Get started with the data loss prevention alerts
Your Microsoft Purview Data Loss Prevention (DLP) policies can be configured to generate alerts when the conditions in a policy are matched.
For a brief overview of alerts see:
This article includes the licensing and permission details and other crucial information you need as you work with alerts.
DLP alerts can be investigated and managed in the Microsoft Defender XDR dashboard and in the Microsoft Purview compliance portal. The Microsoft Defender XDR dashboard is the recommended location for investigating and managing DLP alerts. The Microsoft Purview compliance portal is the recommended location for creating and editing DLP policies.
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Alert types
Alerts can be sent every time an activity matches a rule, which can be noisy or they can be aggregated based on number of matches or volume of items over a set period of time. There are two types of alerts that can be configured in DLP policies.
Single-event alerts are typically used in policies that monitor for highly sensitive events that occur in a low volume, like a single email with 10 or more customer credit card numbers being sent outside your organization.
Aggregate-event alerts are typically used in policies that monitor for events that occur in a higher volume over a period of time. For example, an aggregate alert can be triggered when 10 individual emails each with one customer credit card number is sent outside your org over 48 hours.
Before you begin
Before you begin, make sure you have the necessary prerequisites:
Licensing for alert configuration options
- Single-event alert configuration: Organizations that have an E1, F1, or G1 subscription or an E3 or G3 subscription can configure policies to generate an alert for every time a triggering activity occurs.
- Aggregated alert configuration: To configure aggregate alert policies based on a threshold, you must have either of the following configurations:
- An A5 subscription
- An E5 or G5 subscription
- An E1, F1, or G1 subscription or an E3 or G3 subscription that includes one of the following features:
- Office 365 Advanced Threat Protection Plan 2
- Microsoft 365 E5 Compliance
- Microsoft 365 eDiscovery and Audit add-on license
Customers who use Endpoint DLP and who are eligible for Teams DLP will see their endpoint DLP policy alerts and Teams DLP policy alerts in the DLP alert management dashboard.
Roles and Role Groups
If you want to view the DLP alert management dashboard or to edit the alert configuration options in a DLP policy, you must be a member of one of these role groups:
- Compliance Administrator
- Compliance Data Administrator
- Security Administrator
- Security Operator
- Security Reader
- Information Protection Admin
- Information Protection Analyst
- Information Protection Investigator
- Information Protection Reader
To learn more about them, see Permissions in the Microsoft Purview compliance portal
Here's a list of applicable role groups. To learn more about them, see Permissions in the Microsoft Purview compliance portal.
- Information Protection
- Information Protection Admins
- Information Protection Analysts
- Information Protection Investigators
- Information Protection Readers
To access the DLP alert management dashboard, you need the Manage alerts role and either of these two roles:
- DLP Compliance Management
- View-Only DLP Compliance Management
To access the Content preview feature and the Matched sensitive content and context features, you must be a member of the Content Explorer Content Viewer role group, which has the Data classification content viewer role preassigned.
Tip
If the admin requires access to alerts but not contextual/sensitive information, you can create and assign a custom role that does not include Data Classification Content Viewer permission.
DLP alert configuration
To learn how to configure an alert in your DLP policy, see Create and Deploy data loss prevention policies. There are different alert configuration experiences depending on your licensing.
Note
It may take up to 3 hours to generate alerts after you configure or modify existing alerts in a DLP policy.
Aggregate event alert configuration
If you're licensed for aggregated alert configuration options, then you'll see these options when you create or edit a DLP policy.
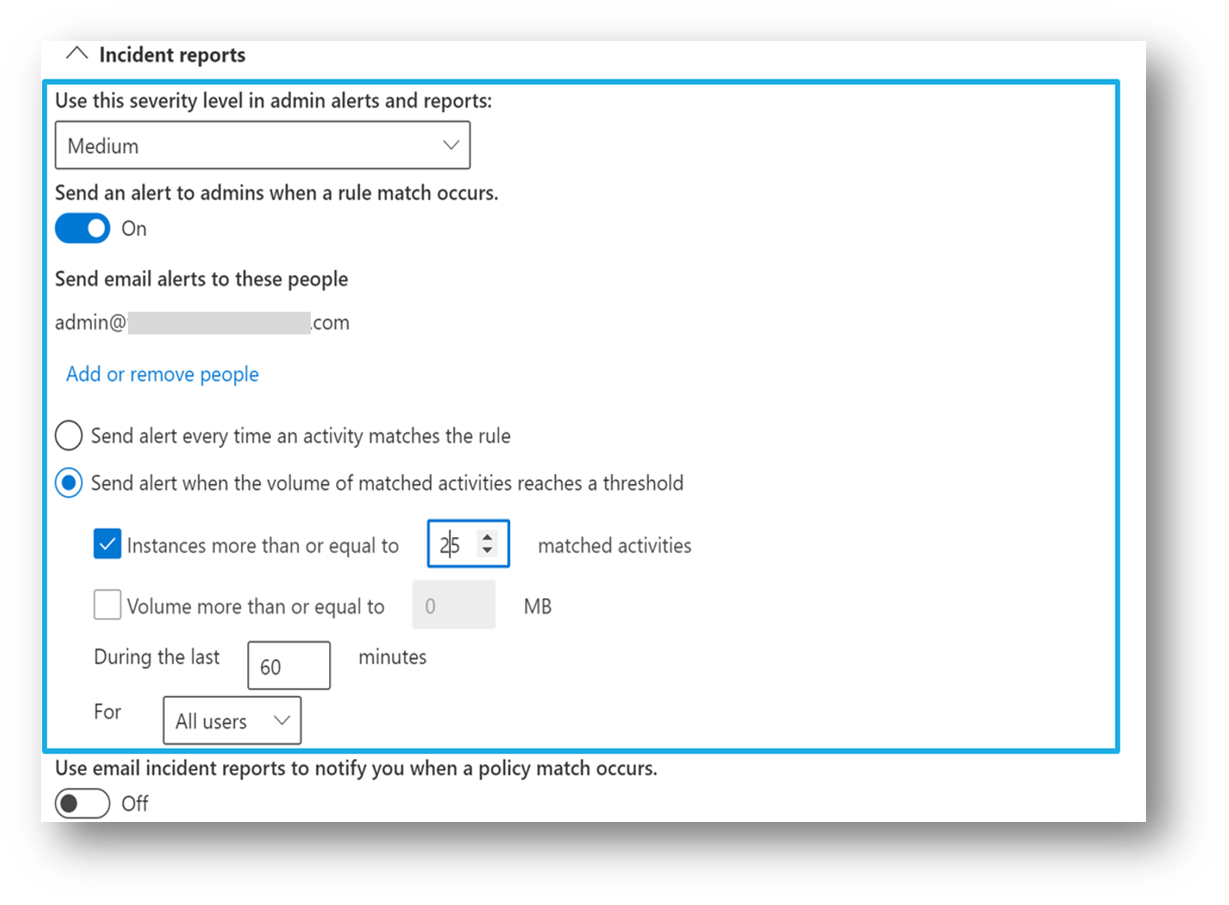
This configuration allows you to set up a policy to generate an alert:
- every time an activity matches the policy conditions
- when the defined threshold is met or exceeded
- based on the number of activities
- based on the volume of exfiltrated data
To prevent a flood of notification emails, all matches that occur within a one-minute time window that are for the same DLP rule and on the same location are grouped together in the same alert. The one-minute aggregation time window feature is available in:
- An E5 or G5 subscription
- An E1, F1, or G1 subscription or an E3 or G3 subscription that includes one of the following features:
- Office 365 Advanced Threat Protection Plan 2
- Microsoft 365 E5 Compliance
- Microsoft 365 eDiscovery and Audit add-on license
For organizations that have an E1, F1, or G1 subscription or an E3 or G3 subscription, the aggregation time window is 15 minutes.
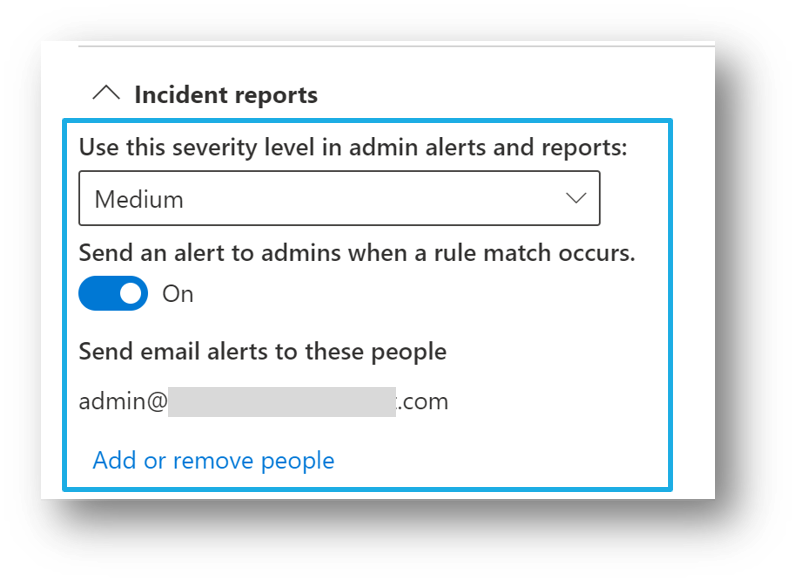
Single event alert configuration
If you're licensed for single-event alert configuration options, then you'll see these options when you create or edit a DLP policy. Use this option to create an alert that's raised every time a DLP rule match happens.
Types of events
Here are some of the events associated with an alert. In the Alert dashboard, you can choose a particular event to view its details.
Event details
| Property name | Description | Event types |
|---|---|---|
| ID | unique ID associated with the event | all events |
| Location | workload where the event was detected | all events |
| time of activity | time of the user activity that matched the criteria of the DLP policy |
Affected entities
| Property name | Description | Event types |
|---|---|---|
| user | user who took the action that caused the policy match | all events |
| hostname | host name of the computer where the DLP policy match occurred | device events |
| IP address | IP address of the computer where the DLP policy match occurred | device events |
| sha1 | SHA-1 hash of the file | device events |
| sha256 | SHA-256 hash of the file | device events |
| MDATP device ID | endpoint device MDATP ID | |
| file size | size of the file | SharePoint, OneDrive, and device events |
| file path | the absolute path of the item involved with the DLP policy match | SharePoint, OneDrive, and devices events |
| email recipients | if an email was the sensitive item that matched the DLP policy, this field includes the recipients of that email | Exchange events |
| email subject | subject of the email that matched the DLP policy | Exchange events |
| email attachments | names of the attachments in the email that matched the DLP policy | Exchange events |
| site owner | name of the site owner | SharePoint and OneDrive events |
| site URL | full of the URL of the SharePoint or OneDrive site where the DLP policy match occurred | SharePoint and OneDrive events |
| file created | time of creation of the file that matched the DLP policy | SharePoint and OneDrive events |
| file last modified | the last time that the file that matched the DLP policy was changed | SharePoint and OneDrive events |
| file size | size of the file that matched the DLP policy | SharePoint and OneDrive events |
| file owner | owner of the file that matched the DLP policy | SharePoint and OneDrive events |
Policy details
| Property name | Description | Event types |
|---|---|---|
| DLP policy matched | name of the matched DLP policy | all events |
| rule matched | name of the matched DLP policy rule | all events |
| sensitive information types (SIT) detected | SITs that were detected as part of the DLP policy match | all events |
| actions taken | actions that were taken that caused the DLP policy match | all events |
| violating action | action on the endpoint device that raised the DLP alert | device events |
| user overrode policy | did the user override the policy via a policy tip | all events |
| use override justification | the text of the reason provided by the user for the override | all events |
Important
Your organization's audit log retention policy configuration controls for how long an alert remains visible in the console. For more information, see Manage audit log retention policies.
See also
- Alerts in DLP policies: Describes alerts in the context of a DLP policy.
- Get started with data loss prevention alerts: Covers the necessary liscensing, permissions, and prerequisites for DLP alerts and alert reference details.
- Create and deploy data loss prevention policies: Includes guidance on alert configuration in the context of creating a DLP policy.
- Learn about investigating data loss prevention alerts: Covers the various methods for investigating of DLP alerts.
- Investigate data loss incidents with Microsoft Defender XDR: How to investigate DLP alerts in Microsoft Defender portal.