1.3.1 NTLM Authentication Call Flow
This section provides an overview of the end-to-end message flow when application protocols use NTLM to authenticate a user to a server.
The following diagram shows a typical connection-oriented NTLM message flow when an application uses NTLM. The message flow typically consists of a number of application messages, followed by NTLM authentication messages (which are embedded in the application protocol and transported by the application from the client to the server), and then additional application messages, as specified in the application protocol.
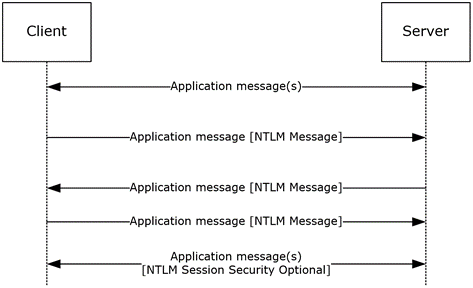
Figure 1: Typical NTLM authentication message flow
Note In the preceding diagram, the embedding of NTLM messages in the application protocol is shown by placing the NTLM messages within [ ] brackets. NTLM messages for both connection-oriented and connectionless authentication are embedded in the application protocol as shown. Variations between the connection-oriented and connectionless NTLM protocol sequence are documented in sections 1.3.1.1 and 1.3.1.2.
After an authenticated NTLM session is established, the subsequent application messages can be protected with NTLM session security. This is done by the application, which specifies what options (such as message integrity or confidentiality, as specified in the Abstract Data Model) it requires, before the NTLM authentication message sequence begins.<3>
Success and failure messages that are sent after the NTLM authentication message sequence are specific to the application protocol invoking NTLM authentication and are not part of the NTLM Authentication Protocol.
Note In subsequent message flows, only the NTLM message flows are shown because they are the focus of this document. Keep in mind that the NTLM messages in this section are embedded in the application protocol and transported by that protocol.
An overview of the connection-oriented and connectionless variants of NTLM is provided in the following sections.