Using hybrid Modern Authentication with Outlook for iOS and Android
The Outlook app for iOS and Android is designed as the best way to experience Microsoft 365 or Office 365 on your mobile device by using Microsoft services to help find, plan, and prioritize your daily life and work. Outlook provides the security, privacy, and support you need while protecting corporate data via capabilities such as Microsoft Entra Conditional Access and Intune app protection policies. The following sections provide an overview of the hybrid Modern Authentication architecture, the required prerequisites for its deployment, and how to securely deploy Outlook for iOS and Android for Exchange on-premises mailboxes.
Microsoft Cloud architecture for hybrid Exchange Server customers
Outlook for iOS and Android is a cloud-backed application. This characteristic indicates that your experience consists of a locally installed app powered by a secure and scalable service running in the Microsoft Cloud.
For Exchange Server mailboxes, Outlook for iOS and Android's architecture is built directly into the Microsoft Cloud, providing customers more benefits such as security, privacy, built-in compliance, and transparent operations that Microsoft commits to in the Microsoft Trust Center and Azure Trust Center.
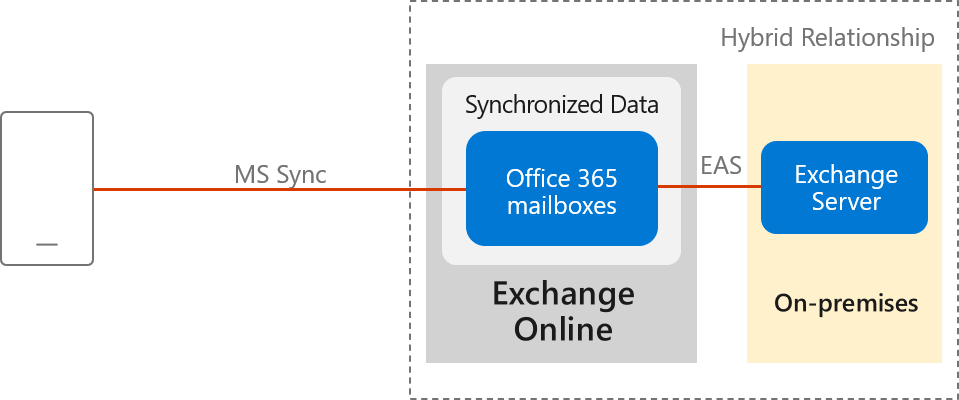
Within the Microsoft 365 or Office 365-based architecture, Outlook for iOS and Android uses the native Microsoft sync technology for data synchronization that is protected by a TLS-secured connection end-to-end, between Microsoft 365 or Office 365 and the app.
The Exchange ActiveSync (EAS) connection between Exchange Online and the on-premises environment enables synchronization of the users' on-premises data and includes four weeks of email, all calendar data, all contact data, and out-of-office status in your Exchange Online tenant. This data is removed automatically from Exchange Online after 30 days when the account is deleted in Microsoft Entra ID.
Data synchronization between the on-premises environment and Exchange Online happens independent of user behavior. This independency ensures that we can send new messages to the devices quickly.
Processing information in the Microsoft Cloud enables advanced features and capabilities, such as the categorization of email for the Focused Inbox, customized experience for travel and calendar, and improved search speed. Relying on the cloud for intensive processing and minimizing the resources required from users' devices enhances the app's performance and stability. Lastly, it allows Outlook to build features that work across all email accounts, regardless of the technological capabilities of the underlying servers (such as different versions of Exchange Server, Microsoft 365, or Office 365).
Specifically, this new architecture has the following improvements:
Enterprise Mobility + Security support: Customers can take advantage of Microsoft Enterprise Mobility + Security (EMS) including Microsoft Intune and Microsoft Entra ID P1 or P2, to enable conditional access and Intune app protection policies, which control and secure corporate messaging data on the mobile device.
Fully powered by Microsoft Cloud: The on-premises mailbox data is synchronized into Exchange Online, which provides the benefits of security, privacy, compliance, and transparent operations that Microsoft commits to in the Microsoft Trust Center.
OAuth protects users' passwords: Outlook uses hybrid Modern Authentication (OAuth) to protect users' credentials. Hybrid Modern Authentication provides Outlook with a secure mechanism to access the Exchange data without ever touching or storing a user's credentials. At sign-in, the user authenticates directly against an identity platform (either Microsoft Entra ID or an on-premises identity provider like ADFS) and receives an access token in return, which grants Outlook access to the user's mailbox or files. The service doesn't have access to the user's password at any point of time.
Provides Unique Device IDs: Each Outlook connection is uniquely registered in Microsoft Intune and can therefore be managed as a unique connection.
Unlocks new features on iOS and Android: This update enables the Outlook app to take advantage of native Microsoft 365 or Office 365 features that aren't supported in Exchange on-premises today, such as using full Exchange Online search and Focused Inbox. These features are available only when using Outlook for iOS and Android.
Note
Device management through the on-premises Exchange admin center (EAC) is not possible. Intune is required to manage mobile devices.
Data security, access, and auditing controls
With on-premises data being synchronized with Exchange Online, customers have questions about how the data is protected in Exchange Online. Encryption in the Microsoft Cloud discusses how BitLocker is used for volume-level encryption. Service Encryption with Microsoft Purview Customer Key is supported in the Outlook for iOS and Android architecture, but note that the user must have an Office 365 Enterprise E5 license (or the corresponding versions of those plans for Government or Education) to have an encryption policy assigned using the set-mailuser cmdlet.
By default, Microsoft engineers have zero standing administrative privileges and zero standing access to customer content in Microsoft 365 or Office 365. Administrative Access Controls discusses personnel screening, background checks, Lockbox and Customer Lockbox, and more.
ISO Audited Controls on Service Assurance documentation provides the status of audited controls from global information security standards and regulations that Microsoft 365 and Office 365 have implemented.
Connection flow
When Outlook for iOS and Android is enabled with hybrid Modern Authentication, the connection flow is as follows.
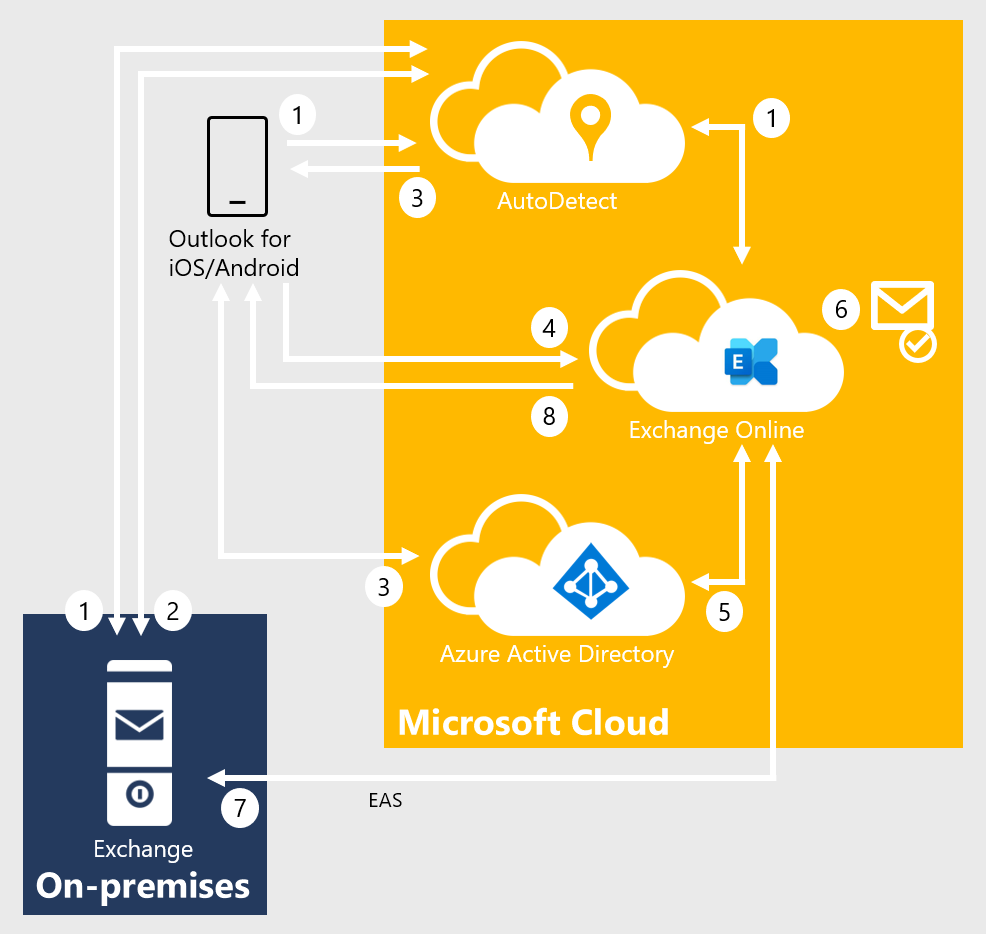
After the user enters their email address, Outlook for iOS and Android connects to the AutoDetect service. AutoDetect determines the mailbox type by starting an AutoDiscover query to Exchange Online. Exchange Online determines that the user's mailbox is on-premises and returns a 302-redirect to AutoDetect with the on-premises Autodiscover URL. AutoDetect starts a query against the on-premises AutoDiscover service to determine the ActiveSync endpoint for the email address. The URL attempted on-premises is similar to this example:
<https://autodiscover.contoso.com/autodiscover/autodiscover.json?Email=test%40contoso.com&Protocol=activesync&RedirectCount=3>.AutoDetect starts a connection to the on-premises ActiveSync URL returned in Step 1 above with an empty bearer challenge. The empty bearer challenge tells the on-premises ActiveSync that the client supports Modern Authentication. On-premises ActiveSync responds with a 401-challenge response and includes the WWW-Authenticate: Bearer header. Within the WWW-Authenticate: Bearer header is the authorization_uri value that identifies the Microsoft Entra endpoint that should be used to obtain an OAuth token.
AutoDetect returns the Microsoft Entra endpoint to the client. The client begins the sign in flow and the user is presented with a Web form (or redirected to the Microsoft Authenticator app) and can enter credentials. Depending on the identity configuration, this process might or might not involve a federated endpoint redirect to an on-premises identity provider. Ultimately, the client obtains an access-and-refresh token pair, which is named AT1/RT1. This access token is scoped to the Outlook for iOS and Android client with an audience of the Exchange Online endpoint.
Outlook for iOS and Android establishes a connection to Exchange Online and issues a provisioning request that includes the user's access token (AT1) and the on-premises ActiveSync endpoint.
The MRS provisioning API within Exchange Online uses AT1 as input and obtains a second access-and-refresh token pair (named AT2/RT2) to access the on-premises mailbox via an on-behalf-of call to Active Directory. This second access token is scoped with the client being Exchange Online and an audience of the on-premises ActiveSync namespace endpoint.
If the mailbox isn't provisioned, then the provisioning API creates a mailbox.
The MRS provisioning API establishes a secure connection to the on-premises ActiveSync endpoint and synchronizes the user's messaging data using the AT2 access token as the authentication mechanism. RT2 is used periodically to generate a new AT2 so that data can be synchronized in the background without user intervention.
Data is returned to the client.
Technical and licensing requirements
The hybrid Modern Authentication architecture has the following technical requirements:
Note
On-premises accounts leveraging hybrid Modern Authentication with Outlook mobile are not supported with Office 365 US Government Community and Defense tenants, Office 365 Germany tenants, and Office 365 China operated by 21Vianet tenants.
Exchange on-premises setup:
Exchange Server 2019 Cumulative Update 1 (CU1) or later, Exchange Server 2016 Cumulative Update 8 (CU8) or later, or Exchange Server 2013 CU19 or later on all Exchange servers. In hybrid deployments (on-premises Exchange and Exchange Online) or in organizations that use Exchange Online Archiving (EOA) with their on-premises Exchange deployment, you need to deploy the most current CU or one CU before the most current version.
All Exchange 2007 or Exchange 2010 servers must be removed from the environment. These versions of Exchange are out of mainstream support and don't work with Intune-managed Outlook for iOS and Android. In this architecture, Outlook for iOS and Android uses OAuth as the authentication mechanism. One of the on-premises configuration changes that occur enables the OAuth endpoint to the Microsoft Cloud as the default authorization endpoint. When this change is made, clients can start negotiating the use of OAuth. Because this change spans the whole organization, Exchange 2010 mailboxes fronted by either Exchange 2013 or 2016 incorrectly think they can do OAuth (they can't), and end up in a disconnected state (Exchange 2010 doesn't support OAuth as an authentication mechanism).
Active Directory Synchronization. Active Directory synchronization of the entire on-premises mail recipient directory with Microsoft Entra ID, via Microsoft Entra Connect. If you have Microsoft Entra app and attribute filtering enabled in Microsoft Entra Connect configuration, ensure that the following applications are selected:
- Office 365 ProPlus
- Exchange Online
- Azure RMS
- Intune
If you don't have Microsoft Entra app and attribute filtering enabled in Microsoft Entra Connect configuration, all required applications are already selected by default.
Important
Outlook for iOS and Android uses the tenant's Exchange Online Global Address List for on-premises mailboxes that leverage hybrid Modern Authentication. If all mail recipients aren't synchronized into Microsoft Entra ID, users will experience mail flow issues.
Exchange hybrid setup: Requires full hybrid relationship between Exchange on-premises with Exchange Online.
A hybrid Microsoft 365 or Office 365 organization is configured in full hybrid configuration using Exchange Classic Hybrid Topology mode and is set up as specified in the Exchange Deployment Assistant.
Note
Hybrid Modern Authentication is not supported with the Hybrid Agent.
Requires a Microsoft 365 or Office 365 Enterprise, Business, or Education organization.
The on-premises mailbox data is synchronized in the same datacenter region where that Microsoft 365 or Office 365 organization is set up or to the datacenter region defined in the account's PreferredDataLocation. For more information about where Microsoft 365 and Office 365 data is located, visit the Microsoft Trust Center. For more information on PreferredDataLocation, see Multi-Geo Capabilities.
The external URL host names for Exchange ActiveSync and AutoDiscover must be published as service principals to Microsoft Entra ID through the Hybrid Configuration Wizard.
AutoDiscover and Exchange ActiveSync namespaces must be accessible from the Internet and can't be fronted by a pre-authentication solution.
Ensure SSL or TLS offloading isn't being used between the load balancer and your Exchange servers, as this set up affects the use of the OAuth token. SSL and TLS bridging (termination and re-encryption) is supported.
Intune setup: Both Intune standalone and Co-Management deployments are supported (Basic Mobility and Security for Microsoft 365 isn't supported).
Microsoft 365 and Office 365 licensing:
- Outlook for iOS and Android is free for consumer usage from the iOS App store and from Google Play. However, commercial users require a Microsoft 365 or Office 365 subscription that includes the Office desktop applications: Microsoft 365 Apps for Business, Microsoft 365 Business Standard, Microsoft 365 Apps for enterprise, Office 365 Enterprise E3, Office 365 Enterprise E5, or the corresponding versions of those plans for Government or Education. Commercial users with the following subscriptions are allowed to use the Outlook mobile app on devices with integrated screens 10.1" diagonally or less: Office 365 Enterprise E1, Office 365 F1, Office 365 A1, Microsoft 365 Business Basic, and if you only have an Exchange Online license (without Office). If you only have an Exchange on-premises (Exchange Server) license, you aren't licensed to use the app.
- Use of advanced Exchange Online features (for example, Service Encryption with Customer Key or Multi-Geo Capabilities) require the on-premises user to be assigned the applicable Office 365 or Microsoft 365 subscription license within the Microsoft 365 Admin Center.
For more information on how to assign a license, see Add users individually or in bulk.
EMS licensing: Each on-premises user must have one of the following licenses:
- Intune standalone + Microsoft Entra ID P1 or P2 or Microsoft Entra ID P1 or P2
- Enterprise Mobility + Security E3, Enterprise Mobility + Security E5
Implementation steps
Enabling support for hybrid Modern Authentication in your organization requires each of the following steps, which are detailed in the following sections:
- Create a conditional access policy
- Create an Intune app protection policy
- Enable hybrid Modern Authentication
Create a conditional access policy
When an organization decides to standardize how users access Exchange data, using Outlook for iOS and Android as the only email app for end users, they can configure a conditional access policy that blocks other mobile access methods. Outlook for iOS and Android authenticates via the Microsoft Entra identity object and then connects to Exchange Online. Therefore, you need to create Microsoft Entra Conditional Access policies to restrict mobile device connectivity to Exchange Online. To do this task, you need two conditional access policies, with each policy targeting all potential users. Details on creating these policies can be found in Conditional Access: Require approved client apps or app protection policy.
Follow the steps in Require approved client apps or app protection policy with mobile devices. This policy allows Outlook for iOS and Android, but blocks OAuth and basic authentication capable Exchange ActiveSync mobile clients from connecting to Exchange Online.
Note
This policy ensures mobile users can access all Office endpoints using the applicable apps.
Follow the steps in Block Exchange ActiveSync on all devices, which prevents Exchange ActiveSync clients using basic authentication on non-mobile devices from connecting to Exchange Online.
The above policies use the grant control Require app protection policy, which ensures that an Intune App Protection Policy is applied to the associated account within Outlook for iOS and Android before granting access. If the user isn't assigned to an Intune App Protection Policy, isn't licensed for Intune, or the app isn't included in the Intune App Protection Policy, then the policy prevents the user from obtaining an access token and gaining access to messaging data.
Finally, follow Block legacy authentication with Microsoft Entra Conditional Access to block legacy authentication for other Exchange protocols on iOS and Android devices; this policy should target only Microsoft 365 or Office 365 Exchange Online cloud app and iOS and Android device platforms. This approach ensures mobile apps using Exchange Web Services, IMAP4, or POP3 protocols with basic authentication can't connect to Exchange Online.
Important
To leverage app-based conditional access policies, the Microsoft Authenticator app must be installed on iOS devices. For Android devices, the Intune Company Portal app is required. For more information, see App-based conditional access with Intune.
To block other mobile device clients (such as the native mail client included in the mobile operating system) from connecting to your on-premises environment (which authenticate via basic authentication against on-premises Active Directory):
You can use the built-in Exchange mobile device access rules and block all mobile devices from connecting by setting the following command in the Exchange Management Shell:
Set-ActiveSyncOrganizationSettings -DefaultAccessLevel Block
Note
The command might impact users connecting to Exchange on-premises with their mobile devices.
Create an Intune app protection policy
After hybrid Modern Authentication is enabled, all on-premises mobile users can use Outlook for iOS and Android using the Microsoft 365 or Office 365-based architecture. Therefore, it's important to protect corporate data with an Intune app protection policy.
Create Intune app protection policies for both iOS and Android using the steps documented in How to create and assign app protection policies. At a minimum, each policy must fulfill the following conditions:
They include all Microsoft mobile applications, such as Word, Excel, or PowerPoint, as this inclusion ensures that users can access and manipulate corporate data within any Microsoft app in a secure fashion.
They mimic the security features that Exchange provides for mobile devices, including:
- Requiring a PIN for access (which includes Select Type, PIN length, Allow Simple PIN, Allow fingerprint)
- Encrypting app data
- Blocking managed apps from running on "jailbroken" and rooted devices
They're assigned to all users. This wide assignation ensures that all users are protected, regardless of whether they use Outlook for iOS and Android.
In addition to the above minimum policy requirements, you should consider deploying advanced protection policy settings like Restrict cut, copy, and paste with other apps to further prevent corporate data leakage. For more information on the available settings, see Android app protection policy settings in Microsoft Intune and iOS app protection policy settings.
Important
To apply Intune app protection policies against apps on Android devices that are not enrolled in Intune, the user must also install the Intune Company Portal. For more information, see Android app protection policy settings in Microsoft Intune.
Enable hybrid Modern Authentication
If you haven't enabled hybrid Modern Authentication, review the prerequisites as outlined in Hybrid Modern Authentication overview and prerequisites for using it with on-premises Skype for Business and Exchange servers. After you complete the prerequisites, do the steps in How to configure Exchange Server on-premises to use hybrid Modern Authentication.
Create an Exchange on-premises device access allow rule to allow Exchange Online to connect to your on-premises environment using the ActiveSync protocol:
If ((Get-ActiveSyncOrganizationSettings).DefaultAccessLevel -ne "Allow") {New-ActiveSyncDeviceAccessRule -Characteristic DeviceType -QueryString "OutlookService" -AccessLevel Allow}Note
Device management through the on-premises Exchange admin center is not possible. Intune is required to manage mobile devices.
Create an Exchange on-premises device access rule that prevents users from connecting to the on-premises environment with Outlook for iOS and Android with basic authentication over the Exchange ActiveSync protocol:
New-ActiveSyncDeviceAccessRule -Characteristic DeviceModel -QueryString "Outlook for iOS and Android" -AccessLevel BlockNote
Once this rule is created, Outlook for iOS and Android with Basic authentication users are blocked.
Ensure your on-premises Exchange ActiveSync maxRequestLength is configured to match your transport configuration's MaxSendSize/MaxReceiveSize:
- Path:
%ExchangeInstallPath%\FrontEnd\HttpProxy\Sync\web.config - Property:
maxRequestLength - Value: set in KB size (10 MB is 10240, for example)
- Path:
Client features that aren't supported
The following features aren't supported for on-premises mailboxes using hybrid Modern Authentication with Outlook for iOS and Android.
- Draft folder and Draft messages synchronization
- Viewing more than four weeks of email by using the "Load More Messages" link at the bottom of the message list
- Shared calendar access and delegate calendar access
- Shared and delegate mailbox data access
- Cortana Time to Leave / Travel Time
- Rich meeting locations
- Task management with Microsoft To Do
- Add-ins
- Interesting Calendars
- Play My Emails
- Sensitivity labeling
- S/MIME
- Schedule Send
The following features are only supported when the on-premises infrastructure uses Exchange Server 2016 and later:
- Calendar attachments
Connection Flow FAQ
Q: My organization has a security policy that requires Internet inbound connections to be restricted to approved IP addresses or FQDNs. Is that configuration possible with this architecture?
A: Microsoft recommends that the on-premises endpoints for AutoDiscover and ActiveSync protocols be opened and accessible from the Internet without any restrictions. In certain situations that might not be possible. For example, if you're in a coexistence period with another third-party unified endpoint management (UEM) solution, you might want to place restrictions on the ActiveSync protocol to prevent users from bypassing the UEM solution while you migrate to Intune and Outlook for iOS and Android. If you must place restrictions on your on-premises firewall or gateway edge devices, Microsoft recommends filtering based on FQDN endpoints. If FQDN endpoints can't be used, then filter on IP addresses. Make sure the following IP subnets and FQDNs are included on your allowlist:
All Exchange Online FQDNs and IP subnet ranges as defined in More endpoints not included in the Microsoft 365 or Office 365 IP Address and URL Web service.
The AutoDetect FQDNs and IP subnet ranges defined in Additional endpoints not included in the Microsoft 365 or Office 365 IP Address and URL Web service. These IP subnets and FQDNs are required because the AutoDetect service establishes connections to the on-premises infrastructure.
All Outlook iOS and Android and Office mobile app FQDNs as defined in Microsoft 365 and Office 365 URLs and IP address ranges.
Q: My organization currently uses a third-party UEM solution to control mobile device connectivity. Exposing the Exchange ActiveSync namespace on the Internet introduces a way for users to bypass the third-party UEM solution during the coexistence period. How can I prevent this situation?
A: There are three potential solutions to resolving this issue:
- Implement Exchange mobile device access rules to control which devices are approved to connect.
- Some third-party UEM solutions integrate with Exchange mobile device access rules, blocking unapproved access, while adding approved devices in the user's ActiveSyncAllowedDeviceIDs property.
- Implement IP restrictions on the Exchange ActiveSync namespace.
Q: Can I use Azure ExpressRoute for managing traffic between the Microsoft Cloud and my on-premises environment?
A: Connectivity to the Microsoft Cloud requires Internet connectivity. Microsoft recommends exposing AutoDiscover and Exchange ActiveSync directly to the Internet; for more information, see Microsoft 365 and Office 365 Network Connectivity Principles. However, Azure ExpressRoute is supported for Exchange hybrid scenarios. For more information, see Azure ExpressRoute for Microsoft 365 and Office 365.
With ExpressRoute, there's no private IP space for ExpressRoute connections, nor can there be "private" DNS resolution. Any endpoint that your company wants to use over ExpressRoute must resolve in public DNS. If that endpoint resolves to an IP that's contained in the advertised prefixes associated with the ExpressRoute circuit (your company must configure those prefixes in the Azure portal when you enable Microsoft peering on the ExpressRoute connection), the outbound connection from Exchange Online to your on-premises environment is routed through the ExpressRoute circuit. Your company needs to ensure that the return traffic associated with these connections goes through the ExpressRoute circuit (avoiding asymmetric routing).
Important
Because Outlook for Android, iOS, and Mac are unable to support Azure ExpressRoute (and mobile native mail clients as well), we do not recommend using Azure ExpressRoute if you are planning to access your email on a mobile or Mac device. This is because there cannot be any overlaps of the public IP space advertised to Microsoft on the ExpressRoute circuit and the public IP space advertised on your Internet circuit(s).
Q: Given only four weeks of message data are synchronized to Exchange Online, does this mean that search queries executed in Outlook for iOS and Android can't return information beyond the data available on the local device?
A: When a search query is performed in Outlook for iOS and Android, items that match the search query are returned if they're located on the device. In addition, the search query is passed to Exchange on-premises via Exchange Online. Exchange on-premises executes the search query against the on-premises mailbox and returns the results to Exchange Online, which relays the results to the client. The on-premises query results are stored in Exchange Online for one day before being deleted.
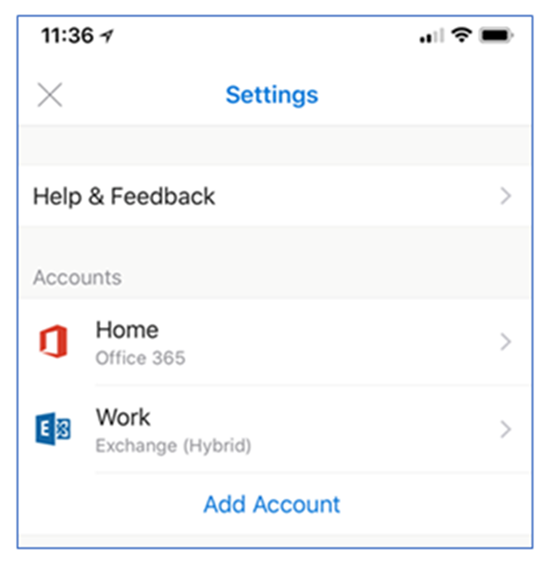
Q: How do I know that the email account is added correctly in Outlook for iOS and Android?
A: On-premises mailboxes that are added via hybrid Modern Authentication are labeled as Exchange (Hybrid) in the account settings in Outlook for iOS and Android, similar to the following example:
Authentication FAQ
Q: What identity configurations are supported with hybrid Modern Authentication and Outlook for iOS and Android?
A: The following identity configurations with Microsoft Entra ID are supported with hybrid Modern Authentication:
- Federated Identity with any on-premises identity provider that is supported by Microsoft Entra ID
- Password Hash Synchronization via Microsoft Entra Connect
- Pass-through Authentication via Microsoft Entra Connect
Q: What authentication mechanism is used for Outlook for iOS and Android? Are credentials stored in Microsoft 365 or Office 365?
A: See Account setup with modern authentication in Exchange Online.
Q: Do Outlook for iOS and Android and other Microsoft Office mobile apps support single sign-on?
A: See Account setup with modern authentication in Exchange Online.
Q: What is the lifetime of the tokens generated and used by the Active Directory Authentication Library (ADAL) in Outlook for iOS and Android?
A: See Account setup with modern authentication in Exchange Online.
Q: What happens to the access token when a user's password is changed?
A: See Account setup with modern authentication in Exchange Online.
Q: Is there a way for a user to bypass AutoDetect when adding their account to Outlook for iOS and Android?
A: Yes, a user can bypass AutoDetect at any time and manually configure the connection using Basic authentication over the Exchange ActiveSync protocol. To ensure that the user doesn't establish a connection to your on-premises environment via a mechanism that doesn't support Microsoft Entra Conditional Access or Intune app protection policies, the on-premises Exchange Administrator needs to configure an Exchange device access rule that blocks the ActiveSync connection. To do this task, type the following command in the Exchange Management Shell:
New-ActiveSyncDeviceAccessRule -Characteristic DeviceModel -QueryString "Outlook for iOS and Android" -AccessLevel Block
Q: What happens when an organization moves from basic authentication with Outlook for iOS and Android to hybrid Modern authentication?
A: After an organization enables hybrid modern authentication following the above Implementation steps, end users need to delete their existing account profile in Outlook for iOS and Android as the profile uses basic authentication. End users can then create a new profile which uses hybrid Modern authentication.
Troubleshooting
This section describes the most common issues or errors with on-premises mailboxes using hybrid Modern Authentication with Outlook for iOS and Android.
AutoDiscover and ActiveSync
During profile creation, the user should be presented a Modern Authentication dialog similar to the one in the following screenshot:
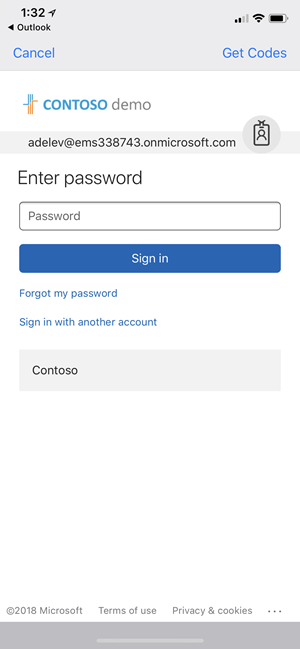
If, instead, the user is presented with one of the following dialogs, then there's an issue with either the Autodiscover or ActiveSync on-premises endpoints.
Here's an example of a user being presented with the legacy Basic authentication Exchange ActiveSync experience:
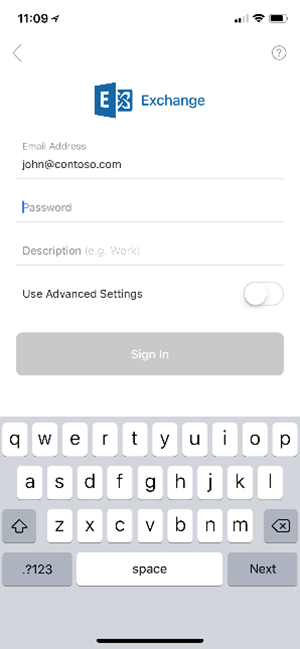
And here's an example of what users see when AutoDetect isn't able to discover the configuration for users' on-premises mailboxes.

In either scenario, verify that your on-premises environment is correctly configured. To do this task: from the TechNet Gallery, download and execute the script for Validating Hybrid Modern Authentication setup for Outlook for iOS and Android.
When you review the output from the script, you should be seeing the following output from AutoDiscover:
{
"Protocol": "activesync",
"Url": "https://mail.contoso.com/Microsoft-Server-ActiveSync"
}
The on-premises ActiveSync endpoint should return the following response, where the WWW-Authenticate header includes an authorization_uri:
Content-Length →0
Date →Mon, 29 Jan 2018 19:51:46 GMT
Server →Microsoft-IIS/10.0 Microsoft-HTTPAPI/2.0
WWW-Authenticate →Bearer client_id="00000002-0000-0ff1-ce00-000000000000", trusted_issuers="00000001-0000-0000-c000-000000000000@5de110f8-2e0f-4d45-891d-bcf2218e253d,00000004-0000-0ff1-ce00-000000000000@contoso.com", token_types="app_asserted_user_v1 service_asserted_app_v1", authorization_uri="https://login.windows.net/common/oauth2/authorize"
Www-Authenticate →Basic realm="mail.contoso.com"
X-Powered-By →ASP.NET
request-id →5ca2c827-5147-474c-8457-63c4e5099c6e
If the AutoDiscover or ActiveSync responses aren't similar to the above examples, you can investigate the following causes to be the possible ones:
If the AutoDiscover endpoint can't be reached, then it's likely there's a firewall or load balancer configuration issue (for example, IP restrictions are configured and the required IP ranges aren't present). Also, there might be a device in front of Exchange requiring pre-authentication to access the AutoDiscover endpoint.
If the AutoDiscover endpoint doesn't return the correct URL, then there's a configuration issue with the ActiveSync virtual directory's ExternalURL value.
If the ActiveSync endpoint can't be reached, then there's a firewall or load balancer configuration issue. Again, one example is IP restrictions are configured and the required IP ranges aren't present. Also, there might be a device in front of Exchange requiring pre-authentication to access the ActiveSync endpoint.
If the ActiveSync endpoint doesn't contain an authorization_uri value, verify that the EvoSTS authentication server is configured as the default endpoint using Exchange Management Shell:
Get-AuthServer EvoSts | Format-List IsDefaultAuthorizationEndpointIf the ActiveSync endpoint doesn't contain a WWW-Authenticate header, then a device in front of Exchange might be responding to the query.
Client synchronization issues
There are a few scenarios that can result in data being stale in Outlook for iOS and Android. Typically, this data condition is due to an issue with the second access token (the token used by MRS in Exchange Online to synchronize the data with the on-premises environment). The two most common reasons for this issue are:
- SSL/TLS offloading on-premises.
- EvoSTS certificate metadata issues.
With SSL/TLS offloading, tokens are issued for a specific uri and that value includes the protocol value ("https://"). When the load balancer offloads SSL/TLS, the request received by Exchange comes in via HTTP, resulting in a claim mismatch due to the protocol value being http://. The following example depicts a response header from a Fiddler trace:
Content-Length →0
Date →Mon, 29 Jan 2018 19:51:46 GMT
Server →Microsoft-IIS/10.0 Microsoft-HTTPAPI/2.0
WWW-Authenticate →Bearer client_id="00000002-0000-0ff1-ce00-000000000000", trusted_issuers="00000001-0000-0000-c000-000000000000@00c118a9-2de9-41d3-b39a-81648a7a5e4d", authorization_uri="https://login.windows.net/common/oauth2/authorize", error="invalid_token"
WWW-Authenticate →Basic realm="mail.contoso.com"
X-Powered-By →ASP.NET
request-id →2323088f-8838-4f97-a88d-559bfcf92866
x-ms-diagnostics →2000003;reason="The hostname component of the audience claim value is invalid. Expected 'https://mail.contoso.com'. Actual 'http://mail.contoso.com'.";error_category="invalid_resource"
As specified above in the section Technical and licensing requirements, SSL/TLS offloading isn't supported for OAuth flows.
For EvoSTS Certificate Metadata, the certificate metadata used by EvoSTS is occasionally updated in Microsoft 365 or Office 365. The Exchange on-premises arbitration mailbox that has the organization capability of "OrganizationCapabilityManagement" is responsible for detecting the changes and for updating the corresponding metadata on-premises; this process executes every eight hours.
Exchange Administrators can find this mailbox by executing the following cmdlet using Exchange Management Shell:
$x=Get-mailbox -arbitration | ? {$_.PersistedCapabilities -like "OrganizationCapabilityManagement"};Get-MailboxDatabaseCopyStatus $x.database.name
On the server hosting the database for the OrganizationCapabilityManagement arbitration mailbox, review the application event logs for events with a source of MSExchange AuthAdmin. The events should tell you if Exchange can refresh the metadata. If the metadata is out of date, you can manually refresh it with this cmdlet:
Set-AuthServer EvoSts -RefreshAuthMetadata
You can also create a scheduled task that executes the above command every 24 hours.
Exchange Online statistics
You can use the following Exchange Online cmdlets to see statistical information for each synchronized on-premises mailbox.
First, obtain the location of the synchronized on-premises mailbox in the tenant, specifying the on-premises mailbox's identity (for example,
jane@contoso.com).$m = Get-MailboxLocation <identity>To see mailbox-related statistics, use
Get-MailboxStatistics $m.idTo see mobile device statistics (like seeing when Outlook for iOS and Android last synchronized to Exchange Online), use
Get-MobileDeviceStatistics -Mailbox $m.id
For more information, see Get-MailboxStatistics and Get-MobileDeviceStatistics.
Other issues
There are other issues that might prevent hybrid Modern Authentication from functioning correctly. For more information, see the troubleshooting section in Announcing Hybrid Modern Authentication for Exchange On-Premises.