Provision Microsoft Entra ID to Active Directory - Configuration
The following document will guide you through configuring Microsoft Entra Cloud Sync for provisioning from Microsoft Entra ID to Active Directory. If you are looking for information on provisioning from AD to Microsoft Entra ID, see Configure - Provisioning Active Directory to Microsoft Entra ID using Microsoft Entra Cloud Sync
Important
The public preview of Group Writeback v2 in Microsoft Entra Connect Sync is no longer available as of June 30, 2024. This feature was discontinued on this date, and you're no longer supported in Microsoft Entra Connect Sync to provision cloud security groups to Active Directory. The feature continues to operate beyond the discontinuation date; however, it no longer receives support and might cease functioning at any time without notice.
We offer similar functionality in Microsoft Entra Cloud Sync called Group Provision to Active Directory that you can use instead of Group Writeback v2 for provisioning cloud security groups to Active Directory. We're working on enhancing this functionality in Microsoft Entra Cloud Sync along with other new features that we're developing in Microsoft Entra Cloud Sync.
Customers who use this preview feature in Microsoft Entra Connect Sync should switch their configuration from Microsoft Entra Connect Sync to Microsoft Entra Cloud Sync. You can choose to move all your hybrid sync to Microsoft Entra Cloud Sync (if it supports your needs). You can also run Microsoft Entra Cloud Sync side by side and move only cloud security group provisioning to Active Directory onto Microsoft Entra Cloud Sync.
For customers who provision Microsoft 365 groups to Active Directory, you can keep using Group Writeback v1 for this capability.
You can evaluate moving exclusively to Microsoft Entra Cloud Sync by using the user synchronization wizard.
Configure provisioning
To configure provisioning, follow these steps.
Sign in to the Microsoft Entra admin center as at least a hybrid identity administrator.
Browse to Identity > Hybrid management > Microsoft Entra Connect > Cloud Sync.
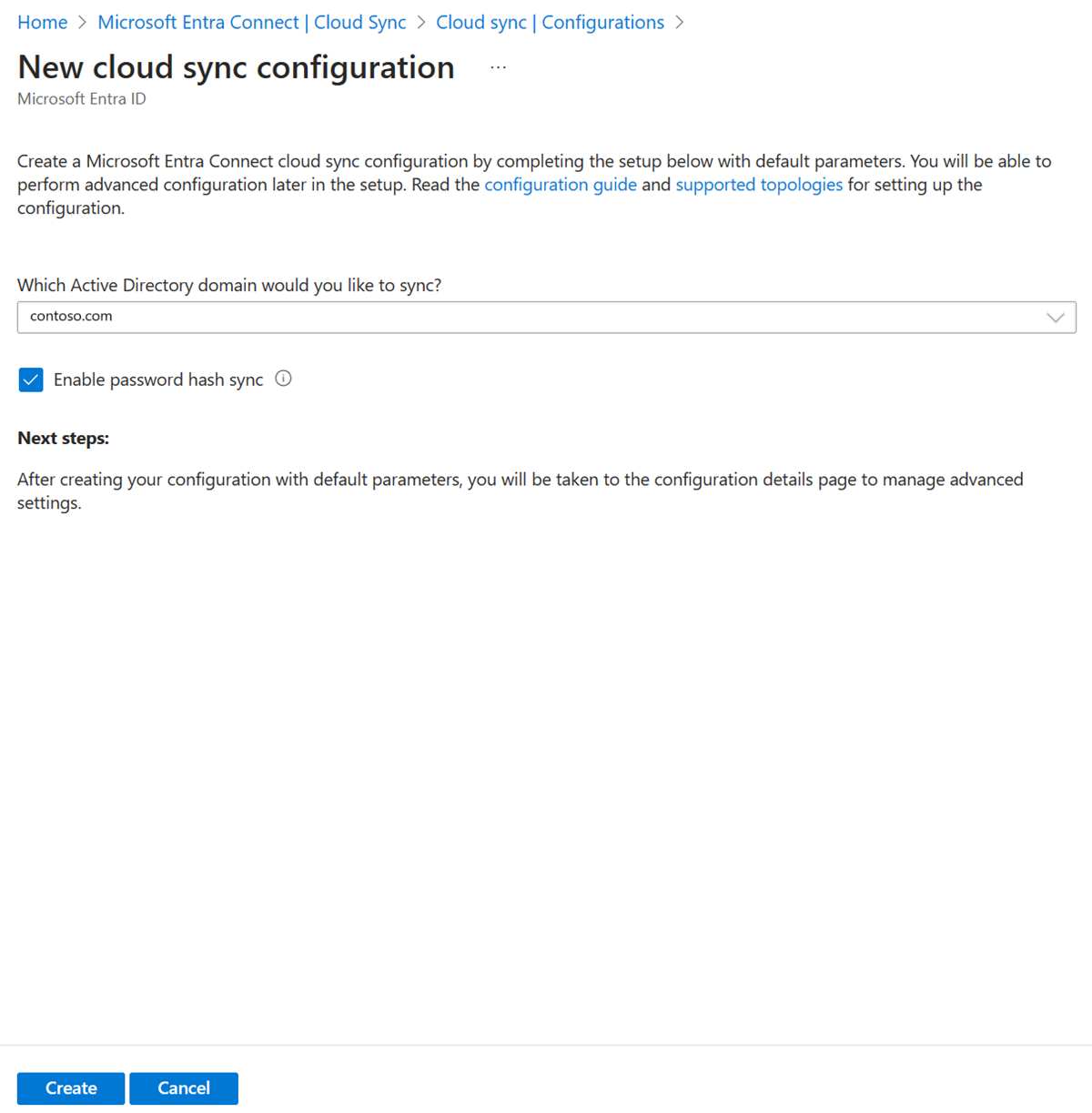
- Select New configuration.
- Select Microsoft Entra ID to AD sync.
- On the configuration screen, select your domain and whether to enable password hash sync. Click Create.
- The Get started screen will open. From here, you can continue configuring cloud sync.
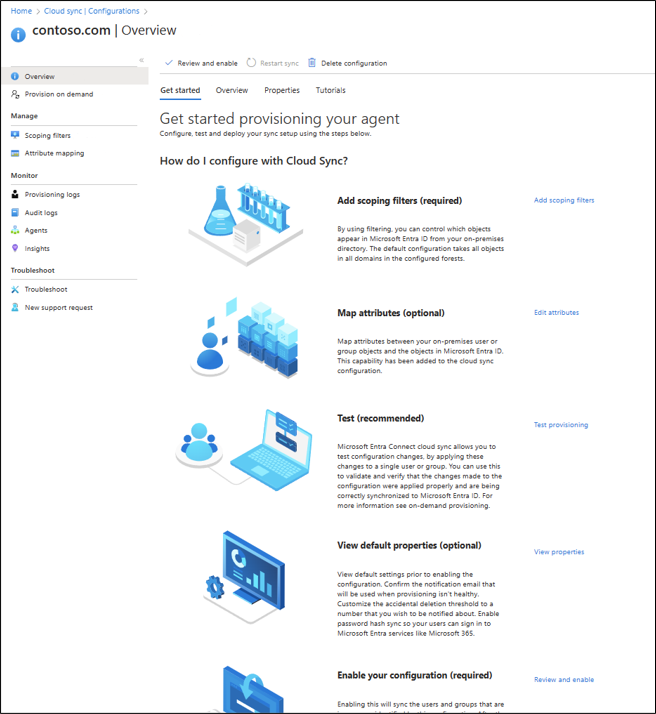
- The configuration is split in to the following 5 sections.
| Section | Description |
|---|---|
| 1. Add scoping filters | Use this section to define what objects appear in Microsoft Entra ID |
| 2. Map attributes | Use this section to map attributes between your on-premises users/groups with Microsoft Entra objects |
| 3. Test | Test your configuration before deploying it |
| 4. View default properties | View the default setting prior to enabling them and make changes where appropriate |
| 5. Enable your configuration | Once ready, enable the configuration and users/groups will begin synchronizing |
Scope provisioning to specific groups
You can scope the agent to synchronize all or specific security groups. You can configure groups and organizational units within a configuration.
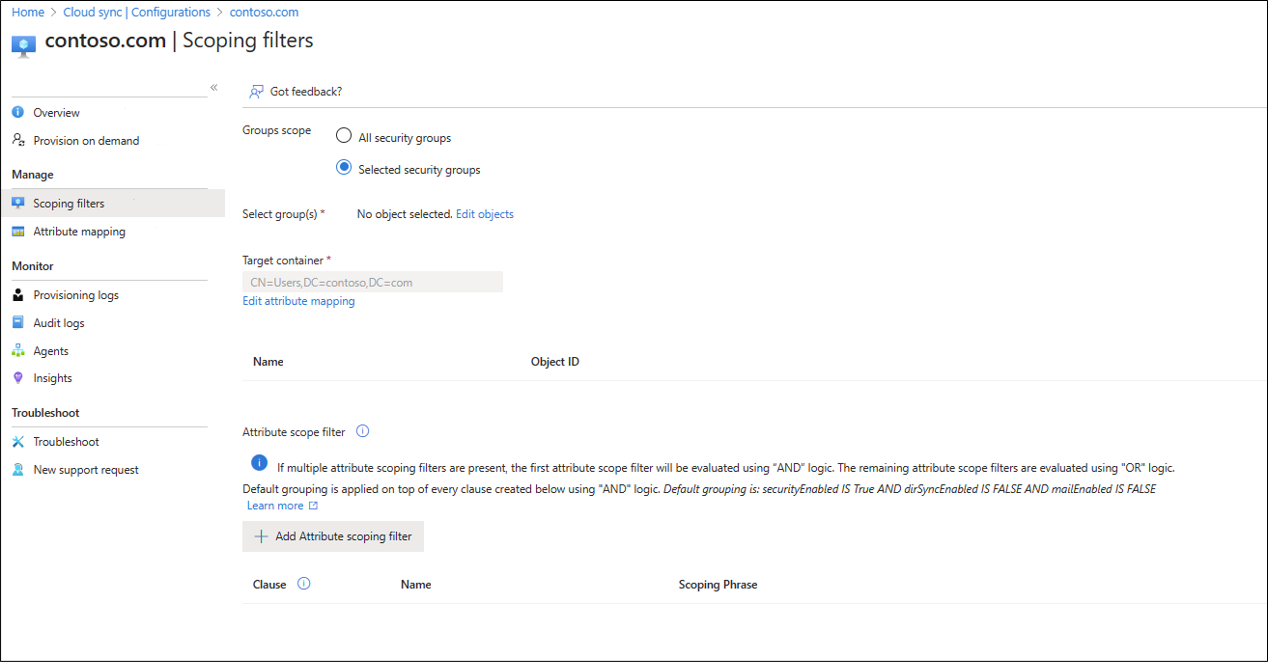
- On the Getting started configuration screen. Click either Add scoping filters next to the Add scoping filters icon or on the click Scoping filters on the left under Manage.
- Select the scoping filter. The filter can be one of the following:
- All security groups: Scopes the configuration to apply to all cloud security groups.
- Selected security groups: Scopes the configuration to apply to specific security groups.
- For specific security groups select Edit groups and pick your desired groups from the list.
Note
If you select a security group that has a nested security group as its member, then only the nested group will be written back and not it's members. For example, if a Sales security group is a member of the Marketing security group, only the Sales group itself will be written back and not the members of the Sales group.
If you want to nest groups and provision them AD, then you will need to add all of the member groups to the scope also.
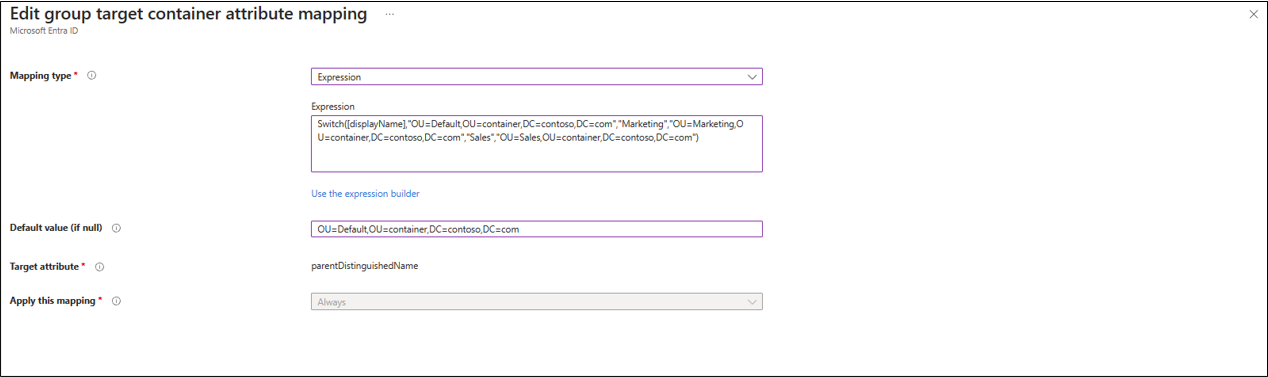
- You can use the Target Container box to scope groups that use a specific container. Accomplish this task by using the parentDistinguishedName attribute. Use either a constant, direct, or expression mapping.
Multiple target containers can be configured using an attribute mapping expression with the Switch() function. With this expression, if the displayName value is Marketing or Sales, the group is created in the corresponding OU. If there's no match, then the group is created in the default OU.
Switch([displayName],"OU=Default,OU=container,DC=contoso,DC=com","Marketing","OU=Marketing,OU=container,DC=contoso,DC=com","Sales","OU=Sales,OU=container,DC=contoso,DC=com")
- Attribute based scope filtering is supported. For more information see Attribute based scope filtering and Reference for writing expressions for attribute mappings in Microsoft Entra ID and Scenario - Using directory extensions with group provisioning to Active Directory.
- Once your scoping filters are configured, click Save.
- After saving, you should see a message telling you what you still need to do to configure cloud sync. You can click the link to continue.
Scope provisioning to specific groups using directory extensions
For more advanced scoping and filtering, you can configure the use of directory extensions. For an overview of directory extensions see Directory extensions for provisioning Microsoft Entra ID to Active Directory
For a step-by-step tutorial on how to extend the schema and then use the directory extension attribute with cloud sync provisioning to AD, see Scenario - Using directory extensions with group provisioning to Active Directory.
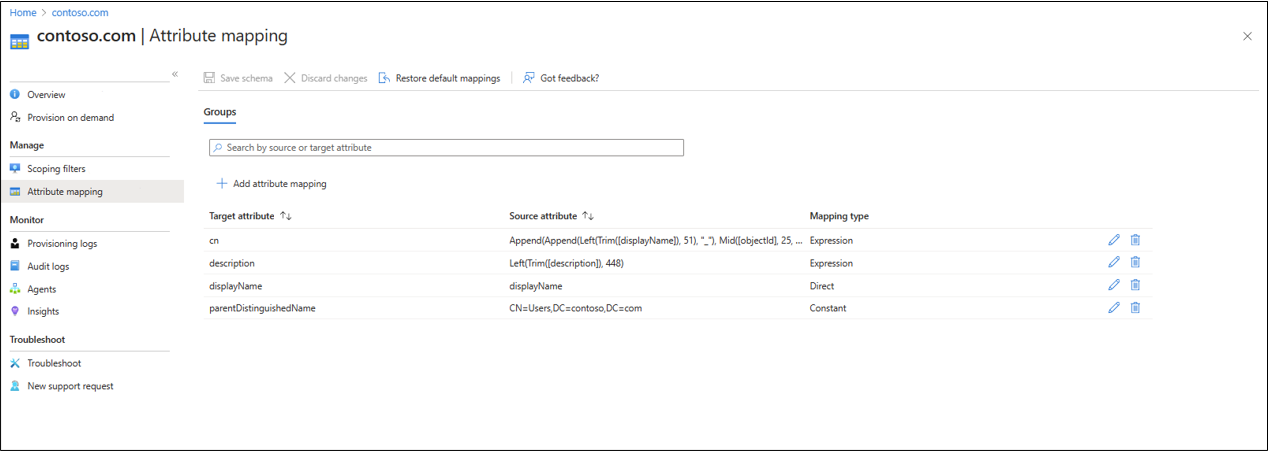
Attribute mapping
Microsoft Entra Cloud Sync allows you to easily map attributes between your on-premises user/group objects and the objects in Microsoft Entra ID.
You can customize the default attribute-mappings according to your business needs. So, you can change or delete existing attribute-mappings, or create new attribute-mappings.
After saving, you should see a message telling you what you still need to do to configure cloud sync. You can click the link to continue.
For more information, see attribute mapping and Reference for writing expressions for attribute mappings in Microsoft Entra ID.
Directory extensions and custom attribute mapping.
Microsoft Entra Cloud Sync allows you to extend the directory with extensions and provides for custom attribute mapping. For more information see Directory extensions and custom attribute mapping.
On-demand provisioning
Microsoft Entra Cloud Sync allows you to test configuration changes, by applying these changes to a single user or group.
You can use this to validate and verify that the changes made to the configuration were applied properly and are being correctly synchronized to Microsoft Entra ID.
After testing, you should see a message telling you what you still need to do to configure cloud sync. You can click the link to continue.
For more information, see on-demand provisioning.
Accidental deletions and email notifications
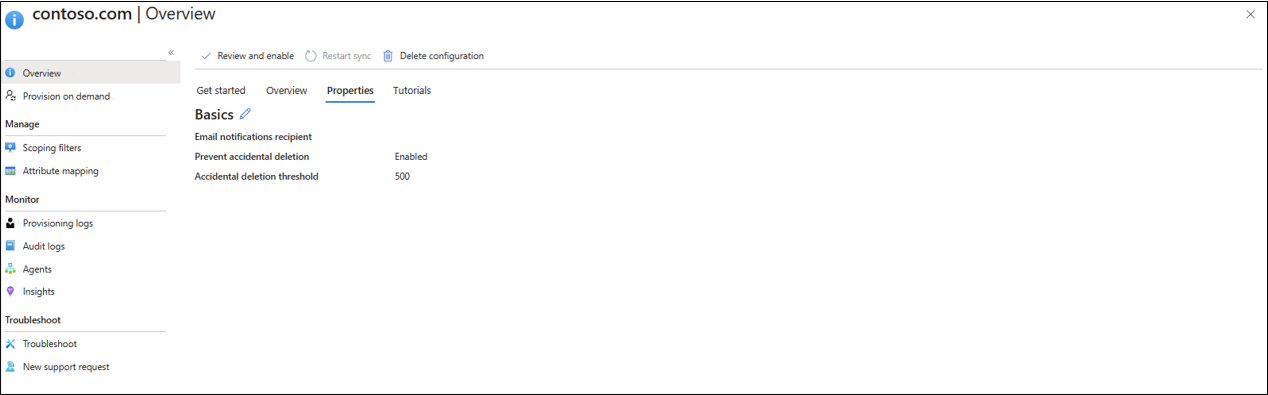
The default properties section provides information on accidental deletions and email notifications.
The accidental delete feature is designed to protect you from accidental configuration changes and changes to your on-premises directory that would affect many users and groups.
This feature allows you to:
- Configure the ability to prevent accidental deletes automatically.
- Set the # of objects (threshold) beyond which the configuration will take effect
- Set up a notification email address so they can get an email notification once the sync job in question is put in quarantine for this scenario
For more information, see Accidental deletes
Click the pencil next to Basics to change the defaults in a configuration.
Enable your configuration
Once you've finalized and tested your configuration, you can enable it.
Click Enable configuration to enable it.
Quarantines
Cloud sync monitors the health of your configuration and places unhealthy objects in a quarantine state. If most or all of the calls made against the target system consistently fail because of an error, for example, invalid admin credentials, the sync job is marked as in quarantine. For more information, see the troubleshooting section on quarantines.
Restart provisioning
If you don't want to wait for the next scheduled run, trigger the provisioning run by using the Restart sync button.
Sign in to the Microsoft Entra admin center as at least a hybrid identity administrator.
Browse to Identity > Hybrid management > Microsoft Entra Connect > Cloud Sync.
Under Configuration, select your configuration.
At the top, select Restart sync.
Remove a configuration
To delete a configuration, follow these steps.
Sign in to the Microsoft Entra admin center as at least a hybrid identity administrator.
Browse to Identity > Hybrid management > Microsoft Entra Connect > Cloud Sync.
Under Configuration, select your configuration.
At the top of the configuration screen, select Delete configuration.
Important
There's no confirmation prior to deleting a configuration. Make sure this is the action you want to take before you select Delete.