Quarantine policies
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
In Exchange Online Protection (EOP) and Microsoft Defender for Office 365, quarantine policies allow admins to define the user experience for quarantined messages:
- What users are allowed to do to their own quarantined messages (messages where they're a recipient) based on why the message was quarantined.
- Whether users receive periodic (every four hours, daily, or weekly) notifications about their quarantined messages via quarantine notifications.
Traditionally, users have been allowed or denied levels of interactivity with quarantine messages based on why the message was quarantined. For example, users can view and release messages that were quarantined as spam or bulk, but they can't view or release messages that were quarantined as high confidence phishing or malware.
Default quarantine policies enforce these historical user capabilities, and are automatically assigned in supported protection features that quarantine messages.
For details about the elements of a quarantine policy, default quarantine policies, and individual permissions, see the Appendix section at the end of this article.
If you don't like the default user capabilities for quarantined messages for a specific feature (including the lack of quarantine notifications), you can create and use custom quarantine policies as described in this article.
You create and assign quarantine policies in the Microsoft Defender portal or in PowerShell (Exchange Online PowerShell for Microsoft 365 organizations with Exchange Online mailboxes; standalone EOP PowerShell in EOP organizations without Exchange Online mailboxes).
What do you need to know before you begin?
In Microsoft 365 operated by 21Vianet in China, quarantine isn't currently available in the Microsoft Defender portal. Quarantine is available only in the classic Exchange admin center (classic EAC).
You open the Microsoft Defender portal at https://security.microsoft.com. To go directly to the Quarantine policies page, use https://security.microsoft.com/quarantinePolicies.
To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell. To connect to standalone EOP PowerShell, see Connect to Exchange Online Protection PowerShell.
If you change the quarantine policy that's assigned to a supported protection feature, the change affects quarantined message after you make the change. Messages that were quarantined before you made the change aren't affected by the settings of the new quarantine policy assignment.
How long messages that were quarantined by anti-spam and anti-phishing protection are held before they expire is controlled by the Retain spam in quarantine for this many days (QuarantineRetentionPeriod) in anti-spam policies. For more information, see the table in Quarantine retention.
You need to be assigned permissions before you can do the procedures in this article. You have the following options:
Microsoft Defender XDR Unified role based access control (RBAC) (If Email & collaboration > Defender for Office 365 permissions is
 Active. Affects the Defender portal only, not PowerShell): Authorization and settings/Security settings/Core Security settings (manage), or Security operations/Security Data/Email & collaboration quarantine (manage).
Active. Affects the Defender portal only, not PowerShell): Authorization and settings/Security settings/Core Security settings (manage), or Security operations/Security Data/Email & collaboration quarantine (manage).Email & collaboration permissions in the Microsoft Defender portal: Membership in the Quarantine Administrator, Security Administrator, or Organization Management role groups.
Microsoft Entra permissions: Membership in the Global Administrator* or Security Administrator roles gives users the required permissions and permissions for other features in Microsoft 365.
Important
* Microsoft recommends that you use roles with the fewest permissions. Using lower permissioned accounts helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
All actions taken by admins or users on quarantined messages are audited. For more information about audited quarantine events, see Quarantine schema in the Office 365 Management API.
Step 1: Create quarantine policies in the Microsoft Defender portal
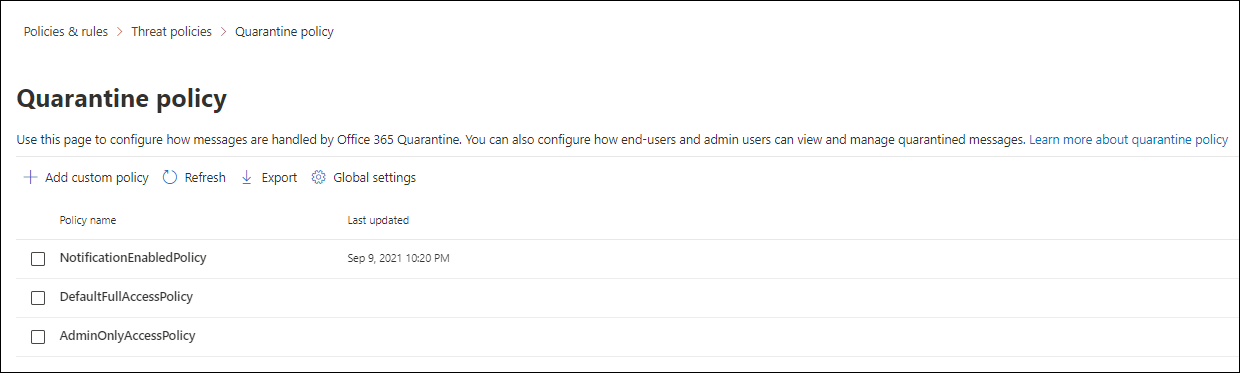
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & Rules > Threat policies > Quarantine policy in the Rules section. Or, to go directly to the Quarantine policy page, use https://security.microsoft.com/quarantinePolicies.
On the Quarantine policies page, select
 Add custom policy to start the new quarantine policy wizard.
Add custom policy to start the new quarantine policy wizard.On the Policy name page, enter a brief but unique name in the Policy name box. The policy name is selectable in dropdown lists in upcoming steps.
When you're finished on the Policy name page, select Next.
On the Recipient message access page, select one of the following values:
Limited access: The individual permissions that are included in this permission group are described in the Appendix section. Basically, users can do anything to their quarantined messages except release them from quarantine without admin approval.
Set specific access (Advanced): Use this value to specify custom permissions. Configure the following settings that appear:
- Select release action preference: Select one of the following values from the dropdown list:
- Blank: Users can't release or request the release of their messages from quarantine. This is the default value.
- Allow recipients to request a message to be released from quarantine
- Allow recipients to release a message from quarantine
- Select additional actions recipients can take on quarantined messages: Select some, all, or none of the following values:
- Delete
- Preview
- Block sender
- Allow sender
- Select release action preference: Select one of the following values from the dropdown list:
These permissions and their effect on quarantined messages and in quarantine notifications are described in the Quarantine policy permission details section later in this article.
When you're finished on the Recipient message access page, select Next.
On the Quarantine notification page, select Enable to turn on quarantine notifications, and then select one of the following values:
- Include quarantined messages from blocked sender addresses
- Don't include quarantined messages from blocked sender addresses
Tip
If you turn on quarantine notifications for No access permissions (on the Recipient message access page, you selected Set specific access (Advanced) > Select release action preference > blank), users can view their messages in quarantine, but the only available action for the messages is
 View message headers.
View message headers.When you're finished on the Quarantine notification page, select Next.
On the Review policy page, you can review your selections. Select Edit in each section to modify the settings within the section. Or you can select Back or the specific page in the wizard.
When you're finished on the Review policy page, select Submit, and then select Done in the confirmation page.
On the confirmation page that appears, you can use the links to review quarantined messages or go to the Anti-spam policies page in the Defender portal.
When you're finished on the page, select Done.
Back on the Quarantine policy page, the policy that you created is now listed. You're ready to assign the quarantine policy to a supported security feature as described in the Step 2 section.
Create quarantine policies in PowerShell
Tip
The PermissionToAllowSender permission in quarantine policies in PowerShell isn't used.
If you'd rather use PowerShell to create quarantine policies, connect to Exchange Online PowerShell or standalone Exchange Online Protection PowerShell and use the following syntax:
New-QuarantinePolicy -Name "<UniqueName>" -EndUserQuarantinePermissionsValue <0 to 236> [-EsnEnabled $true]
The ESNEnabled parameter with the value
$trueturns on quarantine notifications. Quarantine notifications are turned off by default (the default value is$false).The EndUserQuarantinePermissionsValue parameter uses a decimal value that's converted from a binary value. The binary value corresponds to the available end-user quarantine permissions in a specific order. For each permission, the value 1 equals True and the value 0 equals False.
The required order and values for each individual permission are described in the following table:
Permission Decimal value Binary value PermissionToViewHeader¹ 128 10000000 PermissionToDownload² 64 01000000 PermissionToAllowSender 32 00100000 PermissionToBlockSender 16 00010000 PermissionToRequestRelease³ 8 00001000 PermissionToRelease³ 4 00000100 PermissionToPreview 2 00000010 PermissionToDelete 1 00000001 ¹ The value 0 for this permission doesn't hide the
 View message header action in quarantine. If the message is visible to a user in quarantine, the action is always available for the message.
View message header action in quarantine. If the message is visible to a user in quarantine, the action is always available for the message.² This permission isn't used (the value 0 or 1 does nothing).
³ Don't set both of these permission values to 1. Set one value to 1 and the other value to 0, or set both values to 0.
For Limited access permissions, the required values are:
Permission Limited access PermissionToViewHeader 0 PermissionToDownload 0 PermissionToAllowSender 1 PermissionToBlockSender 0 PermissionToRequestRelease 1 PermissionToRelease 0 PermissionToPreview 1 PermissionToDelete 1 Binary value 00101011 Decimal value to use 43 If you set the ESNEnabled parameter to the value
$truewhen the value of the EndUserQuarantinePermissionsValue parameter is 0 (No access where all permissions are turned off), recipients can see their messages in quarantine, but the only available action for the messages is View message headers.
View message headers.
This example creates a new quarantine policy named LimitedAccess with quarantine notifications turned on that assigns the Limited access permissions as described in the previous table.
New-QuarantinePolicy -Name LimitedAccess -EndUserQuarantinePermissionsValue 43 -EsnEnabled $true
For custom permissions, use the previous table to get the binary value that corresponds to the permissions you want. Convert the binary value to a decimal value and use the decimal value for the EndUserQuarantinePermissionsValue parameter.
Tip
Use the equivalent decimal value for EndUserQuarantinePermissionsValue. Don't use the raw binary value.
For detailed syntax and parameter information, see New-QuarantinePolicy.
Step 2: Assign a quarantine policy to supported features
In supported protection features that quarantine email messages, the assigned quarantine policy defines what users can do to quarantine messages and whether quarantine notifications are turned on. Protection features that quarantine messages and whether they support quarantine policies are described in the following table:
| Feature | Quarantine policies supported? |
|---|---|
| Verdicts in anti-spam policies | |
| Spam (SpamAction) | Yes (SpamQuarantineTag) |
| High confidence spam (HighConfidenceSpamAction) | Yes (HighConfidenceSpamQuarantineTag) |
| Phishing (PhishSpamAction) | Yes (PhishQuarantineTag) |
| High confidence phishing (HighConfidencePhishAction) | Yes (HighConfidencePhishQuarantineTag) |
| Bulk (BulkSpamAction) | Yes (BulkQuarantineTag) |
| Verdicts in anti-phishing policies | |
| Spoof (AuthenticationFailAction) | Yes (SpoofQuarantineTag) |
| User impersonation (TargetedUserProtectionAction) | Yes (TargetedUserQuarantineTag) |
| Domain impersonation (TargetedDomainProtectionAction) | Yes (TargetedDomainQuarantineTag) |
| Mailbox intelligence impersonation (MailboxIntelligenceProtectionAction) | Yes (MailboxIntelligenceQuarantineTag) |
| Anti-malware policies | Yes (QuarantineTag) |
| Safe Attachments protection | |
| Email messages with attachments that are quarantined as malware by Safe Attachments policies (Enable and Action) | Yes (QuarantineTag) |
| Files that are quarantined as malware by Safe Attachments for SharePoint, OneDrive, and Microsoft Teams | No |
| Exchange mail flow rules (also known as transport rules) with the action: 'Deliver the message to the hosted quarantine' (Quarantine) | No |
The default quarantine policies that are used by each protection feature are described in the related tables in Recommended settings for EOP and Microsoft Defender for Office 365 security.
The default quarantine policies, preset permission groups, and permissions are described in the Appendix section at the end of this article.
The rest of this step explains how to assign quarantine policies for supported filter verdicts.
Assign quarantine policies in supported policies in the Microsoft Defender portal
Note
Users can't release their own messages that were quarantined as malware by anti-malware or Safe Attachments policies, or as high confidence phishing by anti-spam policies, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware or high confidence phishing messages.
Anti-spam policies
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Anti-spam in the Policies section. Or, to go directly to the Anti-spam policies page, use https://security.microsoft.com/antispam.
On the Anti-spam policies page, use either of the following methods:
- Select an existing inbound anti-spam policy by clicking anywhere in the row other than the check box next to the name. In the policy details flyout that opens, go to the Actions section and then select Edit actions.
- Select
 Create policy, select Inbound from the dropdown list to start the new anti-spam policy wizard, and then get to the Actions page.
Create policy, select Inbound from the dropdown list to start the new anti-spam policy wizard, and then get to the Actions page.
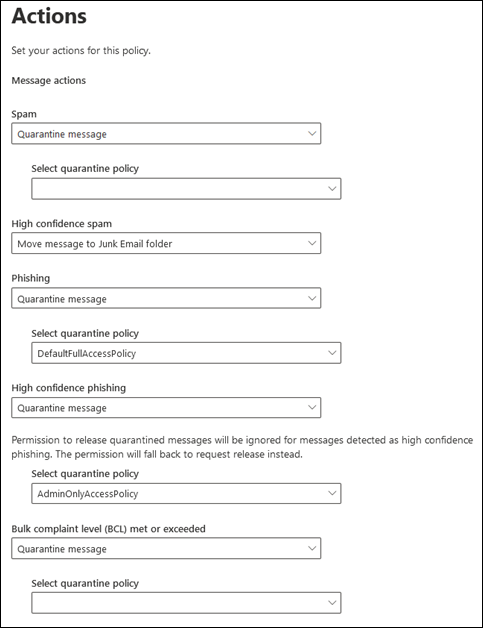
On the Actions page or flyout, every verdict that has the Quarantine message action selected also has the Select quarantine policy box for you to select a quarantine policy.
During the creation of the anti-spam policy, if you change the action of a spam filtering verdict to Quarantine message, the Select quarantine policy box is blank by default. A blank value means the default quarantine policy for that verdict is used. When you later view or edit the anti-spam policy settings, the quarantine policy name is shown. The default quarantine policies are listed in the supported features table.
Full instructions for creating and modifying anti-spam policies are described in Configure anti-spam policies in EOP.
Anti-spam policies in PowerShell
If you'd rather use PowerShell to assign quarantine policies in anti-spam policies, connect to Exchange Online PowerShell or Exchange Online Protection PowerShell and use the following syntax:
<New-HostedContentFilterPolicy -Name "<Unique name>" | Set-HostedContentFilterPolicy -Identity "<Policy name>"> [-SpamAction Quarantine] [-SpamQuarantineTag <QuarantineTagName>] [-HighConfidenceSpamAction Quarantine] [-HighConfidenceSpamQuarantineTag <QuarantineTagName>] [-PhishSpamAction Quarantine] [-PhishQuarantineTag <QuarantineTagName>] [-HighConfidencePhishQuarantineTag <QuarantineTagName>] [-BulkSpamAction Quarantine] [-BulkQuarantineTag <QuarantineTagName>] ...
Quarantine policies matter only when messages are quarantined. The default value for the HighConfidencePhishAction parameter is Quarantine, so you don't need to use that *Action parameter when you create new spam filter policies in PowerShell. By default, all other *Action parameters in new spam filter policies aren't set to value Quarantine.
To see the important parameter values in existing anti-spam policies, run the following command:
Get-HostedContentFilterPolicy | Format-List Name,SpamAction,SpamQuarantineTag,HighConfidenceSpamAction,HighConfidenceSpamQuarantineTag,PhishSpamAction,PhishQuarantineTag,HighConfidencePhishAction,HighConfidencePhishQuarantineTag,BulkSpamAction,BulkQuarantineTagIf you create an anti-spam policy without specifying the quarantine policy for the spam filtering verdict, the default quarantine policy for that verdict is used. For information about the default action values and the recommended action values for Standard and Strict, see EOP anti-spam policy settings.
Specify a different quarantine policy to turn on quarantine notifications or change the default end-user capabilities on quarantined messages for that particular spam filtering verdict.
Users can't release their own messages that were quarantined as high confidence phishing, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined high confidence phishing messages.
In PowerShell, a new anti-spam policy in PowerShell requires a spam filter policy using the New-HostedContentFilterPolicy cmdlet (settings), and an exclusive spam filter rule using the New-HostedContentFilterRule cmdlet (recipient filters). For instructions, see Use PowerShell to create anti-spam policies.
This example creates a new spam filter policy named Research Department with the following settings:
- The action for all spam filtering verdicts is set to Quarantine.
- The default quarantine policy named AdminOnlyAccessPolicy that assigns No access permissions replaces the default quarantine policy that's used (high confidence phishing messages are quarantined by default and the AdminOnlyAccessPolicy quarantine policy is used by default).
New-HostedContentFilterPolicy -Name "Research Department" -SpamAction Quarantine -SpamQuarantineTag AdminOnlyAccessPolicy -HighConfidenceSpamAction Quarantine -HighConfidenceSpamQuarantineTag AdminOnlyAccessPolicy -PhishSpamAction Quarantine -PhishQuarantineTag AdminOnlyAccessPolicy -BulkSpamAction Quarantine -BulkQuarantineTag AdminOnlyAccessPolicy
For detailed syntax and parameter information, see New-HostedContentFilterPolicy.
This example modifies the existing spam filter policy named Human Resources. The action for the spam quarantine verdict is set to Quarantine, and the custom quarantine policy named ContosoNoAccess is assigned.
Set-HostedContentFilterPolicy -Identity "Human Resources" -SpamAction Quarantine -SpamQuarantineTag ContosoNoAccess
For detailed syntax and parameter information, see Set-HostedContentFilterPolicy.
Anti-phishing policies
Spoof intelligence is available in EOP and Defender for Office 365. User impersonation protection, domain impersonation protection, and mailbox intelligence protection are available only in Defender for Office 365. For more information, see Anti-phishing policies in Microsoft 365.
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Anti-phishing in the Policies section. Or, to go directly to the Anti-phishing page, use https://security.microsoft.com/antiphishing.
On the Anti-phishing page, use either of the following methods:
- Select an existing anti-phishing policy by clicking anywhere in the row other than the check box next to the name. In the policy details flyout that opens, select the Edit link in the relevant section as described in the next steps.
- Select
 Create to start the new anti-phishing policy wizard. The relevant pages are described in the next steps.
Create to start the new anti-phishing policy wizard. The relevant pages are described in the next steps.
On the Phishing threshold & protection page or flyout, verify that the following settings are turned on and configured as required:
- Enabled users to protect: Specify users.
- Enabled domains to protect: Select Include domains I own and/or Include custom domains and specify the domains.
- Enable mailbox intelligence
- Enable intelligence for impersonation protection
- Enable spoof intelligence
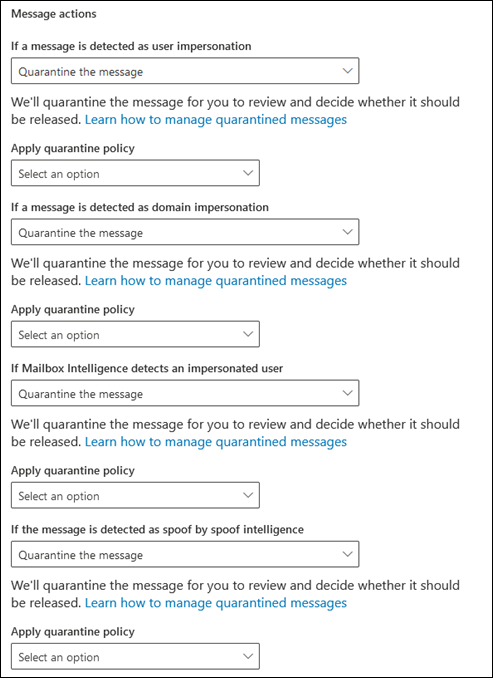
On the Actions page or flyout, every verdict that has the Quarantine the message action also has the Apply quarantine policy box for you to select a quarantine policy.
During the creation of the anti-phishing policy, if you don't select a quarantine policy, the default quarantine policy is used. When you later view or edit the anti-phishing policy settings, the quarantine policy name is shown. The default quarantine policies are listed in the supported features table.
Full instructions for creating and modifying anti-phishing policies are available in the following articles:
- Configure anti-phishing policies in EOP
- Configure anti-phishing policies in Microsoft Defender for Office 365
Anti-phishing policies in PowerShell
If you'd rather use PowerShell to assign quarantine policies in anti-phishing policies, connect to Exchange Online PowerShell or Exchange Online Protection PowerShell and use the following syntax:
<New-AntiPhishPolicy -Name "<Unique name>" | Set-AntiPhishPolicy -Identity "<Policy name>"> [-EnableSpoofIntelligence $true] [-AuthenticationFailAction Quarantine] [-SpoofQuarantineTag <QuarantineTagName>] [-EnableMailboxIntelligence $true] [-EnableMailboxIntelligenceProtection $true] [-MailboxIntelligenceProtectionAction Quarantine] [-MailboxIntelligenceQuarantineTag <QuarantineTagName>] [-EnableOrganizationDomainsProtection $true] [-EnableTargetedDomainsProtection $true] [-TargetedDomainProtectionAction Quarantine] [-TargetedDomainQuarantineTag <QuarantineTagName>] [-EnableTargetedUserProtection $true] [-TargetedUserProtectionAction Quarantine] [-TargetedUserQuarantineTag <QuarantineTagName>] ...
Quarantine policies matter only when messages are quarantined. In anti-phish policies, messages are quarantined when the Enable* parameter value for the feature is $true and the corresponding *\Action parameter value is Quarantine. The default value for the EnableMailboxIntelligence and EnableSpoofIntelligence parameters is $true, so you don't need to use them when you create new anti-phish policies in PowerShell. By default, no *\Action parameters have the value Quarantine.
To see the important parameter values in existing anti-phish policies, run the following command:
Get-AntiPhishPolicy | Format-List EnableSpoofIntelligence,AuthenticationFailAction,SpoofQuarantineTag,EnableTargetedUserProtection,TargetedUserProtectionAction,TargetedUserQuarantineTag,EnableTargetedDomainsProtection,EnableOrganizationDomainsProtection,TargetedDomainProtectionAction,TargetedDomainQuarantineTag,EnableMailboxIntelligence,EnableMailboxIntelligenceProtection,MailboxIntelligenceProtectionAction,MailboxIntelligenceQuarantineTagFor information about the default and recommended action values for Standard and Strict configurations, see EOP anti-phishing policy settings and Impersonation settings in anti-phishing policies in Microsoft Defender for Office 365.
If you create a new anti-phishing policy without specifying the quarantine policy for the anti-phishing action, the default quarantine policy for that action is used. The default quarantine policies for each anti-phishing action are shown in EOP anti-phishing policy settings and Anti-phishing policy settings in Microsoft Defender for Office 365.
Specify a different quarantine policy only if you want to change the default end-user capabilities on quarantined messages for that particular anti-phishing action.
A new anti-phishing policy in PowerShell requires an anti-phish policy using the New-AntiPhishPolicy cmdlet (settings), and an exclusive anti-phish rule using the New-AntiPhishRule cmdlet (recipient filters). For instructions, see the following articles:
This example creates a new anti-phish policy named Research Department with the following settings:
- The action for all spam filtering verdicts is set to Quarantine.
- The default quarantine policy named AdminOnlyAccessPolicy that assigns No access permissions replaces the default quarantine policy that's used.
New-AntiPhishPolicy -Name "Research Department" -AuthenticationFailAction Quarantine -SpoofQuarantineTag NoAccess -EnableMailboxIntelligenceProtection $true -MailboxIntelligenceProtectionAction Quarantine -MailboxIntelligenceQuarantineTag NoAccess -EnableOrganizationDomainsProtection $true -EnableTargetedDomainsProtection $true -TargetedDomainProtectionAction Quarantine -TargetedDomainQuarantineTag NoAccess -EnableTargetedUserProtection $true -TargetedUserProtectionAction Quarantine -TargetedUserQuarantineTag NoAccess
For detailed syntax and parameter information, see New-AntiPhishPolicy.
This example modifies the existing anti-phish policy named Human Resources. The action for messages detected by user impersonation and domain impersonation is set to Quarantine, and the custom quarantine policy named ContosoNoAccess is assigned.
Set-AntiPhishPolicy -Identity "Human Resources" -EnableTargetedDomainsProtection $true -TargetedDomainProtectionAction Quarantine -TargetedDomainQuarantineTag ContosoNoAccess -EnableTargetedUserProtection $true -TargetedUserProtectionAction Quarantine -TargetedUserQuarantineTag ContosoNoAccess
For detailed syntax and parameter information, see Set-AntiPhishPolicy.
Anti-malware policies
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Anti-malware in the Policies section. Or, to go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2.
On the Anti-malware page, use either of the following methods:
- Select an existing anti-malware policy by clicking anywhere in the row other than the check box next to the name. In the policy details flyout that opens, go to the Protection settings section, and then select Edit protection settings.
- Select
 Create to start the new anti-malware policy wizard and get to the Protection settings page.
Create to start the new anti-malware policy wizard and get to the Protection settings page.
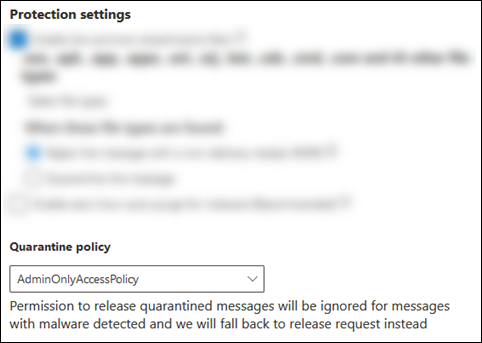
On the Protection settings page or flyout, view or select a quarantine policy in the Quarantine policy box.
Quarantine notifications are disabled in the policy named AdminOnlyAccessPolicy. To notify recipients that have messages quarantined as malware, create or use an existing quarantine policy where quarantine notifications are turned on. For instructions, see Create quarantine policies in the Microsoft Defender portal.
Users can't release their own messages that were quarantined as malware by anti-malware policies, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware messages.
Full instructions for creating and modifying anti-malware policies are available in Configure anti-malware policies.
Anti-malware policies in PowerShell
If you'd rather use PowerShell to assign quarantine policies in anti-malware policies, connect to Exchange Online PowerShell or Exchange Online Protection PowerShell and use the following syntax:
<New-AntiMalwarePolicy -Name "<Unique name>" | Set-AntiMalwarePolicy -Identity "<Policy name>"> [-QuarantineTag <QuarantineTagName>]
When you create new anti-malware policies without using the QuarantineTag parameter, the default quarantine policy named AdminOnlyAccessPolicy is used.
Users can't release their own messages that were quarantined as malware, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware messages.
To see the important parameter values in existing anti-phish policies, run the following command:
Get-MalwareFilterPolicy | Format-Table Name,QuarantineTagA new anti-malware policy in PowerShell requires a malware filter policy using the New-MalwareFilterPolicy cmdlet (settings), and an exclusive malware filter rule using the New-MalwareFilterRule cmdlet (recipient filters). For instructions, see Use Exchange Online PowerShell or standalone EOP PowerShell to configure anti-malware policies.
This example creates a malware filter policy named Research Department that uses the custom quarantine policy named ContosoNoAccess that assigns No access permissions to the quarantined messages.
New-MalwareFilterPolicy -Name "Research Department" -QuarantineTag ContosoNoAccess
For detailed syntax and parameter information, see New-MalwareFilterPolicy.
This example modifies the existing malware filter policy named Human Resources to use the custom quarantine policy named ContosoNoAccess that assigns No access permissions to the quarantined messages.
New-MalwareFilterPolicy -Identity "Human Resources" -QuarantineTag ContosoNoAccess
For detailed syntax and parameter information, see Set-MalwareFilterPolicy.
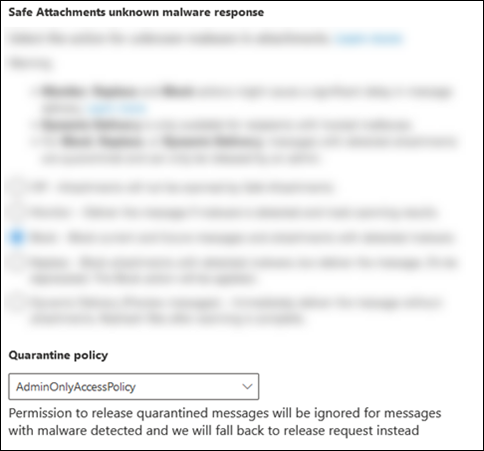
Safe Attachments policies in Defender for Office 365
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Safe Attachments in the Policies section. Or, to go directly to the Safe Attachments page, use https://security.microsoft.com/safeattachmentv2.
On the Safe Attachments page, use either of the following methods:
- Select an existing Safe Attachments policy by clicking anywhere in the row other than the check box next to the name. In the policy details flyout that opens, select the Edit settings link in Settings section.
- Select
 Create to start the new Safe Attachments policy wizard and get to the Settings page.
Create to start the new Safe Attachments policy wizard and get to the Settings page.
On the Settings page or flyout, view or select a quarantine policy in the Quarantine policy box.
Users can't release their own messages that were quarantined as malware by Safe Attachments policies, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware messages.
Full instructions for creating and modifying Safe Attachments policies are described in Set up Safe Attachments policies in Microsoft Defender for Office 365.
Safe Attachments policies in PowerShell
If you'd rather use PowerShell to assign quarantine policies in Safe Attachments policies, connect to Exchange Online PowerShell or Exchange Online Protection PowerShell and use the following syntax:
<New-SafeAttachmentPolicy -Name "<Unique name>" | Set-SafeAttachmentPolicy -Identity "<Policy name>"> -Enable $true -Action <Block | DynamicDelivery> [-QuarantineTag <QuarantineTagName>]
The Action parameter values Block or DynamicDelivery can result in quarantined messages (the value Allow doesn't quarantine messages). The value of the Action parameter in meaningful only when the value of the Enable parameter is
$true.When you create new Safe Attachments policies without using the QuarantineTag parameter, the default quarantine policy named AdminOnlyAccessPolicy is used for malware detections by Safe Attachments.
Users can't release their own messages that were quarantined as malware, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware messages.
To see the important parameter values, run the following command:
Get-SafeAttachmentPolicy | Format-List Name,Enable,Action,QuarantineTagA new Safe Attachments policy in PowerShell requires a safe attachment policy using the New-SafeAttachmentPolicy cmdlet (settings), and an exclusive safe attachment rule using the New-SafeAttachmentRule cmdlet (recipient filters). For instructions, see Use Exchange Online PowerShell to configure Safe Attachments policies.
This example creates a safe attachment policy named Research Department that blocks detected messages and uses the custom quarantine policy named ContosoNoAccess that assigns No access permissions to the quarantined messages.
New-SafeAttachmentPolicy -Name "Research Department" -Enable $true -Action Block -QuarantineTag NoAccess
For detailed syntax and parameter information, see New-MalwareFilterPolicy.
This example modifies the existing safe attachment policy named Human Resources to use the custom quarantine policy named ContosoNoAccess that assigns No access permissions.
Set-SafeAttachmentPolicy -Identity "Human Resources" -QuarantineTag ContosoNoAccess
For detailed syntax and parameter information, see Set-MalwareFilterPolicy.
Configure global quarantine notification settings in the Microsoft Defender portal
The global settings for quarantine policies allow you to customize the quarantine notifications that are sent to recipients of quarantined messages if quarantine notifications are turned on in the quarantine policy. For more information about quarantine notifications, see Quarantine notifications.
Customize quarantine notifications for different languages
The message body of quarantine notifications is already localized based on the language setting of the recipient's cloud-based mailbox.
You can use the procedures in this section to customize the Sender display name, Subject, and Disclaimer values that are used in quarantine notifications based on the language setting of the recipient's cloud-based mailbox:
The Sender display name as shown in the following screenshot:
The Subject field of quarantine notification messages.
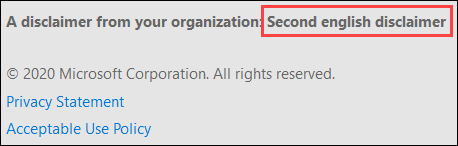
The Disclaimer text that's added to the bottom of quarantine notifications (max. 200 characters). The localized text, A disclaimer from your organization: is always included first, followed by the text you specify as show in the following screenshot:
Tip
Quarantine notifications aren't localized for on-premises mailboxes.
A custom quarantine notification for a specific language is shown to users only when their mailbox language matches the language in the custom quarantine notification.
The value English_USA applies only to US English clients. The value English_Great Britain applies to all other English clients (Great Britain, Canada, Australia, etc.).
The languages Norwegian and Norwegian (Nynorsk) are available. Norwegian (Bokmål) isn't available.
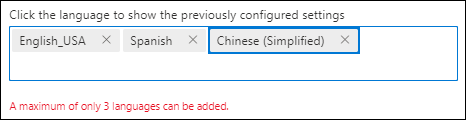
To create customized quarantine notifications for up to three languages, do the following steps:
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Quarantine policies in the Rules section. Or, to go directly to the Quarantine policies page, use https://security.microsoft.com/quarantinePolicies.
On the Quarantine policies page, select
 Global settings.
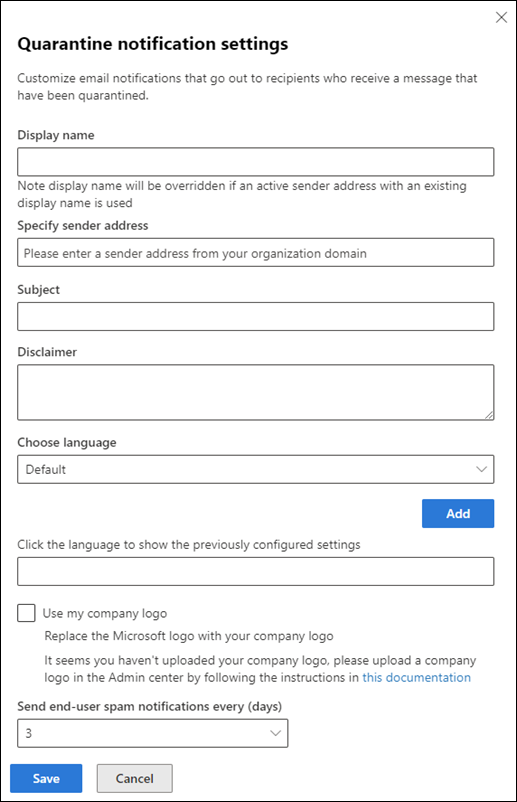
Global settings.In the Quarantine notification settings flyout that opens, do the following steps:
Select the language from the Choose language box. The default value is English_USA.
Although this box isn't the first setting, you need to configure it first. If you enter values in the Sender display name, Subject, or Disclaimer boxes before you select the language, those values disappear.
After you select the language, enter values for Sender display name, Subject, and Disclaimer. The values must be unique for each language. If you try to reuse a value in a different language, you'll get an error when you select Save.
Select the Add button near the Choose language box.
After you select Add, the configured settings for the language appear in the Click the language to show the previously configured settings box. To reload the settings, click on the language name. To remove the language, select
 .
.Repeat the previous steps to create a maximum of three customized quarantine notifications based on the recipient's language.
When you're finished on the Quarantine notifications flyout, select Save.
For information about the Specify sender address
Customize all quarantine notifications
Even if you don't customize quarantine notifications for different languages, settings are available in the Quarantine notifications flyout to customize all quarantine notifications. Or, you can configure the settings before, during, or after you customize quarantine notifications for different languages (these settings apply to all languages):
Specify sender address: Select an existing user for the sender email address of quarantine notifications. The default sender is
quarantine@messaging.microsoft.com.Use my company logo: Select this option to replace the default Microsoft logo that's used at the top of quarantine notifications. Before you do this step, you need to follow the instructions in Customize the Microsoft 365 theme for your organization to upload your custom logo.
Tip
PNG or JPEG logos are the most compatible in quarantine notifications in all versions of Outlook. For the best compatibility with SVG logos in quarantine notifications, use a URL link to the SVG logo instead of directly uploading the SVG file when you customize the Microsoft 365 theme.
A custom logo in a quarantine notification is shown in the following screenshot:
Send end-user spam notification every (days): Select the frequency for quarantine notifications. You can select Within 4 hours, Daily, or Weekly.
Tip
If you select every four hours, and a message is quarantined just after the last notification generation, the recipient will receive the quarantine notification slightly more than four hours later.
When you're finished in the Quarantine notifications flyout, select Save.
Use PowerShell to configure global quarantine notification settings
If you'd rather use PowerShell to configure global quarantine notification settings, connect to Exchange Online PowerShell or Exchange Online Protection PowerShell and use the following syntax:
Get-QuarantinePolicy -QuarantinePolicyType GlobalQuarantinePolicy | Set-QuarantinePolicy -MultiLanguageSetting ('Language1','Language2','Language3') -MultiLanguageCustomDisclaimer ('Language1 Disclaimer','Language2 Disclaimer','Language3 Disclaimer') -ESNCustomSubject ('Language1 Subject','Language2 Subject','Language3 Subject') -MultiLanguageSenderName ('Language1 Sender Display Name','Language2 Sender Display Name','Language3 Sender Display Name') [-EndUserSpamNotificationCustomFromAddress <InternalUserEmailAddress>] [-OrganizationBrandingEnabled <$true | $false>] [-EndUserSpamNotificationFrequency <04:00:00 | 1.00:00:00 | 7.00:00:00>]
- You can specify a maximum of 3 available languages. The value Default is en-US. The value English is everything else (en-GB, en-CA, en-AU, etc.).
- For each language, you need to specify unique MultiLanguageCustomDisclaimer, ESNCustomSubject, and MultiLanguageSenderName values.
- If any of the text values contain quotation marks, you need to escape the quotation mark with an additional quotation mark. For example, change
d'assistancetod''assistance.
This example configures the following settings:
- Customized quarantine notifications for US English and Spanish.
- The quarantine notification sender's email address is set to
michelle@contoso.onmicrosoft.com.
Get-QuarantinePolicy -QuarantinePolicyType GlobalQuarantinePolicy | Set-QuarantinePolicy -MultiLanguageSetting ('Default','Spanish') -MultiLanguageCustomDisclaimer ('For more information, contact the Help Desk.','Para obtener más información, comuníquese con la mesa de ayuda.') -ESNCustomSubject ('You have quarantined messages','Tienes mensajes en cuarentena') -MultiLanguageSenderName ('Contoso administrator','Administradora de contoso') -EndUserSpamNotificationCustomFromAddress michelle@contoso.onmicrosoft.com
For detailed syntax and parameter information, see Set-QuarantinePolicy.
View quarantine policies in the Microsoft Defender portal
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Quarantine policies in the Rules section. Or, to go directly to the Quarantine policies page, use https://security.microsoft.com/quarantinePolicies.
The Quarantine policies page shows the list of policies by Policy name and Last updated date/time.
To view the settings of default or custom quarantine policies, select the policy by clicking anywhere in the row other than the check box next to the name. Details are available in the flyout that opens.
To view the global settings, select Global settings
View quarantine policies in PowerShell
If you'd rather use PowerShell to view quarantine policies, do any of the following steps:
To view a summary list of all default or custom policies, run the following command:
Get-QuarantinePolicy | Format-Table NameTo view the settings of default or custom quarantine policies, replace <QuarantinePolicyName> with the name of the quarantine policy, and run the following command:
Get-QuarantinePolicy -Identity "<QuarantinePolicyName>"To view the global settings for quarantine notifications, run the following command:
Get-QuarantinePolicy -QuarantinePolicyType GlobalQuarantinePolicy
For detailed syntax and parameter information, see Get-HostedContentFilterPolicy.
Modify quarantine policies in the Microsoft Defender portal
You can't modify the default quarantine policies named AdminOnlyAccessPolicy, DefaultFullAccessPolicy, or DefaultFullAccessWithNotificationPolicy.
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Quarantine policies in the Rules section. Or, to go directly to the Quarantine policies page, use https://security.microsoft.com/quarantinePolicies.
On the Quarantine policies page, select the policy by clicking the check box next to the name.
Select the
 Edit policy action that appears.
Edit policy action that appears.
The policy wizard opens with the settings and values of the selected quarantine policy. The steps are virtually the same as described in the Create quarantine policies in the Microsoft Defender portal section. The main difference is: you can't rename an existing policy.
Modify quarantine policies in PowerShell
If you'd rather use PowerShell to modify a custom quarantine policy, replace <QuarantinePolicyName> with the name of the quarantine policy, and use the following syntax:
Set-QuarantinePolicy -Identity "<QuarantinePolicyName>" [Settings]
The available settings are the same as described for creating quarantine policies earlier in this article.
For detailed syntax and parameter information, see Set-QuarantinePolicy.
Remove quarantine policies in the Microsoft Defender portal
Note
Don't remove a quarantine policy until you verify that it isn't being used. For example, run the following command in PowerShell:
Write-Output -InputObject "Anti-spam policies",("-"*25);Get-HostedContentFilterPolicy | Format-List Name,*QuarantineTag; Write-Output -InputObject "Anti-phishing policies",("-"*25);Get-AntiPhishPolicy | Format-List Name,*QuarantineTag; Write-Output -InputObject "Anti-malware policies",("-"*25);Get-MalwareFilterPolicy | Format-List Name,QuarantineTag; Write-Output -InputObject "Safe Attachments policies",("-"*25);Get-SafeAttachmentPolicy | Format-List Name,QuarantineTagIf the quarantine policy is being used, replace the assigned quarantine policy before you remove it to avoid the potential disruption in quarantine notifications.
You can't remove the default quarantine policies named AdminOnlyAccessPolicy, DefaultFullAccessPolicy, or DefaultFullAccessWithNotificationPolicy.
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Policies & rules > Threat policies > Quarantine policies in the Rules section. Or, to go directly to the Quarantine policies page, use https://security.microsoft.com/quarantinePolicies.
On the Quarantine policies page, select the policy by clicking the check box next to the name.
Select the
 Delete policy action that appears.
Delete policy action that appears.Select Remove policy in the confirmation dialog.
Remove quarantine policies in PowerShell
If you'd rather use PowerShell to remove a custom quarantine policy, replace <QuarantinePolicyName> with the name of the quarantine policy, and run the following command:
Remove-QuarantinePolicy -Identity "<QuarantinePolicyName>"
For detailed syntax and parameter information, see Remove-QuarantinePolicy.
System alerts for quarantine release requests
By default, the default alert policy named User requested to release a quarantined message automatically generates an informational alert and sends notification to Organization Management (global administrator) whenever a user requests the release of a quarantined message:
Admins can customize the email notification recipients or create a custom alert policy for more options.
For more information about alert policies, see Alert policies in the Microsoft Defender portal.
Appendix
Anatomy of a quarantine policy
A quarantine policy contains permissions that are combined into preset permission groups. The preset permissions groups are:
- No access
- Limited access
- Full access
As previously described, default quarantine policies enforce historical user capabilities on quarantined messages, and are automatically assigned to actions in supported protection features that quarantine messages.
The default quarantine policies are:
- AdminOnlyAccessPolicy
- DefaultFullAccessPolicy
- DefaultFullAccessWithNotificationPolicy
- NotificationEnabledPolicy (in some organizations)
Quarantine policies also control whether users receive quarantine notifications about messages that were quarantined instead of delivered to them. Quarantine notifications do two things:
- Inform the user that the message is in quarantine.
- Allow users to view and take action on the quarantined message from the quarantine notification. Permissions control what the user can do in the quarantine notification as described in the Quarantine policy permission details section.
The relationship between permissions, permissions groups, and the default quarantine policies are described in the following tables:
| Permission | No access | Limited access | Full access |
|---|---|---|---|
| (PermissionToViewHeader)¹ | ✔ | ✔ | ✔ |
| Allow sender (PermissionToAllowSender) | ✔ | ✔ | |
| Block sender (PermissionToBlockSender) | |||
| Delete (PermissionToDelete) | ✔ | ✔ | |
| Preview (PermissionToPreview)² | ✔ | ✔ | |
| Allow recipients to release a message from quarantine (PermissionToRelease)³ | ✔ | ||
| Allow recipients to request a message to be released from quarantine (PermissionToRequestRelease) | ✔ |
| Default quarantine policy | Permission group used | Quarantine notifications enabled? |
|---|---|---|
| AdminOnlyAccessPolicy | No access | No |
| DefaultFullAccessPolicy | Full access | No |
| DefaultFullAccessWithNotificationPolicy⁴ | Full access | Yes |
| NotificationEnabledPolicy⁵ | Full access | Yes |
¹ This permission isn't available in the Defender portal. Turning off the permission in PowerShell doesn't affect the availability of the ![]() View message header action on quarantined messages. If the message is visible to a user in quarantine, View message header is always available for the message.
View message header action on quarantined messages. If the message is visible to a user in quarantine, View message header is always available for the message.
² The Preview permission is unrelated to the Review message action that's available in quarantine notifications.
³ Allow recipients to release a message from quarantine isn't honored for messages that were quarantined as malware by anti-malware policies or Safe Attachments policies, or as high confidence phishing by anti-spam policies.
⁴ This policy is used in preset security policies to enable quarantine notifications instead of the policy named DefaultFullAccessPolicy where notifications are turned off.
⁵ Your organization might not have the policy named NotificationEnabledPolicy as described in the next section.
Full access permissions and quarantine notifications
The default quarantine policy named DefaultFullAccessPolicy duplicates the historical permissions for less harmful quarantined messages, but quarantine notifications aren't turned on in the quarantine policy. Where DefaultFullAccessPolicy is used by default is described in the feature tables in Recommended settings for EOP and Microsoft Defender for Office 365 security.
To give organizations the permissions of DefaultFullAccessPolicy with quarantine notifications turned on, we selectively included a default policy named NotificationEnabledPolicy based on the following criteria:
The organization existed before the introduction of quarantine policies (July-August 2021).
and
The Enable end-user spam notifications setting was turned on in one or more anti-spam policies. Before the introduction of quarantine policies, this setting determined whether users received notifications about their quarantined messages.
Newer organizations or older organizations that never turned on end-user spam notifications don't have the policy named NotificationEnabledPolicy.
To give users Full access permissions and quarantine notifications, organizations that don't have the NotificationEnabledPolicy policy have the following options:
- Use the default policy named DefaultFullAccessWithNotificationPolicy.
- Create and use custom quarantine policies with Full access permissions and quarantine notifications turned on.
Quarantine policy permission details
The following sections describe the effects of preset permission groups and individual permissions for users in quarantined messages and in quarantine notifications.
Note
As explained earlier, quarantine notifications are turned on only in the default policies named DefaultFullAccessWithNotificationPolicy or (if your organization is old enough) NotificationEnabledPolicy.
Preset permissions groups
The individual permissions that are included in preset permission groups are described in the Anatomy of a quarantine policy section.
No access
The effect of No access permissions (admin only access) on user capabilities depends on the state of quarantine notifications in the quarantine policy:
Quarantine notifications turned off:
- On the Quarantine page: Quarantined messages aren't visible to users.
- In quarantine notifications: Users don't receive quarantine notifications for the messages.
Quarantine notifications turned on:
- On the Quarantine page: Quarantined messages are visible to users, but the only available action is
 View message headers.
View message headers. - In quarantine notifications: Users receive quarantine notifications, but the only available action is Review message.
- On the Quarantine page: Quarantined messages are visible to users, but the only available action is
Limited access
If the quarantine policy assigns Limited access permissions, users get the following capabilities:
On the Quarantine page and in the message details in quarantine: The following actions are available:
 Request release (the difference from Full access permissions)
Request release (the difference from Full access permissions) Delete
Delete Preview message
Preview message View message headers
View message headers Allow sender
Allow sender
In quarantine notifications: The following actions are available:
- Review message
- Request release (the difference from Full access permissions)
Full access
If the quarantine policy assigns Full access permissions (all available permissions), users get the following capabilities:
On the Quarantine page and in the message details in quarantine: The following actions are available:
 Release (the difference from Limited access permissions)
Release (the difference from Limited access permissions) Delete
Delete Preview message
Preview message View message headers
View message headers Allow sender
Allow sender
In quarantine notifications: The following actions are available:
- Review message
- Release (the difference from Limited access permissions)
Individual permissions
Allow sender permission
The Allow sender permission (PermissionToAllowSender) allows users to add the message sender to the Safe Senders list in their mailbox.
If the Allow sender permission is enabled:
![]()
 Allow sender is available on the Quarantine page and in the message details in quarantine.
Allow sender is available on the Quarantine page and in the message details in quarantine.
If the Allow sender permission is disabled, users can't allow senders from quarantine (the action isn't available).
For more information about the Safe Senders list, see Add recipients of my email messages to the Safe Senders List and Use Exchange Online PowerShell to configure the safelist collection on a mailbox.
Block sender permission
The Block sender permission (PermissionToBlockSender) allows users to add the message sender to the Blocked Senders list in their mailbox.
If the Block sender permission is enabled:
 Block sender is available on the Quarantine page and in the message details in quarantine.
Block sender is available on the Quarantine page and in the message details in quarantine.Blocked sender is available in quarantine notifications.
For this permission to work correctly in quarantine notifications, users need to be enabled for remote PowerShell. For instructions, see Enable or disable access to Exchange Online PowerShell.
If the Block sender permission is disabled, users can't block senders from quarantine or in quarantine notifications (the action isn't available).
For more information about the Blocked Senders list, see Block messages from someone and Use Exchange Online PowerShell to configure the safelist collection on a mailbox.
Tip
The organization can still receive mail from the blocked sender. Messages from the sender are delivered to user Junk Email folders or to quarantine depending on the policy precedence as described in User allows and blocks. To delete messages from the sender upon arrival, use mail flow rules (also known as transport rules) to Block the message.
Delete permission
The Delete permission (PermissionToDelete) allows users to delete their own messages from quarantine (messages where they're a recipient).
If the Delete permission is enabled:
 Delete is available on the Quarantine page and in the message details in quarantine.
Delete is available on the Quarantine page and in the message details in quarantine.- No effect in quarantine notifications. Deleting a quarantined message from the quarantine notification is not possible.
If the Delete permission is disabled, users can't delete their own messages from quarantine (the action isn't available).
Tip
Admins can find out who deleted a quarantined message by searching the admin audit log. For instructions, see Find who deleted a quarantined message. Admins can use message trace to find out what happened to a released message if the original recipient can't find it.
Preview permission
The Preview permission (PermissionToPreview) allows users to preview their messages in quarantine.
If the Preview permission is enabled:
 Preview message is available on the Quarantine page and in the message details in quarantine.
Preview message is available on the Quarantine page and in the message details in quarantine.- No effect in quarantine notifications. Previewing a quarantined message from the quarantine notification isn't possible. The Review message action in quarantine notifications takes users to the details flyout of the message in quarantine where they can preview the message.
If the Preview permission is disabled, users can't preview their own messages in quarantine (the action isn't available).
Allow recipients to release a message from quarantine permission
Note
As explained previously, this permission isn't honored for messages that were quarantined as malware by anti-malware or Safe Attachments policies, or as high confidence phishing by anti-spam policies. If the quarantine policy gives users this permission, users are instead allowed to request the release of their quarantined malware or high confidence phishing messages.
The Allow recipients to release a message from quarantine permission (PermissionToRelease) allows users to release their own quarantined messages without admin approval.
If the Allow recipients to release a message from quarantine permission is enabled:
 Release is available on the Quarantine page and in the message details in quarantine.
Release is available on the Quarantine page and in the message details in quarantine.- Release is available in quarantine notifications.
If the Allow recipients to release a message from quarantine permission is disabled, users can't release their own messages from quarantine or in quarantine notifications (the action isn't available).
Allow recipients to request a message to be released from quarantine permission
The Allow recipients to request a message to be released from quarantine permission (PermissionToRequestRelease) allows users to request the release of their quarantined messages. Messages are released only after an admin approves the request.
If the Allow recipients to request a message to be released from quarantine permission is enabled:
 Request release is available on the Quarantine page and in the message details in quarantine.
Request release is available on the Quarantine page and in the message details in quarantine.- Request release is available in quarantine notifications.
If the Allow recipients to request a message to be released from quarantine permission is disabled, users can't request the release of their own messages from quarantine or in quarantine notifications (the action isn't available).