1.3.4 Role-Based Security Configuration
Role-based security is a model for authorization in which user accounts are grouped into roles and authorization decisions for an operation are based on whether the user account of the requestor of an operation belongs to a particular role. COMA enables configuration of role-based security for conglomerations through role and role member objects. The following UML diagram shows the relationship between these types of objects and other object types in the catalog.
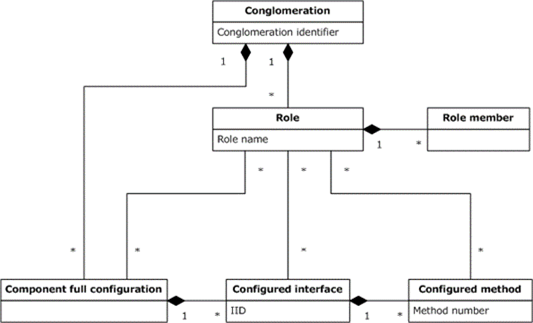
Figure 3: Role-related objects
A role is identified by a role name and is a set of role members that represents authorization for a set of operations that is supported by the components configured in a conglomeration. A role member is a predicate indicating that a particular user account belongs to a role.
Role-based security can be programmatic (dynamic) or declarative (static). In the programmatic model, the ORB provides an implementation-specific mechanism by which a component configured in a conglomeration can dynamically determine whether the user account of the requestor belongs to a particular role, in order to make authorization decisions. In the declarative model, the component configuration entries in a conglomeration statically specify which roles are authorized to perform specific operations. COMA enables configuration of both programmatic and declarative role-based security.
COMA supports enabling or disabling role-based security for a conglomeration. If role-based security is enabled, programmatic role-based security is automatically supported. Declarative role-based security, on the other hand, can be enabled and configured at multiple levels of granularity.
A conglomeration is said to be configured for conglomeration-level access checks if all operations supported by the components configured in the conglomeration require the user account of the requestor to belong to one of the conglomeration's roles. Conglomerations can be configured to enable or disable conglomeration-level access checks.
A COMA server optionally supports configuration of components at the interface and method levels, the primary purpose of which is declarative role-based security configuration. This configuration is supported for component full configuration entries only. A configured interface is a set of methods supported by a component and for which configuration at the interface level is supported. A configured interface is identified by an interface identifier (IID). A configured method is a method in a configured interface for which configuration at the method level is supported.
A component is said to be configured for component-level access checks if the component uses declarative role-based security configuration at the component, interface, and method levels for authorization. For the purpose of component-level access checks, roles can be associated with component full configuration entries, configured interfaces, and configured methods. This configuration has the following semantics:
If a role is associated with a component full configuration entry, that role is authorized for all methods supported by the component.
If a role is associated with a configured interface, that role is authorized for all methods in that interface.
If a role is associated with a configured method, that role is authorized for that method.