View and organize the Microsoft Defender for Endpoint Incidents queue
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
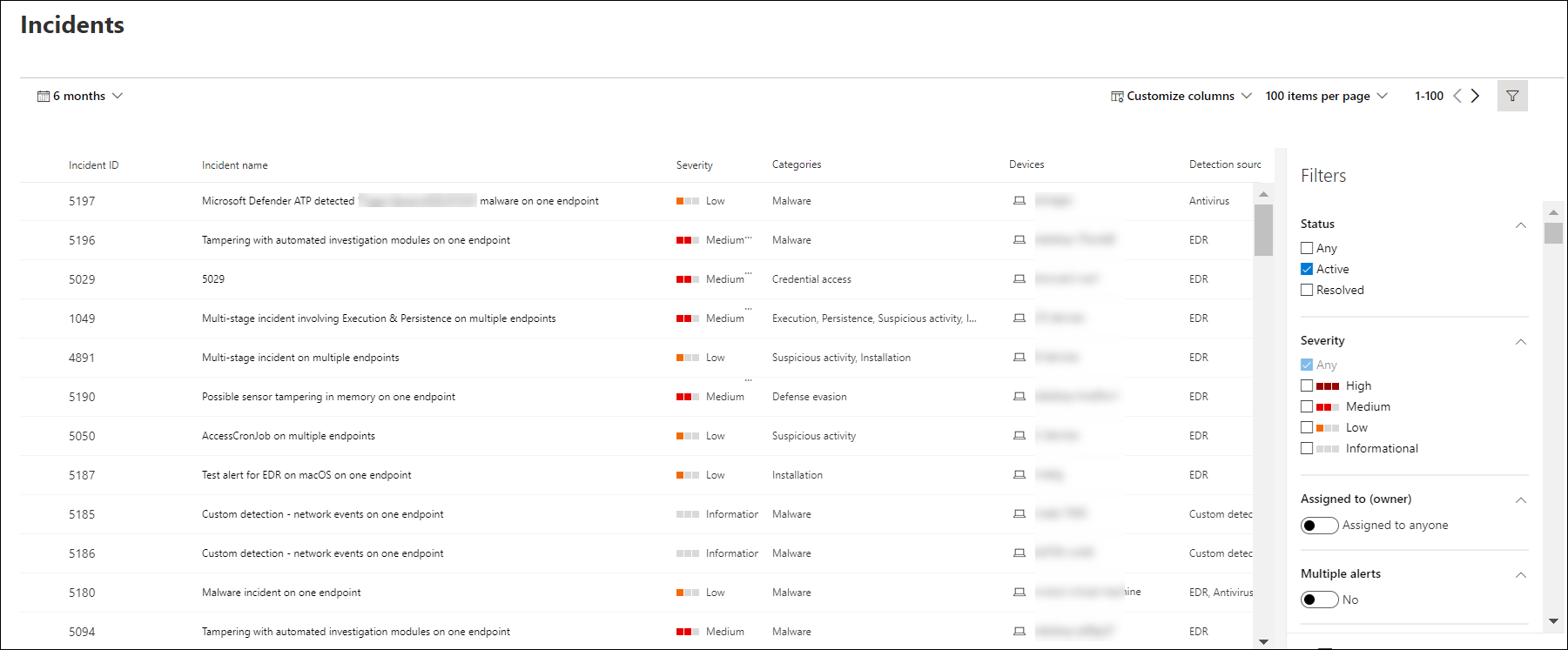
The Incidents queue shows a collection of incidents that were flagged from devices in your network. It helps you sort through incidents to prioritize and create an informed cybersecurity response decision.
By default, the queue displays incidents seen in the last six months, with the most recent incident showing at the top of the list, helping you see the most recent incidents first.
There are several options you can choose from to customize the Incidents queue view.
On the top navigation you can:
- Customize columns to add or remove columns
- Modify the number of items to view per page
- Select the items to show per page
- Batch-select the incidents to assign
- Navigate between pages
- Apply filters
- Customize and apply date ranges
Tip
Defender Boxed, a series of cards showcasing your organization's security successes, improvements, and response actions in the past six months/year, appears for a limited time during January and July of each year. Learn how you can share your Defender Boxed highlights.
Sort and filter the incidents queue
You can apply the following filters to limit the list of incidents and get a more focused view.
Severity
| Incident severity | Description |
|---|---|
| High (Red) |
Threats often associated with advanced persistent threats (APT). These incidents indicate a high risk due to the severity of damage they can inflict on devices. |
| Medium (Orange) |
Threats rarely observed in the organization, such as anomalous registry change, execution of suspicious files, and observed behaviors typical of attack stages. |
| Low (Yellow) |
Threats associated with prevalent malware and hack-tools that don't necessarily indicate an advanced threat targeting the organization. |
| Informational (Grey) |
Informational incidents might not be considered harmful to the network but might be good to keep track of. |
Assigned to
You can choose to filter the list by selecting assigned to anyone or ones that are assigned to you.
Category
Incidents are categorized based on the description of the stage by which the cybersecurity kill chain is in. This view helps the threat analyst to determine priority, urgency, and corresponding response strategy to deploy based on context.
Status
You can choose to limit the list of incidents shown based on their status to see which ones are active or resolved.
Data sensitivity
Use this filter to show incidents that contain sensitivity labels.
Incident naming
To understand the incident's scope at a glance, incident names are automatically generated based on alert attributes such as the number of endpoints affected, users affected, detection sources, or categories.
For example: Multi-stage incident on multiple endpoints reported by multiple sources.
Note
Incidents that existed prior to the rollout of automatic incident naming retains their original name.
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.