Payload automations for Attack simulation training
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
In Attack simulation training in Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2, payload automations (also known as payload harvesting) collect information from real-world phishing attacks that were reported by users in your organization. You can specify the conditions to look for in phishing attacks (for example, recipients, social engineering technique, or sender information).
Payload automation mimics the messages and payloads from the attack and stores them as custom payloads with identifiers in the payload name. You can then use the harvested payloads in simulations or automations to automatically launch harmless simulations to targeted users.
For details about how payload automations are collected, see the Appendix section at the end of this article.
For getting started information about Attack simulation training, see Get started using Attack simulation training.
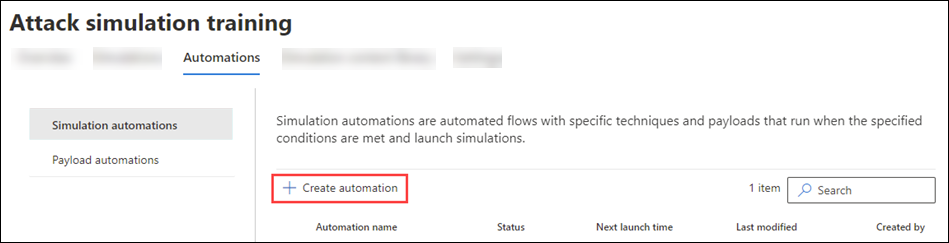
To see any existing payload automations that you created, open the Microsoft Defender portal at https://security.microsoft.com, go to Email & collaboration > Attack simulation training > Automations tab > and then select Payload automations. To go directly to the Automations tab where you can select Payload automations, use https://security.microsoft.com/attacksimulator?viewid=automations.
The following information is shown for each payload automation. You can sort the payload automations by clicking on an available column header.
- Automation name
- Type: The value is Payload.
- Items collected
- Last modified
- Status: The value is Ready or Draft.
Tip
To see all columns, you likely need to do one or more of the following steps:
- Horizontally scroll in your web browser.
- Narrow the width of appropriate columns.
- Remove columns from the view.
- Zoom out in your web browser.
Create payload automations
To create a payload automation, do the following steps:
In the Microsoft Defender portal at https://security.microsoft.com/, go to Email & collaboration > Attack simulation training > Automations tab > Payload automations. To go directly to the Automations tab where you can select Payload automations, use https://security.microsoft.com/attacksimulator?viewid=automations.
On the Payload automations page, select
 Create automation to start the new payload automation wizard.
Create automation to start the new payload automation wizard.Note
At any point after you name the payload automation during the new payload automation wizard, you can select Save and close to save your progress and continue configuring the payload automation later. The incomplete payload automation has the Status value Draft in Payload automations on the Automations tab. You can pick up where you left off by selecting the payload automation and clicking
 Edit automation.
Edit automation.Currently, payload harvesting isn't enabled in GCC environments due to data gathering restrictions.
On the Automation name page, configure the following settings:
- Name: Enter a unique, descriptive name for the payload automation.
- Description: Enter an optional detailed description for the payload automation.
When you're finished on the Automation name page, select Next.
On the Run conditions page, select the conditions of the real phishing attack that determines when the automation runs.
Select
 Add condition and then select from one of the following conditions:
Add condition and then select from one of the following conditions:- No. of users targeted in the campaign: In the boxes that appear, configure the following settings:
- Equal to, Less than, Greater than, Less than or equal to, or Greater than or equal to.
- Enter value: The number of users that were targeted by the phishing campaign.
- Campaigns with a specific phish technique: In the box that appears, select one of the available values:
- Credential Harvest
- Malware Attachment
- Link in Attachment
- Link to Malware
- How-to Guide
- Specific sender domain: In the box that appears, enter a sender email domain value (for example, contoso.com).
- Specific sender name: In the box that appears, enter a sender name value.
- Specific sender email: In the box that appears, enter a sender email address.
- Specific user and group recipients: In the box that appears, start typing the name or email address of the user or group. When it appears, select it.
You can use each condition only once. Multiple conditions use AND logic (<Condition1> and <Condition2>).
To add another condition, select
 Add condition.
Add condition.To remove a condition after you add it, select
 .
.When you're finished on the Run conditions page, select Next.
- No. of users targeted in the campaign: In the boxes that appear, configure the following settings:
On the Review automation page, you can review the details of your payload automation.
You can select Edit in each section to modify the settings within the section. Or you can select Back or the specific page in the wizard.
When you're finished on the Review automation page, select Submit.
On the New automation created page, you can use the links to turn on the payload automation or go to the Simulations page.
When you're finished, select Done.
Back on Payload automations in the Automations tab, the payload automation that you created is now listed with the Status value Ready.
Turn payload automations on or off
You can turn on or turn off payload automations with the Status value Ready. You can't turn on or turn off incomplete payload automations with the Status value Draft.
To turn on a payload automation, select it from the list by clicking the check box next to the name. Select the ![]() Turn on action that appears, and then select Confirm in the dialog.
Turn on action that appears, and then select Confirm in the dialog.
To turn off a payload automation, select it from the list by clicking the check box next to the name. Select the ![]() Turn off action that appears, and then select Confirm in the dialog.
Turn off action that appears, and then select Confirm in the dialog.
Modify payload automations
You can only modify payload automations with the Status value Draft or that are turned off.
To modify an existing payload automation on the Payload automations page, do one of the following steps:
- Select the payload automation from the list by selecting the check box next to the name. Select the
 Edit automation action that appears.
Edit automation action that appears. - Select the payload automation from the list by clicking anywhere in the row except the check box. In the details flyout that opens, on the General tab, select Edit in the Name, Description, or Run conditions sections.
The payload automation wizard opens with the settings and values of the selected payload automation. The steps are the same as described in the Create payload automations section.
Remove payload automations
To remove a payload automation, select the payload automation from the list by clicking the check box. Select the ![]() Delete action that appears, and then select Confirm in the dialog.
Delete action that appears, and then select Confirm in the dialog.
View payload automation details
For payload automations with the Status value Ready, select the payload from the Payload automations page by clicking anywhere in the row other than the check box next to the name. The details flyout that opens contains the following information:
The payload automation name and the number of items collected.
General tab:
- Last modified
- Type: The value is Payload.
- Name, Description, and Run conditions sections: Select Edit to open the payload automation wizard on the related page.
Run history tab: This tab is available only for payload automations with the Status value Ready.
Shows information about the run history of simulations that used the payload automation.
Tip
To see details about other payload automations without leaving the details flyout, use  Previous item and Next item at the top of the flyout.
Previous item and Next item at the top of the flyout.
Appendix
Payload automation relies on email messages that are identified as campaigns by Defender for Office 365:
Admins marking messages as phishing doesn't result in payload harvesting.
Payload automation requires access to the raw payload, which can include user reported messages that meet the following criteria:
- The message was delivered to the Inbox (false negative).
- The user reported the message as phishing.
- The reported message was submitted to Microsoft (directly by the user or by an admin from the Submissions portal), and Microsoft determined that the message was phishing.
Eligible payloads are harvested if the messages meet the criteria of the payload automation as described earlier in this article (Step 4 in Create payload automations).
Related links
Get started using Attack simulation training