使用 Azure PowerShell 或 ARM 範本建立 Azure 資源
本文說明如何使用 Microsoft Azure PowerShell 或 Azure Resource Manager (ARM) 範本建立電子發票所需的 Azure 資源。
若要在 Dynamics 365 Finance 中啟用電子發票,您必須建立和設定多個 Azure 資源,例如 Azure key vault、Azure 儲存體帳戶和 Azure 儲存體帳戶容器。 如果手動完成此過程可能會非常耗時且容易出錯。 為了簡化和自動化此流程,您可以使用 PowerShell 指令碼或 ARM 範本來為您建立和設定所有必需的 Azure 資源。
使用 Azure PowerShell
必要條件
在您執行 PowerShell 指令碼前 ,必須先符合以下先決條件:
- 您擁有一個具有足夠權限來建立和管理資源的 Azure 訂閱。
- 您已安裝 Azure PowerShell 模組。 (建議結合使用受支援的 PowerShell 版本 7 或更新版本與 Azure PowerShell 模組。)
- 您擁有 PowerShell 指令碼檔案。
PowerShell 指令碼
param (
[Parameter(Mandatory=$true)]
[string]$subscriptionId,
[Parameter(Mandatory=$true)]
[string]$resourceGroup,
[Parameter(Mandatory=$true)]
[string]$location,
[Parameter(Mandatory=$true)]
[string]$storageAccountName,
[Parameter(Mandatory=$true)]
[string]$keyVaultName,
[Parameter(Mandatory=$true)]
[string]$containerName,
[Parameter(Mandatory=$true)]
[string]$storageAccountKeyVaultSecretName
)
if (!(Get-Module -ListAvailable -Name Az)) {
throw "Az PowerShell module is required to run this script. Please install from https://learn.microsoft.com/en-us/powershell/azure/install-azure-powershell."
}
function Write-ErrorMessage {
param (
[string]$errorMessage
)
Write-Host "Error: $errorMessage" -ForegroundColor Red
exit 1
}
function Write-VerboseMessage {
param (
[string]$message
)
Write-Host "Verbose: $message" -ForegroundColor DarkYellow
}
function Confirm-ResourceExists {
param (
[string]$resourceType,
[string]$resourceName,
[string]$resourceGroup = ''
)
try {
switch ($resourceType) {
'ResourceGroup' {
Get-AzResourceGroup -Name $resourceName -ErrorAction Stop | Out-Null
}
'StorageAccount' {
Get-AzStorageAccount -ResourceGroupName $resourceGroup -Name $resourceName -ErrorAction Stop | Out-Null
}
'StorageContainer' {
Get-AzStorageContainer -Name $resourceName -ErrorAction Stop | Out-Null
}
'KeyVault' {
$kv = Get-AzKeyVault -ResourceGroupName $resourceGroup -VaultName $resourceName
if ($null -eq $kv)
{
return $false
}
}
}
return $true
} catch {
return $false
}
}
# Connect to Azure account and set the subscription context
try {
Write-VerboseMessage "Connecting to Azure account..."
Connect-AzAccount -Subscription $subscriptionId -ErrorAction Stop -Verbose
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to connect to the Azure account or set subscription context."
}
try {
Write-VerboseMessage "Checking if the e-invoice service principal exists."
$objectId = (Get-AzADServicePrincipal -ApplicationId "ecd93392-c922-4f48-9ddf-10741e4a9b65" -ErrorAction SilentlyContinue -Verbose).Id
if ($null -eq $objectId)
{
Write-VerboseMessage "The e-invoice service principal does not exist. Trying to create now."
New-AzADServicePrincipal -AppId "ecd93392-c922-4f48-9ddf-10741e4a9b65" -ErrorAction Stop -Verbose
}
else {
Write-VerboseMessage "The e-invoice service principal already exists. No action required."
}
}
catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Adding e-Invoicing Service to your tenant as a service principal failed."
}
# Check if the resource group exists
if (-not (Confirm-ResourceExists -resourceType 'ResourceGroup' -resourceName $resourceGroup)) {
try {
Write-VerboseMessage "Creating Azure resource group..."
New-AzResourceGroup -Name $resourceGroup -Location $location -ErrorAction Stop -Verbose
$msg = "Resource group {0} created successfully in at location: {1}." -f $resourceGroup, $location
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to create Azure resource group."
}
} else {
Write-VerboseMessage "Resource group '$resourceGroup' already exists."
}
# Check if the Azure Key Vault exists
if (-not (Confirm-ResourceExists -resourceType 'KeyVault' -resourceName $keyVaultName -resourceGroup $resourceGroup)) {
try {
Write-VerboseMessage "Creating Azure Key Vault..."
New-AzKeyVault -Name $keyVaultName -ResourceGroupName $resourceGroup -Location $location -ErrorAction Stop -Verbose
$msg = "Key vault {0} created successfully in resource group: {1} at location: {2}." -f $keyVaultName, $resourceGroup, $location
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to create Azure Key Vault."
}
} else {
Write-VerboseMessage "Azure Key Vault '$keyVaultName' already exists."
}
# Check if the storage account exists
if (-not (Confirm-ResourceExists -resourceType 'StorageAccount' -resourceName $storageAccountName -resourceGroup $resourceGroup)) {
try {
Write-VerboseMessage "Creating Azure Storage Account..."
New-AzStorageAccount -ResourceGroupName $resourceGroup `
-Name $storageAccountName `
-Location $location `
-SkuName Standard_LRS `
-Kind StorageV2 `
-AllowBlobPublicAccess $true -ErrorAction Stop -Verbose
$msg = "Storage account {0} created successfully in resource group: {1} at location: {2}." -f $storageAccountName, $resourceGroup, $location
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to create Azure Storage Account."
}
} else {
Write-VerboseMessage "Storage account '$storageAccountName' already exists."
}
# Check if the storage container exists
$ctx = (Get-AzStorageAccount -ResourceGroupName $resourceGroup -Name $storageAccountName).Context
Set-AzCurrentStorageAccount -Context $ctx
if (-not (Confirm-ResourceExists -resourceType 'StorageContainer' -resourceName $containerName -resourceGroup $resourceGroup)) {
try {
Write-VerboseMessage "Creating storage container..."
New-AzStorageContainer -Name $containerName -Context $ctx -ErrorAction Stop -Verbose
$msg = "Storage container {0} created successfully in storage account: {1}." -f $containerName, $storageAccountName
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to create storage container."
}
} else {
Write-VerboseMessage "Storage container '$containerName' already exists."
}
# Set the start and end time for the SAS token
$StartTime = Get-Date
$EndTime = $StartTime.AddYears(3)
# Generate SAS token for the container
try {
Write-VerboseMessage "Generating SAS token for the container..."
$sasToken = New-AzStorageContainerSASToken -Name $containerName -Permission racwdli -Protocol HttpsOnly -StartTime $StartTime -ExpiryTime $EndTime -Context $ctx -ErrorAction Stop -Verbose
$msg = "SAS token for container {0} generated successfully with full permissions. The token would expire on {1}." -f $containerName, $EndTime
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to generate SAS token for the container."
}
# Construct the SAS URL
$sasURL = "https://$($storageAccountName).blob.core.windows.net/$($containerName)?$($sastoken)"
# Set access policy for the application to get and list secrets
try {
Write-VerboseMessage "Setting access policy for Azure Key Vault..."
Set-AzKeyVaultAccessPolicy -VaultName $keyVaultName -ObjectId $objectId -PermissionsToSecrets get,list -ErrorAction Stop -Verbose
$msg = "Get and list access policies set successfully on key vault {0} for the e-invoicing application {1}." -f $keyVaultName, $objectId
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to set access policy for Azure Key Vault."
}
# Convert SAS URL to secure string
$secretvalue = ConvertTo-SecureString $sasURL -AsPlainText -Force
# Create a new secret in Azure Key Vault
try {
Write-VerboseMessage "Creating secret in Azure Key Vault..."
Set-AzKeyVaultSecret -VaultName $keyVaultName -Name $storageAccountKeyVaultSecretName -SecretValue $secretvalue -Expires $EndTime -ContentType "" -ErrorAction Stop -Verbose
$msg = "Secret {0} created successfully in {1} and will expire on {2}." -f $storageAccountKeyVaultSecretName, $keyVaultName, $EndTime
Write-VerboseMessage $msg
} catch {
Write-Host $_.Exception.Message
Write-ErrorMessage "Failed to create secret in Azure Key Vault."
}
# Display the secret
Write-Host "Secret created successfully."
執行 PowerShell 指令碼
如要執行 PowerShell 指令碼 ,請按照以下步驟操作。
開啟 PowerShell,進入 PowerShell 指令碼檔案和設定檔所在的資料夾。
若要使用您自己的參數執行 PowerShell 指令碼,請執行以下命令。
.\Create-AzureResourcesForEInvoice.ps1 -subscriptionId <azure_subscription_id> -resourceGroup <resource_group_name> -location <resource_group_location> -storageAccountName <storage_account_name> -containerName <container_name> -storageAccountKeyVaultSecretName <SAS_token_keyvault_secret_name>
PowerShell 指令碼會執行以下動作。
- 該指令碼會提示您登入 Azure 帳戶。 輸入您的認證,然後選取登入。
- 此指令碼會確定電子發票服務主體是否已存在。 如果它不存在,指令碼將建立它。
- 此指令碼會確定以下 Azure 資源是否已存在:Azure 資源群組、 Azure key vault、Azure 儲存體帳戶和 Azure 儲存體帳戶容器。 如果其中任何一個不存在,指令碼將建立並設定它們。
- 此指令碼為儲存體帳戶容器產生共用存取簽章 (SAS) 權杖,並將其新增為金鑰保存庫中的 Key Vault 密碼。
- 該指令碼在密鑰保存庫上設定存取原則,以向電子發票應用程式提供取得和列出權限。
- 作為輸出,此指令碼會產生已建立的 Azure 資源的詳細資訊。 這些詳細資訊包括名稱和 URL。
附註
如果您必須續訂已過期的 SAS 權杖,您可以執行相同的指令碼。 在這種情況下,指令碼不會建立資源。 相反地,它只會產生一個新的 SAS 權杖並在金鑰保存庫中更新它。
使用 ARM 範本
ARM 範本
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"keyVaultName": {
"type": "string",
"metadata": {
"description": "Name of KeyVault to Store secrets/certificates/SaS Token"
}
},
"tenantID": {
"type": "string",
"metadata": {
"description": "Azure AD Tenant ID"
}
},
"keyVaultAccessObjectID": {
"type": "string",
"metadata": {
"description": "ID of user or App to grant access to KV"
},
"defaultValue": "ecd93392-c922-4f48-9ddf-10741e4a9b65"
},
"StorageAccountName": {
"type": "string",
"metadata": {
"description": "Name of Storage Account to Create"
}
},
"ContainerName": {
"type": "string",
"metadata": {
"description": "Name of container for einvoice upload"
}
},
"accountSasProperties": {
"type": "object",
"defaultValue": {
"signedServices": "bf",
"signedPermission": "rwacld",
"signedExpiry": "2024-12-01T00:00:00Z",
"signedResourceTypes": "o"
}
}
},
"variables": {},
"resources": [
{
"name": "[parameters('StorageAccountName')]",
"type": "Microsoft.Storage/storageAccounts",
"apiVersion": "2018-07-01",
"location": "[resourceGroup().location]",
"tags": {
"displayName": "[parameters('StorageAccountName')]"
},
"sku": {
"name": "Standard_LRS"
},
"kind": "StorageV2",
"properties": {
"allowBlobPublicAccess": true
},
"resources":[
{
"type": "blobServices/containers",
"apiVersion": "2018-03-01-preview",
"name": "[concat('default/', parameters('ContainerName'))]",
"dependsOn": [
"[parameters('StorageAccountName')]"
],
"properties": {
"publicAccess": "None"
}
}
]
},
{
"type": "Microsoft.KeyVault/vaults",
"apiVersion": "2018-02-14",
"name": "[parameters('keyVaultName')]",
"location": "[resourceGroup().location]",
"tags": {
"displayName": "[parameters('keyVaultName')]"
},
"properties": {
"enabledForDeployment": true,
"enabledForTemplateDeployment": true,
"enabledForDiskEncryption": true,
"tenantId": "[parameters('tenantID')]",
"accessPolicies": [
{
"tenantId": "[parameters('tenantID')]",
"objectId": "[parameters('keyVaultAccessObjectID')]",
"permissions": {
"keys": [
"get"
],
"secrets": [
"list",
"get"
]
}
}
],
"sku": {
"name": "standard",
"family": "A"
}
}
},
{
"apiVersion": "2018-02-14",
"type": "Microsoft.KeyVault/vaults/secrets",
"dependsOn": [
"[concat('Microsoft.KeyVault/vaults/', parameters('keyVaultName'))]"
],
"name": "[concat(parameters('keyVaultName'), '/', 'StorageSaSToken')]",
"properties": {
"value": "[concat('https://', parameters('StorageAccountName'), '.blob.core.windows.net/', parameters('ContainerName'), '?', listAccountSas(parameters('StorageAccountName'), '2018-07-01', parameters('accountSasProperties')).accountSasToken)]"
}
}
],
"outputs": {}
}
部署 ARM 範本
若要部署 ARM 範本,請按照以下步驟操作。
登入 Azure 入口網站,並搜尋部署自訂範本。
選取在編輯器中組建自己的範本。
複製本文上一節中提供的 ARM 範本,將其貼到編輯器中,然後選取儲存。
提供必要參數:
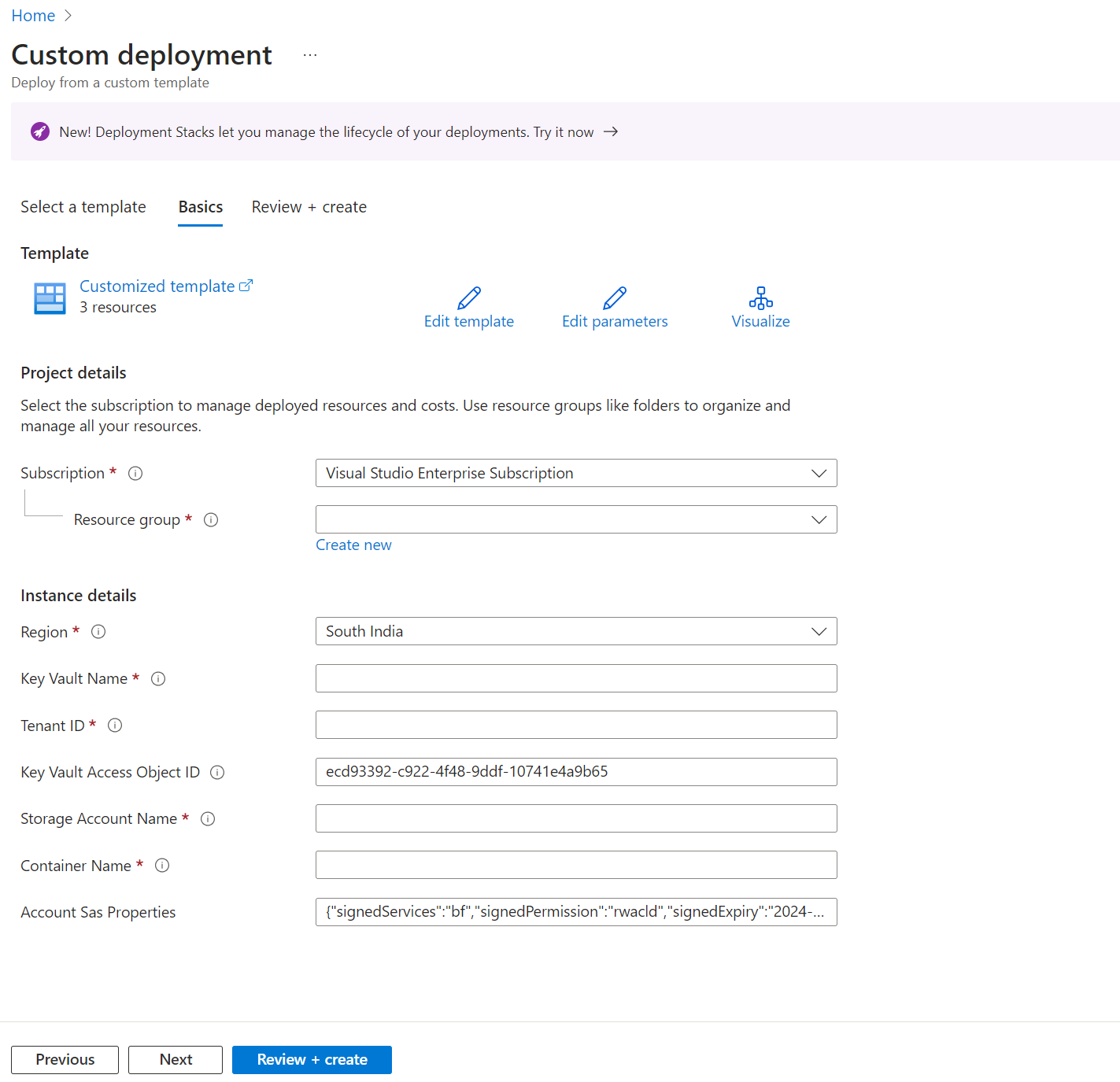
選取檢閱 + 建立。
檢閱詳細資訊,然後選取建立。
驗證 Azure 資源
若要驗證 Azure 資源是否正確建立和設定,您可以執行以下步驟。
- 登入 Azure 入口網站,並移至包含 Azure 資源的資源群組。 您應該會看到具有您在 PowerShell 指令碼或 ARM 範本參數中指定的名稱的資源。
- 開啟 Key Vault 資源,並確認 Azure 儲存體帳戶的 SAS 權杖已建立並具有正確的值。