\HKEY_LOCAL_MACHINE\Software\Microsoft\Global Secure Access Client
RestrictNonPrivilegedUsers REG_DWORD
| Data | Description |
|---|---|
| 0x0 | Nonprivileged users on the Windows device can disable and enable the client. |
| 0x1 | Nonprivileged users on the Windows device are restricted from disabling and enabling the client. A UAC prompt requires local administrator credentials for disable and enable options. The administrator can also hide the disable button (see Hide or unhide system tray menu buttons). |
Disable or enable Private Access on the client
This registry value controls whether Private Access is enabled or disabled for the client. If a user is connected to the corporate network, they can choose to bypass Global Secure Access and directly access private applications.
Users can disable and enable Private Access through the system tray menu.
Tip
This option is available on the menu only if it isn't hidden (see Hide or unhide system tray menu buttons) and Private Access is enabled for this tenant.
Administrators can disable or enable Private Access for the user by setting the registry key:
Computer\HKEY_CURRENT_USER\Software\Microsoft\Global Secure Access Client
| Value | Type | Data | Description |
|---|---|---|---|
| IsPrivateAccessDisabledByUser | REG_DWORD | 0x0 | Private Access is enabled on this device. Network traffic to private applications goes through Global Secure Access. |
| IsPrivateAccessDisabledByUser | REG_DWORD | 0x1 | Private Access is disabled on this device. Network traffic to private applications goes directly to the network. |
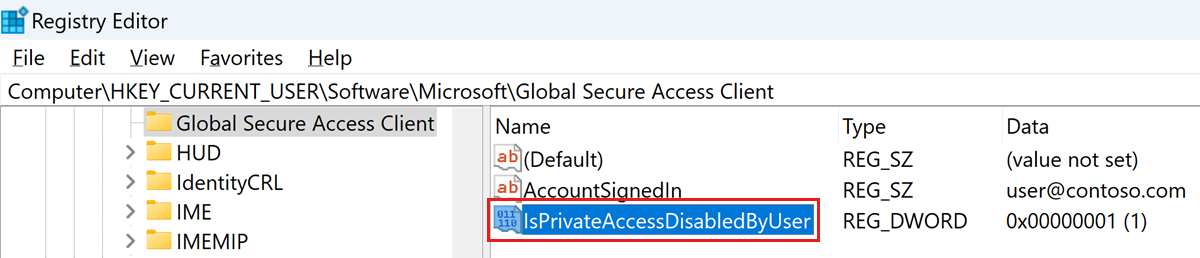
If the registry value doesn't exist, the default value is 0x0, Private Access is enabled.
Hide or unhide system tray menu buttons
The administrator can show or hide specific buttons in the client system tray icon menu. Create the values under the following registry key:
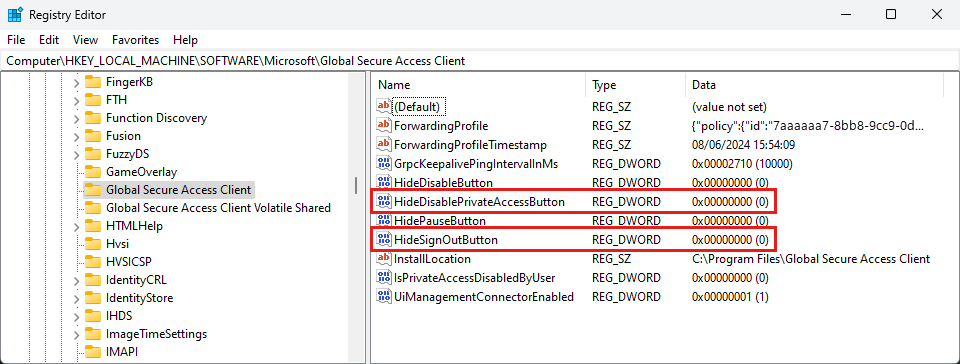
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Global Secure Access Client
| Value | Type | Data | Default behavior | Description |
|---|---|---|---|---|
| HideSignOutButton | REG_DWORD | 0x0 - shown 0x1 - hidden | hidden | Configure this setting to show or hide the Sign out action. This option is for specific scenarios when a user needs to sign in to the client with a different Microsoft Entra user than the one used to sign in to Windows. Note: You must sign in to the client with a user in the same Microsoft Entra tenant to which the device is joined. You can also use the Sign out action to reauthenticate the existing user. |
| HideDisablePrivateAccessButton | REG_DWORD | 0x0 - shown 0x1 - hidden | hidden | Configure this setting to show or hide the Disable Private Access action. This option is for a scenario when the device is directly connected to the corporate network and the user prefers accessing private applications directly through the network instead of through the Global Secure Access. |
| HideDisableButton | REG_DWORD | 0x0 - shown 0x1 - hidden | shown | Configure this setting to show or hide the Disable action. When visible, the user can disable the Global Secure Access client. The client remains disabled until the user enables it again. If the Disable action is hidden, a nonprivileged user can't disable the client. |
For more information, see Guidance for configuring IPv6 in Windows for advanced users.
