Microsoft Defender for Office 365 Plan 2 support for Microsoft Teams
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
With the increased use of collaboration tools like Microsoft Teams, the possibility of malicious attacks using chat messages has also increased. Microsoft Defender for Office 365 already provides time of click protection for URLs and files in Teams messages through Safe Links for Microsoft Teams and Safe Attachments for SharePoint, OneDrive, and Microsoft Teams.
In Microsoft 365 E5 and Defender for Office 365 Plan 2, we've extended Teams protection with a set of capabilities that are designed to disrupt the attack chain:
Report suspicious Teams messages: Users can report malicious Teams messages. Depending on the reported message settings in the organization, the reported messages go to the specified reporting mailbox, to Microsoft, or both. For more information, see User reported settings in Teams.
Zero-hour auto protection (ZAP) for Teams: ZAP is an existing email protection feature that detects and neutralizes spam, phishing, and malware messages after delivery by moving the messages to the Junk Email folder or quarantine.
ZAP for Teams quarantines messages in Teams chats or channels that are found to be malware or high confidence phishing. For more information, see Zero-hour auto purge (ZAP) in Microsoft Teams.
Instructions to configure ZAP for Teams protection are in the next section.
Teams messages in quarantine: As with email messages that are identified as malware or high confidence phishing, only admins are able to manage Teams messages that are quarantined by ZAP for Teams by default. For more information, see Manage quarantined Teams messages.
The Teams message entity panel is a single place to store all Teams message metadata for immediate SecOps review. Any threats coming from Teams chats, group chats, meeting chats, and other channels can be found in one place as soon as they're assessed. For more information, see The Teams message entity panel in Microsoft Defender for Office 365 Plan 2.
Attack simulation training using Teams messages: To ensure users are resilient to phishing attacks in Microsoft Teams, admins can configure phishing simulations using Teams messages instead of email messages. For more information, see Microsoft Teams in Attack simulation training.
Configure ZAP for Teams protection in Defender for Office 365 Plan 2
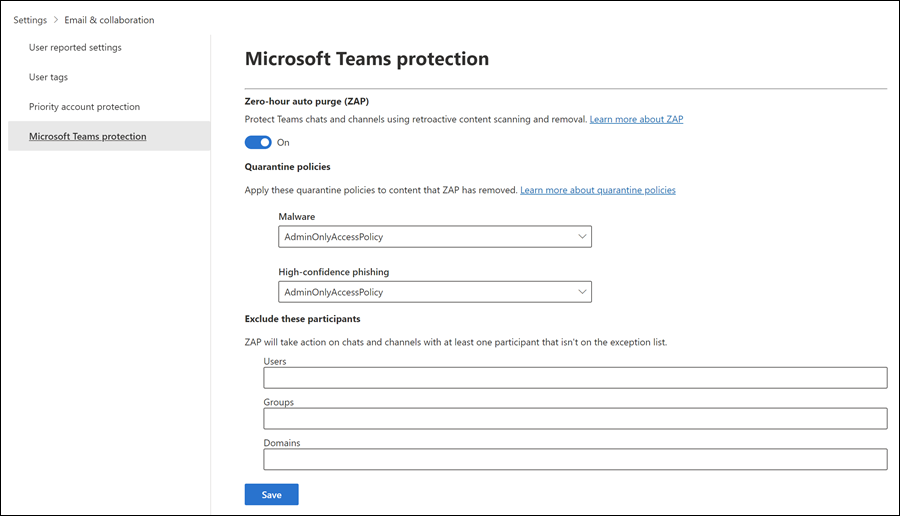
In the Microsoft Defender portal at https://security.microsoft.com, go to Settings > Email & collaboration > Microsoft Teams protection. Or, to go directly to the Microsoft Teams protection page, use https://security.microsoft.com/securitysettings/teamsProtectionPolicy.
On the Microsoft Teams protection page, verify the toggle in the Zero-hour auto purge (ZAP) section:
- Turn on ZAP for Teams: Verify the toggle is On
 .
. - Turn off ZAP for Teams: Slide the toggle to Off
 .
.
- Turn on ZAP for Teams: Verify the toggle is On
When the toggle is On
 , use the remaining settings on the page to customize ZAP for Teams protection:
, use the remaining settings on the page to customize ZAP for Teams protection:Quarantine policies section: You can select the existing quarantine policy to use for messages that are quarantined by ZAP for Teams protection as Malware or High confidence phishing. Quarantine policies define what users are able to do to quarantined messages, and whether users receive quarantine notifications. For more information, see Anatomy of a quarantine policy.
Note
Quarantine notifications are disabled in the policy named AdminOnlyAccessPolicy. To notify recipients that have messages quarantined as malware or high confidence phishing, create or use an existing quarantine policy where quarantine notifications are turned on. For instructions, see Create quarantine policies in the Microsoft Defender portal.
Exclude these participants section: Specify the Users, Groups, or Domains to exclude from ZAP for Teams protection. Exclusions matter for message recipients, not message senders. For more information, see Zero-hour auto purge (ZAP) in Microsoft Teams.
You can use an exception only once, but the exception can contain multiple values:
- Multiple values of the same exception use OR logic (for example, <recipient1> or <recipient2>). If the recipient matches any of the specified values, ZAP for Teams protection isn't applied to them.
- Different types of exceptions use OR logic (for example, <recipient1> or <member of group1> or <member of domain1>). If the recipient matches any of the specified exception values, ZAP for Teams protection isn't applied to them.
When you're finished on the Microsoft Teams protection page, select Save.
Use Exchange Online PowerShell to configure ZAP for Teams protection
If you'd rather use Exchange Online PowerShell to configure ZAP for Microsoft Teams, the following cmdlets are involved:
- The Teams protection policy (*-TeamsProtectionPolicy cmdlets) turns ZAP for Teams on and off and specifies the quarantine policies to use for malware and high confidence phishing detections.
- The Teams protection policy rule (*-TeamsProtectionPolicyRule cmdlets) identifies the Teams protection policy and specifies any exceptions for ZAP for Teams protection (users, groups, or domains).
Notes:
- There's only one Teams protection policy in an organization. By default, that policy is named Teams Protection Policy.
- Using the New-TeamsProtectionPolicy cmdlet is meaningful only if there's no Teams protection policy in the organization (the Get-TeamsProtectionPolicy cmdlet returns nothing). You can run the cmdlet without error, but no new Teams protection policies are created if one already exists.
- You can't remove an existing Teams protection policy or Teams protection policy rule (there's no Remove-TeamsProtectionPolicy or Remove-TeamsProtectionPolicyRule cmdlet).
- By default, there's no Teams protection policy rule (the Get-TeamsProtectionPolicyRule cmdlet returns nothing). Specifying quarantine policies or exceptions for ZAP for Teams in the Defender portal creates the rule automatically. Or, you can use the New-TeamsProtectionPolicyRule cmdlet to create the rule in PowerShell if it doesn't already exist.
Use PowerShell to view the Teams protection policy and Teams protection policy rule
To view the important values in Teams protection policy and Teams protection policy rule, run the following commands:
Get-TeamsProtectionPolicy | Format-List Name,ZapEnabled,HighConfidencePhishQuarantineTag,MalwareQuarantineTag
Get-TeamsProtectionPolicyRule | Format-List Name,TeamsProtectionPolicy,ExceptIfSentTo,ExceptIfSentToMemberOf,ExceptIfRecipientDomainIs
For detailed syntax and parameter information, see Get-TeamsProtectionPolicy and Get-TeamsProtectionPolicyRule.
Use PowerShell to modify the Teams protection policy
To modify the Teams protection policy, use the following syntax:
Set-TeamsProtectionPolicy -Identity "Teams Protection Policy" [-ZapEnabled <$true | $false>] [-HighConfidencePhishQuarantineTag "<QuarantinePolicyName>"] [-MalwareQuarantineTag "<QuarantinePolicyName>"]
This example enables ZAP for Teams and changes the quarantine policy that's used for high confidence phishing detections:
Set-TeamsProtectionPolicy -Identity "Teams Protection Policy" -ZapEnabled $true -HighConfidencePhishQuarantineTag AdminOnlyWithNotifications
For detailed syntax and parameter information, see Set-TeamsProtectionPolicy.
Use PowerShell to create the Teams protection policy rule
By default, there's no Teams protection policy rule, because there are no default exceptions for ZAP for Teams.
To create a new Teams protection policy rule, use the following syntax:
New-TeamsProtectionPolicyRule -Name "Teams Protection Policy Rule" -TeamsProtectionPolicy "Teams Protection Policy" [-ExceptIfSentTo <UserEmail1,UserEmail2,...UserEmailN>] [-ExceptIfSentToMemberOf <GroupEmail1,GroupEmail2,...GroupEmailN>] [-ExceptIfRecipientDomainIs <Domain1,Domain2,...DomainN>]
Important
As explained previously in this article, multiple exception types (users, groups, and domains) use OR logic, not AND.
This example creates the Teams protection policy rule with members of the group named Research excluded from ZAP for Teams protection.
New-TeamsProtectionPolicyRule -Name "Teams Protection Policy Rule" -TeamsProtectionPolicy "Teams Protection Policy" -ExceptIfSentToMemberOf research@contoso.onmicrosoft.com
For detailed syntax and parameter information, see New-TeamsProtectionPolicyRule.
Use PowerShell to modify the Teams protection policy rule
If the Teams protection policy rule already exists (the Get-TeamsProtectionPolicyRule cmdlet returns output), use the following syntax to modify the rule:
Set-TeamsProtectionPolicyRule -Identity "Teams Protection Policy Rule" [-ExceptIfSentTo <UserEmailAddresses | $null>] [-ExceptIfSentToMemberOf <GroupEmailAddresses | $null>] [-ExceptIfRecipientDomainIs <Domains | $null>]
Notes:
- For information about the syntax for adding, removing, and replacing all values for the ExceptIfSentTo, ExceptIfSentToMemberOf, and ExceptIfRecipientDomainIs parameters, see the parameter descriptions in Set-TeamsProtectionPolicyRule.
- To empty the ExceptIfSentTo, ExceptIfSentToMemberOf, or ExceptIfRecipientDomainIs parameters, use the value
$null.
This example modifies the existing Teams protection policy rule by excluding recipients in the domains research.contoso.com and research.contoso.net from ZAP for Teams protection.
Set-TeamsProtectionPolicyRule -Identity "Teams Protection Policy Rule" -ExceptIfRecipientDomainIs research.contoso.com,research.contoso.net
For detailed syntax and parameter information, see Set-TeamsProtectionPolicyRule.