Data Loss Prevention policy reference
Microsoft Purview Data Loss Prevention (DLP) policies have many components to configure. To create an effective policy, you need to understand what the purpose of each component is and how its configuration alters the behavior of the policy. This article provides a detailed anatomy of a DLP policy.
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Before you begin
If you're new to Microsoft Purview DLP, here's a list of the core articles you'll need as you implement DLP:
- Administrative units
- Learn about Microsoft Purview Data Loss Prevention - the article introduces you to the data loss prevention discipline and Microsoft's implementation of DLP
- Plan for data loss prevention (DLP) - by working through this article you will:
- Data Loss Prevention policy reference - this article that you're reading now introduces all the components of a DLP policy and how each one influences the behavior of a policy
- Design a DLP policy - this article walks you through creating a policy intent statement and mapping it to a specific policy configuration.
- Create and Deploy data loss prevention policies - This article presents some common policy intent scenarios that you map to configuration options. It also walks you through configuring those options.
- Learn about investigating data loss prevention alerts - This article introduces you to the lifecycle of alerts from creation, through final remediation and policy tuning. It also introduces you to the tools you use to investigate alerts.
Also, you need to be aware of the following constraints of the platform:
- Maximum number of MIP + MIG policies in a tenant: 10,000
- Maximum size of a DLP policy (100 KB)
- Maximum number of DLP rules:
- In a policy: Limited by the size of the policy
- In a tenant: 600
- Maximum size of an individual DLP rule: 100 KB (102,400 characters)
- GIR evidence limit: 100, with each SIT evidence, in proportion of occurrence
- Maximum size of text that can be extracted from a file for scanning: The first 2 MB of extractable text
- Regex size limit for all matches predicted: 20 KB
- Policy name length limit: 64 characters
- Policy rule length limit: 64 characters
- Comment length limit: 1,024 characters
- Description length limit: 1,024 characters
Policy templates
DLP policy templates are sorted into four categories:
- policies that can detect and protect types of Financial information.
- policies that can detect and protect types of Medical and health information.
- policies that can detect and protect types of Privacy information.
- A Custom policy template that you can use to build your own policy if none of the others meet your organization's needs.
The following table lists all policy templates and the sensitive information types (SIT) that they cover.
Policy scoping
See, Administrative units to make sure you understand the difference between an unrestricted admin and an administrative unit restricted admin.
DLP policies are scoped at two different levels. The first level applies unrestricted admin scope policies to all of the following in your organization (depending on the locations that are selected) or to subgroups of your organization, called Administrative Unit restricted policies:
- users
- groups
- distribution groups
- accounts
- sites
- cloud app instances
- on-premises repositories
- Fabric and Power BI workspaces
At this level, an administrative unit restricted admin will only be able to pick from the administrative units that they're assigned to.
The second level of DLP policy scoping is by the locations that DLP supports. At this level, both unrestricted and administrative unit restricted administrators see only the users, distribution groups, groups, and accounts that were included in the first level of policy scoping and that are available for that location.
Unrestricted policies
Unrestricted policies are created and managed by users in these role groups:
- Compliance administrator
- Compliance data administrator
- Information Protection
- Information Protection Admin
- Security administrator
See, the Permissions article for more details.
Unrestricted administrators can manage all policies and see all the alerts and events that flow from policy matches into the Alerts dashboard and DLP Activity Explorer.
Administrative unit restricted policies
Administrative units are subsets of your Microsoft Entra ID and are created for the purposes of managing collections of users, groups, distribution groups, and accounts. These collections are typically created along business group lines or geopolitical areas. Administrative units have a delegated administrator who is associated with an administrative unit in the role group. These are called administrative unit restricted admins.
DLP supports associating policies with administrative units. See Administrative units for implementation details in the Microsoft Purview compliance portal. Administrative unit admins need to be assigned to one of the same roles or role groups as administrators of unrestricted DLP policies in order to create and manage DLP policies for their administrative unit.
| DLP Administrative Role Group | Can |
|---|---|
| Unrestricted administrator | - create and scope DLP policies to entire organization - edit all DLP policies - create and scope DLP policies to administrative units - view all alerts and events from all DLP policies |
| Administrative Unit Restricted administrator - must be a member of/assigned to a role group/role that can administer DLP |
- create and scope DLP policies only to the administrative unit that they're assigned to - edit DLP policies that are associated to their administrative unit - view alerts and events only from the DLP policies that are scoped to their administrative unit |
Locations
A DLP policy can find and protect items that contain sensitive information across multiple locations.
Note
Endpoint DLP cannot detect the label from another tenant in a document.
| Location | Supports Administrative Units | Include/Exclude scope | Data state | Additional prerequisites |
|---|---|---|---|---|
| Exchange Online | Yes | - Distribution groups - Security groups - Non-email enabled security groups - Dynamic distribution lists - Microsoft 365 groups (Group members only, not the group as an entity) |
data-in-motion | No |
| SharePoint Online | No | Sites | data-at-rest data-in-use |
No |
| OneDrive | Yes | - Distribution groups - Security groups - Non-email enabled security groups - Microsoft 365 groups (Group members only, not the group as an entity) |
data-at-rest data-in-use |
No |
| Teams chat and channel messages | Yes | - Distribution groups - Security groups - Mail-enabled security groups - Microsoft 365 groups (Group members only, not the group as an entity) |
data-in-motion data-in-use |
See Scope of DLP protection |
| Instances | No | Cloud app instance | data-at-rest | - Use data loss prevention policies for non-Microsoft cloud apps |
| Devices | Yes | - Distribution groups - Security groups - Non-email enabled security groups - Microsoft 365 groups (Group members only, not the group as an entity) |
data-in-use data-in-motion |
- Learn about Endpoint data loss prevention - Get started with Endpoint data loss prevention - Configure device proxy and internet connection settings for Information Protection |
| On-premises repositories (file shares and SharePoint) | No | Repository | data-at-rest | - Learn about the data loss prevention on-premises repositories - Get started with the data loss prevention on-premises repositories |
| Fabric and Power BI | No | Workspaces | data-in-use | No |
| Third-party apps | None | No | No | No |
| Microsoft 365 Copilot (preview) | No | account or distribution group | data-at-rest data-in-use |
- Only available in the Custom policy templace - |
Exchange location scoping
If you choose to include specific distribution groups in Exchange, the DLP policy is scoped only to the emails sent by members of that group. Similarly, excluding a distribution group excludes all the emails sent by the members of that distribution group from policy evaluation.
| Sender is | Recipient is | Resultant behavior |
|---|---|---|
| In scope | N/A | Policy is applied |
| Out of scope | In scope | Policy isn't applied |
Exchange location scope calculation
Here's an example of how Exchange location scope is calculated:
Say you have four users in your org and two distribution groups that you'll use for defining Exchange location inclusion and exclusion scopes. Group membership is set up like this:
| Distribution Group | Membership |
|---|---|
| Group1 | User1, User2 |
| Group2 | User2, User3 |
| No group | User4 |
| Include setting | Exclude setting | Policy applies to | Policy doesn't apply to | Explanation of behavior |
|---|---|---|---|---|
| All | None | All senders in the Exchange org (User1, User2, User3, User4) | N/A | When neither are defined, all senders are included |
| Group1 | None | Member senders of Group1 (User1, User2) | All senders who aren't members of Group1 (User3, User4) | When one setting is defined and the other isn't, the defined setting is used |
| All | Group2 | All senders in the Exchange org who aren't members of Group2 (User1, User4) | All senders who are members of Group2 (User2, User3) | When one setting is defined and the other isn't, the defined setting is used |
| Group1 | Group2 | User1 | User2, User3, User4 | Exclude overrides include |
You can choose to scope a policy to the members of distribution lists, dynamic distribution groups, and security groups. A DLP policy can contain no more than 50 such inclusions and exclusions.
OneDrive location scoping
When scoping a policy for OneDrive locations, in addition to applying your DLP policies to all users and groups in your organization, you can limit the scope of a policy to specific users and groups. DLP supports scoping policies to up to 100 individual users.
For instance, if you want to include more than 100 users, you must first put those users in distribution groups or security groups, as appropriate. You can then scope your policy to up to 50 groups.
In some cases, you might want to apply a policy to one or two groups, plus two or three individual users who don't belong to either of those groups. Here, the best practice is to put those two or three individuals into a group of their own. This is the only way to make sure that the policy is scoped to all intended users.
The reason for this is that, when you list only users, DLP adds all of the users specified to the policy scope. Similarly, when you add only groups, DLP adds all the members of all the groups to the policy scope.
Say you have the following groups and users:
| Distribution Group | Membership |
|---|---|
| Group1 | User1, User2 |
| Group2 | User2, User3 |
If you limit the scope of a policy to only users or only groups, the DLP applies the policy to users as illustrated in the following table:
| Specified scope | DLP Scope evaluation behavior | Users in scope |
|---|---|---|
| (Users only) User1 User2 |
DLP takes the union of the specified users | User1, User2 |
| (Groups only) Group1 Group2 |
DLP takes the union of the specified groups | User1, User2, User3 |
However, when users and groups are mixed in the scoping configuration, things get complicated. Here's why: DLP only scopes policies to users to the intersection of the listed groups and users.
DLP uses the following order of operations when determining which users and groups to include in the scope:
- Evaluate the union of group membership
- Evaluate the union of users
- Evaluate the intersection of group members and users, that is, where the results overlap
It then applies the scope of the policy to the intersection of group members and users.
Let's extend our example, working with the same set of groups, and let's add User4, who isn't in a group:
| Distribution Group | Membership |
|---|---|
| Group1 | User1, User2 |
| Group2 | User2, User3 |
| No group | User 4 |
The following table explains how policy scoping works in cases where users and groups are both included in the scoping instructions.
| Specified scope | DLP Scope evaluation behavior | Users in scope |
|---|---|---|
| Group1 Group2 User3 User4 |
First evaluation: Union of groups: (Group1 + Group2) = User1, User2, User3 Second evaluation: Union of users: (User3 + User4) = User3, User4 Third evaluation: Intersection of groups and Users (the overlap): (Group1 + Group2) = User1, User2, User3 (User3 + User4) = User3, User4 |
User3 (User3 is the only user that appears in the results of both the first and second evaluations.) |
| Group1 Group2 User1 User3 User4 |
First evaluation: Union of groups: (Group1 + Group2) = User1, User2, User3 Second evaluation: Union of users: (User1 + User3 + User4) = User1, User3, User4 Third evaluation: Intersection of groups and Users (the overlap): (Group1 + Group2) = User1, User3 (User1 + User3, User4) = User1, User3, User4 |
User1, User3 (These are the only users that appear in the results of both the first and second evaluations.) |
Location support for how content can be defined
DLP policies detect sensitive items by matching them to a sensitive information type (SIT), or to a sensitivity label or a retention label. Each location supports different methods of defining sensitive content. How content can be defined when you combine locations in a policy, can change from how it can be defined when limited to a single location.
Important
When you select multiple locations for a policy, a "no" value for a content definition category takes precedence over "yes" value. For example, when you select SharePoint sites only, the policy will support detecting sensitive items by one or more of SIT, by sensitivity label or by retention label. But, when you select SharePoint sites and Teams chat and channel messages locations, the policy will only support detecting sensitive items by SIT.
| Location | Content can be defined by SIT | Content can be defined sensitivity label | Content can be defined by retention label |
|---|---|---|---|
| Exchange email online | Yes | Yes | No |
| SharePoint in Microsoft 365 sites | Yes | Yes | Yes |
| OneDrive for work or school accounts | Yes | Yes | Yes |
| Teams Chat and Channel messages | Yes | No | No |
| Devices | Yes | Yes | No |
| Instances | Yes | Yes | Yes |
| On-premises repositories | Yes | Yes | No |
| Fabric and Power BI | Yes | Yes | No |
| Microsoft 365 Copilot (preview) | No | Yes | No |
DLP supports using trainable classifiers as a condition to detect sensitive documents. Content can be defined by trainable classifiers in Exchange, SharePoint sites, OneDrive accounts, Teams Chat and Channels, and Devices. For more information, see Trainable Classifiers.
Note
DLP supports detecting sensitivity labels on emails and attachments. For more information, see Use sensitivity labels as conditions in DLP policies.
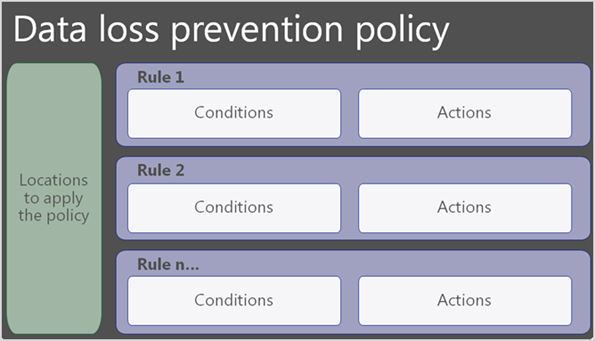
Rules
Rules are the business logic of DLP policies. They consist of:
- Conditions that when matched, trigger the policy Actions
- User notifications to inform your users when they're doing something that triggers a policy and help educate them on how your organization wants sensitive information treated
- User Overrides when configured by an admin, allow users to selectively override a blocking action
- Incident reports that notify admins and other key stakeholders when a rule match occurs
- Additional options which define the priority for rule evaluation and can stop further rule and policy processing.
A policy contains one or more rules. Rules are executed sequentially, starting with the highest-priority rule in each policy.
How DLP classification works
DLP evaluates an item for sensitive information when the item is created, read, or modified. However, events such as "DLP Rule Matched" only appear in Audit Log or Activity Explorer when a user attempts to egress the sensitive item. Egress activities that users attempt are:
Upload to cloud
Print
Copy to removable media
Copy to network share
Copy to clipboard
Transfer using bluetooth
File accessed by unallowed app
Paste to browser
Transfer using remote desktop
An items that is created, read, or modified will match a DLP rule and policy on the client if the conditions and user activity are met. This will be audited as file activity (FileRead, FileRenamed, etc).
If an activity is met, then a DLP rule match event will appear in activity explorer as a 'DLP Rule Matched' event. An event describing the mode of egress will also be generated.
Policies take actions and actions are different from conditions. A rule can match on a file even if no actions are performed.
The priority by which rules are evaluated and applied
Hosted service locations
For the hosted service locations, like Exchange, SharePoint, and OneDrive, each rule is assigned a priority in the order in which it's created. This means that the rule created first has first priority, the rule created second has second priority, and so on.
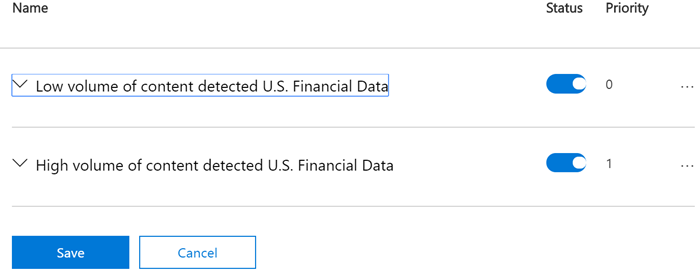
When content is evaluated against rules, the rules are processed in priority order. If content matches multiple rules, the first rule evaluated that has the most restrictive action is enforced. For example, if content matches all of the following rules, Rule 3 is enforced because it's the highest priority, most restrictive rule:
- Rule 1: only notifies users
- Rule 2: notifies users, restricts access, and allows user overrides
- Rule 3: notifies users, restricts access, and doesn't allow user overrides
- Rule 4: restricts access
Rules 1, 2, and 4 would be evaluated, but not applied. In this example, matches for all of the rules are recorded in the audit logs and shown in the DLP reports, even though only the most restrictive rule is applied.
You can use a rule to meet a specific protection requirement, and then use a DLP policy to group together common protection requirements, such as all of the rules needed to comply with a specific regulation.
For example, you might have a DLP policy that helps you detect the presence of information subject to the Health Insurance Portability and Accountability Act (HIPAA). This DLP policy could help protect HIPAA data (the "what") across all SharePoint sites and all OneDrive sites (the "where") by finding any document containing this sensitive information that's shared with people outside your organization (the conditions) and then blocking access to the document and sending a notification (the actions). These requirements are stored as individual rules and grouped together as a DLP policy to simplify management and reporting.
For endpoints
When an item matches multiple DLP rules, DLP goes uses through a complex algorithm to decide which actions to apply. Endpoint DLP applies the aggregate or sum of most restrictive actions. DLP uses these factors when making the calculation.
Policy priority order When an item matches multiple policies and those policies have identical actions, the actions from the highest priority policy is applied.
Rule priority order When an item matches multiple rules in a policy and those rules have identical actions, the actions from the highest priority rule is applied.
Mode of the policy When an item matches multiple policies and those policies have identical actions, the actions from all policies that are in Turn it on state (enforce mode) are applied preferentially over the policies in Run the policy in simulation mode with policy tips and Run the policy in simulation mode state.
action When an item matches multiple policies and those policies differ in actions, the aggregate or sum of the most restrictive actions are applied.
Authorization groups configuration When an item matches multiple policies and those policies differ in action, the aggregate, or sum, of the most restrictive actions are applied.
override options When an item matches multiple policies and those policies differ in the override option, actions are applied in this order:
No override > Allow override
Here are scenarios that illustrate the runtime behavior. For the first three scenarios, you have three DLP policies configured like this:
| Policy name | Condition to match | Action | Policy priority |
|---|---|---|---|
| ABC | Content contains credit card number | Block print, audit all other user egress activities | 0 |
| MNO | Content contains credit card number | Block copy to USB, audit all other user egress activities | 1 |
| XYZ | Content contains U.S. social security number | Block copy to clipboard, audit all other user egress activities | 2 |
Item contains credit card numbers
An item on a monitored device contains credit card numbers, so it matches policy ABC and policy MNO. Both ABC and MNO are in Turn it on mode.
| Policy | Cloud egress action | Copy to clipboard action | Copy to USB action | Copy to network share action | Unallowed apps action | Print action | Copy via Bluetooth action | Copy to remote desktop action |
|---|---|---|---|---|---|---|---|---|
| ABC | Audit | Audit | Audit | Audit | Audit | Block | Audit | Audit |
| MNO | Audit | Audit | Block | Audit | Audit | Audit | Audit | Audit |
| Actions applied at runtime | Audit | Audit | Block | Audit | Audit | Block | Audit | Audit |
Item contains credit card numbers and U.S. social security numbers
An item on a monitored device contains credit card numbers and U.S. social security numbers, so this item matches policy ABC, policy MNO, and policy XYZ. All three policies are in Turn it on mode.
| Policy | Cloud egress action | Copy to clipboard action | Copy to USB action | Copy to network share action | Unallowed apps action | Print action | Copy via Bluetooth action | Copy to remote desktop action |
|---|---|---|---|---|---|---|---|---|
| ABC | Audit | Audit | Audit | Audit | Audit | Block | Audit | Audit |
| MNO | Audit | Audit | Block | Audit | Audit | Audit | Audit | Audit |
| XYZ | Audit | Block | Audit | Audit | Audit | Block | Audit | Audit |
| Actions applied at runtime | Audit | Block | Block | Audit | Audit | Block | Audit | Audit |
Item contains credit card numbers, different policy state
An item on a monitored device contains credit card number, so it matches policy ABC and policy MNO. Policy ABC is in Turn it on mode and policy MNO is in Run the policy in simulation mode state.
| Policy | Cloud egress action | Copy to clipboard action | Copy to USB action | Copy to network share action | Unallowed apps action | Print action | Copy via Bluetooth action | Copy to remote desktop action |
|---|---|---|---|---|---|---|---|---|
| ABC | Audit | Audit | Audit | Audit | Audit | Block | Audit | Audit |
| MNO | Audit | Audit | Block | Audit | Audit | Audit | Audit | Audit |
| Actions applied at runtime | Audit | Audit | Audit | Audit | Audit | Block | Audit | Audit |
Item contains credit card numbers, different override configuration
An item on a monitored device contains credit card number, so it matches policy ABC and policy MNO. Policy ABC is in Turn it on state and policy MNO is in Turn it on state. They have different Override actions configured.
| Policy | Cloud egress action | Copy to clipboard action | Copy to USB action | Copy to network share action | Unallowed apps action | Print action | Copy via Bluetooth action | Copy to remote desktop action |
|---|---|---|---|---|---|---|---|---|
| ABC | Audit | Audit | Block with override | Audit | Audit | Block | Audit | Audit |
| MNO | Audit | Audit | Block without override | Audit | Audit | Audit | Audit | Audit |
| Actions applied at runtime | Audit | Audit | Block without override | Audit | Audit | Block | Audit | Audit |
Item contains credit card numbers, different authorization groups configuration
An item on a monitored device contains credit card number, so it matches policy ABC and policy MNO. Policy ABC is in Turn it on state and policy MNO is in Turn it on state. They have different authorization group actions configured.
| Policy | Cloud egress action | Copy to clipboard action | Copy to USB action | Copy to network share action | Unallowed apps action | Print action | Copy via Bluetooth action | Copy to remote desktop action |
|---|---|---|---|---|---|---|---|---|
| ABC | Audit | Audit | Auth group A - Block | Audit | Audit | Auth group A - Block | Audit | Audit |
| MNO | Audit | Audit | Auth group A - Block with override | Audit | Audit | Auth group B - block | Audit | Audit |
| Actions applied at runtime | Audit | Audit | Auth group A - Block | Audit | Audit | Auth group A - Block, Auth group B - Block | Audit | Audit |
Conditions
Conditions are where you define what you want the rule to look for and the context in which those items are being used. They tell the rule: when you find an item that looks like this and is being used like that—it's a match and the rest of the actions in the policy should be taken on it. You can use conditions to assign different actions to different risk levels. For example, sensitive content shared internally might be lower risk and require fewer actions than sensitive content shared with people outside the organization.
Note
Users who have non-guest accounts in a host organization's Active Directory or Microsoft Entra tenant are considered as people inside the organization.
Content contains
All locations support the Content contains condition. You can select multiple instances of each content type and further refine the conditions by using the Any of these (logical OR) or All of these (logical AND) operators:
The rule will only look for the presence of any sensitivity labels and retention labels you pick.
SITs have a predefined confidence level which you can alter if needed. For more information, see More on confidence levels.
Important
SITs have two different ways of defining the maximum unique instance count parameters. To learn more, see Instance count supported values for SIT.
Adaptive Protection in Microsoft Purview
Adaptive protection integrates Microsoft Purview Insider Risk Management risk profiles into DLP policies so that DLP can help protect against dynamically identified risky behaviors. When configured in insider risk management, the Insider risk level for Adaptive Protection is will show up as condition for Exchange Online, Devices, and Teams locations. Refer to Learn about Adaptive Protection in Data Loss Prevention for more details.
Conditions that Adaptive Protection supports
- Insider risk level for Adaptive Protection is...
with these values:
- Elevated risk level
- Moderate risk level
- Minor risk level
Condition context
The available context options change depending on which location you choose. If you select multiple locations, only the conditions that the locations have in common are available.
Conditions Exchange supports
- Content contains
- Insider risk level for Adaptive Protection is
- Content is not labeled
- Content is shared from Microsoft 365
- Content is received from
- Sender IP address is
- Header contains words or phrases
- Sender AD Attribute contains words or phrases
- Content character set contains words
- Header matches patterns
- Sender AD Attribute matches patterns
- Recipient AD Attribute contains words or phrases
- Recipient AD Attribute matches patterns
- Recipient is member of
- Document property is
- Any email attachment's content could not be scanned
- Document or attachment is password protected
- Has sender overridden the policy tip
- Sender is a member of
- Any email attachment's content didn't complete scanning
- Recipient address contains words
- File extension is
- Recipient domain is
- Recipient is
- Sender is
- Sender domain is
- Recipient address matches patterns
- Document name contains words or phrases
- Document name matches patterns
- Subject contains words or phrases
- Subject matches patterns
- Subject or body contains words or phrases
- Subject or body matches patterns
- Sender address contains words
- Sender address matches patterns
- Document size equals or is greater than
- Document content contains words or phrases
- Document content matches patterns
- Message size equals or is greater than
- Message type is
- Message importance is
Tip
For more information on the conditions that Exchange supports, including PowerShell values, see: Data loss prevention Exchange conditions and actions reference.
Conditions SharePoint supports
- Content contains
- Content is shared from Microsoft 365
- Document property is
- Document could not be scanned
- Document or attachment is password protected
- Document didn't complete scanning
- File extension is
- Document name contains words or phrases
- Document size equals or is greater than
- Document created by
Conditions OneDrive accounts support
- Content contains
- Content is shared from Microsoft 365
- Document property is
- Document could not be scanned
- Document or attachment is password protected
- Document didn't complete scanning
- File extension is
- Document name contains words or phrases
- Document size equals or is greater than
- Document created by
- Document is shared
Conditions Teams chat and channel messages support
- Content contains
- Insider risk level for Adaptive Protection is
- Content is shared from Microsoft 365
- Recipient domain is -Recipient is
- Sender is
- Sender domain is
Conditions supported for Endpoints
Content contains: Specifies content to be detected. For details on supported file types, see Files scanned for content.
Content is not labeled: Detects content that doesn't have a sensitivity label applied. To help ensure only supported file types are detected, you should use this condition with the File extension is or File type is conditions. PDF and Office files are supported:
File Type Format Monitored file extensions Word processing Word, PDF .doc, .docx, .docm, .dot, dotx, .dotm, .docb, .pdf Spreadsheet Excel, CSV, TSV .xls, .xlsx, .xlt, .xlm, .xlsm, xltx, xltm, xlsb, .xlw, .csv, .tsv Presentation PowerPoint .ppt, .pptx, .pos, .pps, .pptm, .potx, .potm, .ppam, .ppsx Document could not be scanned: Applies to files that can't be scanned for one of the following reasons:
- File contains one or more transient text-extraction errors
- File is password-protected
- File size exceeds the supported limit (Maximum file sizes: 64 MB for uncompressed files; 256 MB for compressed files)
Document name contains words or phrases: Detects documents with file names that contain any of the words or phrases you specify, for example:
file,credit card,patent, etc.Document name matches patterns: Detects documents where the file name matches specific patterns. To define the patterns, use wild cards. For information on regex patterns, see the Regular Expression documentation here.
Document or attachment is password protected: Detects only protected files that are open. The following files are supported:
- Archive files (ZIP, .7z, RAR)
- Office files
- PDFs
- Symantec PGP encrypted files
Document size equals or is greater than: Detects documents with file sizes that are equal to or greater than the specified value. DLP only supports content inspection for files less than 64 MB.
Important
We recommend setting this condition to detect items that are larger than 10KB
File type is: Detects the following file types:
File type Apps Monitored file extensions Word processing Word, PDF doc, .docx, .docm, .dot, dotx, .dotm, .docb, .pdf Spreadsheet Excel, CSV, TSV .xls, .xlsx, .xlt, .xlm, .xlsm, xltx, xltm, xlsb, .xlw, .csv, .tsv Presentation PowerPoint .ppt, .pptx, .pos, .pps, .pptm, .potx, .potm, .ppam, .ppsx Email Outlook .msg Important
The file extensions and file types options cannot be used as conditions in the same rule. If you want to use them as conditions in the same policy, they must be in separate rules.
To use the File type is condition, you must have one of the following versions of Windows:
Windows Endpoints (X64):
- Windows 10 (21H2, 22H2)
Windows Endpoints (ARM64):
- Windows 11 (21H2, 22H2)
File extension is: In addition to detecting sensitive information in files with the same extensions as those covered by the File type is condition, you can use the File extension is condition to detect sensitive information in files with any file extension you need to monitor. To do so, add the necessary file extensions, separated by commas to a rule in your policy. The File extension is condition is supported only for those versions of Windows that support the File type is condition.
Warning
Including any of the following file extensions in your policy rules might significantly increase the CPU load: .dll, .exe, .mui, .ost, .pf, .pst.
Scanning did not complete: Applies when the scanning of a file started, but stopped before the entire file was scanned. The primary reason for an incomplete scan is that extracted text within the file exceeds the maximum size allowed. (Maximum sizes for extracted text: Uncompressed files: The first 4 MB of extractable text; Compressed files: N=1000 / Extraction Time = 5 minutes.)
Document property is: Detects documents with custom properties matching specified values. For example:
Department = 'Marketing',Project = 'Secret'. To specify multiple values for a custom property, use double quotes. For example, "Department: Marketing, Sales". Supported file types are Office and PDF:File Type Format Monitored file extensions Word processing Word, PDF .doc, .docx, .docm, .dot, dotx, .dotm, .docb, .pdf Spreadsheet Excel, CSV, TSV .xls, .xlsx, .xlt, .xlm, .xlsm, xltx, xltm, xlsb, .xlw, .csv, .tsv Presentation PowerPoint .ppt, .pptx, .pos, .pps, .pptm, .potx, .potm, .ppam, .ppsx The user accessed a sensitive website from Microsoft Edge: For more information, see Scenario 6 Monitor or restrict user activities on sensitive service domains (preview).
Insider risk level for Adaptive Protection is: Detects the insider risk level.
See also: Endpoint activities you can monitor and take action on.
Operating system requirements for five conditions
- Document could not be scanned
- Document name contains words or phrases
- Document name matches patterns
- Document size equals or is greater than
- Scanning did not complete
To use any of these conditions, your endpoint devices must be running one of the following operating systems:
Windows 11 23H2: December 4, 2023—KB5032288 (OS Builds 22621.2792 and 22631.2792) Preview
Windows 11 22H2: December 4, 2023—KB5032288 (OS Builds 22621.2792 and 22631.2792) Preview - Microsoft Support
Windows 11 21H2: December 12, 2023—KB5033369 (OS Build 22000.2652) - Microsoft Support
Windows 10 22H2: November 30, 2023—KB5032278 (OS Build 19045.3758) Preview - Microsoft Support
Windows 10 21H2: November 30, 2023—KB5032278 (OS Build 19045.3758) Preview - Microsoft Support
Windows Server 2022/2019: November 14, 2023—KB5032198 (OS Build 20348.2113) - Microsoft Support (or later)
Operating system requirements for Condition 'Document Property is'
Windows 11: February 29, 2024—KB5034848 (OS Builds 22621.3235 and 22631.3235) Preview - Microsoft Support (or later)
Windows 10: February 29, 2024—KB5034843 (OS Build 19045.4123) Preview - Microsoft Support (or later)
Important
For information about the Adobe requirements for using Microsoft Purview Data Loss Prevention (DLP) features with PDF files, see this article from Adobe: Microsoft Purview Information Protection Support in Acrobat.
Conditions Instances supports
- Content contains
- Content is shared from Microsoft 365
Conditions On-premises repositories support
- Content contains
- File extension is
- Document property is
Conditions Fabric and Power BI support
- Content contains
Conditions Microsoft 365 Copilot (preview) supports
- Content contains (sensitvity labels)
Condition groups
Sometimes you need a rule to identify only one thing, such as all content that contains a U.S. Social Security Number, which is defined by a single SIT. However, in many scenarios where the types of items you're trying to identify are more complex and therefore harder to define, more flexibility in defining conditions is required.
For example, to identify content subject to the U.S. Health Insurance Act (HIPAA), you need to look for:
Content that contains specific types of sensitive information, such as a U.S. Social Security Number or Drug Enforcement Agency (DEA) Number.
AND
Content that's more difficult to identify, such as communications about a patient's care or descriptions of medical services provided. Identifying this content requires matching keywords from large keyword lists, such as the International Classification of Diseases (ICD-9-CM or ICD-10-CM).
You can identify this type of data by grouping conditions and using logical operators (AND, OR) between the groups.
For the U.S. Health Insurance Act (HIPAA), conditions are grouped like this:

The first group contains the SITs that identify an individual and the second group contains the SITs that identify medical diagnosis.
Conditions can be grouped and joined by boolean operators (AND, OR, NOT) so that you define a rule by stating what should be included and then defining exclusions in a different group joined to the first by a NOT. To learn more about how Purview DLP implements booleans and nested groups see, Complex rule design.
DLP platform limitations for conditions
| Predicate | Workload | Limit | Cost of Evaluation |
|---|---|---|---|
| Content Contains | EXO/SPO/ODB | 125 SITs per rule | High |
| Content is shared from Microsoft 365 | EXO/SPO/ODB | - | High |
| Sender IP address is | EXO | Individual range length <= 128; Count <= 600 | Low |
| Has sender overridden the policy tip | EXO | - | Low |
| Sender is | EXO | Individual email length <= 256; Count <= 600 | Medium |
| Sender is a member of | EXO | Count <= 600 | High |
| Sender domain is | EXO | Domain name length <= 67; Count <= 600 | Low |
| Sender address contains words | EXO | Individual word length <= 128; Count <= 600 | Low |
| Sender address matches patterns | EXO | Regex length <= 128 char; Count <= 600 | Low |
| Sender AD attribute contains words | EXO | Individual word length <= 128; Count <= 600 | Medium |
| Sender AD attribute matches patterns | EXO | Regex length <= 128 char; Count <= 600 | Medium |
| Content of email attachment(s) can't be scanned | EXO | Supported file types | Low |
| Incomplete scan of email attachment content | EXO | Size > 1 MB | Low |
| Attachment is password-protected | EXO | File types: Office files, .PDF, .ZIP, and 7z | Low |
| Attachment's file extension is | EXO/SPO/ODB | Count <= 600 per rule | High |
| Recipient is a member of | EXO | Count <= 600 | High |
| Recipient domain is | EXO | Domain name length <= 67; Count <= 5000 | Low |
| Recipient is | EXO | Individual email length <= 256; Count <= 600 | Low |
| Recipient address contains words | EXO | Individual word length <= 128; Count <= 600 | Low |
| Recipient address matches patterns | EXO | Count <= 300 | Low |
| Document name contains words or phrases | EXO | Individual word length <= 128; Count <=600 | Low |
| Document Name matches patterns | EXO | Regex length <= 128 char; Count <= 300 | Low |
| Document property is | EXO/SPO/ODB | - | Low |
| Document size equals or is greater than | EXO | - | Low |
| Subject contains words or phrases | EXO | Individual word length <= 128; Count <= 600 | Low |
| Header contains words or phrases | EXO | Individual word length <= 128; Count <= 600 | Low |
| Subject or body contains words or phrases | EXO | Individual word length <= 128; Count <= 600 | Low |
| Content character set contains words | EXO | Count <= 600 | Low |
| Header matches patterns | EXO | Regex length <= 128 char; Count <= 300 | Low |
| Subject matches patterns | EXO | Regex length <= 128 char; Count <= 300 | Low |
| Subject or body matches patterns | EXO | Regex length <= 128 char; Count <= 300 | Low |
| Message type is | EXO | - | Low |
| Message size over | EXO | - | Low |
| With importance | EXO | - | Low |
| Sender AD attribute contains words | EXO | Each attribute key value pair: has Regex length <= 128 char; Count <= 600 | Medium |
| Sender AD attribute matches patterns | EXO | Each attribute key value pair: has Regex length <= 128 char; Count <= 300 | Medium |
| Document contains words | EXO | Individual word length <= 128; Count <= 600 | Medium |
| Document matches patterns | EXO | Regex length <= 128 char; Count <= 300 | Medium |
Actions
Any item that makes it through the conditions filter will have any actions that are defined in the rule applied to it. You'll have to configure the required options to support the action. For example, if you select Exchange with the Restrict access or encrypt the content in Microsoft 365 locations action, you need to choose from these options:
- Block users from accessing shared SharePoint, OneDrive, and Teams content
- Block everyone. Only the content owner, last modifier, and site admin will continue to have access
- Block only people from outside your organization. Users inside your organization will continue to have access.
- Encrypt email messages (applies only to content in Exchange)
The actions that are available in a rule depend on the locations that have been selected. The available actions for each individual location are listed below.
Important
For SharePoint and OneDrive locations, documents will be proactively blocked right after detection of sensitive information (regardless of whether the document is shared or not) for all external users; internal users will continue to have access to the document.
Supported actions: Exchange
When DLP policy rules are applied in Exchange, they may be halting, non-halting, or neither. Most of the rules that Exchange supports are non-halting. Non-halting actions are evaluated and applied immediately before processing the subsequent rules and policies, as described in the Hosted service locations earlier in this article.
However, when a halting action is triggered by a DLP policy rule, Purview stops processing any subsequent rules. For instance, when the Restrict access or encrypt the content in Microsoft 365 locations action is triggered, no further rules or policies are processed.
In the event that an action is neither halting nor non-halting, Purview waits for the result of the action to occur before continuing. So, when an outgoing email triggers the Forward the message for approval to sender's manager action, Purview waits to get the manager's decision on whether or not the email may be sent. If the manager approves, the action behaves as a non-halting action and the subsequent rules are processed. In contrast, if the manager rejects sending the email, Forward the message for approval to sender's manager behaves as a halting action and blocks sending the email; no subsequent rules or polices are processed.
The following table lists the actions that Exchange supports, and indicates whether they are halting or non-halting.
| Action | Halting / Non-halting |
|---|---|
| Restrict access or encrypt the content in Microsoft 365 locations | Halting |
| Set headers | Non-halting |
| Remove header | Non-halting |
| Redirect the message to specific users | Non-halting |
| Forward the message for approval to sender's manager | Neither |
| Forward the message for approval to specific approvers | Neither |
| Add recipient to the To box | Non-halting |
| Add recipient to the Cc box | Non-halting |
| Add recipient to the Bcc box | Non-halting |
| Add the sender's manager as recipient | Non-halting |
| Remove message encryption and rights protection | Non-halting |
| Prepend Email Subject | Non-halting |
| Add HTML Disclaimer | Non-halting |
| Modify Email Subject | Non-halting |
| Deliver the message to the hosted quarantine | Halting |
| Apply branding to encrypted messages | Non-halting |
Tip
For the Apply branding to encrypted messages action, if you already have Microsoft Purview Message Encryption implemented, the templates automatically show up in the drop down list. If you want to implement Microsoft Purview Message Encryption, see Add your organization's brand to your Microsoft Purview Message Encryption encrypted messages for background on message encryption and how to create and configure your branding templates.
For more information on the actions that Exchange supports, including PowerShell values, see: Data loss prevention Exchange conditions and actions reference.
Supported actions: SharePoint
- Restrict access or encrypt the content in Microsoft 365 locations
Supported actions: OneDrive
- Restrict access or encrypt the content in Microsoft 365 locations
Supported actions: Teams Chat and Channel Messages
- Restrict access or encrypt the content in Microsoft 365 locations
Supported actions: Devices
You can tell DLP to Allow, Audit only, Block with override, or Block (the actions) these user activities for onboarded Windows devices.
You can tell DLP to Audit only, Block with override, or Block (the actions) these user activities for onboarded macOS devices.
- Restrict access or encrypt content in Microsoft 365 locations
- Audit or restrict activities when users access sensitive sites in Microsoft Edge browsers on Windows devices
- Audit or restrict activities on devices
- Service domain and browser activities
- File activities for all apps
- Restricted app activities
- File activities for apps in restricted app groups (preview)
Restrict access or encrypt content in Microsoft 365 locations
Use this to block users from receiving email, or accessing shared SharePoint, OneDrive, Teams files and Power BI items. This action can block everyone or block only people who are outside your organization.
Audit or restrict activities when users access sensitive sites in Microsoft Edge browsers on Windows devices
Use this action to control when users attempt to:
| Activity | Description/options |
|---|---|
| Print the site | Detects when users try to print a protected site from an onboarded device. |
| Copy data from the site | Detects when users try to copy data from a protected site from an onboarded device. |
| Save the site as local files (Save-As) | Detects when users try to save a protected site as local files from an onboarded device. |
Audit or restrict activities on devices
Use this to restrict user activities by Service domain and browser activities, File activities for all apps, Restricted app activities. To use Audit or restrict activities on devices, you have to configure options in DLP settings and in the policy in which you want to use them. See, Restricted apps and app groups for more information.
DLP rules with the action Audit or restrict activities on devices can have Block with override configured. When this rule is applied to a file, any attempt to perform a restricted action on the file is blocked. A notification is displayed with the option to override the restriction. If the user chooses to override, the action is permitted for a period of 1 minute, during which the user can retry the action without restriction. The exception to this behavior is when a sensitive file is dragged and dropped into Edge, which will immediately attach the file if the rule is overridden.
Service domain and browser activities
When you configure the Allow/Block cloud service domains and the Unallowed browsers list (see Browser and domain restrictions to sensitive data) and a user attempts to upload a protected file to a cloud service domain or access it from an unallowed browser, you can configure the policy action to Audit only, Block with override, or Block the activity.
| Activity | Description/options |
|---|---|
| Upload to a restricted cloud services domain or access from an unallowed app | Detects when protected files are blocked or allowed to be uploaded to cloud service domains. See, Browser and domain restrictions to sensitive data and Scenario 6 Monitor or restrict user activities on sensitive service domains). |
| Paste to supported browsers | Detects when users paste sensitive information into a text field or web form using Microsoft Edge, Google Chrome (with Microsoft Purview extension) or Mozilla Firefox (with Microsoft Purview extension). Evaluation is independent of the classification of the source file. For more information, see: Endpoint activities you can monitor and take action on. |
File activities for all apps
With the File activities for all apps option, you select either Don't restrict file activities or Apply restrictions to specific activities. When you select Apply restrictions to specific activities, the actions that you select here are applied when a user has accessed a DLP protected item.
| Activity | Description/options |
|---|---|
| Copy to clipboard | Detects when protected files are copied to the clipboard on an onboarded device. For more information, see Endpoint activities you can monitor and take action on and Copy to clipboard behavior |
| Copy to a removable device | Detects when protected files are copied or moved from an onboarded device to a removable USB device. For more information, see Removable USB device groups. |
| Copy to a network share | Detects when protected files are copied or moved from an onboarded device to any network share. For more information, see Endpoint activities you can monitor and take action on and Network share coverage and exclusions. |
| Detects when a protected file is printed from an onboarded device. For more information, see Printer groups. | |
| Copy or move using unallowed Bluetooth app | Detects when a protected file is copied or moved from an onboarded Windows device using an unallowed Bluetooth app. For more information, see Unallowed Bluetooth apps. This isn't supported for macOS. |
| Copy or move using RDP | Detects when users copy or move protected files from an onboarded Windows device to another location using RDP. This isn't supported for macOS. |
Restricted app activities
Previously called Unallowed apps, restricted app activities are apps that you want to place restrictions on. You define these apps in a list in Endpoint DLP settings. When a user attempts to access a DLP protected file using an app that is on the list, you can either Audit only, Block with override, or Block the activity. DLP actions defined in Restricted app activities are overridden if the app is a member of restricted app group. Then the actions defined in the restricted app group are applied.
| Activity | Description/options |
|---|---|
| Access by restricted apps | Detects when unallowed apps try to access protected files on an onboarded Windows device. For more information, see Restricted apps and app groups. |
File activities for apps in restricted app groups (preview)
You define your restricted app groups in Endpoint DLP settings and add restricted app groups to your policies. When you add a restricted app group to a policy, you must select one of these options:
- Don't restrict file activity
- Apply restrictions to all activity
- Apply restrictions to specific activity
When you select either of the Apply restrictions options, and a user attempts to access a DLP protected file using an app that is in the restricted app group, you can either Audit only, Block with override, or Block by activity. DLP actions that you define here override actions defined in Restricted app activities and File activities for all apps for the app.
For more information, see Restricted apps and app groups.
Note
The devices location provides many sub-activities (conditions) and actions. To learn more, see Endpoint activities you can monitor and take action on.
Important
The Copy to clipboard condition detects when a user copies information from a protected file to the clipboard. Use Copy to clipboard to block, block with override, or audit when users copy information from a protected file.
The Paste to supported browsers condition detects when a user attempts to paste sensitive text into a text field or web form using Microsoft Edge, Google Chrome with Microsoft Purview extension, or Mozilla Firefox with Microsoft Purview extension regardless of where that information came from. Use Paste to supported browsers to block, block with override, or audit when users paste sensitive information into a text field or web form.
Instances actions
- Restrict access or encrypt the content in Microsoft 365 locations
- Restrict Third Party Apps
On-premises repositories actions
- Restrict access or remove on-premises files.
- Block people from accessing files stored in on-premises repositories
- Set permissions on the file (permissions inherited from the parent folder)
- Move file from where it's stored to a quarantine folder
See, DLP On-premises repository actions for full details.
Fabric and Power BI actions
- Notify users with email and policy tips
- Send alerts to Administrator
- Restrict access
Note
The restrict access action is only enforced on semantic models.
Microsoft 365 Copilot (preview) actions
- Exclude content in Copilot location
Actions available when you combine locations
If you select Exchange and any other single location for the policy to be applied to, the
- Restrict access or encrypt the content in Microsoft 365 locations and all actions for the non-Exchange location actions are available.
If you select two or more non-Exchange locations for the policy to be applied to, the
- Restrict access or encrypt the content in Microsoft 365 locations and all actions for non-Exchange locations actions will be available.
For example, if you select the Exchange and Devices locations, these actions will be available:
- Restrict access or encrypt the content in Microsoft 365 locations
- Audit or restrict activities on Windows devices
If you select Devices and Instances, these actions will be available:
- Restrict access or encrypt the content in Microsoft 365 locations
- Audit or restrict activities on Windows devices
- Restrict Third Party Apps
Whether an action takes effect or not depends on how you configure the mode of the policy. You can choose to run the policy in simulation mode with or without showing policy tip by selecting the Run the policy in simulation mode option. You choose to run the policy as soon as an hour after it's created by selecting the Turn it on right away option, or you can choose to just save it and come back to it later by selecting the Keep it off option.
DLP platform limitations for actions
| Action Name | Workload | Limits |
|---|---|---|
| Restrict access or encrypt content in Microsoft 365 | EXO/SPO/ODB | |
| Set headers | EXO | |
| Remove header | EXO | |
| Redirect the message to specific users | EXO | Total of 100 across all DLP rules. Can't be DL/SG |
| Forward the message for approval to sender's manager | EXO | Manager should be defined in AD |
| Forward the message for approval to specific approvers | EXO | Groups aren't supported |
| Add recipient to the To box | EXO | Recipient count <= 10; Can't be DL/SG |
| Add recipient to the Cc box | EXO | Recipient count <= 10; Can't be DL/SG |
| Add recipient to the Bcc box | EXO | Recipient count <= 10; Can't be DL/SG |
| Add the sender's manager as recipient | EXO | Manager attribute should be defined in AD |
| Apply HTML disclaimer | EXO | |
| Prepend subject | EXO | |
| Apply message encryption | EXO | |
| Remove message encryption | EXO | |
| (preview) Exclude content in Copilot location | Microsoft 365 Copilot (preview) | Only content in SharePoint and OneDrive for Business can be excluded from being processed by Microsoft 365 Copilot |
User notifications and policy tips
When a user attempts an activity on a sensitive item in a context that meets the conditions of a rule (for example, content such as an Excel workbook on a OneDrive site that contains personally identifiable information (PII) and is shared with a guest), you can let them know about it through user notification emails and in-context policy tip popups. These notifications are useful because they increase awareness and help educate people about your organization's DLP policies.
An Alert email, Incident Report email, and User Notification will only be sent once per document. If a document with a 'Content is Shared' predicate is shared twice, there will still be only one notification.
Important
- Notification emails are sent unprotected.
- Email notifications are only supported for the Microsoft 365 services.
Email notifications support by selected location
| Selected location | Email notifications supported |
|---|---|
| Devices | - Not supported |
| Exchange + Devices | - Supported for Exchange - Not supported for Devices |
| Exchange | - Supported |
| SharePoint + Devices | - Supported for SharePoint - Not supported for Devices |
| SharePoint | - Supported |
| Exchange + SharePoint | - Supported for Exchange - Supported for SharePoint |
| Devices + SharePoint + Exchange | - Not supported for Devices - Supported for SharePoint Supported for Exchange |
| Teams | - Not supported |
| OneDrive | - Supported for OneDrive for work or school - Not supported for Devices |
| Fabric and Power-BI | - Not supported |
| Instances | - Not supported |
| On-premises repositories | - Not supported |
| Exchange + SharePoint + OneDrive | - Supported for Exchange - Supported for SharePoint - Supported for OneDrive |
| M365 Copilot (preview) | - Not supported |
You can also give people the option to override the policy, so that they're not blocked if they have a valid business need or if the policy is detecting a false positive.
The user notifications and policy tips configuration options vary depending on the monitoring locations you've selected. If you selected:
- Exchange
- SharePoint
- OneDrive
- Teams Chat and Channel
- Instances
You can enable/disable user notifications for various Microsoft apps, see Data Loss Prevention policy tips reference.
You can also enable/disable notifications with a policy tip.
- email notifications to the user who sent, shared, or last modified the content OR
- notify specific people
Furthermore, you can customize the email text, subject, and the policy tip text.
For detailed information on customizing end user notification emails, see Custom email notifications.
If you selected Devices only, you'll get all the same options that are available for Exchange, SharePoint, OneDrive, Teams Chat and Channel, and Instances, plus the option to customize the notification title and content that appears on the Windows 10/11 device.
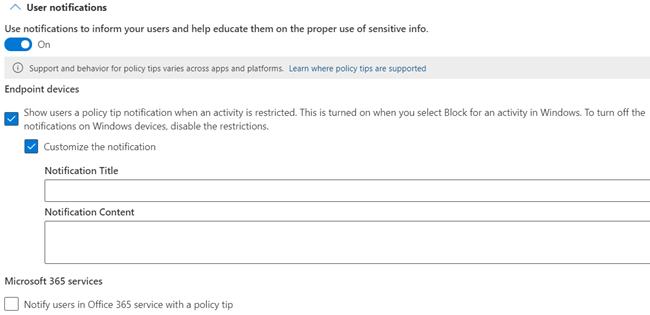
You can customize the title and body of text using the following parameters.
| Common name | Parameter | Example |
|---|---|---|
| file name | %%FileName%% | Contoso doc 1 |
| process name | %%ProcessName%% | Word |
| policy name | %%PolicyName%% | Contoso highly confidential |
| action | %%AppliedActions%% | pasting document content from the clipboard to another app |
Custom message character limits popups
User notifications are subject to the following character limits:
| Variable | Character Limit |
|---|---|
DLP_MAX-SIZE-TITLE |
120 |
DLP_MAX-SIZE-CONTENT |
250 |
DLP_MAX-SIZE-JUSTIFICATION |
250 |
%%AppliedActions%% substitutes these values into the message body:
| action common name | value substituted in for %%AppliedActions%% parameter |
|---|---|
| copy to removeable storage | writing to removable storage |
| copy to network share | writing to a network share |
| printing | |
| paste from clipboard | pasting from the clipboard |
| copy via bluetooth | transferring via Bluetooth |
| open with an unallowed app | opening with this app |
| copy to a remote desktop (RDP) | transferring to remote desktop |
| uploading to an unallowed website | uploading to this site |
| accessing the item via an unallowed browser | opening with this browser |
Using this customized text
%%AppliedActions%% File name %%FileName%% via %%ProcessName%% isn't allowed by your organization. Select 'Allow' if you want to bypass the policy %%PolicyName%%
produces this text in the customized notification:
pasting from the clipboard File Name: Contoso doc 1 via WINWORD.EXE isn't allowed by your organization. Select the 'Allow' button if you want to bypass the policy Contoso highly confidential
You can localize your custom policy tips by using the Set-DlpComplianceRule -NotifyPolicyTipCustomTextTranslations cmdlet.
Custom Policy Tips will show for the most restrictive rule, not necessarily the rule that is performing the restriction.
Note
User notifications and policy tips are not available for the On-premises location
Only the policy tip from the highest priority, most restrictive rule will be shown. For example, a policy tip from a rule that blocks access to content will be shown over a policy tip from a rule that simply sends a notification. This prevents people from seeing a cascade of policy tips.
To learn more about user notification and policy tip configuration and use, including how to customize the notification and tip text, see Send email notifications and show policy tips for DLP policies.
Policy tip references
Details on support for policy tips and notifications for different apps can be found here:
- Data loss prevention policy tip reference for Outlook for Microsoft 365
- Data loss prevention policy tip reference for Outlook on the Web
- Data loss prevention policy tip reference SharePoint in Microsoft 365 and OneDrive. web client
Blocking and notifications in SharePoint in Microsoft 365 and OneDrive
The following table shows the DLP blocking and notification behavior for policies that are scoped to SharePoint in Microsoft 365 and OneDrive. Note that this is not intended to be an exhaustive list, and there are additional settings that are not in scope for this article.
Note
The notification behavior described in this table may require the following settings to be enabled:
User notifications:
- On
- Notify users in Office 365 service with a policy tip
- Notify the user who sent, shared, or last modified the content
Incident reports:
- Send an alert to admins when a rule match occurs
- Send alert every time an activity matches the rule is selected
- Use email incident reports to notify you when a policy match occurs
| Conditions | Restrict access setting | Blocking and notification behavior |
|---|---|---|
| - Content is shared from Microsoft 365**- with people outside my organization | Not configured | User notifications, alerts, and incident reports will be sent only when a file is shared with an external user and an external user access the file |
| - Content is shared from Microsoft 365**- only with people inside my organization | Not configured | User notifications, alerts, and incident reports are sent when a file is uploaded |
| - Content is shared from Microsoft 365**- only with people inside my organization | - Restrict access or encrypt the content in Microsoft 365 locations - Block users from receiving email or accessing shared SharePoint, OneDrive, and Teams files -Block everyone |
- Access to sensitive files is blocked as soon as they're uploaded. - User notifications, alerts, and incident reports are sent when a file is uploaded |
| - Content is shared from Microsoft 365 - with people outside my organization | - Restrict access or encrypt the content in Microsoft 365 locations - Block users from receiving email or accessing shared SharePoint, OneDrive, and Teams files - Block only people outside your organization |
- Access to a sensitive file is blocked as soon as its uploaded, regardless of whether the document is shared or not for all external users. - If the sensitive information is added to a file after it is shared and accessed by a user outside the organization, then alerts and incident reports will be sent. - If the document contains sensitive information before it is uploaded, external sharing will be blocked proactively. Because external sharing in this scenario is blocked when the file is uploaded, no alerts or incident reports are sent. Suppression of the alerts and incident reports is designed to prevent a flood of alerts to the user for each blocked file. - Proactive blocking will show up as event in the Audit Log and Activity Explorer. |
| - Content is shared from Microsoft 365 - with people outside my organization | - Restrict access or encrypt the content in Microsoft 365 locations - Block users from receiving email or accessing shared SharePoint, OneDrive, and Teams files - Block everyone |
- When the first user outside the organization access the document, the event will cause the document to be blocked. - It is expected that for a short time, the document will be accessible by external users who have the link to the file. - User notifications, alerts, and incident reports are sent when a file is shared with an external user and an external user access that file |
| - Content is shared from Microsoft 365 | - Restrict access or encrypt the content in Microsoft 365 locations - Block only people who were given access to the content through the "Anyone with the link" option |
User notifications, alerts, and incident reports are sent when a file is uploaded |
Learn more URL
Users may want to learn why their activity is being blocked. You can configure a site or a page that explains more about your policies. When you select Provide a compliance URL for the end user to learn more about your organization's policies (only available for Exchange), and the user receives a policy tip notification in Outlook Win32, the Learn more link will point to the site URL that you provide. This URL has priority over the global compliance URL configured with Set-PolicyConfig -ComplainceURL.
Important
You must configure the site or page that Learn more points to from scratch. Microsoft Purview doesn't provide this functionality out of the box.
User overrides
The intent of User overrides is to give users a way to bypass, with justification, DLP policy blocking actions on sensitive items in Exchange, SharePoint, OneDrive, or Teams, so that they can continue their work. User overrides are enabled only when Notify users in Office 365 services with a policy tip is enabled, so user overrides go hand-in-hand with Notifications and Policy tips.
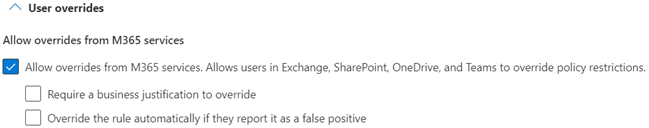
Note
User overrides are not available for the On-premises repositories location.
Typically, user overrides are useful when your organization is first rolling out a policy. The feedback that you get from any override justifications and identifying false positives helps in tuning the policy.
- If the policy tips in the most restrictive rule allow people to override the rule, then overriding this rule also overrides any other rules that the content matched.
Business justification X-Header
When a user overrides a block with override action on an email, the override option and the text that they provide are stored in the Audit log and in the email X-header. To view the business justification overrides, search the audit log for ExceptionInfo value for the details. Here's an example of the audit log values:
{
"FalsePositive"; false,
"Justification"; My manager approved sharing of this content",
"Reason"; "Override",
"Rules": [
"<message guid>"
]
}
If you have an automated process that makes use of the business justification values, the process can access that information programmatically in the email X-header data.
Note
The msip_justification values are stored in the following order:
False Positive; Recipient Entitled; Manager Approved; I Acknowledge; JustificationText_[free text].
Notice that the values are separated by semicolons. The maximum free text allowed is 500 characters.
Incident reports
When a rule is matched, you can send an Alert email to your compliance officer (or any people you choose) with details of the event and you can view them in the Microsoft Purview Data Loss Prevention Alerts dashboard and in the Microsoft 365 Defender portal. An alert includes information about the item that was matched, the actual content that matched the rule, and the name of the person who last modified the content.
In preview admin alert emails include details such as:
- The alert severity
- The time the alert occurred
- The activity.
- The sensitive data that was detected.
- The alias of the user whose activity triggered the alert.
- The policy that was matched.
- The alert ID
- The endpoint operation that was attempted if the Devices location is in the scope of the policy.
- The app that was being used.
- The device name, if the match occurred on an endpoint device.
DLP feeds incident information to other Microsoft Purview Information Protection services, like insider risk management. In order to get incident information to insider risk management, you must set the Incident reports severity level to High.
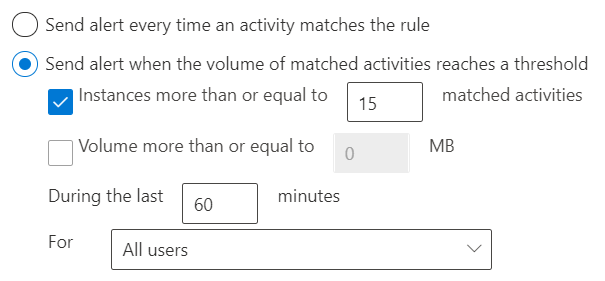
An Alert email, Incident Report email, and User Notification will only be sent once per document. If a document with a 'Content is Shared' predicate is shared twice, there will still be only one notification.
Alert types
Alerts can be sent every time an activity matches a rule, which can be noisy or they can be aggregated based on number of matches or volume of items over a set period of time. There are two types of alerts that can be configured in DLP policies.
Single-event alerts are typically used in policies that monitor for highly sensitive events that occur in a low volume, like a single email with 10 or more customer credit card numbers being sent outside your organization.
Aggregate-event alerts are typically used in policies that monitor for events that occur in a higher volume over a period of time. For example, an aggregate alert can be triggered when 10 individual emails each with one customer credit card number is sent outside your org over 48 hours.
Other alert options
When you select Use email incident reports to notify you when a policy match occurs you can choose to include:
- The name of the person who last modified the content.
- The types of sensitive content that matched the rule.
- The rule's severity level.
- The content that matched the rule, including the surrounding text.
- The item containing the content that matched the rule.
For more information on alerts, see:
- Alerts in DLP policies: Describes alerts in the context of a DLP policy.
- Get started with data loss prevention alerts: Covers the necessary liscensing, permissions, and prerequisites for DLP alerts and alert reference details.
- Create and deploy data loss prevention policies: Includes guidance on alert configuration in the context of creating a DLP policy.
- Learn about investigating data loss prevention alerts: Covers the various methods for investigating of DLP alerts.
- Investigate data loss incidents with Microsoft Defender XDR: How to investigate DLP alerts in Microsoft Defender portal.
Evidence collection for file activities on devices
If you've enabled Setup evidence collection for file activities on devices and added Azure storage accounts, you can select Collect original file as evidence for all selected file activities on Endpoint and the Azure storage account you want to copy the items to. You must also choose the activities you want to copy items for. For example, if you select Print but not Copy to a network share, then only items that are printed from monitored devices will be copied to the Azure storage account.
Additional options
If you have multiple rules in a policy, you can use the Additional options to control further rule processing if there's a match to the rule you're editing as well as setting the priority for evaluation of the rule. This is only supported for Exchange and Teams locations