下列要求可用來使用 Microsoft Graph API 擷取建議和受影響的資源。 若要使用 Microsoft Graph API,您需要 DirectoryRecommendations.Read.All 和 DirectoryRecommendations.ReadWrite.All 許可權。 如需詳細資訊,請參閱 如何使用身分識別建議。
使用 Microsoft Graph 更新服務主體認證時,您必須執行查詢以取得服務主體上的密碼認證、新增密碼認證,然後移除舊的認證。
- 登入 Graph 總管。
- 從下拉式清單中選取 [GET] 作為 HTTP 方法。
若要擷取租使用者的所有建議:
GET https://graph.microsoft.com/beta/directory/recommendations
從回應中,尋找符合下列模式的建議標識碼: {tenantId}_Microsoft.Identity.IAM.Insights.servicePrincipalKeyExpiry。
若要識別受影響的資源:
GET https://graph.microsoft.com/beta/directory/recommendations/{tenantId}_Microsoft.Identity.IAM.Insights.servicePrincipalKeyExpiry
若要根據資源的狀態篩選資源清單,例如,只有標示為 active的資源:
https://graph.microsoft.com/beta/directory/recommendations/{tenantId}_Microsoft.Identity.IAM.Insights. servicePrincipalKeyExpiry/impactedResources?$filter=status eq Microsoft.Graph.recommendationStatus'active'
- 記下
AppId您想要移除之認證的、 CredentialId和 來源。
- 使用這些Microsoft Graph API 來新增密碼或金鑰認證:
- 使用這些Microsoft Graph API 來移除舊的認證:
範例回覆
{
"id": "536279f6-15cc-45f2-be2d-61e352b51eef_Microsoft.Identity.IAM.Insights.ServicePrincipalKeyExpiry",
"recommendationType": "servicePrincipalKeyExpiry",
"createdDateTime": "2022-05-29T00:11:17Z",
"impactStartDateTime": "2022-05-29T00:11:17Z",
"postponeUntilDateTime": null,
"lastModifiedDateTime": "2024-07-26T12:31:58Z",
"lastModifiedBy": "System",
"displayName": "Renew expiring service principal credentials",
"featureAreas": [
"applications"
],
"insights": "Your tenant has service principals with credentials that will expire soon.",
"benefits": "Renewing the service principal credential(s) before expiration ensures the application continues to function and reduces the possibility of downtime due to an expired credential.",
"category": "identityBestPractice",
"status": "completedBySystem",
"priority": "high",
"requiredLicenses": "microsoftEntraWorkloadId",
"impactType": "apps",
"actionSteps": [
{
"stepNumber": 1,
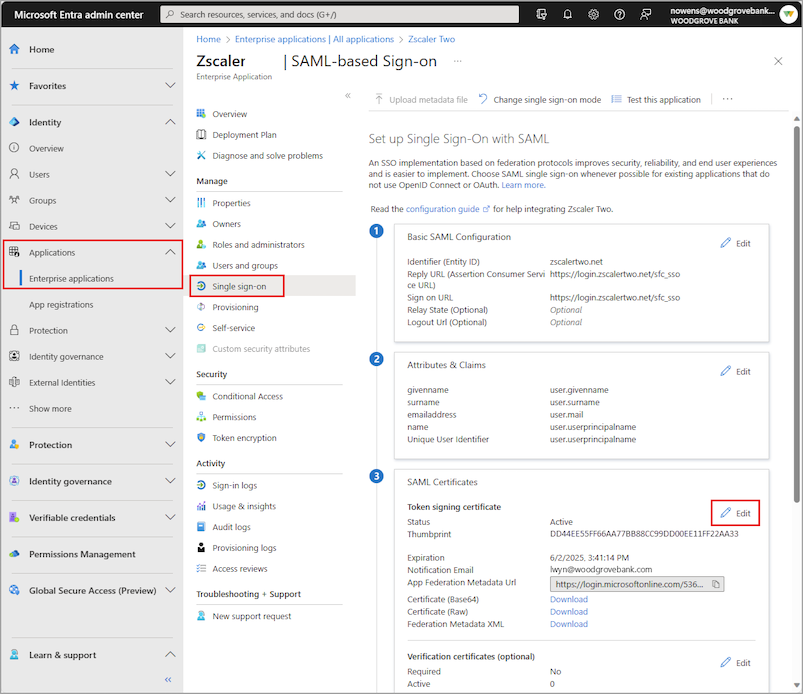
"text": "1. Navigate to the Enterprise applications section and locate the Enterprise application for which the credential needs to be rotated."
},
{
"stepNumber": 2,
"text": "2. Navigate to the “Single sign-on” blade."
},
{
"stepNumber": 3,
"text": "3. Edit the 'SAML signing certificate' section and follow prompts to add a new certificate."
},
{
"stepNumber": 4,
"text": "4. After adding the certificate, change its properties to make certificate active. This will make the previous certificate inactive."
},
{
"stepNumber": 5,
"text": "5. Once the certificate is successfully added and activated, validate that your service is working with the new credential, and remove the old credential."
},
{
"stepNumber": 6,
"text": "6. If the service principal does not show any credentials after navigating to the enterprise apps blade, we recommend checking the 'passwordCredentials' and 'keyCredentials' property of the service principal object using PowerShell or Microsoft Graph service principal API and use the Microsoft Graph API to rotate credentials."
}
]
}